Embedded systems power many of the technologies around us, from microwave ovens to vehicles and aircraft — and the market for such systems is steadily growing. It was estimated to be worth $178 billion in 2024 and is anticipated to reach $284 billion by 2034. Embedded systems exchange data and empower human-to-machine communication, which is why they are popular targets for hacking.
Protecting embedded systems is quite a challenge because of their many limitations. To create effective and secure software for such systems, developers need deep experience with embedded solutions, cybersecurity tools and practices, and network communications. Such expertise is rare, but Apriorit’s embedded development team is ready to share their knowledge of embedded system security challenges, common attacks, and effective strategies for protecting your devices.
This article will be useful for tech leaders of companies who want to improve the security of embedded systems in their devices or plan on developing such a system and need expert support.
Contents:
What is embedded system security?
An embedded system is a combination of embedded devices that are located within a larger mechanism. Such a system is dedicated to executing one specific task, which sets it apart from any other system of devices. For example, a laptop has lots of embedded systems that control its performance, but it isn’t an embedded system itself because a laptop can perform various tasks.
Generally, an embedded system consists of a CPU, memory, and a peripheral device. In modern systems, those are united into a microcontroller or a microprocessor. An embedded system is governed by integrated software that determines the behavior of the embedded devices. Usually, developers can interact with embedded software via a user interface, but systems with severe hardware limitations may not support this.
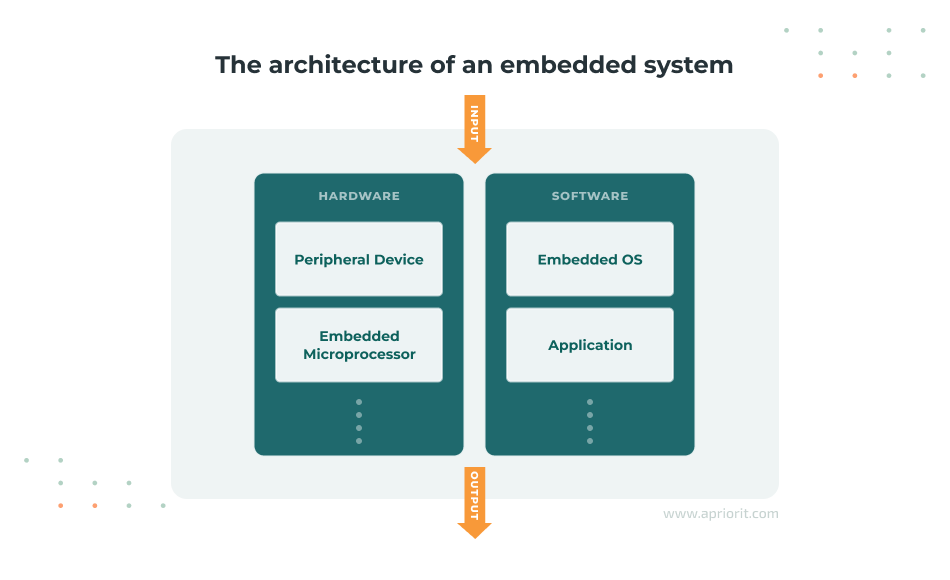
The key benefit of embedded systems is their ability to work in real time, solving a task with no or little delay. Such performance is achieved by optimizing system resources and hardware to perform one activity. Because of this optimization, using an embedded system is cheaper and less power-consuming than building a more complex device.
The drawbacks of embedded systems also arise from their compactness and dedication to a single task. Limited computing power and memory prevent them from running complex software. Embedded systems virtually can’t scale, as there’s no way to add significant computing power.
Hardware limitations also make it challenging to secure an embedded system, as its resources are focused on the task it performs. That’s why embedded developers have to plan security measures before building firmware and software for their products.
So, what is embedded system security? It’s a policy for developing embedded firmware and software that helps protect devices and the data they process from malicious activities. The exact details of the policy depend on the tasks the embedded system performs, but it’s a good practice to follow the CIA principle:
- Confidentiality — Protect the privacy of data in motion, at rest, and in storage from unauthorized and unwanted access.
- Integrity — Create a way to continuously make sure that the embedded system and its data aren’t modified.
- Availability — Ensure that the embedded system is available for authorized requests.
Following the CIA principle will help you create an embedded system security policy that protects your particular device. Let’s take a look at the key security risks that endanger embedded systems and that you need to take into account.
Ensure your project’s success with a trusted development team
Apriorit experts will help you get precise low-level control over your device’s security, functionality, and performance, helping you build a competitive product.
6 challenges of ensuring embedded system security
A vulnerability in embedded system security provides hackers a chance to access confidential information, use an embedded system as a platform to execute further attacks, and even cause physical damage to devices that can potentially lead to human harm. Yet implementing security in embedded systems is connected with numerous challenges:
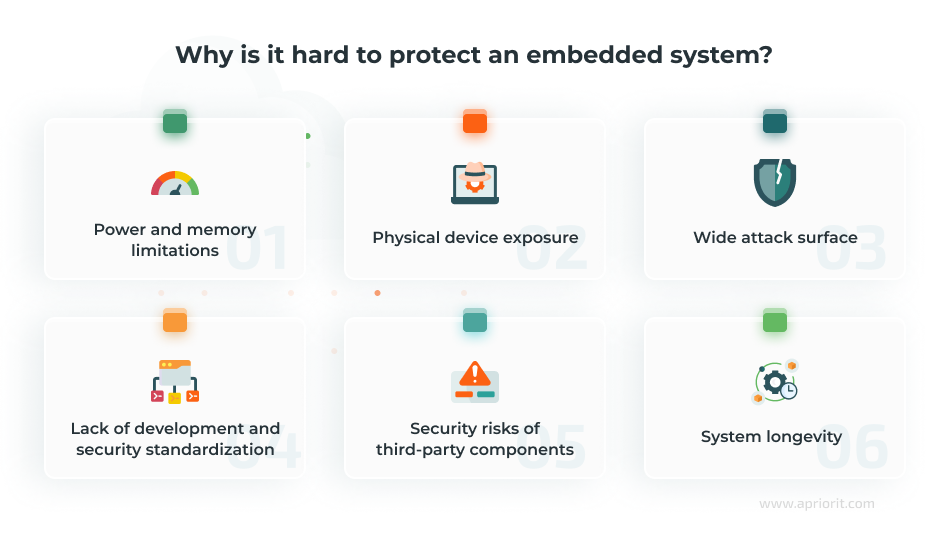
Power and memory limitations. Embedded systems operate with strict power and memory constraints, limiting the use of resource-intensive security measures like encryption and real-time monitoring. This makes it challenging for developers to balance functionality and security features while maintaining adequate performance, and it often leads to vulnerabilities that can be exploited.
Physical device exposure. Embedded devices are frequently deployed in uncontrolled environments, making them susceptible to physical tampering, side-channel attacks, and firmware extraction. Attackers can exploit debug interfaces, unsecured storage, or power analysis to gain unauthorized access.
Wide attack surface. Embedded systems interact with a range of hardware and software components, increasing the number of potential entry points for attackers. Lack of protection of communication channels, outdated protocols, and exposed APIs can be exploited for remote access or data interception.
Lack of development and security standardization. Many embedded systems are developed using proprietary or legacy technologies, leading to inconsistent security implementations across platforms. The absence of standardized frameworks for authentication, encryption, and vulnerability management results in fragmented protection measures.
Security risks of third-party components. Embedded software often relies on third-party libraries, open-source code, and pre-built firmware, introducing potential vulnerabilities if components are not properly vetted. Supply chain attacks, hidden backdoors, and outdated dependencies can compromise system integrity.
System longevity. Embedded systems are designed for longevity, often remaining in operation for years or even decades with minimal maintenance. This makes them attractive targets for attackers looking to exploit outdated firmware, unpatched vulnerabilities, or deprecated cryptographic algorithms.
Solving these challenges requires unique expertise of seasoned development teams. Failing to do so can result in security breaches, data leaks, and even physical damage to devices and vehicles. For example, unauthorized access to a healthcare device resulted in one of the biggest healthcare data leaks in 2024, resulting in the exposure of personally identifiable information of 4.3 million people. Another example is a security vulnerability in Mazda’s infotainment system that was discovered by security researchers. It allowed an attacker to abuse device input, get access to a vehicle’s systems, and even control the vehicle.
Read also
How to Create an SBOM to Secure Your Embedded System
Explore how a quality software bill of materials (SBOM) helps manage and secure embedded systems. Pick up real-life practices for generating a useful multi-layered SBOM for complex systems.

12 common attacks on embedded systems
Attacks on embedded systems can be divided into three categories depending on their targets:
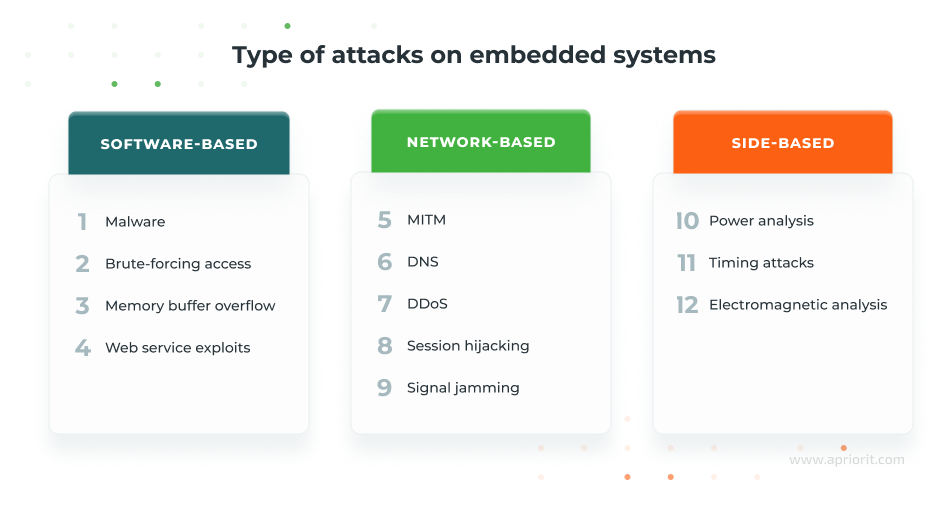
Let’s find out key characteristics of, common examples of, and possible countermeasures against these types of attacks.
Software-based attacks
Software-based attacks target the brains of the system — the application that manages the devices. A successful attack on software allows a hacker to access data or gain control over an embedded system.
Searching for vulnerabilities in software design and code is the most popular vector of attack because it’s possible to conduct such an attack remotely. Also, a software-based attack doesn’t require specific knowledge from hackers, as they can use typical attacks like deploying malware and brute-forcing.
Here are the most widespread software-based attacks:
- Malware attacks on embedded systems work the same way as with any other system: a hacker deploys a piece of malicious code that tries to intercept the data stored inside the system, take control over the victim system, or harm it. Usually, hackers fake firmware updates, drivers, or security patches to deliver malware.
- Brute-forcing access credentials is, to put it simply, the process of guessing them. Most embedded systems provide remote access to a graphical user interface that hackers can exploit.
- Memory buffer overflow is a type of attack when hackers manually overflow the buffer of memory allocated to contain data that moves inside an embedded system. Hackers deploy exploits that swamp the memory buffer with too much data. In this case, the embedded operating system will record some of that data in memory sections located next to the buffer. Recorded data may contain shellcode or other exploits that help hackers obtain credentials and elevate their access rights.
- Exploiting a web service isn’t an attack directly on an embedded system but on a service it communicates with. Vulnerabilities in a web portal can endanger data processed by the system, give hackers access to it, or let them control the device.
Network-based attacks
This type of attack exploits network infrastructure vulnerabilities and can also be performed remotely. Using these vulnerabilities, hackers can listen for, intercept, and modify traffic transmitted by an embedded system.
Let’s take a look at the most common network-based attacks:
- Man-in-the-middle (MITM) attack allows hackers to intercept or alter data transmitted by an embedded system. To execute it, they change the connection parameters of two devices in order to place a third one between them. If hackers can obtain or alter the cryptographic keys used by both devices, they can eavesdrop in a way that’s very hard to detect as it causes no disruption in the network.
- Session hijacking is similar to an MITM attack but has a different goal: the hacker listens to embedded system traffic to obtain authentication credentials. There are various ways to execute hijacking: fixating a user session identifier, stealing a session cache, cross-site scripting, and more.
- Domain name system (DNS) poisoning forces a local DNS server to modify its records according to a hacker’s needs. A DNS server converts human-memorable domain names and hostnames into corresponding IP addresses. By using a DNS server’s vulnerabilities and poisoning its cache, hackers can reroute traffic from a targeted website to any other address.
- Distributed denial of service (DDoS) is a well-known attack that makes a system unavailable by overflowing it with requests from various sources. Such attacks are hard to stop because requests come from a vast number of IPs.
- Signal jamming is a technique that allows hackers to create interference in the network to jam or distort communication from a device. Depending on the type of jammer, it can jam any communication on the channel, start working when a targeted device transmits data, or be activated upon detection of specific packets. Such an attack can make an embedded system unavailable.
Side-channel attacks
Side-channel attacks intend to use hardware security flaws in embedded systems to hack them. A side-channel attack is the hardest and most expensive type of attack, as it requires precise knowledge of the hardware design and physical availability of the target system. To carry out a side-channel attack, hackers gather information on system power consumption, electromagnetic leakage, operation timing, etc.
As a result, they may work out the internal operation of a system and connected devices, steal cryptographic keys, or even gain control over the system.
Here’s a list of the most common side-channel attacks:
- Power analysis requires physical access to an embedded system in order to probe its connections and detect changes in power consumption. These changes depend on the data processed by the system, so hackers may detect when a system processes a particular type of information and intercept it.
- Timing attacks are based on the timing of embedded system operations. They’re used to gain information such as applied cryptographic algorithms, data-dependent differences in instruction times and code branches, cache access times, and more. This type of attack also requires physical access to a device and deep knowledge of embedded system architectures.
- Electromagnetic analysis provides hackers with a way to record and analyze emissions from a device, figure out its cryptographic operations, and even extract secret keys. This is the most time-consuming and costly type of attack as it requires physical proximity to an targeted embedded system, information on the layout of the device, and isolation from other devices to protect the system from electromagnetic interference.
The cybersecurity measures for embedded systems we discussed above can help you prevent or stop particular types of attacks. But you can never be too careful, right? In the next section, we offer ten recommendations for effectively protecting embedded hardware and software.
Read also
Hardware Reverse Engineering: Use Cases, Benefits, and a Practical Example
Learn when you can ethically reverse engineer a device, which skills and tools are required for this, and how your embedded development project can benefit from it.

10 best practices to secure embedded systems
Before you start coding, study industry standards for embedded software development to discover effective security measures and development practices. For example, pay attention to:
- OWASP Embedded Application Security
- IEEE standards
- Foundational Cybersecurity Activities for IoT Device Manufacturers [PDF] by NIST
- Embedded System Development Process Reference guide [PDF] by IPA
It’s possible to make your protection even more reliable at all stages of development from design to support by following these practices:
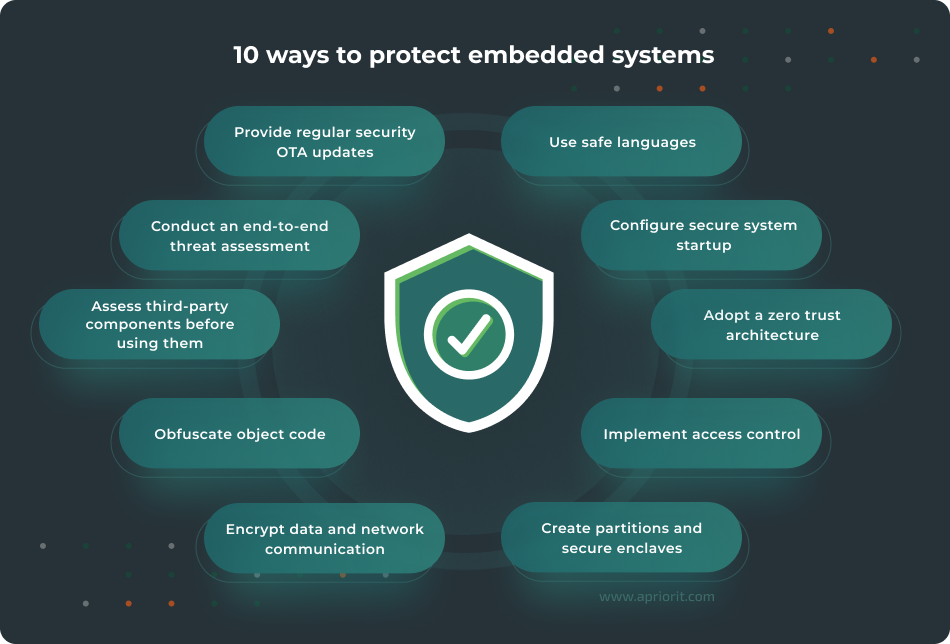
1. Use safe languages. Embedded software development requires a language that offers precise low-level control of the device. Usually, developers choose C/C++ or Rust for firmware, with Rust becoming increasingly popular thanks to its memory safety, interoperability with other languages, and cybersecurity capabilities. For integrations and web services that manage embedded systems, you can use Python or Go. Both are high-level and easy-to-learn languages that provide all the required tools and security checks.
2. Configure secure system startup. The first step here is to enable secure boot, a feature that allows a microprocessor to verify the cryptographic key and location of the firmware before executing it. To enhance this protection, you can also enable a processor’s trusted execution environment feature, which creates a secure region in the microprocessor to store firmware. Also, make sure to disable all insecure and non-essential services at system startup. To define such services, analyze your system’s operation. Usually, the list of such services includes Telnet and Trivial File Transfer protocols, the debug agent, open ports, etc.
3. Adopt a zero trust architecture. This type of architecture is based on the principle that any connection to the embedded system is untrusted until proven otherwise. A zero trust architecture improves the security of the system itself and stops malicious lateral movement inside the network in case a hacker gains access to another network element. Implementing zero trust technology requires many security mechanisms like a role-based access model, continuous and multi-factor authentication, network segmentation, and identification of users and devices.
4. Implement access control. Unprotected access to any part of an embedded system or network is an open invitation for hackers. To secure your access points, use strong encrypted credentials, implement the principle of least privilege, and enable identity verification wherever possible.
5. Create partitions and secure enclaves. Separating important parts of the embedded system like the operating system, GUI, and security applications into different partitions helps isolate them from each other and prevent or contain an attack. You can create both physical and virtual partitions. To improve the isolation of embedded systems, you can also create secure enclaves — isolated execution environments with strong hardware-based protection that store data or contain sensitive processes.
6. Encrypt data and network communication. All firmware updates, transmitted and processed data, and stored credentials have to be encrypted. Use cryptographic signatures to verify files obtained from trusted sources and detect suspicious modifications. Encrypting data on an embedded device may require a significant chunk of its resources, especially if it has to operate in real time. However, implementing strong encryption is a necessary step for securing your data. To improve network protection, you can also use IPsec, DNS SEC, SSH, or SSL protocols, and you can use a VPN to protect any communications with embedded systems. It’s also a good practice to deploy a firewall to filter traffic.
7. Obfuscate object code. Obfuscation is the process of making your code entangled and unclear for hackers yet executable for an embedded system. It’s even possible to speed up execution by obfuscating code. This measure will make it harder for hackers to reverse engineer your code.
8. Assess third-party components before using them. Embedded firmware often relies on third-party frameworks and libraries, which can introduce vulnerabilities to your system. Before adding them to your code, check your components for known security issues. You can research vulnerability databases, bug tracking systems, and other known vulnerability records. You can also conduct security testing of third-party elements before using them.
9. Conduct an end-to-end threat assessment. You should conduct a threat assessment before releasing your embedded system to make sure it is secure and reliable. A complete security assessment includes:
- Performing a complete lifecycle analysis and identifying potential threats from the viewpoints of the device manufacturer, software developer, and end user
- Creating a risk matrix and estimating the likelihood of and success rate of an attack via each possible channel
- Simulating a hacker attack on your own or performing black-box penetration testing
10. Provide regular OTA security updates. Updating any embedded software and firmware is always a challenge due to several factors:
- Embedded devices are usually deployed for a very long time
- Not all embedded systems have network connectivity
- The limited power of embedded systems means they can’t always run new security features
However, regular security updates help you keep your devices and users’ data protected. When designing an embedded system, make sure to add support for future over-the-air (OTA) updates and add signature verification so that your system installs only trusted updates.
With these practices in place, you can make it much harder for a cybercriminal to compromise your software for embedded systems.
How does Apriorit help secure your embedded systems?
Apriorit specializes in complex low-level development, reverse engineering, and cybersecurity. Our skill set is exactly what you need for fast and efficient embedded development. In particular, you can leverage our:
- Security-first development approach based on the secure software development lifecycle. This approach helps us focus on protecting your solution at each stage of development, resulting in an all-around secure product.
- Deep expertise in driver, embedded, and IoT development. Our engineers have real-life experience in designing, implementing, maintaining, and upgrading low-level solutions for various devices, from virtual reality headsets to drone management units.
- Niche reverse engineering skills that help us look inside legacy software and devices in a legal and ethical way. Our reverse engineers will help you understand and improve legacy products, build reliable integrations with third-party services and devices, and conduct penetration testing.
- Focus on flexible and efficient cooperation. With three cooperation models and years of experience with different clients and industries, we adjust our workflow to your preferences. Whether you need a dedicated team for a long-term project or quick fixed-price development, we have your back.
Conclusion
Developing software for embedded systems is quite a challenge. A developer has to implement all the required functionality while taking into account multiple device limitations and securing the software from attacks. Threats may come from various sources and channels, so ensuring protection against all of them with a microprocessor and a tiny amount of memory may seem impossible.
At Apriorit, we have over 20 years of experience in embedded software development. During that time, our team has worked with a variety of devices and platforms, assuring fast and secure operations for all of them.
Planning an embedded development project?
Partner with Apriorit’s skilled team to ensure the security, performance, and reliability of your device.


