Ensuring secure communication over the internet is becoming harder for developers as new security solutions are limited in their sources of entropy. So how can developers increase the security of their encryption to protect user data? Entropy as a Service can be a good answer, and here’s why.
In this article, we discuss what entropy is in encryption and why it is worth your attention. This article will be helpful for developers who want to know how to use entropy in security projects.
Contents:
What is entropy?
In computing, entropy is a measure of the randomness or unpredictability of information that’s collected by an operating system or application to use in generating cryptographic keys that require random data. When a high level of entropy is used for encryption, user data can be securely protected against attacks both in transit over the network and at rest on storage devices.
Traditional computing systems look to human interactions with machines such as mouse movements, network activities, and keyboard entries for entropy. Unpredictable data based on software entropy is then transformed into random numbers and used for cryptographic needs.
But in addition to traditional computers, people use a wide range of other devices and systems with access to the internet. Thus, there’s increasing demand for random data to mitigate embedded systems vulnerabilities, as well as security issues in cloud computing environments and Internet of Things (IoT) devices. In contrast, cloud-based systems and innovative devices are limited in their interactions with users, so they are unable to produce software-based entropy that’s strong enough for cryptographic needs. Let’s explore entropy security in detail in the next section.
Why is entropy so important?
Before 2012, hardly anyone thought about problems with software-based entropy. Then a group of researchers from the University of California, San Diego, and the University of Michigan found that RSA and DSA no longer produced secure keys. During their study, the researchers investigated the security of the public keys used in internet devices like firewalls and routers. The results revealed that most SSH and TLS servers contained easily guessed public keys. Additionally, the researchers were extremely surprised to discover that 10 percent of SSH and 5 percent of HTTPS keys were duplicates.
The reason for this is that internet-connected devices are resource-constrained and are also limited in their interactions with users. IoT devices were developed based on the assumption that entropy generated with software was enough for cryptography, but this approach appears to be ineffective. As you can see from our article on IoT security challenges, IoT devices with guessable cryptographic keys can be easily converted from useful assets into spying tools.
In addition, cloud-based systems don’t interact with user hardware. Instead, cloud service providers use a single golden image of a guest virtual machine and create multiple instances of it in response to user demand. However, these instances have a very limited ability to generate entropy. Thus, cloud computing is becoming an attractive vector for cyber attacks too.
Consequently, finding a reliable source of true entropy has become a real headache for developers. While there’s an increasing deficiency in high-quality entropy, the traditional software approach for entropy generation fails when applied to modern computing systems. Though experts recommend generating cryptographic keys with deterministic random bit generators, there’s a risk that initial values or seeds supplied to these generators for key development can be easily traced and compromised by cyber criminals.
One possible solution to this problem is finding external sources of entropy that can be securely shared by multiple applications in production environments.
Entropy as a Service
Taking into account the increasing demand for random data, the United States’ National Institute of Standards and Technology (NIST) has proposed developing a new service for providing high-quality entropy to application and device developers: Entropy as a Service.
What is Entropy as a Service (EaaS)?
EaaS is an innovative internet service designed to provide high-quality sources of entropy to IoT devices, embedded systems, and cloud service providers. These sources of entropy are based on physical processes of ring oscillators or quantum devices that can provide true randomness. Developers can use EaaS for seeding their applications or devices with high-quality entropy and be sure that their products are strongly protected against cyberattacks.
Read also:
How to Ensure Chat Security with OpenSSL
NIST’s EaaS architecture
NIST offers a secure method of providing seeds for random number generators (RNGs) that are built into devices and applications. NIST recommends that developers configure their applications and devices to send HTTP GET requests for the necessary number of bytes of random data to an Entropy as a Service server and receive freshly generated random data using a related Entropy as a Service protocol. According to NIST, an EaaS system should have the following components:
- A quantum entropy device
- An EaaS server
- A hardware root of trust device in the client’s system
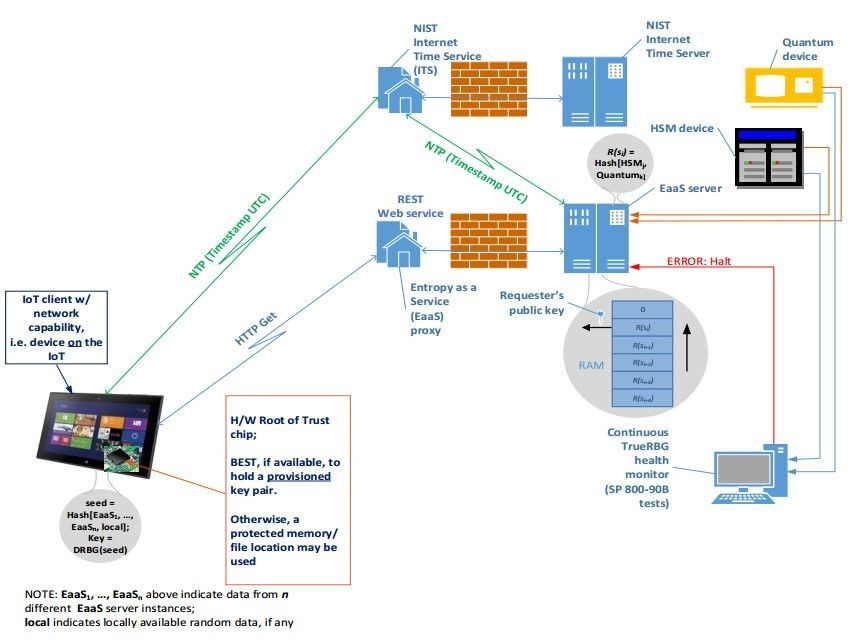
NIST’s EaaS architecture
An EaaS server continuously receives entropy from the attached quantum device and stores it securely. When it gets a request from a client system, the server signs and encrypts its fresh random data before sending it to the requester. The freshness of data is confirmed with a UTC timestamp that can be verified by the client by comparing it with the local machine’s time. The digital signature ensures the authenticity and origin of the seed. Moreover, the encryption of random data is performed with a unique public key specific to each client and with the server’s own private key.
The client system should have a classic computing device with a secure hardware component for storing cryptographic keys and seeds (for instance TPM, Intel IPT, or ARM TrustZone). In addition, it also should be equipped with application software that ensures communication between the EaaS server and the client’s hardware component. It’s not obligatory for the client system or device to have dedicated hardware, but its availability will make seed storage more secure.
An EaaS server doesn’t provide cryptographic keys to its clients; it only supplies the client’s RNG with unique seeds in a secure fashion. But you don’t need to trust just one EaaS provider; NIST recommends seeding applications with responses from multiple EaaS servers. EaaS architecture is scalable and can include thousands of EaaS servers across the world, which is important for establishing collective authority and keeping the architecture open and viewable by experts.
To ensure perfect forward secrecy, developers can mix random data obtained from an EaaS server with locally-produced pseudo-random data (using hashing) or with data received from another EaaS server.
EaaS providers
There are an increasing number of examples of successful Entropy as a Service solutions on the market. For instance, Whitewood, an American developer of crypto-security solutions, offers its free Entropy as a Service solution for on-site software as well as paid options for a perpetual license or consumption-based model. Whitewood has created netRandom software that receives random data from an entropy engine and supplies operating systems, IoT devices, and virtual machines with unique seed material.
Crypto4A, a Canadian cybersecurity company, also implements all of NIST’s recommendations in its quantum-ready solution. This Entropy as a Service provider uses a specially developed hardware security module for implementing multiple entropy sources and feeding a NIST SP-800-90 random number generator design with quantum-based data. Their module ensures the necessary level of cryptographic confidentiality and service authenticity for the company’s clients.
Quintessence Labs, an Australian-based security company, is now rigorously testing their qStream product that provides quantum-generated entropy at a high speed for pseudo random number generators. The company has developed an effective entropy management system that’s compliant with KMIP and FIPS 140-2 level 3.
Read also:
Security Attacks on Cloud Computing
Benefits of EaaS for developers
EaaS is highly beneficial for application and device developers, who no longer need to break their necks over finding their own secure entropy sources. Instead, they can launch their products faster and be sure that devices and applications will securely protect user data. EaaS lets new products access true entropy from an internet-based architecture. This approach allows developers to always keep their products updated with true entropy for generating the strongest cryptography and be sure that their solutions can withstand modern cyber attacks.
Moreover, Entropy as a Service solutions can also be useful for enterprises in assessing the security of their corporate systems. With the help of EaaS, companies can attest to the strength of keys generated from data coming from their software-based resources. In addition, businesses can also use EaaS to get entropy for their endpoints if they want to be completely sure that their databases are protected.
As for the use of entropy in cloud environments, EaaS can help avoid cases when two virtual machine instances created from a common golden image duplicate their local entropy pool. To avoid this, the image, after cloning, just needs to request fresh random data from the EaaS server on boot.
Conclusion
Entropy as a Service is a new cloud-based service that allows developers to get the high-quality entropy necessary for strong encryption of user data. This service fills the need for cloud-based applications and embedded and IoT devices. Using entropy in cryptography is a sure way to enhance your solutions. While EaaS doesn’t generate cryptographic keys, it provides unique seeds for random number generators in a secure manner.
At Apriorit, we always use strong encryption to protect our clients’ sensitive data, and that includes using strong sources of entropy. If you need a development team with extensive expertise in using entropy in cybersecurity, send us your request for a proposal.




