The importance of reliable web security is hard to overstate. Vulnerabilities in web applications can open your business to devastating attacks. There’s a lot of information about web application penetration testing methodology and related tools available on the internet, but it can be hard to find solutions that will work well for your particular situation. In order to achieve a high level of operations security (OPSEC), it’s important to understand that ensuring security is a constant process that requires a holistic, systematic approach.
This article provides an overview of how to achieve reliable OPSEC and covers five of the most popular web application security testing methodologies. It also takes a look at prominent web security testing standards and guidelines.
Contents:
- Main stages of OPSEC
- 1. Open Source Security Testing Methodology Manual (OSSTMM)
- 2. Open Web Application Security Project (OWASP)
- 3. Web Application Security Consortium Threat Classification (WASC-TC)
- 4. Penetration Testing Execution Standard (PTES)
- 5. Information Systems Security Assessment Framework (ISSAF)
- Choosing a methodology and running tests
- Conclusion
Main stages of OPSEC
What is application security testing? It’s a complex and systematic process meant to check and analyze the security of a web application or platform. While there are lots of tools and products you can use for running quick tests, out-of-the-box solutions don’t account for individual use cases. Therefore, it isn’t enough just to use the most popular penetration testing tools as is to ensure the security of your web platform or application.
Maintaining a high level of OPSEC involves designing countermeasures based on web application security vulnerabilities your product faces. You can find an illustration of a regular OPSEC process in Figure 1 below.
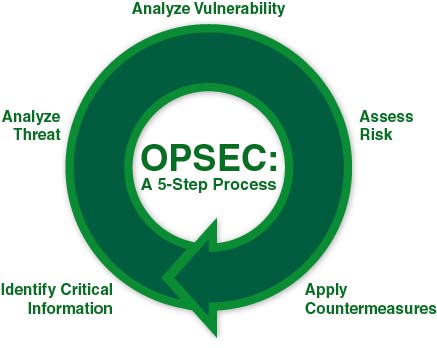
Figure 1. OPSEC: A 5-Step Process
Any risk assessment starts with identifying critical information. For an e-commerce website, this can be customer data such as credit card numbers, phone numbers, and addresses, or company-related information such as lists of suppliers, data on turnover or margins, or employee phone numbers.
The next step is creating a threat analysis and testing strategy. This step is the most important because we need to make sure that all important potential threats are covered.
The best way to create a threat analysis and testing strategy is to base your tests on well-known security assessment methodologies and standards. Doing so will help you choose the most effective testing strategy, taking into account the specifics of your web platform. Let’s get acquainted with five of the most popular types of security testing methodologies for web applications.
1. Open Source Security Testing Methodology Manual (OSSTMM)
The Open Source Security Testing Methodology Manual (OSSTMM) focuses on what to test instead of how to test it and contains web security testing basics as well as information about how to interpret the results of the tests.
From a technical perspective, OSSTMM is divided into four key groups:
- scope
- channel
- index
- vector
The last free version of the manual, OSSTMM V3, was published in 2010, and is partially outdated. The latest version is only available for paid members.
Benefits: The OSSTMM framework is adaptable to several types of tests, including vulnerability assessments, penetration tests, white box audits, and more.
Area of use: Any environment
2. Open Web Application Security Project (OWASP)
The Open Web Application Security Project (OWASP) is an open-source project that offers a wide array of free resources focused on web application testing and cybersecurity awareness.
OWASP offers several types of guides for assessing web application security:
- OWASP Top 10. This is the main OWASP publication that details the most frequently encountered security vulnerabilities in web applications according to business impact and technical complexity.
- OWASP Testing Guide. This guide contains a collection of best practices and practical security testing examples for testing web application security.
- OWASP Developer Guide. This guide contains recommendations on writing solid, safe, and secure code.
- OWASP Code Review Guide. This guide is meant for both software developers and managers; it describes best practices of secure code review and explains how it can be used within a secure software development life cycle (S-SDLC).
Benefits: OWASP guidelines provide all necessary information for every stage of the secure software development life cycle. It’s the most popular and complete collection of web application security best practices and testing tools that you can find online.
Area of use: Web applications, although there are several OWASP projects focused on mobile app testing.
Read also:
10 Best Low-Code Development Platforms
3. Web Application Security Consortium Threat Classification (WASC-TC)
The Web Application Security Consortium Threat Classification (WASC-TC) is a classification of website security threats. This document also contains descriptions and examples of attacks. Classifications are presented in several ways, called Views:
- Enumeration View – lists attacks and weaknesses that can compromise the security of a website and its data
- Development Phase View – tells at which stage of the development life cycle a particular vulnerability can occur
- Taxonomy Cross Reference View – helps map WASC-TC terminology to terminology used by other similar projects including OWASP Top Ten, CWE, and CAPEC
Benefits: WASC-TC shows traceability between development phases and threats across different classifications.
Area of use: Web applications
4. Penetration Testing Execution Standard (PTES)
The Penetration Testing Execution Standard (PTES) is an application penetration testing methodology that covers seven main stages from initial communication with a customer to reporting:
- Pre-engagement interactions
- Intelligence gathering
- Threat modeling
- Vulnerability analysis
- Exploitation
- Post exploitation
- Reporting
Detailed descriptions of each stage as well as mind maps detailing the steps required can be found on the PTES website.
Benefits: The main benefit of PTES is its technical guide, which contains detailed technical information on tools and commands for every stage of penetration testing. We highly recommend using this framework when you need full information about what to test and how to test it.
Area of use: Any environment
5. Information Systems Security Assessment Framework (ISSAF)
The Information Systems Security Assessment Framework (ISSAF) is separated into two parts: technical and managerial. The technical part provides a set of the most important rules and procedures for creating an adequate security assessment process. The managerial side contains general recommendations on setting up an effective testing process.
Benefits: ISSAF helps close the gap between the technical and managerial sides of security testing and implements necessary controls to efficiently handle both sides.
Area of use: Any environment
Choosing a methodology and running tests
The usefulness of each of the guidelines listed above will vary based on your particular situation. We recommend following OWASP security checklist for creating a testing strategy. For technical details, we suggest using the PTES Technical Guideline.
Once you’re done creating test documentation, it’s time to perform the actual testing and look at how your web application works rather than how you think it works.
As a result of this testing, you’ll get a list of issues that should be assessed for exploitability and impact. You can use the following classifications for your assessment.
Issue Impact
| Value | Description |
| Critical | An issue that poses an extreme threat; for instance, an issue that prevents a security control device from filtering traffic or allows an attacker to gain full administrative access to the system. |
| High | An issue that poses a significant security threat but has a limited scope; for instance, a DoS vulnerability in a critical service or the possibility to gain user-level access to the system. |
| Medium | An issue with limited impact; for instance, a significant information leak that allows limited access to the system or denial of service. |
| Low | An issue with small impact; for instance, a leak of information that may be useful to an attacker by providing software version details, lists of users, etc. |
Issue Exploitability
| Value | Description |
| Trivial | An attacker doesn’t need specific knowledge; the issue can be exploited with the help of standard operating system tools. |
| Easy | An attacker needs to have basic knowledge and use standard operating system tools or other tools downloaded from the internet. |
| Moderate | An attacker has to have some specific knowledge and use a combination of operating system tools and tools easily available on the internet. |
| Challenging | An attacker has to have specific knowledge and put a lot of effort into exploiting the issue, for instance by gaining physical access to network infrastructure or resources, using a combination of different attacks, etc. |
| N/A | An issue that is not directly exploitable. |
The next step is calculating risk. Find where the results from the Issue Impact and Issue Exploitability charts intersect to determine the risk value for each issue.
Risk level calculation
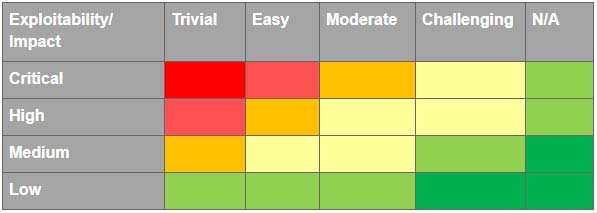
Fig 2. Risk level calculation
Based on the results of this risk calculation, you can prioritize all issues from low-priority vulnerabilities to high-priority. Then you can focus your remediation activities on the most important issues.
Conclusion
When it comes to ensuring the security of your business’s website, it’s best to use well-known web application testing methodologies and standards. The guidelines and resources covered in this article provide a comprehensive knowledge base that you should use to your advantage.
For the best results, choose and start using appropriate security testing techniques for web application or platform at the earliest stages of the development process. Need a team of experienced quality assurance specialists for penetration testing consulting and web application testing? Send us your request for proposal and we’ll get back to you. And if you want to learn more about typical web application security issues and solutions, check our latest tutorial here.



