Modern vehicles include many advanced technologies to provide better connectivity and a better user experience. As a result, the attack surface for vehicles has grown exponentially. Gartner’s 2025 Global Automotive Consumer Study revealed that more than half of surveyed consumers in the United States, the United Kingdom, and India remain concerned about the safety of autonomous technology in vehicles.
To earn customer trust, automotive companies must constantly update their cybersecurity strategies to ensure reliable protection of software systems. A crucial part of doing so is including penetration testing, or pentesting, in the project lifecycle.
Pentesting allows companies to simulate attacks, discover weak spots, and fix vulnerabilities before hackers exploit them. As a result, automotive businesses can deliver highly protected solutions, improving their reputations and competitiveness.
In this post, we discuss the main reasons to apply pentesting for vehicle software and what systems to use it for. You’ll also find key information about essential automotive pentesting phases, approaches, and tools. This article will be helpful for automotive software providers who care about their product security and are looking for ways to improve it with penetration testing.
Contents:
- Why use pentesting for automotive software?
- Target software systems for automotive penetration testing
- 1. Telematics and application servers
- 2. APIs
- 3. Infotainment systems
- 4. Mobile apps
- 5. CAN bus
- Automotive pentesting essentials: phases, approaches, and tools
- How Apriorit can help with your automotive software projects
- Conclusion
Why use pentesting for automotive software?
What is automotive pentesting?
Automotive penetration testing is dedicated to discovering security flaws in vehicles and their associated systems in order to defend against cyber attacks. The idea is to simulate real-world attacks to find vulnerabilities so that developers can fix discovered issues before they cause harm. You can request pentesting services for various systems, from infotainment products and telematics to communication modules and in-vehicle networks.
Is penetration testing mandatory for automotive software systems?
Pentesting is not mandated for all automotive software systems. However, some original equipment manufacturers (OEMs) require their Tier 1 suppliers to run pentesting as a part of their cybersecurity efforts.
Why apply penetration testing to automotive software?
Automotive penetration testing emulates an attack on automotive software in an attempt to find any vulnerabilities and assess the potential damage from an attack. Pentesting services can be provided by an in-house security testing team that knows the software well or by an outside team that can analyze the product from a new angle.
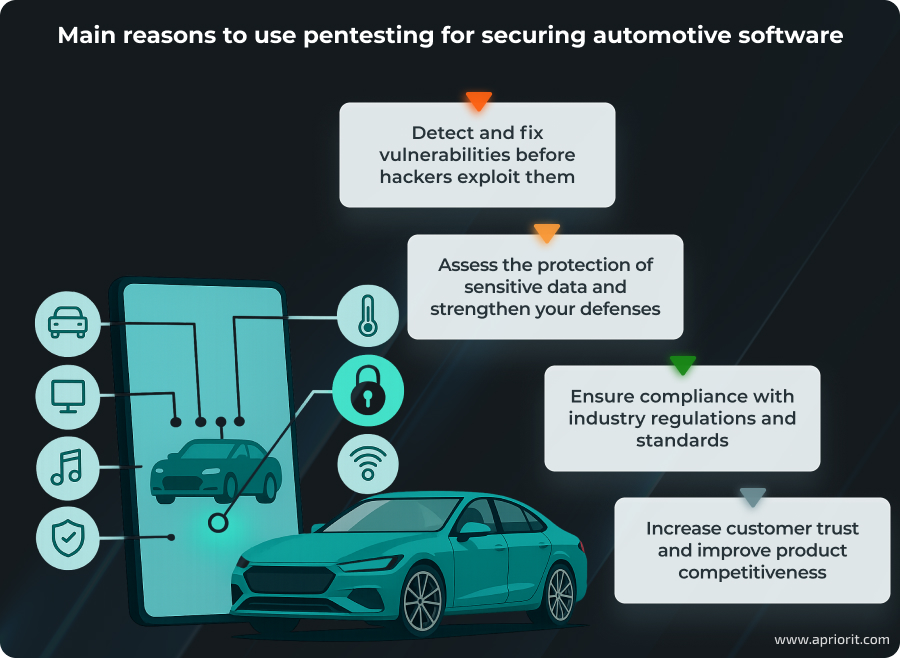
Conducting penetration testing can help your team:
- Detect vulnerabilities in vehicle systems and weak spots within the software that are prone to break under attacks, addressing issues proactively before hackers can exploit them
- Assess the protection of user data and other sensitive and confidential information that’s processed by software or stored in its components
- Check whether built-in protection measures work as intended or need to be updated by exploring how systems behave in different attack scenarios
- Take steps towards complying with industry regulations and standards such as ISO 26262, ISO/SAE 21434, and UNECE R155, as well as adhere to process assessment models like Automotive SPICE
- Ensure continuous improvement of the software security posture, as regular testing helps with adapting software to evolving threats and vulnerabilities
- Increase customer trust and product competitiveness by showing that software passes regular penetration checks, thereby validating its resilience
Once pentesting is over, your automotive software team will receive extensive reports with a detailed description of each identified issue, flaw, and vulnerability. With knowledge of your software’s weak spots, you can plan improvements, prioritizing issues to fix depending on their severity. As a result, you can deliver secure software, increase your product’s competitiveness, and strengthen your reputation as a reliable vendor.
Should you choose an in-house team or an outsourcing company for pentesting services?
If your company employs penetration specialists with the necessary skills and relevant experience, it could make sense to use internal resources. However, keep in mind that outsourcing vendors specializing in providing penetration testing services usually have broader expertise and act as independent parties.
Looking for professional penetration testing services?
Build reliable protection for your automotive software systems with Apriorit’s niche expertise in cybersecurity, pentesting, and reverse engineering.
Target software systems for automotive penetration testing
Where should you apply pentesting?
The simple answer is that you should apply pentesting to any vehicle software and embedded system, as nothing is 100% secure from vulnerabilities and attacks.
To adequately prioritize penetration testing in automotive software, make sure that your team monitors and analyzes evolving threats along with their impact on the cybersecurity posture. Thus, you’ll know which automotive systems are most vulnerable and pose the greatest threat.
Let’s take a look at some of the most targeted software automotive systems from our experience.
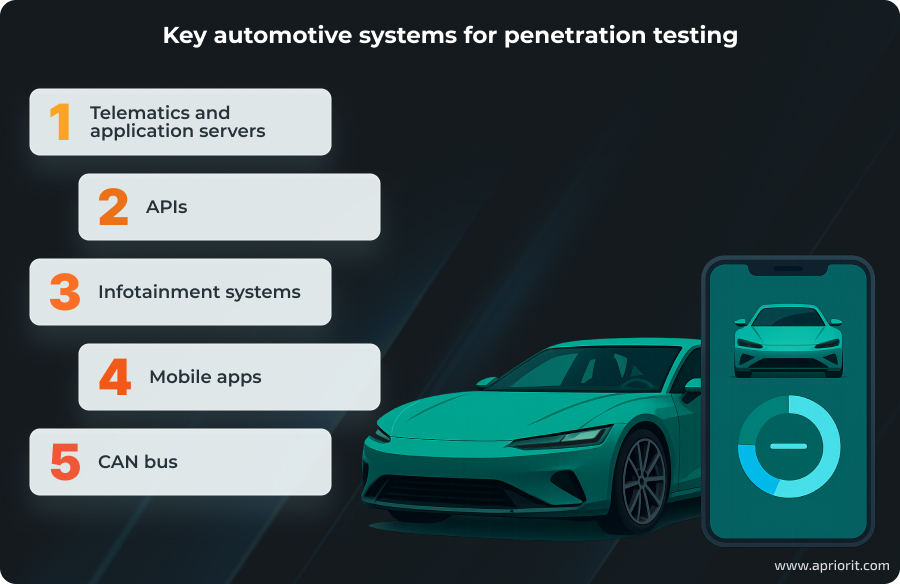
1. Telematics and application servers
To handle information from OEM backend servers and vehicle owners, connected vehicles use telematics and application servers. Some vehicles might also interact with backend servers that communicate with third parties like insurance and car rental companies.
If vulnerabilities exist in these servers or in the software systems that interact with them, criminals might find a way to exploit those vulnerabilities. As a result, they may be able to steal sensitive data, launch attacks against vehicles while they are on the road, or send inaccurate weather and navigational data.
Attacks on telematics and application servers have grown significantly, from 43% in 2023 to 66% in 2024 according to the 2025 Automotive & Smart Mobility Global Cybersecurity Report by Upstream [data from this report is also shared elsewhere in this post]. Oftentimes, sensitive data can be accessed due to vulnerabilities. For example, in September 2024, a member of a cybersecurity consultancy and assessment firm discovered a vulnerability in a third-party accident reporting application that revealed sensitive data to anyone typing a report number in the URL of a car rental company.
2. APIs
APIs are used in connected vehicles as well as in smart mobility devices and services. Both external and internal APIs are crucial in automotive systems as they interact with almost everything, connecting over-the-air (OTA) systems, telematics servers, mobile apps, EV charging management systems, infotainment systems, and more.
On the downside, APIs can be prone to attacks aiming to steal sensitive personally identifiable information (PII), manipulate backend systems, or take remote control of a vehicle. API hacking is considered a relatively cheaper and easier option for large-scale attacks, as it doesn’t require special hardware.
In 2024, API-related incidents accounted for 17% of total vehicle-related attacks. Here’s what such an attack can look like: In November 2024, a hacker exploited a REST API vulnerability to infiltrate Schneider Electric, a company specializing in several domains including automotive and e-mobility. The hacker managed to capture 400,000 data records, including 75,000 unique email addresses associated with the full names of Schneider Electric employees and customers.
Related project
Auditing the Security of a Connected Vehicle Communication System
Discover how Apriorit strengthened a vehicle communication platform’s defenses by identifying exploitable gaps and delivering targeted security improvements through a custom audit.
3. Infotainment systems
In-vehicle infotainment (IVI) systems are a must for modern cars, as they provide entertainment and information features that improve a vehicle’s competitiveness. Such systems include navigation, Bluetooth connectivity, media players, Wi-Fi hotspots, smartphone integration, and voice controls.
However, since infotainment systems usually connect to external devices, internet, and other networks, they are a promising entry point for cyber attacks. Malicious actors might try hacking IVI systems to access PII, intercept internal vehicle networks, or inject malicious software to penetrate internal systems.
In 2024, IVI-related attacks accounted for 14% of all vehicle-related cybersecurity incidents. In that same year, researchers discovered a vulnerability in all versions of Smartplay head units, which are widely used in Suzuki and Toyota cars. A misconfiguration could lead to leaking of sensitive details like diagnostic log traces, system logs, head unit passwords, and PII.
4. Mobile apps
Modern vehicles tend to connect with devices via mobile apps for a better user experience. OEMs often provide remote services and functionalities via vehicle companion apps and third-party apps. The use cases are numerous, from remote vehicle control to car monitoring, diagnostics, navigation, charging management for electric vehicles, and integration with smart home systems.
But an advanced digital experience comes with a price. Hackers can attack vehicle-related mobile apps, potentially gaining access to a vehicle itself, backend servers, and the vehicle owner’s personal information. Not to mention that third-party apps may have vulnerabilities that automotive companies can’t check themselves.
While attacks against vehicle-related mobile apps made up only 3% of all incidents in 2024, the consequences of such attacks may be rather unpleasant, as you never know when malicious actors will find and exploit vulnerabilities. In 2024, Toyota reported a security incident that resulted in the unauthorized disclosure of information about customers who used the MyToyota app. Per TMP’s investigation, the security incident involved human error and threatened the confidentiality of data of affected customers.
5. CAN bus
The controller area network (CAN) bus is a communication system that enables electronic control units (ECUs) in vehicles to communicate with each other without a host computer. The CAN bus facilitates real-time data exchange for functions like engine control, braking, and safety systems.
Unfortunately, CAN bus solutions are vulnerable to both physical and remote threats. For example, criminals might use message injection, eavesdropping, or spoofing attacks to disrupt vehicle operations and gain unauthorized control of critical systems.
Although only 2% of all vehicle-related attacks in 2024 targeted CAN bus systems, securing them is worth the effort. In 2022, cybersecurity researchers discovered that access to unified diagnostics services on the Škoda Superb III was transmitted via CAN bus in a form that could be easily decoded by attackers with physical access to the vehicle.
Read also
Automotive Software Development: Trends and Challenges
Stay ahead in the automotive software race. Discover key development trends and how to tackle emerging challenges in this competitive field.

Automotive pentesting essentials: phases, approaches, and tools
Though penetration testing activities vary depending on the system you need to check for vulnerabilities, the general workflow usually consists of three phases:
- Preparation. The main idea here is to evaluate potential entry points and attack vectors, considering both internal and external actors. Before simulating attacks, pentesting specialists must explore the product’s architecture, infrastructure, business logic, and features. Then, they have to accurately define the goal, scope, and targets for attack simulation. Once the testing methodology is finalized and agreed with the team, pentesters prepare for testing.
- Attack simulation. During attempts to breach a system — such as an in-vehicle network, a wireless interface like Bluetooth or Wi-Fi, or a communication channel like OTA updates — pentesters look for vulnerabilities and potential attack vectors. For example, a pentester could try to intercept and alter CAN bus messages to disrupt vehicle functions or gather sensitive data.
- Impact analysis. In the end, experts prepare a penetration testing report describing discovered weaknesses, potential ways of exploiting them, and the impact of vulnerabilities on the system, along with their risk levels.
Pro tip: Some professional pentesting service providers like Apriorit also provide actionable insights to strengthen your product protection and offer to create a continuous pentesting policy tailored to your system. Such services can help you build a mature security strategy with systemic vulnerability assessments to scan vehicle software, networks, and applications in order to detect security flaws early.
The contents of a penetration testing report differ significantly depending on your service provider. Here’s what we offer to Apriorit clients as a result of our pentesting services:

Three main pentesting approaches for automotive
When choosing a pentesting approach, it’s essential to consider the system type, software architecture, and security concerns for the target system.
1. In white-box testing, penetration testers have full knowledge of an automotive system. With access to documentation, pentesters can analyze source code, architecture, and components, along with connections between components. Thus, they can purposefully try to attack code in a certain place. For example, a car stereo (or infotainment) system may have a menu allowing the user to name a radio station. Testers may be aware that this feature does not have a limit on the number of input symbols, or that it lacks input sanitizing mechanisms. In such a case, penetration testers can search for ways to interrupt car stereo performance or even go beyond the car stereo system by exploiting a discovered vulnerability.
2. In black-box testing, specialists have no prior knowledge of a system’s architecture and code. Hence, they simulate attacks from an external threat actor, such as a hacker or rogue device. For example, a tester might attempt to gain unauthorized access to vehicle functions via Bluetooth or a connected mobile app, mimicking real-world attackers. Pentesters can apply methods like fuzzing (injecting malformed data into communication protocols to trigger unexpected behavior) and see how the system handles malformed inputs like CAN messages or wireless packets. Other techniques include vulnerability scanning, social engineering, brute forcing, and reverse engineering.
3. In grey-box testing, pentesters have partial knowledge of the system. For example, they might have network architecture or system documentation. This approach is often used for evaluating both internal and external threats. For example, a grey-box test might evaluate whether an infotainment system compromised via a USB device can be made to send malicious commands to other in-vehicle systems.
Key tools, frameworks, and platforms for automotive pentesting
The tech stack for each project should be carefully planned during the preparation stage. However, we can name a few of the most common and helpful automotive penetration testing tools from our experience:
- CANalyzer is analysis software primarily used by automotive and electronic control unit suppliers to analyze the data traffic in serial bus systems.
- Wireshark is an open-source packet analyzer for network troubleshooting and analysis, as well as for developing communications protocols and software.
- Metasploit is a pentesting framework that allows security specialists to write, test, and execute exploit code.
- Burp Suite is a platform for vulnerability scanning, penetration testing, and web app security that assesses web applications and APIs linked to vehicle systems.
- ChipWhisperer is an open-source tool for investigating side-channel attacks on embedded devices and validating their side-channel resistance.
- SavvyCAN is a GUI tool for capturing and reverse engineering CAN frames.
- Ghidra is a disassembler that allows pentesters to analyze extracted firmware and perform decompilation and patching.
- ImHex is a powerful open-source hex editor that helps with raw data and protocol research.
- SocketCAN userspace utilities and tools is a repository containing several helpful userspace utilities for the Linux CAN subsystem.
Related project
Streamlining Electric Vehicle Charging Support with an AI Chatbot
Explore how we delivered a smart chatbot integration for electric vehicle charging support, enhancing user interaction and reducing the human workload through intelligent automation.

How Apriorit can help with your automotive software projects
Our experienced specialists are ready to assist you with any task, from software development and quality assurance to strengthening cybersecurity defence and conducting thorough penetration testing.
Apriorit is committed to protecting the confidentiality, availability, and integrity of client data. As part of this commitment, we have successfully completed TISAX certification to meet strict information security standards tailored to the automotive industry.
Apart from that, we have obtained ISO 9001 (Quality Management System Requirements) and ISO 27001 (Information Security Management System Requirement) certifications. Operating under these internationally recognized standards allows our teams to ensure continuous product improvement, build transparent and effective processes, and achieve client satisfaction.
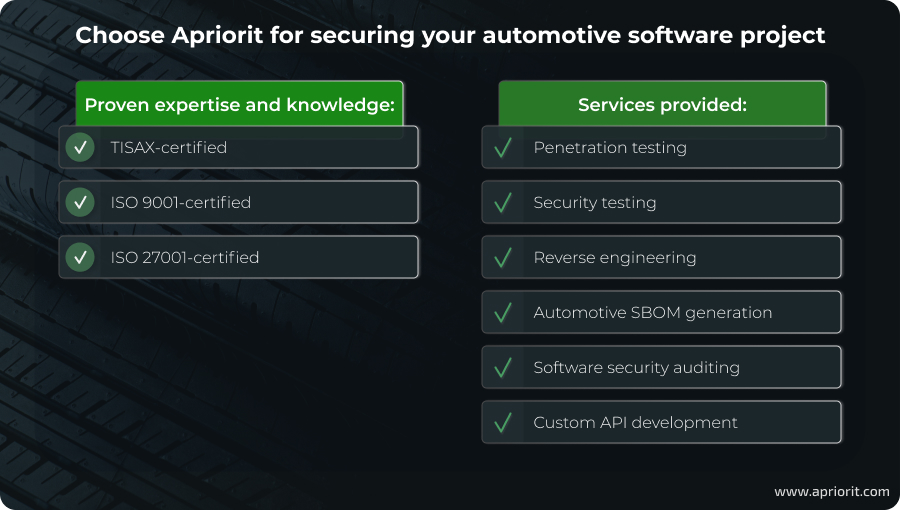
Whatever idea you have in mind, you can count on us to turn it into a real product. Apriorit has extensive expertise working on automotive software products as well as niche skills and service offerings:
- Proficient pentesting skills to find hidden flaws and vulnerabilities in different vehicle systems and related software, including Android applications.
- Professional cybersecurity testing services to help automotive companies prevent and mitigate attacks on vehicle software, as well as to comply with industry standards, regulations, and laws.
- Versatile reverse engineering services to uncover vulnerabilities in automotive software and hardware, understand discovered threats, and develop strong defenses.
- Rich experience auditing automotive software security, including systems for advanced vehicle communication. For many years, our security testing teams have been crafting a comprehensive internal security audit checklist, so we will make sure your project is safeguarded from threats.
- Expertise in generating automotive SBOMs to help our clients manage software components and mitigate cybersecurity risks.
- Competence in API development and security for complex interconnected systems. Our experts will help you protect your APIs against security issues from the start of development.
Conclusion
Penetration testing for automotive software systems is crucial, as it helps you detect critical vulnerabilities in order to prevent painful incidents and ensure advanced protection. Moreover, pentesting also helps automotive businesses move closer to UNECE R155 and ISO/SAE 21434 compliance.
To make the most out of pentesting, it’s essential to accurately prioritize which systems require the most attention and what pentesting approaches and tools to use. Last but not least, it’s important to choose a trusted and experienced vendor.
Apriorit has vast experience in penetration testing, as well as experience with a wide range of automotive and embedded projects. Our specialists are ready to perform penetration testing for your project and help you integrate relevant pentesting activities into your software development lifecycle to effectively remediate vulnerabilities.
Leave no chance for attackers by catching vulnerabilities!
Let Apriorit’s penetration testing specialists, cybersecurity professionals, and reverse engineering gurus assess your automotive systems and provide actionable insights for enhanced security.



