Internet of Things (IoT) systems help your customers automate various aspects of their business operations and daily lives. However, since IoT devices share and process lots of data, safeguarding that data becomes rather challenging. To secure sensitive data and maintain customer trust, you need to protect not only your devices but also the network through which data is shared.
In this article, we explore the key security challenges in the Internet of Things and the attack vectors in this field. We also discuss best practices for securing devices, data, and networks within your IoT environments. This article will be helpful for development teams and business owners who want to ensure the proper security of their IoT projects.
Contents:
IoT landscape: components and use cases
Before we dive into the specifics of security, let’s go over some essentials of IoT.
The Internet of Things is a network of smart devices that connect to each other in order to exchange data via the internet without any human intervention.
The architecture of IoT systems usually consists of wireless networks, cloud databases for communication, sensors, data processing programs, and smart devices that interact closely with each other. IoT systems use the following components to exchange and process data:
- Smart devices that collect, store, and share data about the environment and other devices and components. Smart devices range from simple sensors to DNA analysis hardware, depending on the IoT system’s goals.
- Embedded systems used by smart devices that include various processors, sensors, and communication hardware. The main goal of these systems is to collect, send, and act on data they acquire from environments.
- IoT gateways, hubs, or other edge devices that route data between IoT devices and the cloud.
- Cloud or on-premises data centers with remote servers that exchange data through wireless connections.
Organizations deliver IoT solutions for various industries, including healthcare, agriculture, logistics, home automation, retail, and manufacturing.
Such wide application of IoT systems means that many organizations are ready to rely on the Internet of Things technology to improve their business processes. This, in turn, requires IoT development companies to pay special attention to system security to efficiently secure customer data. Let’s explore what IoT security is and how to approach it.
Ready to take your business to the next level with IoT?
Entrust the development of your embedded and IoT solution to Apriorit’s team of experts to receive reliable and secure software!
What is IoT security?
Internet of Things security is a set of approaches and practices towards protecting physical devices, networks, processes, and technologies that comprise an IoT environment from a broad spectrum of attacks. Establishing IoT security helps prevent data breaches, mitigate threats, and keep systems working as expected.
To maintain IoT security, organizations might use different processes, including:
- Monitoring the work of existing security measures within the system environment
- Identifying and mitigating potential IoT security risks across devices
- Fixing any compromised connections that may be found
Which protection strategy you should choose will depend on your project’s goals and requirements. But in general, you can approach IoT security from three directions:
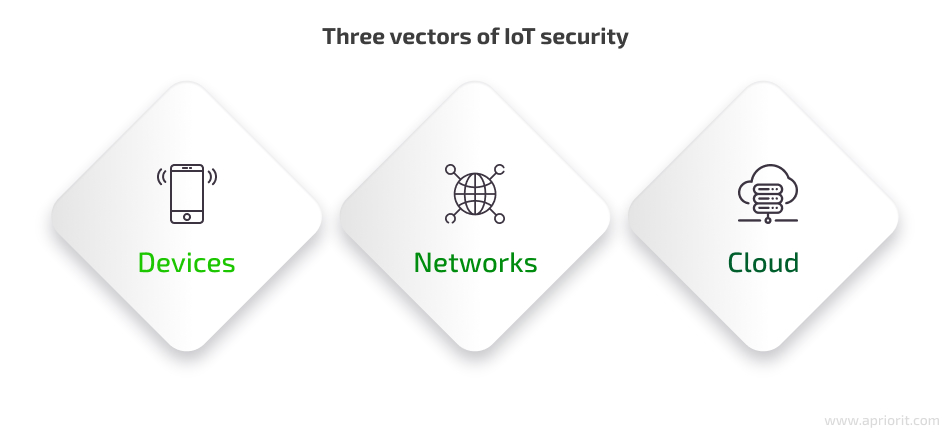
- Device protection is the first layer where your team can start defending your system from cyberattacks by applying different security measures. Essential measures include boot procedures, continuous firmware updates (especially vulnerability patching), and the introduction of secure communication protocols like TLS/SSL.
- Network security is essential to prevent interceptions during data transfer and to minimize the chance of hackers gaining access to the entire network. Security measures for this layer include firewalls, VPNs, intrusion prevention systems (IPS), and DDoS security measures.
- Cloud security has to be strong and continuously maintained and updated to protect data storage and access controls. Your team should implement reliable encryption and authentication methods.
You can also look at IoT security thought the CIA triad:
- Confidentiality. Only authorized people or devices can access sensitive information. This is especially important for IoT devices that operate in sensitive settings like hospitals or homes.
- Integrity. The entire life cycle of an IoT device needs to maintain the consistency, accuracy, and trustworthiness of data.
- Availability. IoT services and applications need to be consistently available to authorized people or devices.
Taking care of IoT security is quite challenging, as many IoT devices have outdated, poor, or even no built-in security measures. The reason for this is that some manufacturers focus on features and usability rather than security. Let’s dive into the main reasons why your team should put extra effort into securing your IoT product.
Why is IoT security important?
Since it is the nature of IoT systems to connect multiple devices and applications, an IoT system itself is only as strong as its weakest link. If one device is compromised, the entire environment is in danger.
The latest State of IoT report by IoT Analytics shows that the $236 billion IoT market is still on the rise. According to the KPMG global tech report 2023, 42% of technology professionals said in 2023 that edge computing, including IoT, would be most important in helping their business achieve its short-term ambitions. Since this technology isn’t going anywhere, it’s imperative to make IoT systems as secure as possible.
Here are the main reasons why taking IoT security seriously is crucial for your business:
- Data protection. Data leaks and breaches can result in legal liabilities and financial losses.
- Continuity of business operations. IoT security issues can disrupt system operations, resulting in service downtime.
- Reputation and trust. A security breach can damage a company’s reputation and decrease clients’ trust.
Let’s take a closer look at legal requirements regarding the security of IoT devices.
How is IoT security guaranteed in the legal field?
Smart devices gather tons of sensitive data, including personally identifiable information, which must be protected according to various cybersecurity laws, standards, and regulations. The compromise of sensitive information can result in lawsuits and fines. It can also lead to reputational damage and the loss of customer trust.
Governments also care about security and privacy in IoT, so there are several laws and regulations related to privacy, security, and consumer rights that you should take into account when you create an IoT system. They provide rules, checklists, and recommendations for implementing safe IoT services.
- In 2017, the US passed a law prohibiting any IoT device sold in the United States from using default passwords. This and other requirements were introduced in the IoT Cybersecurity Improvement Act.
- In 2018, California approved an IoT security bill SB-327 on information privacy, which contains a list of requirements for all IoT devices sold within the state.
- If your target market is the EU, you should pay attention to the GDPR and the privacy by design concept. Though not IoT-specific, privacy by design protects user data and establishes rules by which manufacturers and developers should ensure IoT device security.
- The Cyber Resilience Act, approved by the European Parliament in 2024, also regulates connected devices.
- Various industry-specific and international standards, such as ISO/IEC 27001 for information security management and the NIST Cybersecurity Framework, provide guidelines and best practices for securing IoT devices and networks. However, developing secure IoT systems and keeping them protected from attacks is not an easy task.
Apriorit cybersecurity specialists know how to develop compliant IoT projects and have already put in place several practices for strengthening IoT security. But before we dive deep into the practical part, let’s see why IoT security needs to be held to the highest standards.
Read also
Discovering and Mitigating Security Vulnerabilities in Routers: A Practical Guide
Does your IoT project include working with routers? If it does, make sure your team secures them properly. Read the full article to find out key attack vectors against routers and best practices for protecting them.
5 most common IoT security challenges
In the first six months of 2023, IoT attacks increased globally, resulting in a total of 77.9 million attacks compared to 57 million attacks in the first six months of 2022. The 2024 IoT Device Security report by Asimily highlights that routers are the most targeted IoT devices, accounting for 75% of all IoT-related attacks.
To understand how to secure IoT systems, it’s essential to explore potential cybersecurity risks first. Here’s Apriorit’s breakdown of the most common security challenges with the Internet of Things:
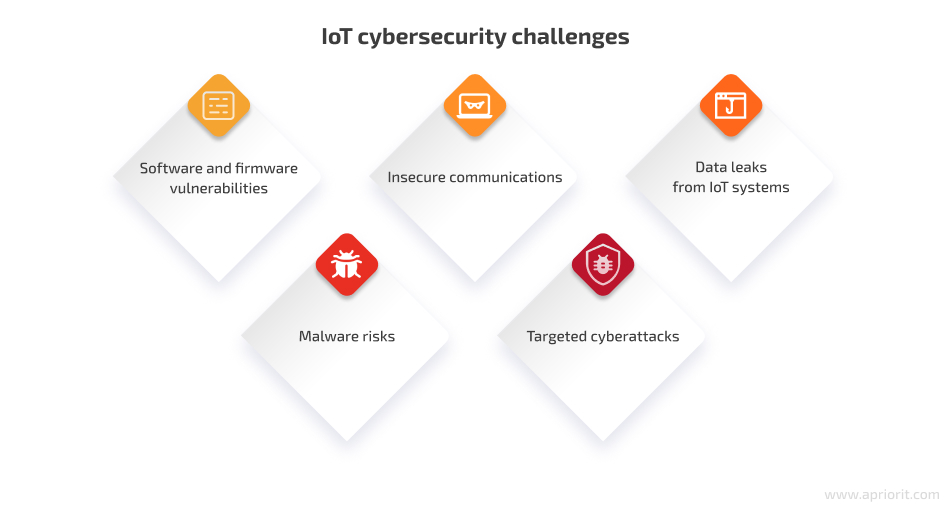
1. Software and firmware vulnerabilities
IoT systems often face many security concerns because of a lack of computing resources for security functions. As a result, IoT devices are likely to have more vulnerabilities than their non-IoT counterparts. These vulnerabilities can come from bugs in code as well as from insecure system settings, known as misconfigurations.
These IoT security vulnerabilities emerge for the following reasons:
- Lack of computational capacity for efficient built-in security
- Weak access control in IoT systems
- Limited budget for proper testing and improving firmware security
- Infrequent patches and updates
- User neglect in updating devices, thus restricting vulnerability patching
- Unavailability of software updates for older devices over time
- Poor protection from physical attacks, such as during factory assembly
Malicious actors aim to leverage vulnerabilities they’ve found in a target IoT system to compromise its communications, install malware, and steal valuable data.
One of the most famous hacks of recent years caused by misconfiguration of employees’ privileges is the Verkada hack. This cloud-based surveillance service was hacked in March 2021 when attackers gained unauthorized access to sensitive data belonging to Verkada’s software clients. They also managed to access live feeds from more than 150,000 cameras in factories, hospitals, schools, prisons, and other locations. Shockingly, the intruders used legitimate admin account credentials that they had discovered on the internet. Later, it was discovered that over 100 employees held super admin privileges, granting them access to a multitude of customer cameras. This shows the risks that are connected to granting excessive privileges to users within the company.
2. Insecure communications
Most existing security mechanisms were initially designed for desktop computers and are difficult to implement on resource-constrained IoT devices. That’s why traditional security measures aren’t as efficient when it comes to protecting the communication of IoT devices.
One of the most dangerous threats caused by insecure communications is the possibility of a man-in-the-middle (MitM) attack. Hackers can compromise an update procedure and take control of your device if it doesn’t use secure encryption and authentication mechanisms. Attackers can even install malware or change a device’s functionality. Even if not directly impacted by a MitM attack, IoT devices can inadvertently expose data during communication, making it susceptible to interception by hackers.
There are other threats connected to insecure communications:
- Eavesdropping. If the connection isn’t secure enough, attackers can eavesdrop on data exchanged between IoT devices and systems, revealing sensitive information.
- Replay attacks. Attackers might intercept and store communications between IoT devices and then replay them later to manipulate systems or gain unauthorized access.
- Data tampering. Insecure channels can allow attackers to alter transmitted information.
- Resource exhaustion. Inadequate security in communications allows hackers to flood devices with malicious traffic. As a result, systems can become unresponsive or malfunction.
Connected devices are susceptible to attacks from other devices. For instance, if attackers gain access to just one device in a home network, they can easily compromise all other unisolated devices in it. For example, in 2018, hackers used a vulnerability in an IoT thermostat for a fish tank to gain access to a casino’s Wi-Fi network and steal millions of dollars by accessing customer data and credit card information.
Read also
Using Rust for IoT Development: Everything You Need to Know to Start a Project
Find out how Rust enables safer firmware and IoT software development while maintaining low-level control and predictable performance.

3. Data leaks from IoT systems
We’ve already established that by capturing unencrypted messages from your IoT system, hackers can get access to sensitive data. This might include data like users’ locations, bank account details, and health records. However, abusing poorly secured communications isn’t the only way attackers can gather valuable data.
All data is transferred via and stored in the cloud, and cloud-hosted services can also experience external attacks. Thus, data leaks are possible from both the devices themselves and the cloud environments they’re connected to.
Third-party services in your IoT systems are another possible source of data leaks. For instance, Ring, a subcontractor for the Electronic Frontier Foundation, was found to be sending customer data from their smart doorbells to companies, including Facebook and Google, without proper customer consent. This incident happened because of third-party tracking services enabled in the Ring mobile app. As a result, clients of the Electronic Frontier Foundation became the victims of a classic data leak.
4. Malware risks
Most common IoT devices that can be hacked by a malware attack are smart home appliances, security cameras, and medical devices. One of the riskiest IoT devices is an IP camera because it’s always exposed to the internet and often protected by a weak password.
If attackers find a way to inject malware into an IoT system, they may compromise its functionality, collect personal data, and launch other attacks. Moreover, some devices may even come infected with malware out of the box if manufacturers don’t prioritize adequate software security.
Some organizations have already found ways to deal with the most famous IoT-targeted malware. For instance, an FBI agent shared how the agency stopped the Mirai botnet attacks, and Microsoft has released a guide on how to proactively defend your systems against the Mozi IoT botnet.
However, hackers keep inventing new ways to abuse IoT networks and devices. For example, in 2022, a new IoT RapperBot malware was discovered that targets Linux servers via SSH brute-forcing.
5. Targeted cyberattacks
Apart from the malware and MITM attacks discussed above, there are many other cyberattacks that IoT systems can be susceptible to. Here’s a list of the most common types of attacks on IoT devices:
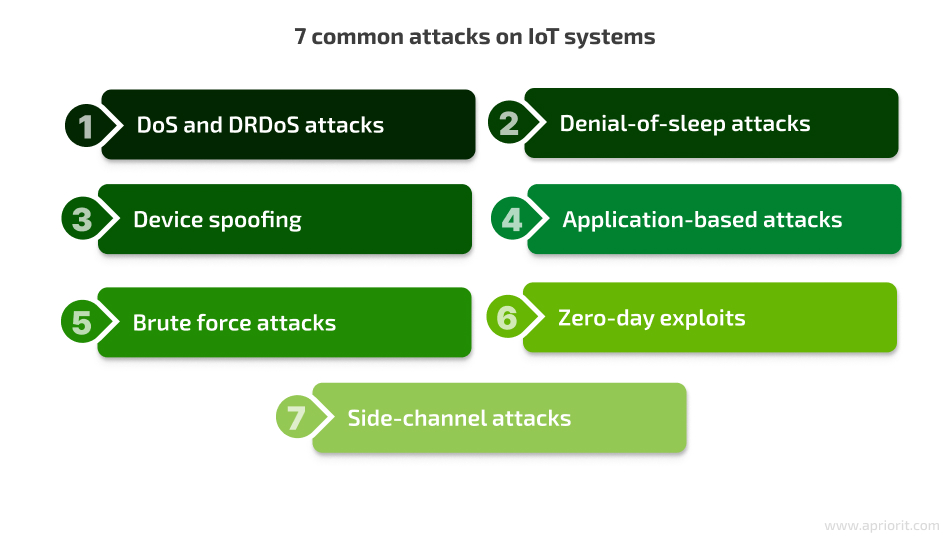
- Denial-of-service (DoS) and distributed reflection denial-of-service (DRDoS) attacks. IoT devices have limited processing power, which makes them highly vulnerable to denial-of-service attacks. During a DoS attack, a device’s ability to respond to legitimate requests is compromised due to a flood of fake traffic. DRDoS is an amplified version of a DDoS attack that uses vulnerable IoT devices as reflectors. Attackers take advantage of the ways multiple servers reflect and amplify packers back to the source.
- Denial-of-sleep (DoSL) attacks. Sensors connected to a wireless network should continuously monitor the environment. Some IoT sensors are powered by batteries and use sleep mode to preserve their charge. Sleep and awake modes are controlled according to the communication needs of different protocols, such as medium access control (MAC). Attackers may exploit vulnerabilities in the MAC protocol to carry out a DoSL attack. This type of attack drains battery power and thus disables the sensor.
- Device spoofing. This attack is possible when a device has improperly implemented digital signatures and encryption. For instance, a poor public key infrastructure (PKI) may be exploited by hackers to “spoof” a network device and disrupt IoT deployments.
- Application-based attacks. These types of attacks are possible when there are security vulnerabilities in device firmware or software or weaknesses in cloud servers or backend applications.
- Brute force attacks. Attackers may attempt to gain access to IoT devices by systematically trying all possible username and password combinations until they find the correct one.
- Zero-day exploits. These attacks target vulnerabilities that are not yet known to the device manufacturer and the security community, making zero-day attacks particularly dangerous.
- Side-channel attacks. In this case, criminals might use side-channel techniques to gather data from IoT devices, like monitoring power consumption or electromagnetic radiation to extract cryptographic keys.
IoT attacks can be launched even at the international level. For example, BlackTech (a Chinese APT) has been caught hacking into network edge devices of U.S. and Japanese multinational companies, using firmware implants to stay hidden and silently hop around corporate networks.
With these challenges in mind, let’s proceed to Internet of Things security best practices that can help you protect your IoT system.
Related project
Developing Software for a Drone Battery Charging and Data Management Unit
Check out the details of delivering automatic drone battery charging systems for aerial photography. Find out how Apriorit’s expertise helped our client better manage the charging process and upload data to the cloud.

IoT security best practices
Knowing how to secure your systems and continuously checking and improving protection can help you avoid cyber attacks. For example, in 2023, WAGO, a networking solutions company, managed to detect and fix vulnerabilities before attackers could exploit them by using an emulated device.
By leveraging IoT security best practices, you increase the protection of three main components of IoT systems: devices, networks, and data. The main advice for security is to know all the ins and outs of your infrastructure — including all devices and servers — and monitor their statuses. Here are the best practices for maximizing the security of your IoT systems:
Now, we will take a closer look at each of these practices.
1. Secure your smart devices
Smart devices can range from simple sensors to DNA analysis hardware depending on a particular IoT system’s goals. Let’s see how you can boost the security of your smart devices.
- Identify each device. You should be able to quickly identify the device that causes IoT security issues, so put unique identifiers on each device to learn what data a device sends and how it works.
- Ensure tamper-resistant hardware. IoT devices may be stolen by attackers in order to tamper with them or access sensitive data. To secure device data, it’s necessary to make your product tamper-proof. You can ensure physical security by using port locks or camera covers as well as by applying strong boot-level passwords or implementing approaches that will disable the product in case of tampering.
- Provide patches and updates. Ongoing device maintenance entails additional costs. However, proper product security can be ensured only with constant updates and patches. It’s best to establish automatic and mandatory security updates that require no actions from end users. Inform consumers about the timespan during which you’ll support the product and tell users what they should do after the end of this period. Once your system is released, make sure to keep an eye on upcoming vulnerabilities and develop updates accordingly.
- Run thorough testing. Penetration testing is your main tool for finding vulnerabilities in IoT firmware and software and reducing the attack surface as much as possible. You can use static code analysis to find the most obvious flaws and use dynamic testing to dig up well-hidden vulnerabilities.
- Implement device data protections. IoT devices should ensure the security of data both during and after exploitation. Make sure that cryptographic keys are stored in nonvolatile device memory. Additionally, you can offer to dispose of used products or provide a way to discard them without exposing sensitive data.
- Meet component performance requirements. IoT device hardware has to meet certain performance requirements in order to ensure proper usability. For example, IoT hardware should use little power but offer high processing capabilities. Moreover, devices must ensure robust authorization, data encryption, and wireless connections. It’s also preferable for your IoT solution to work even if its connection to the internet is temporarily disrupted.
Read also
Connecting IoT Devices with Mesh Networking: Pros, Cons, and Existing Solutions
Interested in learning more about IoT devices and how to implement them in your system? Explore IoT connectivity opportunities with mesh networking: pros, cons, and currently available solutions. Read the full article to find out the main innovations in this field!
2. Improve network security
It’s a bit harder to implement network security for IoT devices than for other types of hardware because devices use many different protocols and don’t have clear standards. Here are some ways your development team can ensure IoT network security.
- Ensure strong authentication. This can be achieved using unique default credentials. When naming or addressing your products, use the latest protocols to ensure their functionality for a long time. If possible, provide your product with multi-factor authentication. Even if you sell devices with default credentials for convenience, make sure the user immediately sets their own strong password. Back this up with two-step authentication or biometrics for better protection.
- Enable encryption and secure communication protocols. Communication between devices also requires security protection. However, cryptographic algorithms should be adapted to the limited capacities of IoT devices. For these purposes, you can apply Transport Layer Security or Lightweight Cryptography. An IoT architecture allows you to use wireless or wired technologies such as RFID, Bluetooth, cellular, ZigBee, Z-Wave, Thread, and Ethernet. Moreover, you can ensure network security with optimized protocols such as IPsec and Secure Sockets Layer.
- Minimize device bandwidth. Limit network traffic to the amount necessary for the functioning of the IoT device. If possible, program the device to limit hardware and kernel-level bandwidth and reveal suspicious traffic. This will protect your product from possible DoS attacks. The product should also be programmed to reboot and clear code in case malware is detected, as malware can be used to hijack the device and use it as part of a botnet to perform distributed denial of service attacks.
- Divide networks into segments. Divide a large network into segments and restrict access to each segment so that a data breach in a small part of the network won’t affect your whole system. Implement next-generation firewall security by separating big networks into several smaller ones. For this purpose, use ranges of IP addresses or VLANs. For secure internet connections, implement a VPN in your IoT system. Each segment should be responsible for all activity that happens inside it, detect any anomalies, and immediately report them.
- Think about your API safety. An API can become an entry point into your system for hackers, so be sure to regularly check the security of your APIs. It’s essential that only authorized devices can connect to your back end through an API so data sent from devices to servers can’t be manipulated.
3. Ensure data security
When it comes to IoT systems, ensuring IoT data security means guaranteeing the integrity, confidentiality, and availability of data across all IoT environments. Let’s see how you can achieve that.
- Protect sensitive information. Use unique default passwords for each product or require immediate password updates on the first use of a device. Apply robust authentication to ensure that only valid users have access to data. To go the extra mile for better privacy protection, you can also implement a reset mechanism to allow the deletion of sensitive data and the clearing of configuration settings if a user decides to return or resell the product.
- Collect only necessary data. Ensure that your IoT product collects only data necessary for its operation. This will reduce the risk of data leakage, protect consumers’ privacy, and eliminate risks of non-compliance with various data protection regulations, standards, and laws.
- Secure network communications. For better security, restrict your product’s unnecessary communication within the IoT network. Don’t rely entirely on the network firewall, and ensure secure communication by making your product invisible via inbound connections by default. Moreover, use encryption methods optimized to the needs of IoT systems, such as the Advanced Encryption Standard, Triple DES, RSA, and Digital Signature Algorithm.
- Use digital certificates. Digital certificates help with identifying public encryption keys, exchanging data securely, and setting up identity verification. Public key identification or PKI-based certificates protect device-to-device and device-to-server data transmission. To make your certificates effective, pair them with security protocols.
Apart from the practices mentioned above, make sure to follow recommendations like the updated NIST guide on IoT device cybersecurity, offering guidance to federal organizations in including IoT devices in their systems.
Related project
Developing a Custom Secrets Management Desktop Application for Secure Password Sharing and Storage
Unveil the details of creating secrets management software for the internal use of a US-based cybersecurity company. Discover how Apriorit developers helped our client improve their overall security score by 30%.

4. Check your firmware security
It’s always a good idea to secure not only software, data, and networks in your IoT projects but also IoT device firmware. It’s best to mitigate IoT security concerns and protect your devices at four levels:
- Provide secure code at compile time by obfuscating it, using safe stack and memory operations, validating variable initialization, and wiping data traces.
- Protect the solution during runtime by checking binary code and data integrity and detecting debuggers, monitoring software, and any other intrusive activities.
- Ensure firmware integrity with encryption (and partial decryption at runtime on demand), digital signatures for binary code, hardware identification, and regular security updates.
- Conduct software security testing that includes penetration testing, critical code fuzzing, and source code security audits.
If you want to create a secure IoT system, make sure your software developers follow the best practices of end-to-end IoT security.
5. Analyze your IoT security
Security analytics uses telemetry data from IoT devices to analyze and detect anomalies in an IoT ecosystem. Security analytics for IoT is more complex than any other system because of the data volume and two-way data flow. To implement analytics, you’ll need to deploy massively parallel processing (MMP) to process large amounts of data in real time.
MMP allows you to detect anomalies in real time. You can also set up rules, for example, to have the system automatically shut down if it detects a threat or to block all access to untouched components of your infrastructure. You can also use AI and machine learning to derive valuable conclusions from all the data you collect.
Here are some specific tasks that you can solve with the help of IoT security analysis:
- Detect anomalous behavior. Anomalies can include unusual traffic spikes or unexpected changes in device configurations. This can help to identify devices that may have been compromised by malware or other attacks.
- Identify security vulnerabilities. This includes identifying known vulnerabilities in firmware and software as well as identifying new and emerging vulnerabilities in IoT devices and networks.
- Investigate security incidents. By doing this in real time, you can understand the scope of an attack and take steps to mitigate the damage.
- Prevent future attacks. IoT security analytics can be used to learn from past attacks and to develop new security strategies to prevent future attacks.
The most popular analytics tools commonly used for IoT security include Splunk for IoT, IBM QRadar, and Senrio.
Conclusion
The field of IoT shows great promise, as it transforms industries and daily life through innovation and connectivity. However, ensuring robust cybersecurity of devices, networks, and data in IoT environments is challenging because of frequent cyberattacks and the complexity of searching for potential system vulnerabilities. Apart from running up against hardware limitations, implementing security features may increase resource expenditures and development time.
Developing secure IoT products requires the skills of expert IoT software developers and quality assurance specialists with experience in penetration testing. At Apriorit, we’ve gathered teams of professionals in embedded and IoT solutions development that can create a custom IoT system of any complexity. Thanks to our engineering for cybersecurity projects and security testing expertise, we can guarantee the best and the most secure result for your business.
Ready to leverage the power of IoT for a more connected future?
Let’s start working on a reliable and advanced project together! Leverage Apriorit’s 20+ years of cybersecurity experience to deliver a protected solution.




