When improving software, keeping your customers’ security in mind is crucial. One of the key vectors your team should consider is protection against the ever-increasing number of browser-based attacks targeting remote employees.
To protect themselves from online threats, organizations used to filter incoming traffic or block access to suspicious websites. But those measures aren’t effective when you need protection against zero day attacks. Remote browser isolation (RBI) is the next step for providing such protection, moving internet browsing to an isolated environment and securing the user endpoint.
But what is remote browser isolation and how does it work? In this article, we answer these questions and share insights into how this technology secures an internet user from cyberattacks. You’ll also discover types of RBI, must-have features, and challenges to consider during development.
This article will be useful for tech leaders wanting to protect their companies and development leaders looking into useful technologies for their cybersecurity products.
Contents:
- What is remote browser isolation?
- The increasing threat of web-based attacks
- How does remote browser isolation work?
- Types of remote browser isolation
- Who can benefit from remote browser isolation?
- Advantages of RBI solutions
- Key functionality of an RBI solution
- Overcoming the challenges of RBI implementations
- Is RBI enough for all-round protection?
- Conclusion
What is remote browser isolation?
Browser isolation is a virtualization technology that moves browser execution from a user’s device to a secured environment — locally on the user’s device or remotely in the cloud (RBI). This way, browser activity is isolated from the user, preventing any attempts at malware infection via web-based attacks.
Browser isolation takes a fundamentally different approach to web security compared to traditional cybersecurity solutions. Usually, a security solution needs a list of known attacks and suspicious activities so it can recognize threatening web content and block access to it. Web isolation technology secures any web content inside the remote endpoint, sanitizes it, and sends safe content to the user’s local browser. As a result, the user gets access to content while being protected even against zero day attacks.
The key function of RBI is protecting employees that work with highly sensitive data like government, medical, banking, or military records. Malicious actors may try to steal this valuable data from employees’ machines using a variety of methods, including web-based attacks. Let’s examine how such attacks can threaten an organization.
The increasing threat of web-based attacks
The number of web-based attacks is growing precipitously as more and more daily activities go online. The number of attacks in the second half of 2023 increased by 198% compared to the first half of the year according to the 2023 State of Browser Security Report by Menlo Security. Of those attacks, 30% relied on evasion techniques, which make it hard for common cybersecurity tools to detect and stop them.
Web-based threats expose organizations to two major threat sources: browser-based malware and phishing attacks.
Browser-based attacks occur when hackers inject a piece of malicious code into website components or files. This code leverages browser vulnerabilities or user mistakes to deliver malware, intercept traffic, or gain access to the user endpoint. As a result, attackers can:
- Infect a user’s device with malware
- Steal or encrypt sensitive data
- Abuse computational resources
- Compromise the enterprise network and other devices connected to it
Phishing is a social engineering technique aimed at obtaining sensitive information (personal data, credentials, credit card details, etc.) and using it to gain access to private or corporate resources. In a phishing attack, attackers communicate with users while pretending to be a trusted entity (for example, a social network, bank, or colleague), lead users to a phishing site, and motivate them to input sensitive data.
Remote browser isolation is one of the key technologies for corporate protection from web-based threats. Since RBI executes web content on a remote endpoint instead of a user machine, the data on the endpoint stays safe even during an attack. With RBI explained, let’s examine the details of RBI technology.
Looking for a way to secure remote environments from web-based threats?
Let’s discuss how to efficiently and securely integrate custom remote browser isolation into your environment.
How does remote browser isolation work?
Your team can isolate a browser from users in two ways:
As we mentioned above, a browser can be isolated from the user in two ways:
- Locally, or by client-side browser isolation. This moves browser execution to a virtual machine or sandbox (app-level or OS-level) created on the user endpoint or an on-premises server. This type of isolation can’t be considered totally secure because the browser is still executed on the user’s device. It’s possible for an attacker to break out of isolation and access the user’s local files and networks.
- Remotely, or by server-side browser isolation. Remote browser isolation moves the browsing to a remote server. Server-side isolation provides a higher level of security because it uses a remote server or cloud service as an intermediary between the user’s device and web content. In case of an attack, the hacker will break out of the isolation and reach the remote browser, not the user endpoint.
An RBI architecture is usually based on virtualization or containerization. Solutions that employ centralized virtualization are more demanding on server resources. To initiate one browser, each virtual machine (VM) needs to run a full copy of the operating system and a virtual copy of all the hardware that the operating system needs.
Containerization technology is much more efficient. With containerization, a remote browser isolation solution needs to run one operating system and an RBI program without the necessity to emulate hardware. A browser running in a container requires up to 10 times less server infrastructure than one using virtualization. Also, the distributed nature of containers makes RBI more reliable: if attackers breach one containerized browser, there’s no way they can reach another container.
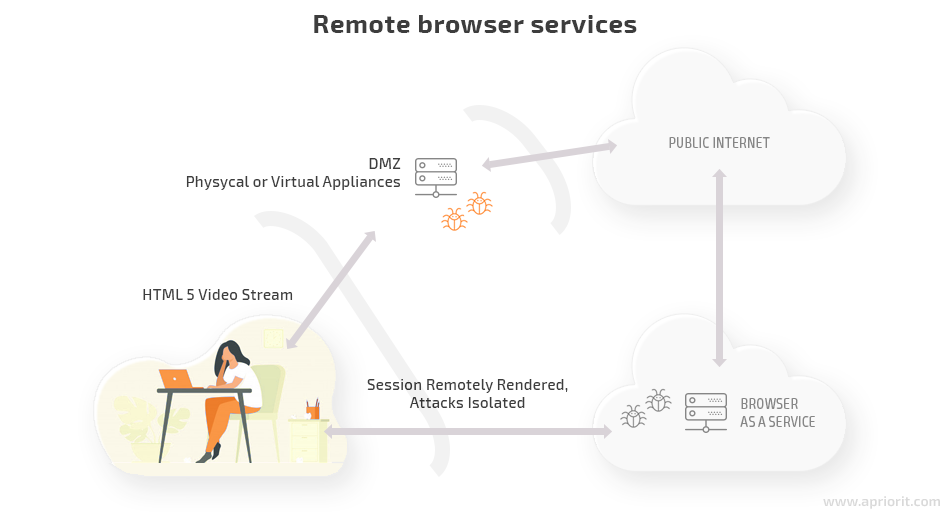
For a user, RBI works this way:
- The user connects and authenticates in a remote browser isolation service.
- The RBI service creates a virtual instance and provides the user with access to a remote browser.
- The user interacts with web content as usual via the local browser.
- The remote browser passes the web content (in the form of a video stream or sanitized HTML code) to the user’s local browser.
- When the user session ends, the instance that contains the remote browser is terminated.
Types of remote browser isolation
Regardless of the choice of technology, there are three types of architecture for an RBI solution:
- Pixel pushing — This technology is similar to a remote desktop or Virtual Network Computing. It captures events in the user’s browser (clicks, mouse movements, keystrokes, etc.), transmits them to a remote browser, and returns a response in the form of a series of screenshots or a video stream. In this way, the user’s endpoint doesn’t receive any web application code and the user interacts only with images or video renders.
- Document Object Model (DOM) reconstruction — This technology sanitizes the HTML or CSS code of a web application from threats on a remote endpoint and then forwards clean code to the user’s endpoint. If an RBI solution detects a piece of suspicious code, it deletes it. Some RBI solutions consider all pieces of dynamic code as potentially harmful and delete them. After sanitization, the RBI solution sends static web page code to the user’s local browser and the page is rendered on the client side.
- Network vector rendering (NVR) — This technology streams draw commands to a remote endpoint. Similarly to pixel pushing, NVR draws web page contents on a remote or virtual endpoint using Draw commands. These commands consume less traffic than transmitting a web page pixel by pixel.
Any organization that manages sensitive data and has remote employees or offices can benefit from RBI. Let’s examine key use cases for this technology.
Related project
Developing a Custom Secrets Management Desktop Application for Secure Password Sharing and Storage
Discover a success story of delivering an internal secrets management tool that helped our client significantly improve their cybersecurity. Read on to explore details of creating a robust solution with support for Windows, macOS, and Linux platforms, as well as compliance with the GDPR and ISO 27001.

Who can benefit from remote browser isolation?
Remote browser isolation can help almost any organization improve its security posture and data protection capabilities. Let’s take a look at key use cases for RBI deployment in industries that often prioritize data security. Keep in mind that this list is not exhaustive.
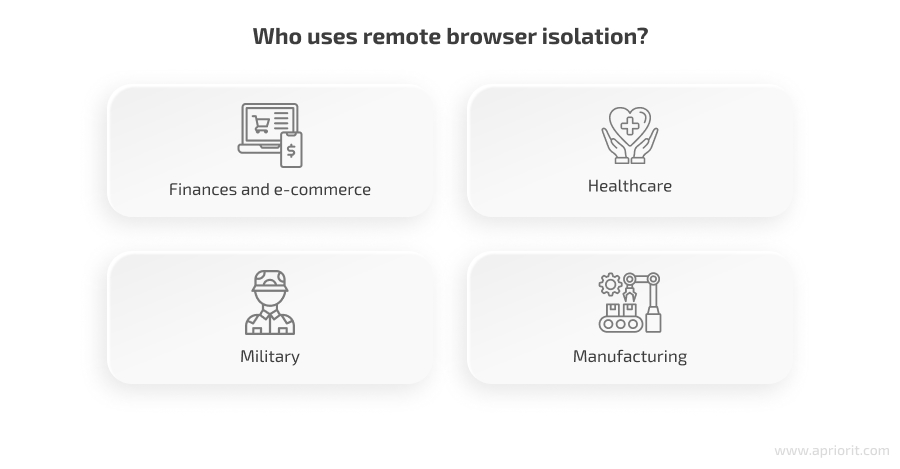
Finance and e-commerce
Most companies that work in finance and e-commerce have a divided structure with numerous offices and branches. Managing sensitive information in a distributed organization requires implementing strong network and endpoint protection measures. Financial and e-commerce companies can use RBI to:
- Prevent data theft from employee endpoints
- Secure client data
- Access high-risk websites during research and fraud investigations
- Ensure regulatory compliance
Healthcare
Healthcare practitioners commonly use multiple devices during their workday, both in the office and when visiting a patient at home. Since such devices accumulate tons of private medical records, they are often connected to a mobile device management system. An RBI application can be a part of this system, allowing healthcare workers to safely access the internet.
Here’s how healthcare organizations can benefit from using RBI:
- Safeguard patient data
- Ensure the security of remote consultations and house calls
- Protect endpoints of doctors and scientists conducting research
- Prevent leaks of lab results and other medical records
Military
Modern military organizations face a unique set of challenges as they have to learn to withstand attacks in both real and digital worlds. By enhancing their security with RBI, military organizations can:
- Gather intelligence and OSINT data safely
- Protect personnel from targeted attacks
- Enhance the security of classified information
- Enable secure communication with allies and partners
Manufacturing
While manufacturing organizations tend to have fewer remote jobs compared to other industries, their employees use lots of connected devices that need to be protected. Deploying an RBI solution can help manufacturers to:
- Protect intellectual property
- Prevent production shutdowns caused by hacking attacks
- Secure engineering research and data exchange
- Safeguard components of the organization’s supply chain
These are only key use cases for remote browser isolation. Your company may have unique requirements and applications for such technology depending on the nature of your business and the data you need to protect.
Now, we can look at advantages of enhancing your data protection systems with RBI.
Related project
Developing a Custom MDM Solution with Enhanced Data Security
Explore how we helped a client develop an MDM solution for secure management of Android tablets in corporations and federal institutions. Thanks to our work, the client successfully released the first 5,000 tablets, expanded their services, and maintained a high level of data security.
Advantages of RBI solutions
Remote browser isolation is a new yet promising cybersecurity technology. Implementing an RBI solution provides organizations with these advantages:
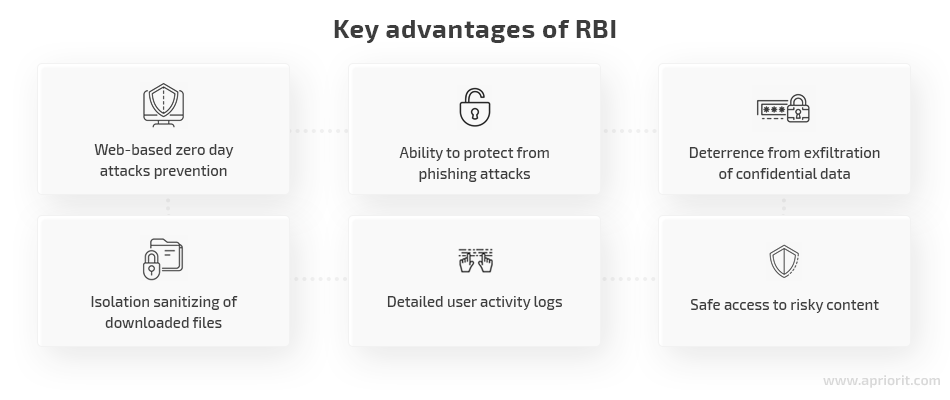
- Web-based zero day attack prevention. Traditional cybersecurity solutions like firewalls and antivirus software can stop suspicious or harmful web activity only if they detect markers of known attacks. RBI solutions provide more reliable security because they can also block zero-day browser-based attacks. Since all browsing activity is isolated in the remote instance and the user interacts with mirrored or sanitized content, there’s no way a hacker can infect a user endpoint.
- Ability to protect from phishing attacks. When a user clicks on a phishing email or file, an RBI solution displays the sanitized email text, scans the attached files, and isolates the phishing web page if an email contains a URL to a malicious website. In this way, the user’s interaction with phishing websites is completely secured.
- Deterrence from exfiltration of confidential data. System administrators can change RBI settings to display suspicious URLs in read-only mode. This allows users to access such web pages but doesn’t allow them to input any credentials. Alternatively, administrators can allow users to access only trusted websites.
- Isolated sanitizing of downloaded files. If a user wants to download a file, it’s also isolated in the remote instance. RBI systems provide tools for reviewing this content remotely (e.g. PDF or image viewers). If the software can’t read the downloaded file, it sanitizes the content on a remote server and sends it to the user’s endpoint. In this way, an RBI solution reduces the risk of downloading malicious and suspicious files.
- Detailed user activity logs. An RBI system logs all events on the remote instance and the communication with end users. If an attack or security violation happens, system administrators can review those logs to get a clear understanding of the cybersecurity incident, report on it, suggest security improvements to prevent similar issues, collect data for forensic activities, etc.
- Safe access to risky content. An RBI system allows users to access any websites and download data they need while neutralizing threats. This approach doesn’t disrupt web browsing; meanwhile, other security solutions like antivirus or firewall software will block any access to a website if they detect a threat.
To ensure the benefits listed above, an RBI solution requires a certain set of features. In the next section, you’ll learn about the capabilities necessary for an RBI system to provide a sufficient level of security.
Read also
Secure and Anonymous Virtual Networking Infrastructure: How It Works, How to Implement It, and What’s Next
Looking for more ways to secure remote environments? Explore how software-defined networking can help you establish protected communications and how to configure advanced network routing.

Key functionality of an RBI solution
Regardless of the type of isolation, an RBI solution needs a specific set of functionality to ensure secure internet browsing. There are eight basic components of an RBI solution that ensure remote browser isolation and security:
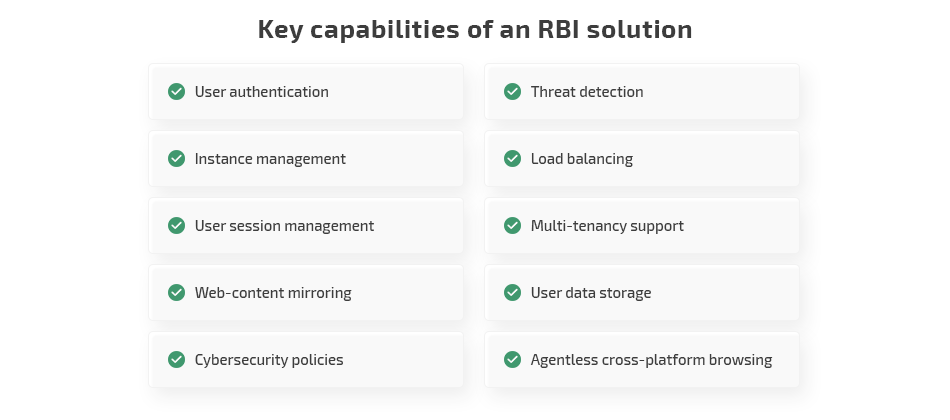
- User authentication. Before creating an isolated browser instance, an RBI solution needs to authenticate the user connecting to it. After that, the solution loads the user’s profile permissions, settings, and preferences. Some solutions cache authentication data so users don’t need to provide credentials each time they connect.
- Instance management. When a user initiates a session, an RBI solution creates an isolated instance to run a browser and connects the user to it. Depending on the RBI architecture, this instance may be a virtual machine, a container, a sandbox, or something else. When the RBI solution detects a threat, the instance tries to eliminate it. If the instance has been compromised, the RBI shuts it down and launches a new one with all the tabs opened during the session. When the user ends the session, the RBI solution shuts down the corresponding instance.
- User session management. During the session, the RBI system processes user requests and passes them to the instance, collects data on the session (duration, opened URLs, browser cache), and saves the data after session termination.
- Web content mirroring. An RBI system’s core functionality is streaming browser data from a remote browser to a user’s local endpoint. An RBI system needs to process user events (keystrokes, scrolling, mouse clicks, etc.), match them with the corresponding web page elements, detect changes open tabs, and send them to the user in the form of video or a sanitized web page. Also, a remote browser has to support browsing functionality, plug-ins, and SaaS applications.
- Cybersecurity policies. These policies allow an organization’s security officers to whitelist trusted web applications and types of content that can be rendered on local devices. Security officers can also specify users who can access particular types of web content or URLs. Such policies help security officers efficiently manage RBI and local network resources.
- Threat detection. During the session, an RBI solution applies a zero trust approach to each instance and monitors it for possible threats and suspicious activity. When the RBI solution detects a threat, it sanitizes the web content and sends the sanitized content to the user endpoint.
- Load balancing. Constant content mirroring puts a heavy load on the user’s bandwidth and a remote instance. RBI solutions must balance the load on those components by compressing data sent to the user’s device, creating additional instances if the original instance is overloaded (e.g. if the user opens too many tabs), and reducing the quality of video and audio content. This functionality helps to optimize RBI performance and the user experience.
- Multi-tenancy support. Multi-tenancy allows an RBI solution to ensure high availability for users all around the world, improve load and bandwidth management, and increase scaling capabilities.
- User data storage. If a user downloads files during the remote session, an RBI solution needs to scan them for possible threats and sanitize them before sending them to the user endpoint. An RBI solution should also store data on uploads, viewed documents, session cache, and user settings. Additionally, it has to provide remote viewing of downloaded files.
- Agentless cross-platform browsing. To minimize the number of security threats, it’s best to develop agentless RBI software. This software needs to support all popular operating systems (both for PC and mobile platforms) and browsers to ensure the best user experience.
The set of features listed above allows an RBI solution to ensure comfortable and secure browsing and is particularly useful for companies that work with highly sensitive data. However, it’s not a perfect solution. Let’s take a look at the key challenges of RBI and ways to overcome them.
Read also
How to Ensure SaaS Data Security with Curated Database Design
Discover how database structure affects SaaS security and which structure will best fit your project.

Overcoming the challenges of RBI implementations
RBI technology has several limitations that you need to take into account:
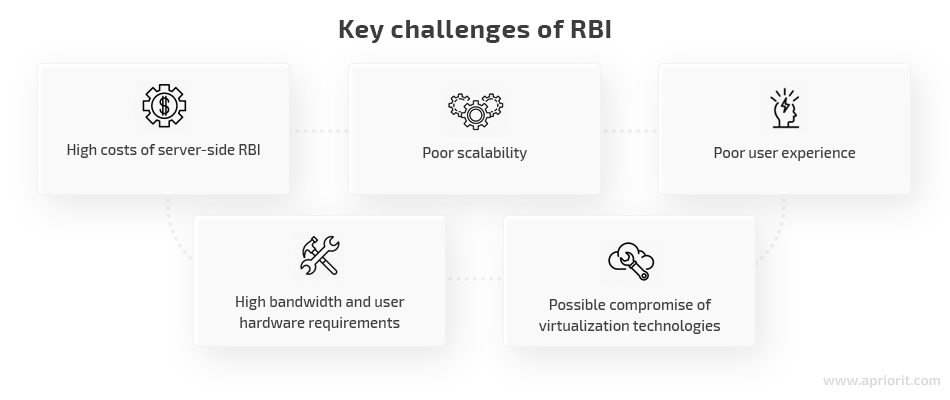
- High costs of server-side RBI. True remote isolation requires remote servers that support thousands of virtual environments and can perform well under heavy loads. Building and supporting such an infrastructure is expensive, especially if RBI is based on virtualization technologies. Containerization greatly reduces the maintenance cost of an RBI solution because it takes fewer resources to run a container than to run a virtual machine.
- Poor scalability. The more users an RBI solution has, the harder it is to manage and orchestrate all remote sessions. Scalability issues are caused by the centralized architecture of virtualization technologies used in RBI development and the growing need for hardware to build remote servers. Partially, this limitation can be overcomed by choosing a decentralized architecture during RBI development.
- Poor user experience (UX). Both pixel pushing and DOM reconstruction technologies influence the UX.
- With pixel pushing, a user can experience delays since streaming video and audio content can be time-lagged. Also, the video displayed on the user endpoint may be blurry because the web content is streamed in a resolution set on the remote instance. System administrators can improve the UX by carefully adjusting the RBI system to the capabilities of an organization’s network and hardware.
- DOM reconstruction deletes all suspicious or dynamic code from a web page, meaning a user might not receive important blocks of the page. It’s possible to whitelist safe web apps to reduce the risk of losing important information.
- High requirements for internet bandwidth and user hardware. An RBI solution needs a lot of resources to flawlessly stream remote browser sessions. For pixel pushing, it requires broad and stable bandwidth to video stream sessions without delays and in high quality. DOM reconstruction puts an additional load on the user’s device, as it has to render web pages from the content that a remote browser sends to it. However, a custom solution developed with possible limitations and load balancing in mind won’t put a lot of additional stress on an organization’s resources.
- Possible compromise of virtualization technologies. Isolating web content and all threats related to it on RBI servers ensures the security of enterprise endpoints and networks. But the compromise of those remote servers means the loss of isolation for RBI clients. Depending on an organization’s security policies, its users will either reconnect to an uncompromised server or lose the ability to securely browse. There’s no way to guarantee the complete protection of remote servers, but leveraging cybersecurity best practices helps to minimize the risks.
The limitations listed above stop RBI from being a one-size-fits-all solution. When developing such a solution, developers have to carefully balance the loads, taking into account the limitations of the technology and a particular client’s request.
Is RBI enough for all-round protection?
RBI solutions provide a solid defense against web-based attacks, but they aren’t enough to guarantee maximum security for corporate data and networks. Implementing RBI technology doesn’t replace the need for other common cybersecurity solutions, but it can complement and enhance them.
To broaden the protection layer for users and organizations, you can combine RBI with the following security approaches and technologies:
- Zero trust networks — This cybersecurity approach treats all devices as untrusted, even if they’re connected to the enterprise network and have already been verified. A device can connect to another device, application, or network only after it’s identified and its user is authenticated. If identification or authentication fails, the device is isolated from the network.
RBI enforces the zero trust approach to web browsing. Applying it to internal networks and resources protects an organization from both internal and external threats.
- Software defined perimeter (SDP) — In our previous article, we’ve already mentioned various software defined perimeter benefits. This approach creates a “black cloud” over the enterprise network and resources for all unauthenticated devices. To access a resource inside the SDP, a user and device need to be authenticated using a multi-factor token. After that, the device can access only the requested resource. To access other resources and apps, the user and device need to authenticate themselves once again.
RBI complements SDP the same way it works with zero trust networks: by securing external connections while SPD protects internal activities.
- User behavior analytics (UBA) — This technology detects suspicious user activity by analyzing logs of normal user behavior, establishing a baseline, and spotting unusual user actions. User behavior analytics solutions are usually based on artificial intelligence algorithms or statistical analysis. This technology is especially effective for detecting insider threats and targeted attacks that involve theft of user credentials.
One of RBI’s advantages is the collection of detailed logs on user activity: access to and interactions with websites, downloads, inputted information, etc. These logs can provide a basis for UBA solutions.
Conclusion
Browser-based threats like phishing, credential theft, and web-based attacks are getting more and more widespread. They target both private users and large organizations, stealing and corrupting their sensitive data.
Remote browser isolation technology moves browser execution from a user’s device to a remote endpoint, isolating any possible threats. In this way, RBI provides solid protection against web-based threats for an organization’s data, devices, and networks. This technology provides companies with many cybersecurity benefits. It also brings several challenges that RBI developers need to take into account.
To gain maximum benefits and avoid the limitations of RBI, such a solution has to be adjusted to a company’s needs. Or even better — designed and developed specifically for a certain organization.
Looking for an experienced cybersecurity partner?
Apriorit security experts know all the nuances of RBI development and will gladly create an RBI solution that meets the precise needs of your organization. Let’s start protecting your remote environments!



