Microsoft Azure is the second most popular cloud platform in the world after Amazon Web Services according to the RightScale 2019 State of the Cloud Report by Flexera. And it keeps gaining in popularity. This makes Microsoft Azure a popular target for hackers, which is why you need to pay special attention to the security of your Azure environment.
Though Microsoft has high security standards and prioritizes the protection of customer data, tuning the default defense system according to your needs makes it even more secure. To make sure your Microsoft Azure environment is secure enough, you need to conduct periodic audits.
In this article, we share our experience auditing nine of the most common Microsoft Azure services and elements. This post will be useful for developers and testers who are looking for ways to ensure data security in their Azure environments.
Contents:
The key advantages of Microsoft Azure are its scalability, flexibility, vast number of tools, and geographical presence. Azure offers more than 100 services in 54 regions around the globe. This variety allows users to create and manage almost any application. But as with any cloud solution, you need to keep the security of your data in mind.
In this article, you’ll find tips on how to improve your Microsoft Azure security posture with regular audits. We’ll cover the most common Microsoft Azure services and the mistakes that make the Azure environment especially vulnerable. We’ll also provide you with general recommendations for establishing a secure Azure configuration based on security best practices.
For convenience, we’ve divided these recommendations into two levels.
The first level includes recommendations that are prudent and practical, and that provide a clear safety advantage. They’re easy to implement, as they don’t require additional technology.
The second level includes recommendations for environments or use cases where security is critical. They provide an in-depth defense, but they may harm performance.
We’ll discuss how to improve the security of the following Microsoft Azure services:
- Identity and access management (IAM)
- Storage
- SQL Database services
- Network security
- Network logging and monitoring
- Virtual Machines
- Security center
- Key Vault
- App Service Environment

Need to improve the security of your cloud infrastructure?
Get an in-depth security audit and practical steps to improve your protection from Apriorit specialists.
Azure identity and access management
Identity and access management (IAM) is a set of authorization and authentication procedures for security principals – services, applications, users, groups, etc.
Establishing a secure identity and access management policies is the first step to protecting your Azure environment.
IAM helps you protect access to applications and resources located both on-premises and in the cloud. Azure IAM provides additional levels of validation such as multi-factor authentication and conditional access policies.
But simply following the basic IAM protection instructions won’t guarantee the complete security of IAM in your Azure environment. Let’s look at the two levels of recommendations for auditing your Azure IAM.
Level 1
- Don’t create custom subscription owner roles in the environment.
- Enable multi-factor authentication for all users with privileged roles: co-administrators, owners, contributors, etc.
- Don’t create guest users unless there’s an urgent need.
Level 2
- Enable multi-factor authentication for all users with non-privileged roles.
- Forbid users to autofill multi-factor authentication passwords on their devices.
- Send an email notification to users if their password is reset.
- Deny non-administrators access to the Azure Active Directory (AD) administrative portal, as it has confidential data.
- Deny the creation of custom owner roles with subscription ownership.
- Allow only administrators to create security groups and invite other users and to access the Azure AD administration portal.
- Allow only administrators to create self-service groups. Self-service group management enables users to create and manage security groups in Azure AD.
- Unless a project requires day-to-day delegation for some users, disable self-service group management.
Azure Storage
Azure Storage provides durable, scalable, and available cloud storage for applications and resources. Gaining access to this service requires creating a unique namespace for an account. When it comes to securing your Azure Storage account, there are a lot of embedded features: restricting access with role-based access control (RBAC) or Azure Active Directory, securing data with client-side encryption, HTTPS, SMB 3.0, etc.
Here’s how to audit the security of Azure Storage:
Level 1
- Encrypt data in transit. You can increase the security of your storage account by enabling the secure transfer option so that only requests with a secure connection will be accepted. With secure transfer enabled, you can access your Azure Storage using the HTTPS protocol. Any request using HTTP will be rejected.
- Disable anonymous access to Azure Blob containers unless it’s absolutely necessary.
- Disable the default network access rules for storage accounts. This option provides an additional level of security since by default storage accounts accept connections from clients on any network.
Level 2
- Regenerate storage account access keys regularly. Circular shifting of these keys ensures that any unintentional access or exposure doesn’t compromise them.
- Enable logging storage analytics. Data on successful and failed requests to the Azure Storage service is useful for monitoring individual requests and diagnosing issues with your storage service.
Related project
Improving a SaaS Cybersecurity Platform with Competitive Features and Quality Maintenance
Examine how Apriorit’s experts helped the client enrich stability and competitiveness of their SaaS cybersecurity platform. Unveil the details of how our development efforts helped the client enhance the software and improve user experience.

Azure SQL Database
Azure SQL Database is based on the Microsoft SQL Server Database Engine. It provides users with a fully managed scalable PaaS database. The connection to it is secured with firewall rules and connection encryption. Authentication is provided by creating user credentials and using Azure AD. Authorization is provided with the help of RBAC.
A lot of administrators disable audits and all types of threat detection on SQL servers. But these actions leave the Azure SQL Database vulnerable to cyber attacks. These are our key recommendations for setting up general database services policies:
- Audit SQL servers. This allows you to monitor Azure SQL Database events and log them into the Azure Storage profile. This information is useful for gaining a deeper understanding of the processes inside a database, tracking anomalies, and detecting vulnerabilities.
- Enable all types of threat detection on SQL servers. This helps to prevent SQL injection, database vulnerabilities, and abnormal user activity.
- Allow service admins and co-admins to receive security alerts from the SQL server. An email alert is one of the fastest ways to report suspicious activity, reducing risk.
- Encrypt transparent data on every SQL server. This protects data by performing real-time encryption and decryption of the database, associated backups, and transaction log files at rest.
- Enable SSL connections. SSL connections between a database server and client applications encrypt the data stream to protect against man-in-the-middle attacks.
Azure network security
Network security protects the network from unauthorized access. Azure networking infrastructure supports your application and service connectivity requirements. Network connectivity is possible between:
- Resources located in Azure
- On-premises and Azure-hosted resources
- External resources and Azure
While creating networking policies for Azure, always remember to:
- Deny direct RDP and SSH access from the internet to your network security groups. The risk of attackers gaining unauthorized access to Azure virtual machines (VMs) with RDP or SSH is one of the main security concerns with Azure. Once attackers access a VM, they can use it as a launch point for compromising other machines in the Azure Virtual Network or even attacking external devices connected to the Azure network. To securely control your VMs remotely, you can use other features such as Point-to-site VPN, Site-to-site VPN, and ExpressRoute.
- Disable access from 0.0.0.0/0 (any IP) for Azure SQL Databases. By default, the firewall for an Azure SQL server has Start IP and End IP of 0.0.0.0, allowing any IP to access all Azure services. Define firewall rules with a narrower range of IP addresses within the range available from specific data centers to reduce the chance of an attack.
- Enable Network Watcher for Azure subscriptions. This helps with monitoring, diagnosing, and logging issues in an Azure private network.
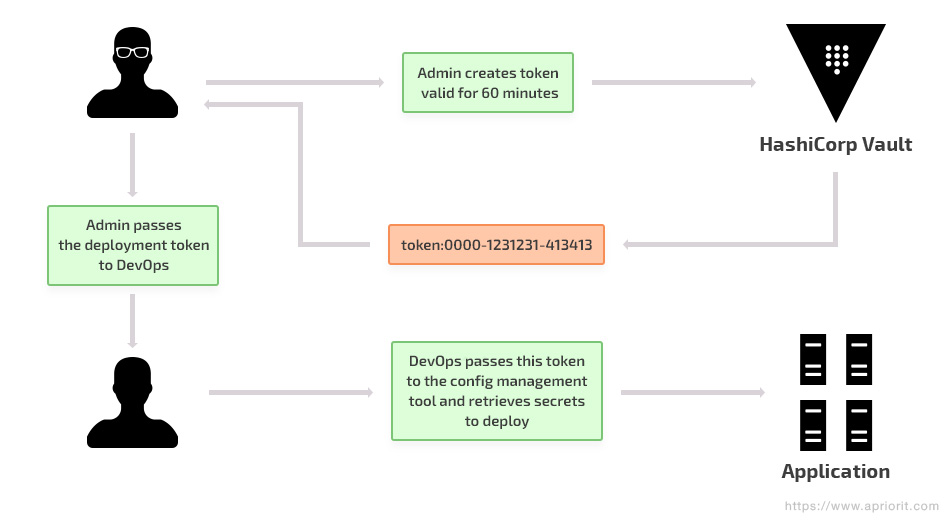
Additionally, Microsoft Azure provides a couple of tools that are useful for securing network connections: Azure VPN Gateway and ExpressRoute. Let’s look closer at each of them.
Azure VPN Gateway enables you to establish secure, cross-premises connections between your virtual network within Azure and on-premises IT infrastructure. Setting up a virtual network with the Azure VPN Gateway is free, but you have to pay for the VPN gateway that connects to on-premises networks and other virtual networks in Azure. The price depends on the amount of time for which the gateway is provisioned and available.
ExpressRoute helps you create private connections between Azure datacenters and on-premises or co-located infrastructure. ExpressRoute offers a more reliable, faster, lower latency, and more secure connection than over the public internet.
Read also
Releasing a Multi-part Client-Server Application on Azure Marketplace: How-to Guide with Examples
Gain practical insights into publishing on Azure Marketplace, including creating ARM templates, configuring scripts with DSC, and testing applications with TTK.

Logging and monitoring the Azure network
A wide range of Azure security auditing and logging options serve to detect weaknesses in your cybersecurity system.
Logs are a great help when it comes to fixing detected issues and preventing potential ones. Using data from logs, you can improve application efficiency and maintainability or create alerts to get information on issues occurring in real time.
There are three categories of Azure logs:
- Control and management logs help you find information about the Create, Update, and Delete operations of the Azure Resource Manager.
- Data plane logs collect information about events that used Azure resources; these logs include Windows event system, security, and application logs on a virtual machine and diagnostics logs configured with Azure Monitor.
- Processed events logs keep data on analyzed events or Azure Security Center alerts triggered by a user. Available alerts differ depending on the Azure subscription type.
Configuring a log profile
The Azure activity log collects data on control and management activities performed within an account. The log profile defines the type of events, both past and real-time. It also defines output data from the storage account container. When properly configured, the log profile ensures that all activity logs keep data for a longer period than by default. In order to achieve this, apply the following settings:
- Configure the log profile to export activity logs. Azure Portal stores activity logs for 90 days by default. Set the storage period for activity logs to 365 days or longer. A log profile controls how the activity log is exported and retained.
- Configure log profiles to export all activities from the control and management plane and supported regions or locations, including global.
- Deny public access to a storage account container with the activity log export. Allowing access may help a hacker to identify weaknesses in the affected account’s use or configuration.
Monitoring with activity log alerts
Setting alerts and monitoring for critical activities in an Azure account helps you monitor network access changes and may reduce the time needed to detect suspicious activity.
To set up monitoring, follow these instructions:
- Create an activity log alert for the Create Policy Assignment event. The log collects data on changes in Azure policy assignments. This alert may reduce the time it takes to detect undesired changes.
- Create an activity log alert for Create, Update, and Delete events for:
- Network Security Group
- Network Security Group Rule
- SQL Server Firewall Rule
- SQL Server Firewall Rule
Related project
Building AWS-based Blockchain Infrastructure for International Banking
Discover how we built cloud-based blockchain infrastructure for a US-based company which they successfully pitched to banking and government clients.

Azure Virtual Machines
An Azure Virtual Machine (VM) allows you to virtualize a wide range of software, environments, and specifications without having to buy and maintain the physical hardware that runs it. However, you still need to install, configure, and patch the software on your VM.
There are many Azure services and features that help you protect your VMs by securing access to your virtual machines and data storage.
Our tips for securing Azure VMs:
Level 1
- Encrypt operating system (OS) disks (boot volumes) and data disks (non-boot volumes) if possible. This makes the entire contents of a volume unreadable without a key and thus protects it from unauthorized access.
- Encrypt unattached disks. Even if a disk isn’t attached to any VM, there’s always a risk of sensitive information being disclosed or tampered with. For example, a compromised user account with administrative access to the VM service can mount or attach these data disks.
Level 2
- Install only organization-approved extensions on VMs.
- Apply the latest operating system patches for all VMs.
- Install endpoint protection on all VMs for real-time protection.
Azure Security Center
The Azure Security Center is developed to strengthen the security of your data centers and protect your hybrid workloads in the cloud — whether or not they’re in Azure — as well as on-premises.
Here’s a set of recommendations for auditing the security of this functionality:
- Prioritize responses by assessing your security posture with Azure Security Center using the “Quickly assess your security posture with Secure Center” feature, which provides recommendations with numeric values.
- Authorize automatic provisioning of the monitoring agent to collect security data. When this feature is enabled, the Microsoft Monitoring Agent automatically scans an environment for various security-related configurations and events such as system updates, operating system vulnerabilities, and endpoint protection and provides alerts.
- Enable system update recommendations for VMs so they get a daily list of available security updates and critical updates from Windows Update or Windows Server Update Services.
- Enable OS vulnerability recommendations to monitor your VM. This allows you to analyze operating system configurations daily in order to identify issues that could make a virtual machine vulnerable.
- Enable endpoint protection recommendations for a VM. This helps all Windows virtual machines identify and remove viruses, spyware, and other malicious software.
- Enable disk encryption recommendations for VMs. Encrypting the disk in all VMs (Windows and Linux) helps to strengthen the protection of data at rest.
- Enable storage encryption recommendations. This allows you to cipher any new data in Azure Blobs and files.
- Enable SQL auditing recommendations. Access audits of Azure SQL databases should be enabled for compliance, advanced threat detection, and investigation purposes.
- Enable SQL encryption recommendations. Enabling this setting allows encrypting data at rest in the Azure SQL Database, associated backups, and transaction log files. This way in the event of a data breach, an attacker will not be able to read your data.
- Provide security contact email and phone number. Microsoft will contact your security team in case their specialists find out the organization’s resources have been compromised.
Note that in case a security violation is detected, the majority of the recommendations in this section only produce an alert. You’ll need to enforce the security settings yourself.
Azure Key Vault
Azure Key Vault is a service for secure key storage and management. It allows for creating, encrypting, importing, and changing encryption keys and secrets stored in hardware security modules within the Microsoft Azure environment.
There are several security tips to strengthen Key Vault protection.
Level 1
Set an expiration time for all keys and secrets in the Azure Key Vault. By default, they never expire, which is why we recommend rotating the key and secrets as well as setting an explicit expiration time for all keys and secrets.
Level 2
Set resource locks for mission-critical Azure resources. With Resource Manager locks, administrators can lock down Azure resources to prevent unwanted changes to them. These locks exist outside the RBAC hierarchy and, when applied, place restrictions on the resource for all users. They’re useful when an administrator wants to protect an important resource that other users should not be allowed to change or delete.
Azure App Service Environment
The Azure App Service Environment provides fully isolated and dedicated surroundings for safely running app services on a large scale. This feature can host your Windows and Linux web apps, Docker containers, and mobile apps.
Best practices for securing the Azure App Service:
Level 1
- Enable App Service authentication. This feature can prevent anonymous HTTP requests from entering the API or authenticate them with tokens.
When you enable this feature, every incoming HTTP request passes through App Service authentication before being handled by the application. It also manages:
- authentication of users with the defined provider validation (Azure Active Directory, Google, Facebook, Microsoft Account, Twitter)
- storage and validation
- updating of tokens
- authenticated sessions and injection of identity information into request headers
- Configure your web application to redirect HTTP traffic to HTTPS. HTTPS provides a better level of security using the SSL/TLS protocol to allow for authenticated and encrypted connections.
- Use web apps with the latest TLS encryption. Some outdated cryptographic protocols have critical vulnerabilities, such as POODLE and Heartbleed.
Level 2
Use the newest versions of the .NET framework, PHP, Python, and Java, if used as a part of the web application. Support of the outdated version may be problematic because updating one of the components can lead to compatibility issues.
Conclusion
A security audit of your Azure environment should be a priority for enterprises during all phases of the system development life cycle. Our experience with Microsoft Azure shows that it’s best to conduct periodic audits of the Azure environment to ensure it’s configured securely. Such audits will help you do the following:
- Reduce the risk of hacking attacks and data breaches
- Increase visibility into your network
- Provide data for investigating cybersecurity incidents
- Respond to cybersecurity incidents effectively
In this article, we talked about auditing the most popular elements of the Microsoft Azure environment. To get a deeper understanding of this topic or ensure thorough security testing of your own Azure project, feel free to contact our team!
Prove security and reliability of your software
Reach out to get yourself a comprehensive and honest security audit of your solution to discover vulnerabilities and receive helpful and practical advice on how to fix them.




