More than 2.5 quintillion bytes of data are created and uploaded to the internet each day. A lot of that data is confidential: personal information, bank transfers, documents, credentials. It’s important to securely transmit such data between network endpoints.
TCP/IP is the most widespread data transfer protocol because of its high compatibility. However, TCP/IP vulnerabilities are well known to hackers. The TCP protocol uses open channels for data transfer, and an attacker can abuse this to access, listen to, and modify traffic.
There are many types of attacks — varying in their patterns, goals, and dispositions — that cybercriminals can use to intercept data in transit. Here, we’d like to discuss how to protect a network against a man-in-the-middle (MITM) attack.
In this article, we simulate such an attack on an unprotected network. We use a computer with two network interface cards to intercept traffic and use Wireshark to analyze that traffic. We also discuss if encryption is an effective method of protecting data from MITM attacks.
Contents:
What is an MITM attack?
MITM is a type of attack where a hacker secretly reroutes traffic and changes the connection parameters between endpoints that don’t know they are compromised. Such an attack is hard to detect because it doesn’t affect a network directly.
We’ve already discussed what a man-in-the-middle attack is in another article. Now let’s take a look at the typical scenario for an MITM attack:
- There’s a network with several machines that exchange data.
- An attacker wants to intercept data or even change data sent by one of those machines over the network.
The attacker acts as an intermediary between the targeted machine and the network, intercepting traffic between them.
There are many forms of MITM attacks. One of the most widespread is ARP spoofing, which is based on an Address Resolution Protocol (ARP) vulnerability: this protocol doesn’t confirm the authenticity of ARP requests and responses. ARP spoofing is common because computer network interfaces allow gratuitous ARP.
Now let’s simulate a passive MITM attack in order to see if we can intercept traffic and obtain data from a target.
Configuring an MITM attack
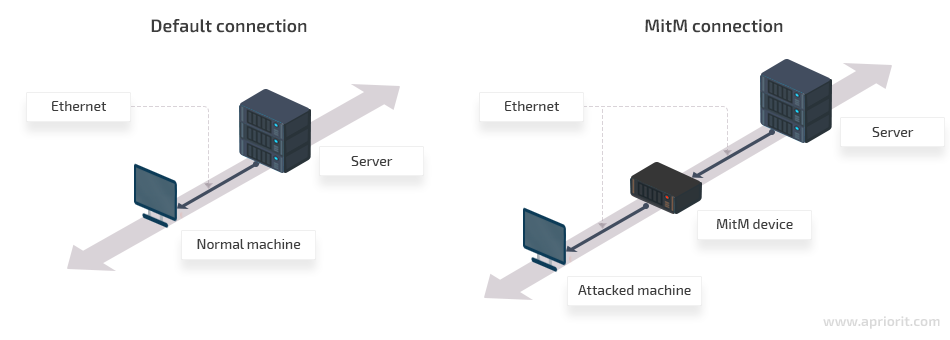
For our MITM attack example, we’ll create a simple network with two computers that exchange data and place an MITM device between them. We’ll use a computer with two network interface cards as the MITM device. Our network looks like this:
Here’s how we can turn a standard Windows computer into an MITM device:
- Place the MITM device between the device whose data you want to intercept and the rest of the network. In our example, we’ll connect the first computer to one of the Ethernet ports of the MITM device and plug the second computer into the second Ethernet port on that same device.
- Bridge these Ethernet connections on the MITM device. You can do this with default Windows tools. Just go to Settings — Ethernet — Network and Sharing Center — Change adapter options.
Creating an MITM device — step 1.
Creating an MITM device — step 2.
- Choose the network interfaces with the connections you want to bridge, right-click them, and choose Bridge Connections.
Creating an MITM device — step 3.
Once the bridge is created, our man-in-the-middle attack is ready to work. The targeted computer will connect to the network with no alert about traffic being intercepted, scanned, or changed.
Now we can intercept traffic from our target. Let’s see if we can restore data sent from it.
Analyzing network traffic with Wireshark
There are a lot of tools for analyzing traffic:
- Wireshark
- tcpdump
- Kismet
- Cain & Abel
- And more
In our case, we’ll use Wireshark. It’s one of the most popular protocol analyzers and has robust network diagnostic functionality. Wireshark works with various types of network protocols, as it’s equipped with a powerful filter system and a user-friendly interface. In addition, Wireshark intercepts streaming video and images, works with SIP, RTCP, SRTP, and other voice protocols, and saves voice traffic.
In its monitoring mode, Wireshark allows you to dump all traffic into one file and analyze or decipher it by applying different filters.
In order to start working with Wireshark, we have to choose the interface whose traffic we would like to intercept.

Let’s choose the interface connected to the first computer and analyze incoming data. After we run a sniffer, we can input the targeted computer’s IP address and TCP packet type:
ip.host==10.100.5.149 && tcp
Now we can listen to traffic coming from the first computer.
In order to simulate an MITM attack, we generated a secret file on the first computer. Now let’s send this unencrypted file to the second computer via the unprotected channel.
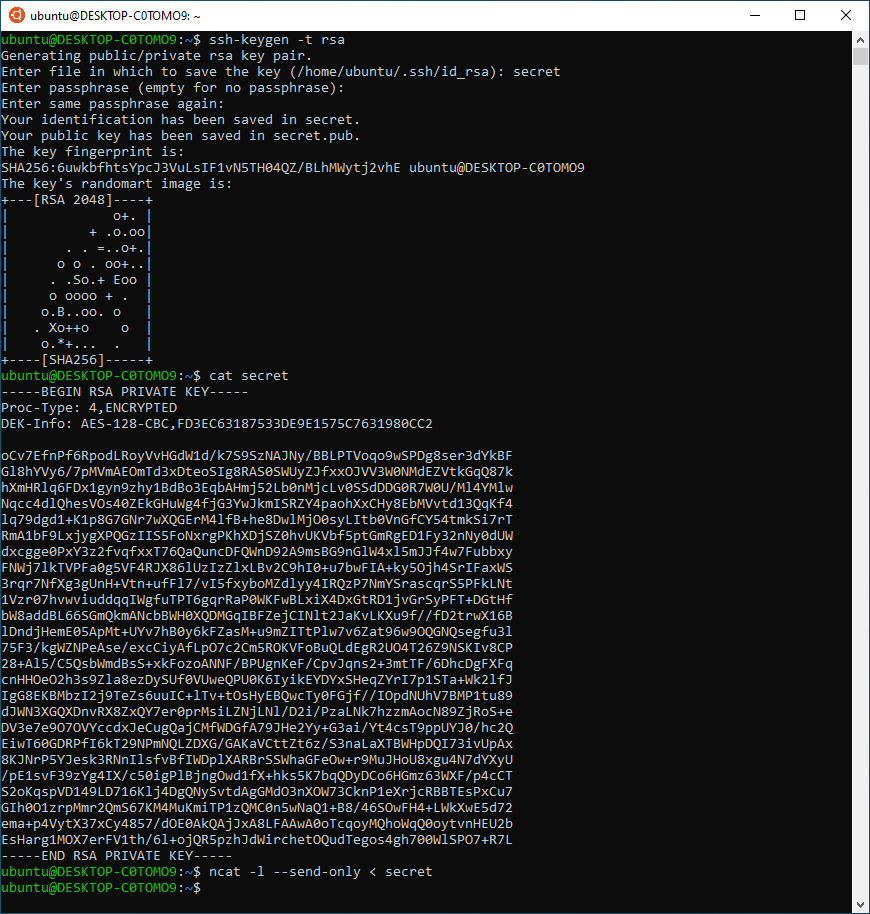
We successfully received this file on the second computer, and now we can take a look at its data.
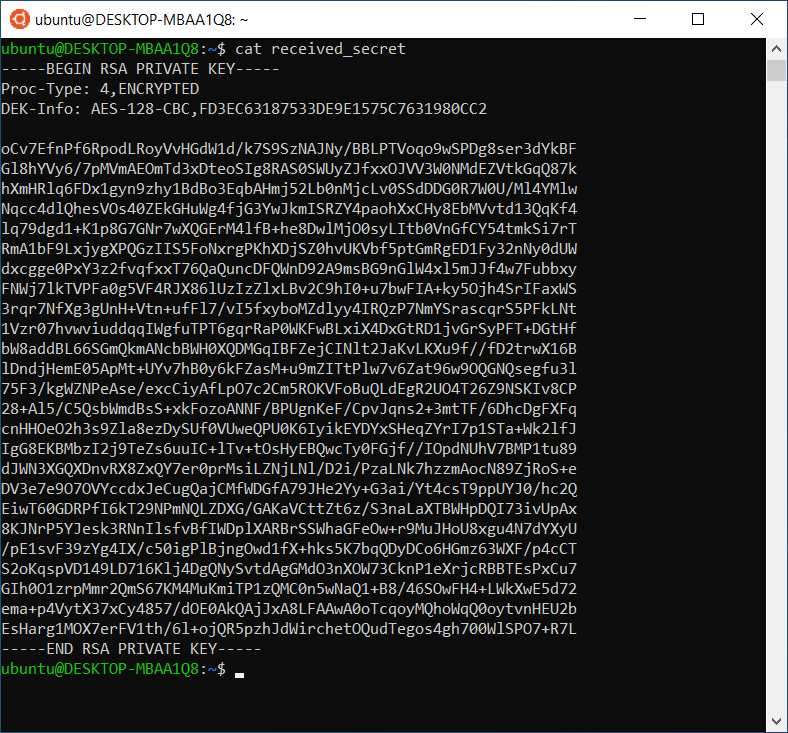
At the same time, our MITM device intercepted traffic between our target computers and copied it.
Now we can check the data from the intercepted TCP packet and compare it to the data on the second computer.
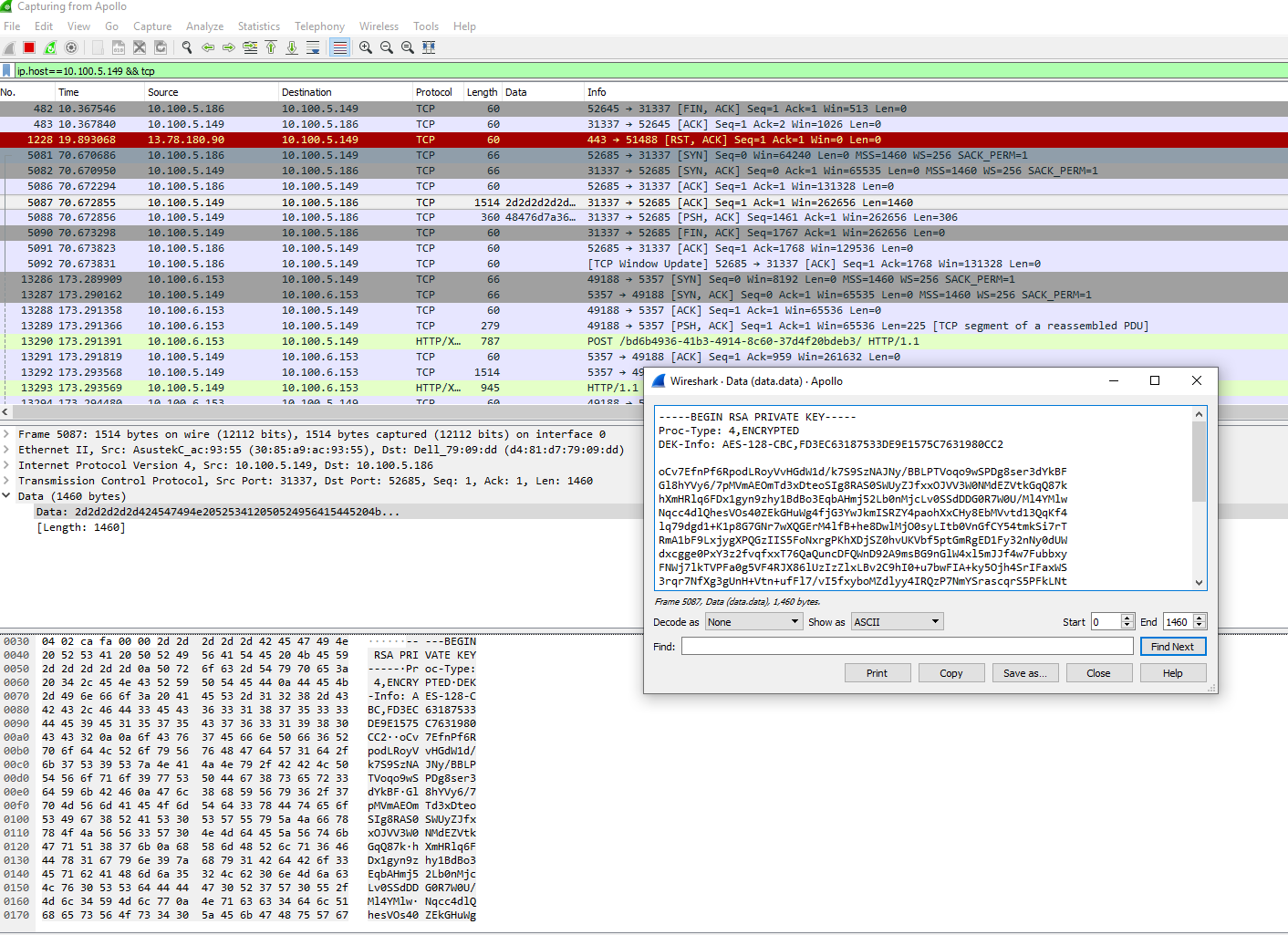
As you can see, in our scenario, unprotected data ended up in the hands of the attacker. Now let’s find out if encryption can help to mitigate this threat.
Protecting data with encryption
The most popular way of preventing a man-in-the-middle attack is by encrypting communication. For example, you can use Android encryption methods to secure Android applications. Here’s how it works: When a server transfers data, it identifies itself to the client by providing a digital certificate. After that, an encrypted communication channel is established between the client and the server.
There are two popular ways of encrypting client–server data:
-
Symmetric encryption is a system that uses one encryption key to cipher and decipher messages. The key becomes a shared secret between the communicating parties.
The main advantage of this protection method is the high speed of encryption. The drawback is the need for a secure channel to distribute the key between all communication participants. If hackers intercept the key, they can easily decrypt transmitted data.
Symmetric encryption is an old and widely used way to encipher data. For example, the US government is obliged to use the Advanced Encryption Standard (AES) to cipher communications. AES is a symmetric block-to-clock encryption algorithm.
-
Asymmetric encryption uses public and private encryption keys to secure transferred data. The public key is known to everyone; it’s transmitted through an open communication channel and is used for ciphering data. The private key is known only to the message recipient and is used for deciphering that data.
This type of encryption allows for exchanging keys via an open channel. Only a private key has to be securely stored by its owner. On the one hand, asymmetric encryption is more reliable than symmetric. On the other hand, the ciphering process includes more calculations and takes more time. This method is appropriate in cases when a group of people need to encrypt and decrypt data and the speed of this process is of small importance.
Asymmetric encryption is used for ciphering data by websites with HTTPS support, banking systems, messengers, and other services. Even popular blockchain technology that powers cryptocurrencies uses an electronic signature based on asymmetric encryption to verify transactions.
-
Hybrid encryption is a combination of symmetric and asymmetric methods. With such encryption, data is ciphered with symmetric encryption using a single key. That key is then ciphered with asymmetric encryption and sent with the data.
This way, you can have both the encryption speed from the symmetric method and the reliability of the asymmetric method. This type of encryption still isn’t perfect, though. For example, it’s susceptible to an adaptive chosen-ciphertext attack.
In an encrypted communication, a transport-level cryptographic protocol ensures a protected client–server data exchange. There are two versions of this protocol:
- Secure Sockets Layer (SSL) – the older one
- Transport Layer Security (TLS) – the newer one
SSL is considered less secure than the newer TLS. Both protocols use asymmetric encryption to authenticate communication parties and symmetric encryption to ensure confidential data exchange. Also, these cryptographic protocols ensure message integrity with message authentication codes. These protection measures allow TLS/SSL to make eavesdropping or accessing traffic without encryption keys impossible.
Now we’ve covered basic encryption methods. Let’s encrypt a piece of data with the TLS protocol and see if it offers reliable protection from an MITM attack.
When we recreate the attack described in the previous part of the article, our MITM device is still able to intercept the TCP packets transmitted between our two target computers. But now the intercepted data is encrypted with the TLS protocol:
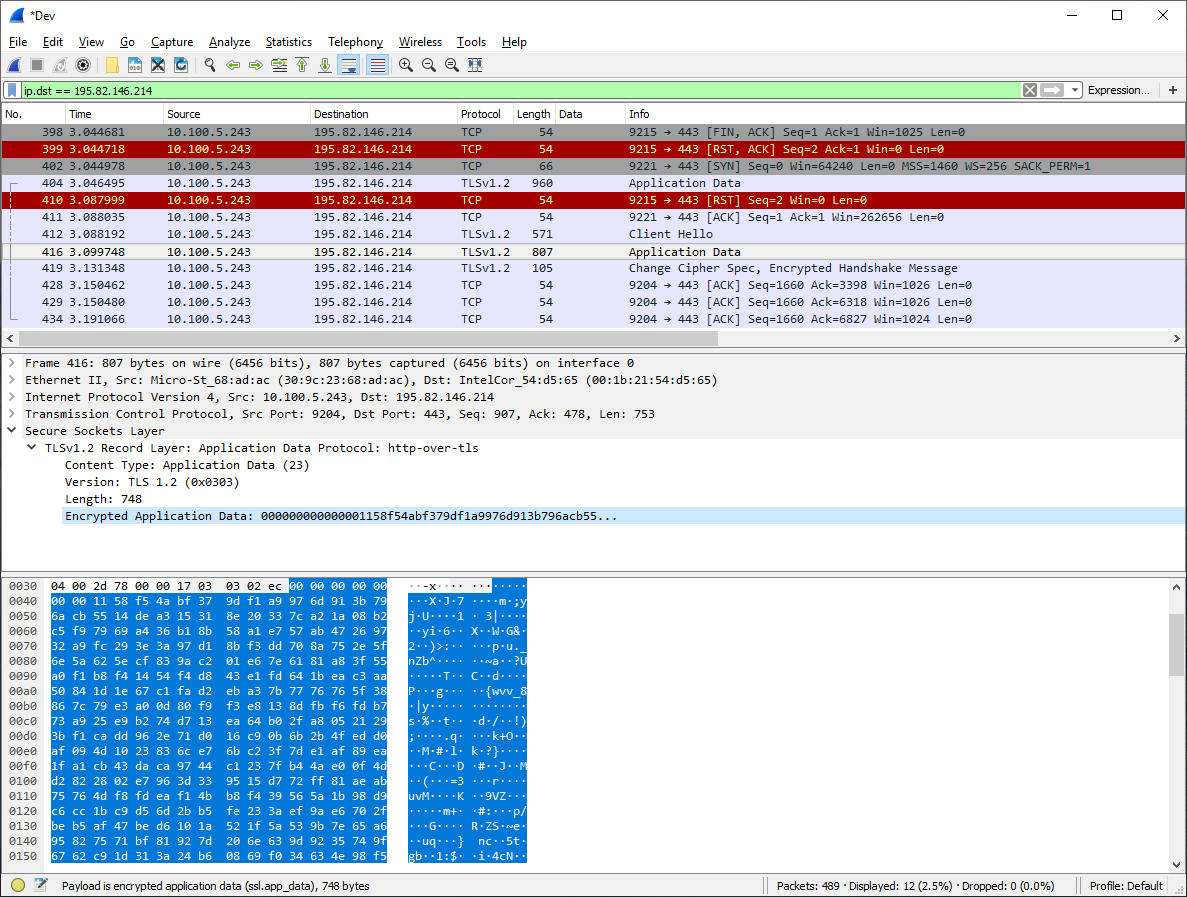
As you can see, an encrypted data packet looks like a chaotic mix of symbols. If attackers intercept such packets, they will have little to no chance of deciphering the encrypted data. Even if the attack is successful, the intercepted data is of no use to the attacker and therefore can’t be compromised.
Conclusion
MITM attacks are one of the most widespread and effective types of hacker attacks. And while it’s impossible to fully protect your network against them, you can ensure that your data stays protected.
Encrypting communication is an essential part of any cybersecurity project. This is the most reliable way to ensure that data transferred across your network is protected even if attackers can intercept it.
At Apriorit, we take network monitoring and management seriously. If you need to ensure data security, including against MITM attacks, contact our development team and start discussing your project!



