Sandboxing is a proven way to detect malware and prevent its execution. However, malicious actors search for ways to teach their malware to stay inactive in the sandbox. Sandbox-evading malware can bypass protections and execute malicious code without being detected by modern cybersecurity solutions.
In this article, we analyze techniques used by malware to avoid sandbox analysis and share best practices we use at Apriorit to build sandboxes that can detect and stop evading malware.
This article will be useful for developers who are working on cybersecurity solutions and want to improve their sandboxes.
Contents:
What are sandboxes and sandbox-evading malware?
Before we discuss sandbox-evading malware, let’s figure out what sandboxing is. NIST defines a sandbox as “a system that allows an untrusted application to run in a highly controlled environment where the application’s permissions are restricted to an essential set of computer permissions.”
A sandbox solution can be a standalone tool or part of your cybersecurity software, such as a firewall or antivirus program. By placing a potentially dangerous program into a controlled virtualized environment where it can’t cause any harm, security software can analyze the behavior of suspicious code and develop protection against it.
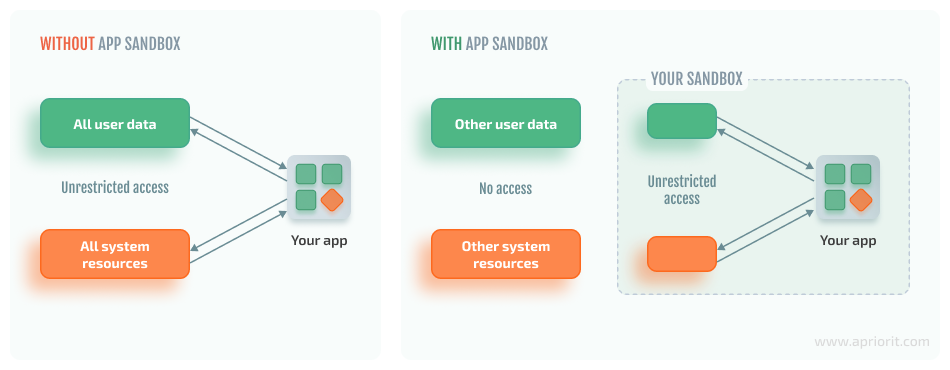
Though sandboxing technology has been considered effective, cybercriminals are now applying techniques that let malware evade sandbox analysis.
Sandbox-evading malware can recognize if it’s inside a sandbox or virtual machine environment. Such malware infections don’t execute their malicious code until they’re outside of the controlled environment. To hide threats, malware can use anti sandbox techniques like:
- Encryption
- Environment scanners
- User activity monitoring
- Artificial intelligence (AI) algorithms
- Etc.
We’ll discuss evasion techniques later in this article. For now, let’s look at a couple examples of sandbox-evading malware to understand the severity and possible consequences of such threats.
Stay one step ahead of cyber attackers with our cybersecurity services
Take proactive steps to secure your business and let our team of experts protect your products.
Real-world examples of sandbox-evading malware
Sandbox evasion is an extremely common attack technique, and cybersecurity accidents caused by malware with evading capabilities often get in the news.
For example, the information-stealing malware Beep, discovered in 2023, uses 17 evasion techniques to stay undetected by a victim’s cybersecurity system. This malware can obfuscate and deobfuscate malicious code, detect if it’s being traced, turn off debuggers, hide its API functions, and more. At the time of discovery, Beep was still under development, so it’s possible that this malware now has even more sandbox-evading capabilities.
Another recently discovered malware, Batloader, also has a lot of anti-sandbox capabilities. It can stop security software services, avoid activity of antivirus solutions, and mask itself as a legitimate file.
The majority of sandbox-evading malware doesn’t get on the news or become the focus of prominent cybersecurity research simply because there are so many types of malware out there. Malicious actors can use popular technologies like Python, automated code generation, and AI algorithms to quickly develop malware with evasion capabilities. It’s even possible to convince ChatGPT to write evasive malware for you.
There are dozens of sandbox-evading techniques that can be embedded in malware. Let’s look closer at how these techniques work to hide malware from cybersecurity solutions.
Most common sandbox evasion techniques
MITRE ATT&CK, a well-known knowledgebase of cybersecurity attacks, defines three key malware sandbox evasion techniques. Let’s examine how they work:
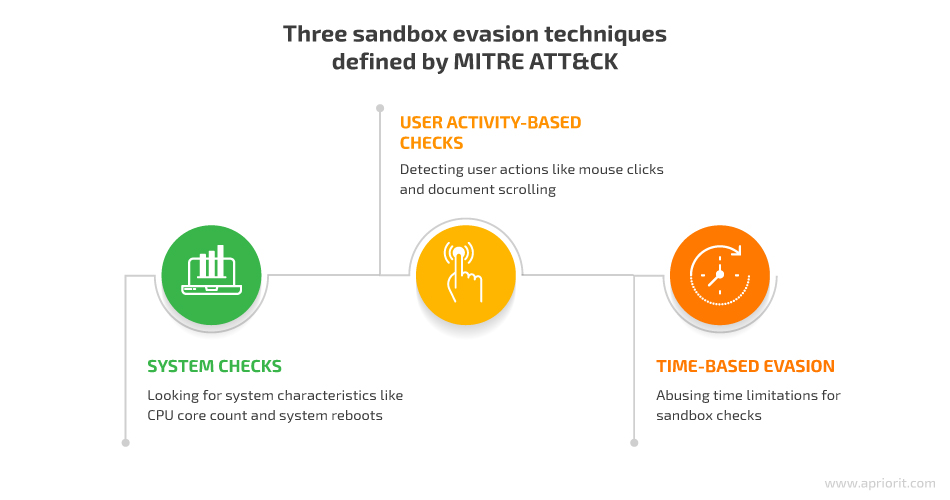
1. System checks
Sandbox-evading malware can be programmed to identify some features of a real system that aren’t available in a sandbox or virtual environment.
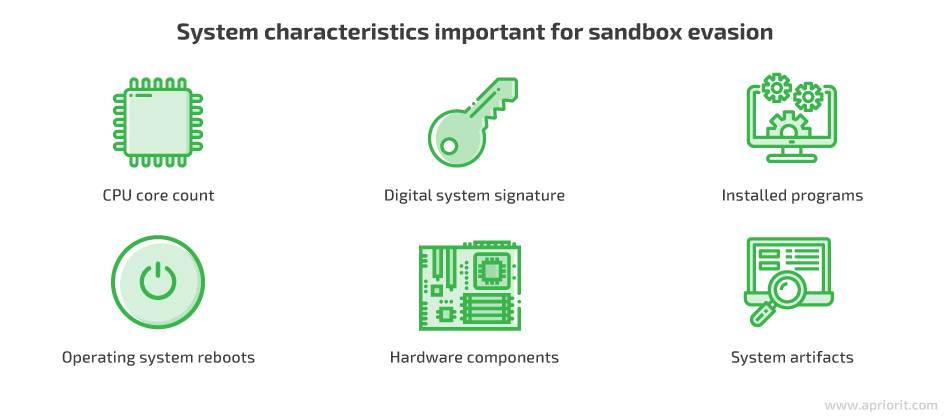
Here’s how malware can use system information to get out of a sandbox:
- СPU core count and hardware components. Malware can find discrepancies between virtual and physical systems, such as the number of CPU cores, and use it for sandbox detection. This is why many sandbox vendors hide their actual configurations so hackers are unable to detect sandbox specifications.
- Digital system signature. Some malware is designed to find a system’s digital signature, which contains information about the computer’s configuration.
- Installed programs. This technique allows the malware to check for the presence of antivirus programs by looking for active processes in the operating system.
- Operating system reboots. Some sandboxes can’t survive operating system reboots, so malware can be programmed to activate only after a reboot. Though the virtual environment may try to emulate a reboot by logging the user in and out, malware can detect this, as not all reboot triggers are executed.
- System artifacts. A virtual machine contains specific artifacts in its memory, processes, and files. Malware can look for artifacts like virtual machine (VM) instructions and communication with I/O ports to detect whether it’s launched inside a sandbox.
Read also
Remote Browser Isolation — The Next Step in Endpoint Security?
Discover how you can protect your organization’s remote assets with remote browser isolation (RBI), which can safeguard organizations against browser-based attacks.
2. User activity-based checks
Users interact with computers in different ways, but there are no human-like interactions in the sandbox environment. Thus, hackers can teach malware to wait for a specific user action and exhibit malicious behavior only afterward. Here are some examples of sandbox detection techniques that rely on user actions:
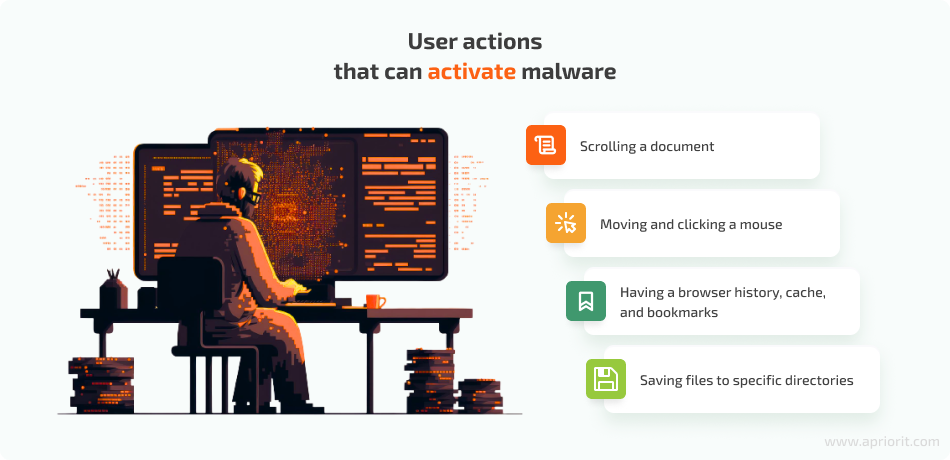
- Scrolling a document. Modern malware can be programmed to execute only after a user reaches a particular place in a document. Malware written in Microsoft Word documents may contain special paragraph codes to detect scrolling. The sandbox environment doesn’t contain any scroll movements, allowing the malware to stay dormant.
- Moving and clicking a mouse. Some malware is programmed to check the speed of mouse movements and clicks and remain inactive if the speed is suspiciously fast, it doesn’t detect enough mouse clicks, or the user doesn’t take a particular action.
- Having a browser history, cache, and bookmarks. A real user that surfs the internet daily will have their history and cache saved on their machine. A sandbox will have none of that because it regularly cleans the browsing cache to delete potential malware and ensure the correct operation of the sandbox. Malware can check whether a system has such information and lay dormant if it doesn’t find anything.
- Saving files to specific directories. Malware can check whether a system allows for saving custom files to the desktop and the root folder. It’s not recommended to save your files in these directories, so a sandbox wouldn’t do that. But the majority of real users save their files to the desktop and root despite system recommendations.
3. Time-based evasion
In some cases, malware evades the sandbox using timing-based techniques. Sandboxes usually analyze malware for a limited period of time, and timing-based techniques gladly abuse this feature.
Here are three common types of sandbox detection methods based on time:
- Extended sleep. When malware uses extended sleep, it can successfully leave the sandbox before execution.
- Logic bomb. In some cases, malware can be programmed to execute on a particular date and at a particular time.
- Stalling code. Malware can contain code that executes useless CPU cycles to delay malicious code execution until the sandbox has finished testing.
Additional sandbox evasion mechanisms
When developing malware, malicious actors try implementing as many evasion techniques and mechanisms as possible to ensure the success of their code. Here are key additional mechanisms they use to enhance the techniques discussed above:
- Encryption and obfuscation. Encrypted malware usually contains a decryption loop and a main body. The decryption loop encrypts and decrypts the main body, which contains the malicious code.
- Changes to IP addresses and DNS names. This mechanism helps malware hide phishing and malware delivery addresses. It allows malware to bypass the website blacklists that security solutions create.
- Steganography and polyglots. These types of malware hide malicious code in passive parts of code like images. It’s possible to place code both in an image’s metadata and within the image itself. This method of evasion is especially useful for browser-based exploits.
- Oligomorphism, polymorphism, metamorphism. Malware can tamper with its decryptors to make it harder for a sandbox to detect malicious code. For example, it can create new decryptors for each infection and type of code (oligomorphism), modify malware code slightly for every new decryptor (polymorphism), or use a mutation engine to modify malicious code depending on the properties of a sandbox (metamorphism).
- Packet fragmentation. Security solutions usually wait for the whole traffic packet to arrive and then analyze it. Malware can take advantage of this packet fragmentation protocol and send malicious code only as part of a packet.
This variety of sandbox evasion techniques and mechanisms makes containing malware in a secure environment a tricky task. At Apriorit, we can solve this challenge in several ways depending on the nature of the solution. Let’s take a look at some of the best practices we use to ensure malware containment.
Read also
Improving Code Quality with Static Code Analysis Using SonarQube: A Practical Guide
Let us help you ensure top-notch product quality through effective code quality assurance practices. Explore our knowledge about continuous code quality assurance in software development and learn how SonarQube can enhance your QA strategy.
Best practices for developing a reliable sandbox
The evasion techniques we’ve described can provide developers with a deeper understanding of malware detection in a sandbox. That’s why we at Apriorit combine a variety of cybersecurity checks and defenses when developing a sandbox. Here are some principles you can implement in your security solution to protect it from sandbox-evading malware:
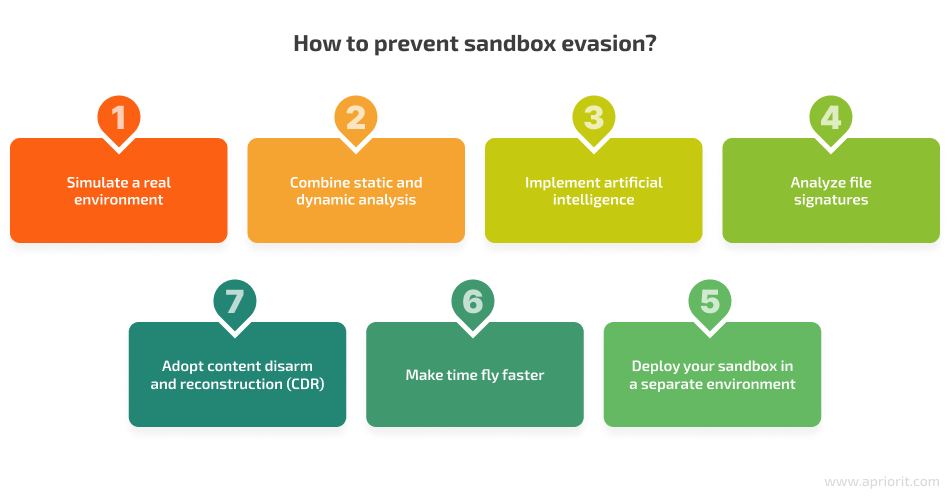
1. Simulate a real environment
A virtual machine operates differently compared to a real environment with real users. Modern malware can pick up differences, like infrequent reboots and VM-specific instructions, as well as detect fake mouse clicks and movements. Retrieving hardware information in your sandbox will help you detect malware that checks for hard disk size, recent files, the number of CPU cores, operating system version, memory capacity, and other system and hardware characteristics.
You can also configure your sandbox to dynamically change the sleep duration and the period of malware analysis. While a sandbox usually analyzes malware for seconds, a prolonged analysis significantly increases the chances of detecting malware with an increased sleep duration. Note that this approach to malware detection requires a lot of time.
2. Combine static and dynamic analysis
Sandboxing technology is a form of dynamic code analysis, as it examines malware behavior in a safe environment. Knowing that, many malware developers try evading dynamic analysis by putting their code to sleep or making it take as few actions as possible.
To detect such malware, add static code analysis to your sandbox. Static analysis checks potential malware for evasion techniques or encrypted pieces of code with no regard to file activities. This method is effective for detecting malware with scripts for delayed execution. However, you can’t rely solely on static analysis to stop malware.
3. Implement artificial intelligence
AI algorithms can improve the accuracy of sandboxing and detect more threats before they are executed. In contrast to traditional rule-based cybersecurity mechanisms, artificial intelligence can learn to detect zero-day threats, adjust to new evasion techniques, and identify malware based on its early actions.
You can add cybersecurity-focused AI algorithms that:
- Simulate real user behavior to make malware think it’s outside of a sandbox
- Analyze the behavior of potentially malicious files
- Enhance static and dynamic analysis
4. Analyze file signatures
Signature-based detection analyzes the unique digital footprint, or signature, of each piece of software that gets into the system. Each antivirus solution has a built-in database of known malware signatures. If a signature of new software matches a record in this database, the sandbox automatically deletes or quarantines the software.
However, a signature check can’t stop dynamically changing malware. To detect such threats, consider implementing calculation of cyclic redundancy check. Checksumming helps verify that files under analysis haven’t changed from the time they entered the system.
5. Adopt content disarm and reconstruction technology
Content disarm and reconstruction (CDR) is a cybersecurity technology that deletes any suspicious code from files. To determine that code is suspicious, CDR uses system policies and definitions. This technology is often considered the opposite of sandboxing, but it may serve as an add-on to other security solutions.
CDR removes all active content from a file and provides the user with a sanitized document. It allows you to instantly prevent malware hidden in documents, yet there’s a risk of corrupting files containing scripts (such as Office macros written in JavaScript) even though they’re not malicious.
6. Make time fly faster
Delaying execution of malicious code is one of the basic evasion tactics for malware. A sandbox isn’t active 24/7, so even the simplest malware can evade security checks by putting itself to sleep for several hours. Because of that, when a sandbox becomes active, it can mistake a malicious file for a safe one.
One way to detect time-evading malware is to change time configurations of your VM when a sandbox becomes active. This way, you’ll be able to trick malware into waking up and executing its malicious code. Another option is to make time go faster inside the VM and simply wait out the malware’s sleeping period.
7. Deploy your sandbox in a separate environment
Even the most secure sandbox might break at some point and let malware into your environment. To prevent this from happening, deploy your sandbox in an environment separate from your main one. For example, you can use a cloud deployment, remote endpoints with restricted access, or another virtual machine.
Related project
Improving a SaaS Cybersecurity Platform with Competitive Features and Quality Maintenance
Explore our success story of collaboration with a worldwide provider of SaaS-based cybersecurity platform. Our dedicated specialists enhanced their product’s feature set, stability, and user experience.

Conclusion
Sandbox-evading malware is designed to avoid detection by protection programs based on sandboxing technology. This means that traditional approaches for malware detection aren’t effective against such malware. To develop a sandbox that can detect and stop malware, you need to combine various cybersecurity techniques, approaches, and tools.
During our 20+ years of work in the cybersecurity market, the Apriorit team of security experts has delivered dozens of solutions with sandboxing functionality. Depending on the needs of your product, we can use Python, AI algorithms, reverse engineering skills, virtualization techniques, and many other tools and technologies to develop a secure and fitting sandbox.
Ready to protect your business from cyber threats?
Partner with us to strengthen your defenses and maintain the integrity of your systems!



