Just as paparazzi always follow celebrities, hackers always keep an eye on popular trends, solutions, and products. Cryptocurrency and blockchain technologies are some of the hottest targets for cyber criminals today. According to a report by Carbon Black, more than $1.1 billion was stolen in various cryptocurrencies in 2018 alone. Curiously, nearly half of this stolen money is attributed to a single case — the CoinCheck exchange hack, the largest cryptocurrency heist so far.
In this post, we take a detailed look at what made the CoinCheck hack possible, explain the mechanism behind the attack, provide interesting CoinCheck hack details, and describe how the CoinCheck exchange and the NEM network handled this problem.
Contents:
The CoinCheck hack
CoinCheck is one of the largest cryptocurrency exchanges in the world. The CoinCheck hack date — January 26, 2018. That day, the exchange reported a major security breach and stopped all activity to prevent further damage. Unfortunately, by the time CoinCheck discovered the problem, hackers had already stolen an enormous number of XEM coins — the native token of the NEM blockchain. In total, CoinCheck hackers laid their hands on 560 million XEM coins, worth around $400 million.
What made it easy for hackers to steal all this money was one strategic mistake by CoinCheck. You see, many centralized exchanges like CoinCheck store all of their customers’ currency in on-chain wallets, while actual conversions usually happen off-chain. In other words, an exchange service’s wallet usually holds huge amounts of cryptocurrency and, therefore, has to be well protected. Unfortunately, the people at CoinCheck chose flexibility over increased security.
Choosing the wrong wallet
Cryptocurrency is stored in digital wallets. There are two basic types of wallets:
- Cold wallet – This type of wallet offers a high level of protection. A cold wallet isn’t connected to the internet and can be stored in a safe place. The main drawback of cold wallets is the slow speed of operations with the cryptocurrency.
- Hot wallet – In contrast to a cold wallet, a hot wallet is connected to the internet and is always online. This way, funds stored in the wallet are easier to move and trade. The price of this increased flexibility is a lower level of security.
Cold and hot wallets complement each other, and many people who own cryptocurrency prefer to have both types of wallets. This way they can store the majority of their funds in a safer cold wallet and move cryptocurrency to a hot wallet only when necessary.
Unfortunately, CoinCheck decided to store all of their XEM tokens in a hot wallet. Furthermore, that wallet had a regular account on the NEM network and didn’t even implement NEM’s built-in multi-signature features.
As a result, it wasn’t that difficult for hackers to compromise one of CoinCheck’s accounts and gain access to the wallet. Hackers used conventional methods — phishing and malware — to target a CoinCheck employee. Next, they stole the private key to the hot wallet where all of the exchange’s XEM was stored. Once the attackers got their hands on that single private key to the hot wallet, all that was left to do was to take the coins and run.
There’s no denying that CoinCheck is mostly at fault here since they could’ve done a better job protecting their wallet and their customers’ cryptocurrency. Luckily for the victims of the CoinCheck hack, NEM developers were quick to mitigate the attack.
Tracking suspicious transactions with a mosaic
The speed with which NEM developers responded to the attack is noteworthy. They detected a suspicious transaction performed by the attackers on the same day, and in a matter of hours the NEM team was already looking for a way to track and mark the stolen funds.
1/ @coincheckjp hack update: NEM is creating an automated tagging system that will be ready in 24-48 hours. This automated system will follow the money and tag any account that receives tainted money. NEM has already shown exchanges how to check if an account has been tagged.
— Inside NEM (@Inside_NEM) January 26, 2018
Tracking cryptocurrency isn’t as difficult as you may think. Every transaction from every account on the NEM blockchain is public. And what’s more important, the blockchain is immutable, so the attackers left a trail that they can’t erase. You can even try to follow the stolen money yourself by clicking through from address to address (scroll down to see the first transactions).
For the attackers, the only way to “launder” the stolen XEM was to send it to an exchange where it would be stored in a common wallet. Once the funds got there, it would be impossible to tell which of the stored currency was stolen.
The good news is that the NEM network has a solution to this problem: a tracking system that flags every account that receives stolen currency with a special mosaic. NEM’s mosaic is similar to a custom cryptocurrency, but it can have additional properties and meaning. For instance, a mosaic may be used for marking an account as a hacker. If a particular account has a balance of that specific mosaic, then it’s somehow related to the attack.
Following the attack on CoinCheck, all major exchanges were instructed by NEM to block transactions received from the flagged accounts. As a result of these measures, it became much more difficult for the attackers to get any profit out of the hack.
The bad news is that in March 2018, the system that was tracking stolen funds was disabled. So in the end, the hackers reached their target and got away unpunished.
Mitigating the attack
When such a hack takes place in a blockchain network, there’s one ultimate option for mitigating the impact of the attack: a hard fork.
A hard fork happens when the community doesn’t agree on the current state of the blockchain and reverts to a previous state. From there, a second blockchain is created, like an alternative history, and the past is rewritten. Figure 1 below shows a basic scheme of this process.
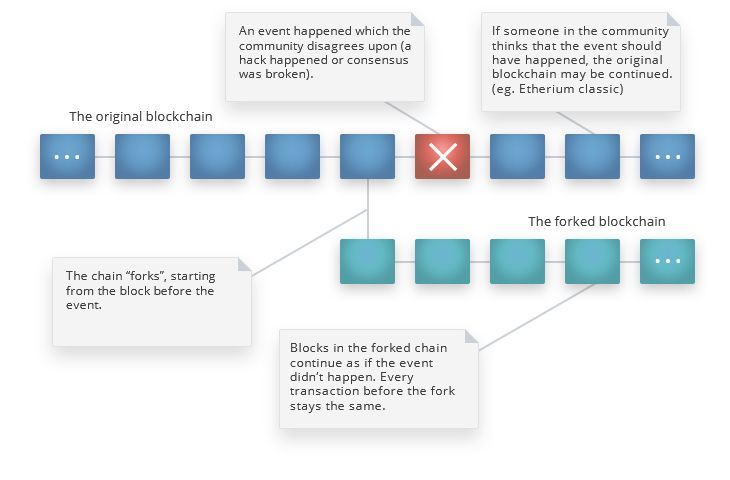
Figure 1. A hard fork scheme
One of the brightest examples of a hard fork is in the famous Ethereum blockchain. After the DAO hack in 2016, the Ethereum blockchain split into two separate blockchains: Ethereum (where the hack hasn’t happened) and Ethereum classic (where the hack has happened).
As for the NEM network, its officials stated that they had no intention to do a hard fork since the blockchain itself wasn’t compromised. CoinCheck, in turn, promised to return most of the stolen funds, and they delivered on that promise.
After all, the CoinCheck hack wasn’t as fatal as the previous largest hack. Thanks to NEM’s quick response and CoinCheck’s honest reparations, the markets recovered within a few weeks of the attack and most of the stolen funds were returned to victims.
What we can learn from the CoinCheck hack
The CoinCheck hack shows just how much the cryptocurrency markets have matured over the last few years. Today, these markets are much more stable than at the beginning of the cryptocurrency era. However, if we want that stability to keep growing, it’s important that every cryptocurrency exchange owner follows best practices and learns as much as possible from every mistake made by others.
In the case of CoinCheck, for instance, there are at least two important lessons for every exchange owner to learn:
- The majority of your passive funds must be stored in a well-protected cold wallet, and only a minor amount of currency should be kept in a hot wallet.
- You need to constantly monitor network activity around your wallets so you can detect any unauthorized transactions quickly.
As for personal accounts, just remember that it’s better not to store all your currency on an exchange unless you’re actively trading it. You need to understand that when you keep your funds on an exchange, you don’t actually own them. And unfortunately, not every exchange service can provide reparations in case of a hack like CoinCheck did. Therefore, make sure to keep your personal investments safe!
Conclusion
Now you have it – the CoinChack hack explained. Even though the recent CoinCheck hack was named the largest cryptocurrency heist so far, its consequences weren’t as devastating as they could have been. In fact, CoinCheck’s case showed the community that a quick and appropriate response can effectively mitigate the impact of nearly any attack, even the largest.
Another important lesson we can learn from the CoinCheck hack is that one strategic mistake can lead to devastating consequences in the future and that security should always be a high priority for both exchange services and regular cryptocurrency owners.
At Apriorit, we have a team of data encryption and cybersecurity professionals who are incredibly passionate about what they do. We make cybersecurity our number one priority and do our best to make sure that there isn’t a single flaw left for attackers. Get in touch with us by filling out the form below and learn how we can assist you in developing a secure solution using blockchain technology.




