Key takeaways:
- Non-compliance with HIPAA rules can result in fines of up to $2,134,831 per year.
- When building healthcare software, developers must overcome different challenges, from securely integrating AI to providing compliance across diverse mobile and IoT devices.
- The latest update to the HIPAA Security Rule proposes a significant review of the cybersecurity requirements for HIPAA-regulated entities.
- To deliver HIPAA-compliant software, it’s essential to partner with a reliable vendor that has expertise in developing healthcare solutions under HIPAA.
Cyber threats in healthcare are on the rise, and data breaches are affecting more patients than ever. This makes strong security measures essential for any medical software. In the US, the Health Insurance Portability and Accountability Act (HIPAA) outlines administrative, physical, and technical safeguards to protect sensitive health information.
Whether you’re building new healthcare software or modernizing an existing solution, what does it take to make it HIPAA-compliant?
In this article, you’ll find a checklist of security safeguards to verify HIPAA compliance of healthcare software, challenges that may arise during the development of medical solutions, and insights on how to build HIPAA-compliant software.
This article will be useful for healthcare software product owners and development leads who are planning to build a HIPAA-compliant solution or looking for ways to check whether their existing solution is HIPAA-compliant.
Contents:
- HIPAA overview: 5 rules that govern protected health information
- Who must comply with HIPAA?
- Penalties for violating HIPAA requirements
- Challenges of developing HIPAA-compliant software
- Checklist to verify HIPAA compliance of software
- What to consider when developing HIPAA-compliant software
- How Apriorit can help you build a HIPAA-compliant solution
- Conclusion
HIPAA overview: 5 rules that govern protected health information
HIPAA is a US federal law designed to protect health information and enhance the efficiency of the healthcare system. HIPAA consists of five rules that govern the security, handling, transmission, storage, auditing, and disclosure of protected health information (PHI), including in electronic formats (electronic protected health information, or EPHI).
1. Privacy Rule
The Privacy Rule regulates the use and disclosure of PHI by covered entities and sets standards for the rights of individuals to understand and control how their health information is used.
For example, when building or auditing software that processes, stores, or transmits PHI, under the Privacy Rule, such software must ensure access controls, user authentication, and logging to prevent unauthorized disclosure.
2. Security Rule
The Security Rule is a set of security standards to protect health information maintained or transmitted electronically (EPHI). This Rule outlines the administrative, physical, and technical safeguards that covered entities and business associates must implement to protect EPHI.
A major goal of the Security Rule is to ensure EPHI security, allowing regulated entities to adopt new technologies that improve the quality and efficiency of healthcare.
On December 27, 2024, the U.S. Department of Health and Human Services (HHS) issued a Security Rule Notice of Proposed Rulemaking (NPRM) to improve cybersecurity in light of the growing number of cyber attacks. The proposed modifications to the Security Rule would require HIPAA-compliant organizations to strengthen cybersecurity protections for EPHI.
3. Breach Notification Rule
The HIPAA Breach Notification Rule requires covered entities and their business associates to notify of any breach of unsecured PHI. A breach is defined as the impermissible use or disclosure of PHI under the HIPAA Privacy Rule that compromises the security or privacy of PHI.
In case of a breach, notification must be sent to affected individuals, to the Secretary of HHS, and, in certain circumstances, to the media. In addition, business associates must notify covered entities if a breach occurs on their end.
4. Enforcement Rule
The Enforcement Rule establishes procedures to investigate HIPAA violations and impose penalties on covered entities and business associates for non-compliance with HIPAA Rules.
5. Omnibus Rule
The Omnibus Rule implements provisions of the Health Information Technology for Economic and Clinical Health (HITECH) Act to strengthen the privacy and security protections for health information established under HIPAA. Among the key provisions are:
- Making business associates of covered entities directly liable for HIPAA compliance
- Strengthening limitations on use and disclosure of PHI
- Expanding individuals’ rights to restrict disclosures of PHI
- Expanding individuals’ rights to request copies of their PHI
- Adopting a four-tier civil monetary penalty structure for HIPAA violations
With these HIPAA basics in mind, let’s define the types of organizations that are obliged to comply with this act.
Want to align your healthcare products with HIPAA requirements?
Apriorit experts will help you build a customized solution in compliance with HIPAA requirements.
Who must comply with HIPAA?
There are two major categories of organizations that have to be HIPAA-compliant:
1. Covered entities
Covered entities include:
- Healthcare providers — Organizations that provide medical services, including clinics, hospitals, pharmacies, labs, and psychiatric facilities
- Healthcare plans — Insurance and health maintenance companies, government and private medical programs
- Healthcare clearinghouses — Organizations that aren’t involved in healthcare services but work with PHI or EPHI, such as aggregators and hubs for transmitting medical data
2. Business associates
Business associates are vendors or contractors that process PHI/EPHI on behalf of covered entities. To ensure that business associates protect PHI/EPHI in compliance with HIPAA, they should sign a Business Associate Agreement (BAA).
All IT solutions developed for an organization from the list above must comply with HIPAA requirements to secure EPHI.
Non-compliance with the demands of this act may lead to data disclosures and severe punishment for both the organization and individuals responsible for an incident. That’s why it’s paramount to follow principles of HIPAA compliance for software development when designing healthcare solutions and to verify compliance before a product is released.
Let’s take a closer look at possible penalties for breaking HIPAA rules.
Penalties for violating HIPAA requirements
For non-compliance with HIPAA requirements, the Department of Health and Human Services’ Office for Civil Rights (OCR) can impose fines depending on the level of culpability, ranging from $141 per violation to $2,134,831 per year.
Moreover, if the OCR believes there are grounds for a possible criminal conviction, such cases may be referred to the Department of Justice, which can pursue criminal charges for HIPAA violations.
HIPAA penalties, which are annually adjusted, are divided into four categories (tiers). When determining a penalty, OCR considers such factors as:
- Duration of the violation
- Number of people affected
- Nature of the data exposed
- Willingness to assist with the OCR investigation
Factors also include prior history, the entity’s financial condition, and the level of harm caused by the violation.
Let’s see the current penalty structure:
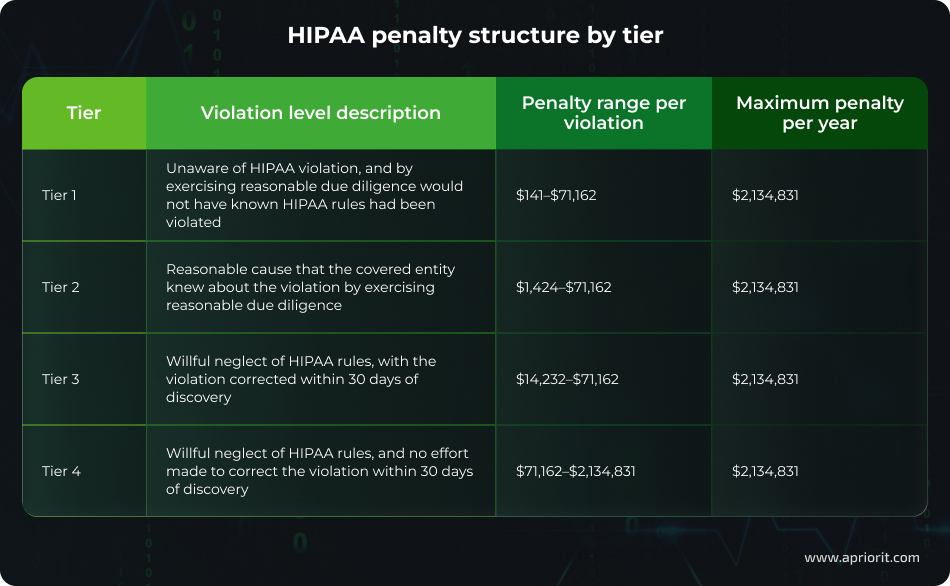
As you can see, HIPAA violations can result in severe financial and reputational damage. To avoid these risks, organizations must ensure full compliance. However, achieving this is far from simple. Let’s explore the key challenges of implementing HIPAA-compliant software.
Challenges of developing HIPAA-compliant software
Here are the key challenges developers encounter when creating a HIPAA-compliant application or system:

- Too much data to protect and manage. Before implementing any sort of data protection, developers have to get a clear understanding of the amount, nature, and layout of sensitive information. In healthcare organizations, evaluating such data is particularly complex, as it’s stored in numerous locations: electronic health record (EHR) systems, data centers, physical storage locations, mobile devices, supply chains, vendor environments, etc.
- Lack of resources and knowledge. Creating and deploying a HIPAA-compliant solution involves lawyers, cybersecurity experts, medical experts, and DevOps engineers. All of them need to contribute deep knowledge and lots of time to the project; otherwise, the solution won’t cover all the requirements. Budget cuts and acceleration of product development often result in insecure and non-compliant software.
- Managing security across multiple platforms. All platforms used in a healthcare organization have to be protected with the same security measures. Modern hospital infrastructure includes real and virtual user endpoints, servers, data centers, mobile devices, cloud resources, and more. An IT team needs knowledge of and experience with mobile device management architecture design and development for all of these platforms to secure sensitive data.
- Sacrificing security for compliance. While implementing HIPAA requirements surely improves software cybersecurity, it isn’t a silver bullet. Some development teams check the boxes and think they can skip a risk assessment. However, such an approach leads to data breaches and penalties. To protect a software product, developers must critically evaluate potential threats and risks and implement as many security measures as possible.
- Lack of flexibility and scalability. Systems developed with many security requirements in mind are usually quite rigid. At the same time, healthcare organizations need flexible software to be able to adapt to changes. During the design stage, developers have to take into account software scalability and flexibility to meet needs that may arise in the future.
- Need to regularly reassess security measures. Work on a healthcare system doesn’t stop when it’s deployed. HIPAA requirements, cybersecurity threats, and an organization’s IT environment are all constantly changing. To make sure your software remains HIPAA-compliant, developers have to conduct regular audits, carry out risk assessments, and update documentation and security policies.
- Insufficient ransomware protection. Ransomware attacks in healthcare can endanger patients’ health and lives, so HIPAA-compliant medical software needs strong built-in security. Proactive security measures against ransomware include regular data backups and system updates, strong access control (such as multi-factor authentication, or MFA), and network segmentation.
- Risk of software supply chain attacks. Such attacks occur when actors exploit vulnerabilities in third-party vendors, software providers, or service partners (e.g., EHR systems, billing firms, medical device manufacturers) to indirectly compromise patient data. To prevent or mitigate the risks of such attacks and stay compliant under HIPAA, it’s important to conduct supply chain security audits, implement third-party risk management, continuously monitor the supply chain for vulnerabilities, and require vendors to follow secure SDLC principles.
- Difficulties establishing proper cloud infrastructure. When healthcare entities adopt cloud solutions, it leads to the emergence of new cloud-specific challenges that developers must consider when creating HIPAA-compliant software. These challenges include unintentionally storing EPHI in non-compliant regions when setting up multi-cloud infrastructure, managing excessive permissions and orphaned workloads, handling data encryption complexities in advanced cloud setups, misconfiguration of cloud environments, and fragmented logging.
- Absence of compliance across mobile and IoT devices. Extensive use of mobile and IoT solutions in healthcare increases the cyber attack surface. This adds new challenges for developers such as device heterogeneity — not all platforms support HIPAA safeguards — and a lack of built-in security capabilities. Developers also need to address such problems as poor authentication and access control across devices, devices connecting to unknown networks, no support of audit logging, and increased security risks in case of device loss.
- Insecure integration of AI and ML. When integrating AI and ML to streamline various healthcare activities and enhance patient outcomes, developers must consider technology-specific risks to ensure EPHI safety. Among the issues developers must resolve are data minimization and access control, end-to-end security of AI pipelines, handling unstructured medical data and data de-identification, and preventing the risk of sensitive data leakage.
- Complexities of securing telemedicine services. To provide remote HIPAA-compliant services, it’s essential to ensure secure, encrypted video conferencing that prevents EPHI leakage through screen recording and screenshots. It’s also important to use HIPAA-compliant platforms, provide strong identity verification, and enable secure storage and encryption of medical records.
- Need for protected data interoperability and sharing. Each connection between systems may be a potential vulnerability for data breaches or unauthorized access. To mitigate this challenge and to be HIPAA-compliant, developers can implement interoperability standards like FHIR or HL7 that secure data exchange across different EHR systems.
At Apriorit, we’ve developed dozens of HIPAA-compliant solutions for healthcare, tackled many challenges, and accumulated unique experience on this subject. To speed up the verification of all required IT measures, we’ve created a HIPAA compliance checklist for software development that you can use when implementing and testing your healthcare solution.
Read also
Cybersecurity Risks in Healthcare Software: Key Threats and How to Address Them
Discover proactive strategies to enhance your medical solution.

Checklist to verify HIPAA compliance of software
Administrative, physical, and technical safeguards for IT systems and EPHI protection are laid out in the HIPAA Security Rule. The latest update to the HIPAA Security Rule to Strengthen Cybersecurity of Electronic Protected Health Information was proposed on January 6, 2025.*
This update would represent a significant revision of the cybersecurity requirements for HIPAA-regulated entities, aimed at improving protection against internal and external threats.
One of the important changes would be the removal of addressable implementation specifications from the HIPAA Security Rule. All specifications would be required, although there are limited exceptions for certain implementation specifications.
To verify that your solution or security system meets HIPAA requirements, taking into account the proposed changes to the Security Rule, you can use this HIPAA compliance checklist prepared by Apriorit’s experts:
* Note: As of the date of publication, these changes are still under review and are not yet enforced.
Table 1. HIPAA compliance checklist based on proposed changes to the Security Rule
| Requirement | Type | Desired outcome |
|---|---|---|
| Access control §164.312(a), Title 45 of the CFR | Required | – All technology assets have a unique identifier – Access controls are implemented to restrict users to only the information required for their job duties – Procedures exist for getting necessary EPHI during an emergency – Technical controls are deployed to terminate the electronic session in case of inactivity – Technical controls are deployed to disable or suspend the user’s / technology asset’s access to an electronic information system in case of unsuccessful access attempts – Technical controls are deployed to segment an electronic information system |
| Encryption and decryption §164.312(b), Title 45 of the CFR | Required | – Technical controls are configured and implemented for encrypting all EPHI in compliance with industry-standard cryptography – All EPHI is encrypted, at rest and in transit |
| Configuration management §164.312(c), Title 45 of the CFR | Required | – Technical assets/controls are deployed to protect technology assets in an electronic information system against malware – Extraneous software is removed from electronic information systems – Operating systems and software are configured and secured, and network ports are disabled according to results of risk analysis |
| Audit trail and system log controls §164.312(d), Title 45 of the CFR | Required | – Technical assets/controls are deployed for real-time monitoring and recording of all activity, including for detecting unauthorized activity in an electronic information system – Technical assets/controls are deployed to retain records of all activity in an electronic information system |
| Integrity §164.312(e), Title 45 of the CFR | Required | – Technical controls are deployed to protect EPHI from improper alteration or destruction at rest and in transit |
| Authentication §164.312(f), Title 45 of the CFR | Required | – Technical controls are deployed that require users to set unique passwords – MFA is deployed to all technology assets in an electronic information system |
| Transmission security §164.312(g), Title 45 of the CFR | Required | – Technical controls are deployed against unauthorized access to EPHI in transmission |
| Vulnerability management §164.312(h), Title 45 of the CFR | Required | – Automated scanning is performed to detect vulnerabilities in an electronic information system and all its components – Regular monitoring for known vulnerabilities is conducted, and measures are taken in response to identified vulnerabilities – Penetration testing for vulnerabilities in an electronic information system is periodically performed – Technical controls to promptly install software patches and critical updates are configured and implemented |
| Data backup and recovery §164.312(i), Title 45 of the CFR | Required | – EPHI copies are created no later than 48 hours after EPHI is stored in an electronic information system – Technical controls are deployed that monitor and alert in real time about any failures and errors of backups, including controls that record backup status |
| Information systems backup and recovery §164.312(j), Title 45 of the CFR | Required | – Technical controls are deployed to create and maintain backups of an electronic information system |
Note: All listed controls must be reviewed and tested at least annually or after significant environmental or operational changes.
The listed safeguards cover technical controls for EPHI protection. To be fully HIPAA-compliant, you must also meet administrative and physical requirements.
Building HIPAA-compliant healthcare software requires thorough planning. Let’s explore the main things you need to include in your plan before proceeding to development.
Read also
Healthcare Software Modernization: Overcoming Challenges, Delivering Results
Explore best practices that allow you to transform your systems smoothly and improve operations for long-term success.

What to consider when developing HIPAA-compliant software
To develop HIPAA-compliant healthcare solutions, it’s obligatory to implement all administrative, physical, and technical safeguards listed and described in HIPAA’s Security Rule.
Administrative safeguards are actions and policies designed to manage the selection, development, implementation, and maintenance of security measures that protect EPHI. Physical safeguards provide physical measures to protect a covered entity’s or business associate’s electronic information systems, and technical safeguards involve technical controls governing the use of the technology that protects and controls access to EPHI.
Here, we explore the six main things to consider when planning HIPAA-compliant healthcare software development:
1. Conduct a HIPAA compliance risk assessment
Identify and document where and how EPHI is collected, stored, processed, or transmitted, including APIs, databases, and backups. Then, analyze potential security threats and vulnerabilities by preparing detailed data flow diagrams that consider HIPAA requirements.
2. Design architecture with HIPAA principles in mind
Designing a HIPAA-compliant architecture involves considering and implementing security safeguards that enable robust protection of EPHI throughout the system. Such safeguards include:
- Implementing strict access controls through defining user roles and access levels according to HIPAA requirements
- Integrating MFA into your solution
- Encrypting data at rest and in transit
- Separating sensitive data from other data
- Integrating with clouds that offer HIPAA-compliant services and signing a Business Associate Agreement (BAA) with cloud providers
- Designing reliable backup and disaster recovery plans to guarantee EPHI availability during emergencies
This list of safeguards is not exhaustive and needs to be tailored to the specific characteristics of your solution.
It’s best to consider HIPAA requirements at the design stage of software development. This way, you can create a solution with top-notch security in mind.
Stanislav, Security Testing Team Software Developer
3. Implement logging and monitoring
Logging and monitoring play a crucial role in ensuring HIPAA compliance, as they enable the tracking and auditing of all interactions with EPHI. As a result, they help you detect unusual patterns or potential data breaches in a timely manner and respond promptly.
4. Develop breach notification workflows
To comply with HIPAA’s Breach Notification Rule, you need to develop plans and workflows for detecting, reporting, and managing data breaches. When developing workflows, consider:
- How to notify individuals impacted by a data breach, HHS, and media in a timely manner
- Content of notifications
- How to deliver notifications
- Responsibilities of business associates to notify covered entities of a breach
- Procedure for maintaining documentation on breach notification
5. Test software for HIPAA compliance
Testing for HIPAA compliance aims to check that your solution meets all HIPAA rules and ensures the confidentiality, integrity, and availability of EPHI. Testing strategies include:
- Security and penetration testing to identify and mitigate system weaknesses, ensuring robust defenses against potential breaches
- Privacy and access control testing to verify that only authorized individuals can view or handle EPHI (evaluates how data is accessed, shared, and protected in your solution or system)
- Backup and recovery testing to check disaster recovery plans and data restoration processes to maintain the availability and integrity of EPHI
- Automated scanning for vulnerabilities and compliance risks
6. Maintain documentation and continuously monitor
For audit purposes, it’s crucial to document all risk assessments, policies, safeguards, and the security architecture to demonstrate the solution’s HIPAA compliance. Moreover, to maintain HIPAA compliance within the SDLC, you can implement continuous monitoring, vulnerability scanning, and software updates.
To ensure that your software is HIPAA-compliant, it’s essential to partner with a vendor that has relevant expertise in developing and testing healthcare solutions. Let’s explore how Apriorit professionals can assist you.
Related project
Developing a GDPR-Compliant AI-Powered LMS for Pharma Employee Training
Explore how Apriorit experts enhanced the client’s LMS system by integrating an AI-assisted LMS.

How Apriorit can help you build a HIPAA-compliant solution
With 20+ years of experience in cybersecurity, Apriorit offers full-cycle healthcare software development services that adhere to universal and industry-specific compliance requirements at every stage of the SDLC. To further enhance data protection and the solution’s overall security, the Apriorit team follows secure SDLC principles. Among the services we offer are:
- Developing customized healthcare software. We can help you build software that fully aligns with your vision and the requirements of your healthcare area.
- Enhancing cybersecurity protection for software. With vast experience creating cybersecurity solutions of any complexity, we implement innovative best security practices, taking into account the specifics of the industry.
- Testing software for HIPAA compliance. Apriorit QA specialists have experience assessing software products for HIPAA compliance and verifying solutions against the latest changes in HIPAA rules. Our experts apply different testing strategies depending on the solution specifics and conduct diverse types of testing, from comprehensive testing to security testing and penetration testing.
- Auditing healthcare software for HIPAA compliance. Say that you already have a healthcare solution or system and you need to verify whether it fully complies with recent HIPAA demands. Apriorit professionals are ready to perform a full audit of your software and provide a detailed report on discrepancies and ways to fix them to be HIPAA-compliant.
Moreover, we offer flexible cooperation models: dedicated team, time and materials, and fixed price.
Conclusion
Building secure and reliable medical software is more challenging than it may seem. It requires implementing and regularly reviewing advanced security safeguards to resist and withstand evolving cybersecurity threats. Moreover, you must stay compliant with industry requirements, including the latest guidelines on strengthening software security postures.
At Apriorit, we have extensive experience developing and testing HIPAA-compliant solutions. Our professional engineers will help you build secure software that meets your business expectations and adheres to the latest legal and regulatory requirements.
Looking for a reliable vendor for developing healthcare software?
Partner with Apriorit to get software that fully aligns with the latest HIPAA requirements.
FAQ
What types of organizations and software systems must comply with HIPAA?
Organizations regulated under HIPAA are covered entities (including healthcare providers, healthcare plans, and healthcare clearinghouses) and business associates, which are vendors that manage PHI/EPHI on behalf of covered entities. Software systems that handle EPHI also must comply with HIPAA.
Who is this HIPAA compliance checklist for?
The checklist prepared by Apriorit experts is for developers who build healthcare software that uses or stores EPHI and for QA specialists who verify the adherence of such solutions to the latest HIPAA requirements.
What is considered protected health information (PHI), and when does HIPAA apply to software handling PHI?
<p>Protected health information (PHI) under HIPAA is any information that can identify an individual and relates to their health status, medical history, treatment, or payment for healthcare.</p>
<p>HIPAA applies to software systems that create, receive, maintain, or transmit PHI electronically (referred to as EPHI). HIPAA requires the implementation of strict administrative, physical, and technical safeguards to protect this data.</p>
What is the difference between a covered entity and a business associate under HIPAA?
<p>A covered entity is a healthcare provider, health plan, or healthcare clearinghouse that directly handles PHI in providing healthcare services, payment, or operations.</p>
<p>A business associate is a person or organization that performs certain functions or activities on behalf of a covered entity that involve creating, receiving, maintaining, or transmitting PHI.</p>
Does simply using a “HIPAA-compliant” software solution guarantee my organization is HIPAA-compliant in healthcare?
Using a “HIPAA-compliant” software solution alone does not guarantee that your organization is fully HIPAA-compliant. Compliance is a comprehensive process that involves not only using secure, certified software but also implementing appropriate administrative, physical, and technical safeguards across the entire organization. This includes risk assessments, access controls, policies, procedures, breach response plans, and ongoing monitoring.
What are the primary HIPAA rules relevant to software?
The core HIPAA rules that directly impact software design, development, deployment, and maintenance are:
<ul class=apriorit-list-markers-green>
<li>Privacy Rule — governs how PHI may be used and disclosed, and the rights of individuals over their health information</li>
<li>Security Rule — governs how EPHI must be protected through administrative, physical, and technical safeguards</li>
<li>Breach Notification Rule — describes what must happen if there is a breach of unsecured PHI/EPHI</li>
<li>Enforcement Rule — regulates investigations, penalties, and procedures when breaches or violations occur</li>
<li>Omnibus Rule — serves to strengthen privacy and security protections, expanding the responsibilities of business associates</li>
</ul>



