Key takeaways:
- Healthcare software faces unique cybersecurity risks due to IoT device integration, legacy systems, accumulation of sensitive patient data, and other factors.
- Beyond that, healthcare software needs to comply with industry regulations, cybersecurity standards, and local laws.
- Cyber attacks in healthcare can disrupt critical services, compromise protected health information (PHI), and lead to severe regulatory and financial consequences.
- Implementing proactive security practices, such as secure development, regular testing, and strong access controls, can help mitigate risks.
Since healthcare environments are highly connected, a single breach can compromise sensitive records, disrupt life-critical systems, violate regulatory requirements, and erode patient trust. And cybercriminals are acutely aware of the value of healthcare data and the operational urgency of the industry.
In this article, you will gain a clear understanding of the biggest cybersecurity threats in healthcare software today. You will also find proactive strategies for mitigating them during the software development lifecycle.
This article will be suitable for those who are responsible for managing patient data and securing healthcare systems.
Contents:
Why does healthcare demand higher cybersecurity standards?
Healthcare software is a rather broad category of digital tools that are designed to support medical care delivery, streamline operations, and improve patient outcomes. These solutions can include:
- Electronic health record (EHR) systems
- Medical IoT device interfaces
- Telemedicine platforms
- Clinical decision support tools
- Patient portals
- Billing systems
- And more
Such software improves care quality, accessibility, and operational efficiency, but it also expands the digital attack surface and exposes healthcare organizations to evolving cybersecurity threats.
Unlike other types of business software, healthcare solutions manage life-critical operations and store extremely sensitive data. Any downtime, data breach, or system compromise doesn’t just disrupt workflows. It can directly impact patient safety, delay urgent care, or expose confidential health information. This makes cybersecurity in healthcare software more than just a precaution — it’s a necessity.
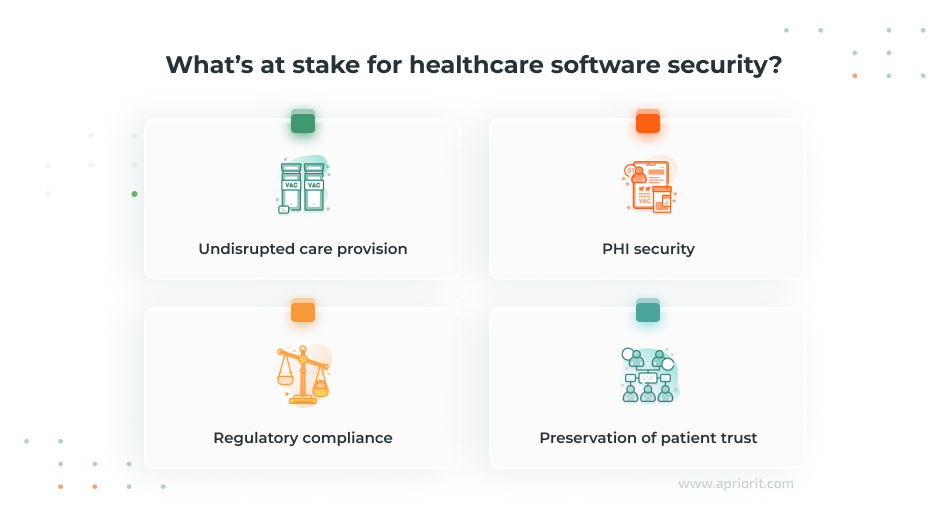
Undisrupted care provision. Healthcare software often controls systems that are essential for life-critical operations such as diagnosing, monitoring, and treating patients. A cyber attack could interrupt a pacemaker’s monitoring feed or delay a surgery by locking down surgical scheduling software. Maintaining operational continuity is vital, as any downtime could cost lives or worsen patients’ quality of life.
PHI security. Protected health information (PHI) includes any data that can identify a patient, such as names, birth dates, medical histories, diagnoses, test results, and insurance details. This is why PHI is a prime target for cybercriminals, who are looking for opportunities for identity theft or financial gain. Exposure of sensitive medical details can lead to abuse of medical systems, misuse of health insurance, discrimination, and privacy violations. Also, in the case of medical identity theft, attackers can add incorrect information to a patient’s medical record, potentially leading to misdiagnosis, wrong treatments, or dangerous drug prescriptions.
Legal and regulatory compliance. The healthcare industry is subject to numerous laws and regulations aimed at protecting patient data and ensuring the security of healthcare systems. Requirements vary by country and region:
- United States: The Health Insurance Portability and Accountability Act (HIPAA) mandates strict security and privacy rules for handling PHI.
- EU: The General Data Protection Regulation (GDPR) applies to the processing of personal data, including health data, and imposes strict requirements on organizations. This regulation applies to all EU residents and businesses that operate in the EU. The EU is also actively working to strengthen cybersecurity, specifically within the healthcare sector. The European Health Data Space (EHDS) Regulation entered into force in March 2025, enhancing secure exchange and access to health data across EU member states.
- Canada: The Personal Information Protection and Electronic Documents Act (PIPEDA) regulates how private-sector organizations collect, use, and disclose personal information.
- Other regions: In Australia, the Privacy Act 1988 provides the Australian Privacy Principles (APPs), which govern the handling of personal information, including health information. In the UK, healthcare software must comply with the UK General Data Protection Regulation (UK GDPR) and the Data Protection Act 2018.
Failure to comply with these laws and regulations can lead to severe penalties, including fines, legal actions, reputational harm, and operational disruptions.
Patient trust. The foundation of the patient–provider relationship is trust. Patients share highly personal and sensitive information with healthcare providers with the expectation that it will be kept confidential and secure. Right now, there is growing awareness among the public about the risks of data breaches. When trust declines, healthcare organizations may face reputational damage, reduced patient engagement, and lower satisfaction scores. This leads to lower operational performance and long-term patient retention.
The high-stakes nature of healthcare makes cybersecurity not just a technical concern but a core component of patient safety, regulatory compliance, and operational stability. However, understanding why security matters is only the first step. To build truly resilient systems, healthcare software providers must also recognize where the most critical vulnerabilities lie. Let’s take a look at the common cybersecurity threats facing healthcare software today, what they put at risk, and what consequences they can bring.
Need a tech partner for your healthcare product?
Team up with Apriorit to build reliable, secure, and regulatory-compliant healthcare solutions, from EHR platforms to remote patient monitoring systems.
Common cybersecurity threats in healthcare software
Healthcare software faces a unique set of cybersecurity challenges due to the sensitive nature of patient data and the critical role these systems play in medical operations. Let’s take a look at some of the most pressing threats, as well as their potential consequences.
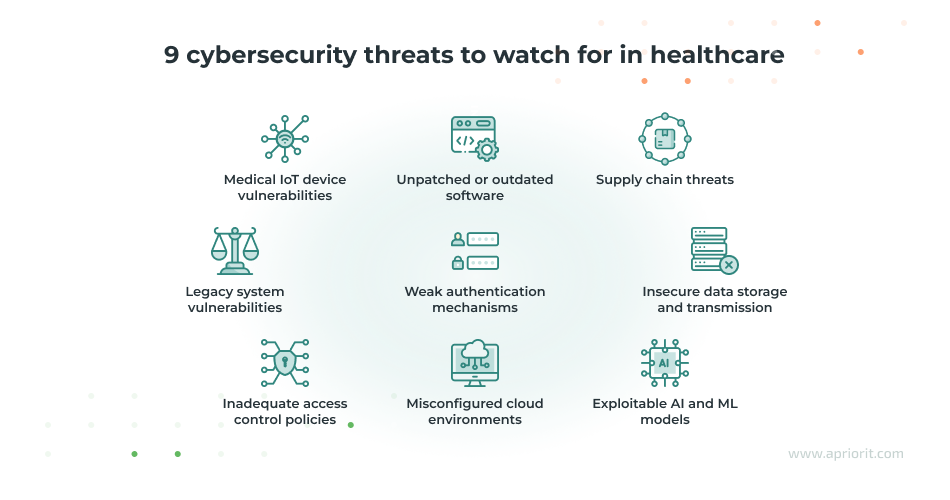
Medical IoT device vulnerabilities. Connected medical devices, from pacemakers and insulin pumps to imaging equipment, often run on proprietary software with limited security features. These devices may lack regular updates, ship with hardcoded credentials, or have unsecured wireless connections.
What can this lead to?
- Hackers can exploit IoT devices to launch attacks or intercept data.
- Patients may be put at risk due to inaccurate readings or disabled devices.
- A compromised IoT device can act as a pivot point to access broader hospital infrastructure.
Unpatched or outdated software. Many healthcare environments rely on software components that aren’t regularly updated, sometimes due to compatibility issues with medical devices or the need for 24/7 system availability.
What can this lead to?
- Attackers can exploit known vulnerabilities to infiltrate networks or unpatched software.
- Unpatched software can lead to ransomware infections, which in turn can lock healthcare providers out of critical systems.
- Since outdated software may also not comply with new security standards, businesses can face legal or financial consequences.
Supply chain threats. The software supply chain includes third-party APIs, external services, open-source libraries, and software components integrated during development. Each of these dependencies can become a vulnerability as it introduces new attack vectors, especially since healthcare organizations often lack visibility into their software vendors’ security practices. Supply chain attacks may go undetected for months, putting healthcare organizations at risk.
What can this lead to?
- A compromised third-party element can become a backdoor into the primary system.
- Malicious actors can gain unauthorized access to PHI through vulnerable APIs.
- Third-party breaches can lead to violations of regulatory requirements and loss of patient trust.
Legacy system vulnerabilities. Legacy systems were not designed to meet today’s cybersecurity standards and frequently lack compatibility with modern security tools. In addition, attackers find new vulnerabilities that often can’t be patched. Because legacy systems are deeply embedded in hospital workflows, replacing or upgrading them can be costly and disruptive, making them persistent weak points in healthcare IT infrastructure.
What can this lead to?
- Outdated data protection mechanisms may lead to the exposure of medical records.
- System failures can interrupt care delivery or delay critical diagnostics.
- Lack of monitoring capabilities leads to challenging detection of breaches and incident investigation.
Weak authentication mechanisms. Systems that rely on single-factor authentication, reused credentials, or outdated login practices have weaker protection of access to EHR/EMR systems and sensitive patient data. This makes them easy targets for unauthorized access to EHR/EMR systems and sensitive patient data.
What can this lead to?
- Weak, reused, or insecurely shared credentials can lead to the manipulation of medical records.
- Poor authentication practices, such as shared credentials or a lack of multi-factor authentication, make it easier for malicious insiders or unauthorized users to access sensitive patient data and steal or misuse it.
- Compromised accounts may be hijacked and used for fraudulent billing or identity theft.
Insecure data storage and transmission. When sensitive data is not properly encrypted, either at rest or in transit, it becomes vulnerable to interception, theft, and tampering. This puts all types of healthcare data at risk, including PHI, diagnostic reports, backup files, and internal communications. Securing this data is especially critical in environments that rely on mobile health apps, remote monitoring tools, or cloud platforms, where data moves frequently across networks and is more exposed to potential breaches.
What can this lead to?
- It becomes easier for malicious actors to steal or manipulate unencrypted patient data.
- Leaked data due to misconfigurations or internal errors may be intercepted by unauthorized third parties.
- Unsecured backups and internal communications can serve as entry points for broader attacks.
- Unprotected PHI and diagnostic records can lead to breaches of patient confidentiality.
Inadequate access control policies. Poorly defined access rights, like overly broad admin privileges or a lack of role-based access, make it easy for users to access data and functions beyond their needs.
What can this lead to?
- A broader attack surface increases the potential impact of both internal and external security breaches.
- Unauthorized access to sensitive systems and patient data becomes more likely, especially when accounts are compromised.
- Meeting compliance requirements is impossible when access to regulated assets isn’t properly restricted.
- Granting users excessive privileges contributes to the increased risk of insider threats.
Misconfigured cloud environments. Healthcare software can benefit from migration to the cloud, but issues like misconfigured storage buckets, APIs, or access controls can have devastating consequences. These mistakes can expose massive datasets to the public or unauthorized users and create vulnerabilities in cloud-based healthcare systems and data storage. Security incidents in cloud environments may go unnoticed because of insufficient logging or monitoring. Lack of cloud security expertise also contributes to these issues.
What can this lead to?
- The risk of large-scale data leaks is rising, and such leaks can affect thousands of patients at once.
- Unsecured cloud services can create backdoors for attackers, allowing them to steal traffic without any restrictions.
- Organizations may face legal consequences if software providers mishandle protected health data.
Exploitable AI and ML models. The growing use of AI in healthcare for diagnostics, treatment recommendations, and operational efficiency introduces new attack vectors that can be overlooked. Malicious actors can tamper with training datasets or exploit AI models through adversarial inputs.
What can this lead to?
- Corrupted AI training data can cause diagnostic systems to make inaccurate or unsafe recommendations, potentially endangering patient health.
- Adversarial inputs can manipulate AI algorithms in real time, undermining clinical and insurance decisions and creating new patient safety risks.
- Sensitive patient information used during AI model training can be reconstructed or exposed through model inversion attacks.
- Undetected manipulation of AI models can result in long-term degradation of healthcare service quality and decision-making reliability.
Cybersecurity risk awareness on its own isn’t enough to protect sensitive healthcare environments. Each vulnerability, from outdated systems to misconfigured cloud setups, requires targeted measures to minimize risks. That’s why security must be embedded directly into the software development process. Next, we will see what practical strategies your team can implement to strengthen your software against evolving cyber threats.
Read also
Healthcare Software Development: Challenges and Solutions
Explore the most critical challenges in healthcare software development, from interoperability to compliance, and gain practical insights on building reliable, compliance-ready healthcare systems.

Best practices for boosting healthcare software security
Your teams need to address cybersecurity risks in healthcare proactively during healthcare software development and after deployment. This is crucial for protecting sensitive data, maintaining compliance, and preserving patient trust.
Let’s take a look at these best practices for healthcare cybersecurity in more detail.
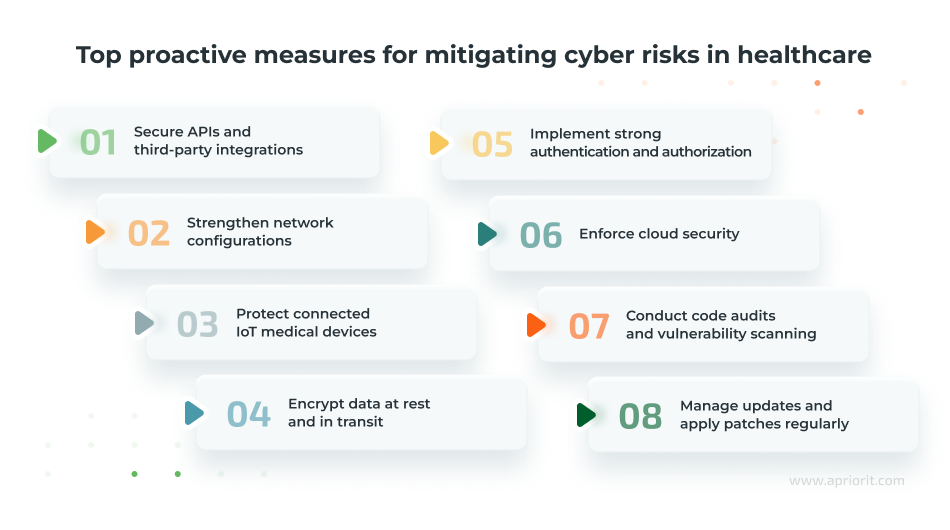
Secure APIs and third-party integrations. Healthcare applications frequently exchange sensitive patient data with other systems, labs, pharmacies, and third-party analytics platforms via APIs. The complexity of these integrations creates a certain challenge: you need to secure data handling and access control across systems that you don’t fully own or manage.
Here is how your team can boost API security:
- Implement robust authentication and authorization mechanisms, such as OAuth 2.0, for all API endpoints.
- Employ strong input validation and sanitization techniques to prevent injection attacks like SQL injection or XSS.
- Use encryption for all API communications to protect data in transit.
- Apply rate limiting and throttling to prevent API abuse or denial-of-service attacks.
- Set up secure data exchange protocols with third-party vendors, including data mapping and access control.
- Conduct regular security testing and vulnerability scanning of API endpoints.
Apriorit expert tip: Consider evaluating third-party security practices before integrating them into your software using standardized vendor risk assessment practices.
Strengthen network configurations. While healthcare networks are designed for high availability and fast access to data, their openness can make them a prime target for attackers. You need to design software that not only functions within segmented environments but actively reinforces a secure traffic flow between services, limiting lateral movement in case of compromise. Here is how you can achieve that:
- Design systems with segmented networks — for example, with separate zones for admin, patient data, and development environments.
- Apply least privilege rules to network-level access during development and deployment.
- Use secure protocols like HTTPS, SFTP, and SSH for all network communications.
- Configure firewalls, proxies, and routing policies in development and staging environments to mirror production.
- Disable unused ports and services in application servers and virtual machines.
Apriorit expert tip: Your team needs to conduct regular reviews of the system and network to detect misconfigurations early on.
Protect connected IoT medical devices. Many medical IoT systems have long operational lifespans, limited firmware update capabilities, and strict performance requirements. Your teams must consider how their software interacts with these devices and how to secure those interactions without compromising reliability or clinical accuracy. To achieve this, here is what you can do:
- Require mutual authentication between IoT devices and backend services.
- Ensure secure firmware update mechanisms are built into the device firmware.
- Avoid using default credentials and enforce strong, unique device identities.
- Use message integrity checks like HMAC to prevent tampering.
- Encrypt device communication using TLS and isolate device traffic in the network.
Apriorit expert tip: Our experts recommend incorporating endpoint monitoring agents to detect unusual device behavior during testing.
Encrypt data at rest and in transit. Apart from protecting patient information, encryption plays a major role in meeting compliance requirements and enabling secure inter-hospital communication. Your team has to embed encryption practices early to ensure that all modules handling sensitive data meet industry standards without adding latency or complexity. Here is how they can achieve that:
- Apply AES-256 encryption for databases, storage volumes, and backups.
- Use TLS 1.3 to encrypt data during transit between all services and endpoints.
- Regularly test encryption settings and ensure certificate validity.
- Implement field-level encryption for highly sensitive fields.
Apriorit expert tip: Our security experts don’t recommend using automation for encryption management. Instead, you can use dedicated solutions like AWS Key Management Service or HashiCorp Vault.
Implement strong authentication and authorization. Healthcare applications often serve a wide range of user types, from temporary contractors to long-term staff, and they all require different access levels. Building flexible, scalable identity management systems from the start is critical to reduce the risk of privilege abuse or identity spoofing. Here are some tips on how to implement this:
- Enforce multi-factor authentication for all user and admin roles.
- Use standardized protocols like OAuth 2.0 and OpenID Connect for access delegation.
- Set strict session timeouts, IP restrictions, and device recognition checks.
- Use secure libraries for session and token management (for example, JWT with proper expiration).
- Implement role-based access control and test access rules during development.
Apriorit expert tip: Strengthen your software’s defenses by implementing logic on the back end that blocks credential reuse and enforces password complexity requirements.
Enforce cloud security. Cloud environments offer scalability, but many healthcare developers face challenges adapting traditional software security models to dynamic, containerized, or serverless architectures. Here’s how you can prevent cloud misconfiguration and improve security:
- Adopt a zero-trust architecture where access is never implicit, even within the network.
- Perform automated infrastructure configuration scans with tools like AWS Config or Azure Security Center.
- Enforce encryption for all cloud-based storage and communication layers.
- Set up logging and monitoring with tools like AWS CloudTrail or Azure Monitor during development for auditability.
- Include secrets management in the CI/CD pipeline.
Apriorit expert tip: We recommend using identity and access management practices to restrict access to development, staging, and production environments separately.
Manage updates and apply patches regularly. With so many healthcare systems operating 24/7, downtime for patching can be limited. This places even more responsibility on your team to build solutions that can be updated seamlessly, without disrupting clinical workflows or introducing regressions that compromise safety. Here is how you can do that:
- Monitor all software dependencies for known vulnerabilities.
- Automate update checks in your build and deployment pipelines.
- Maintain a software bill of materials (SBOM) to track open-source components in use.
- Retire and replace unsupported libraries or SDKs, especially in legacy codebases.
Apriorit expert tip: If possible, apply security patches to third-party libraries and frameworks as well.
Conduct code audits and vulnerability scanning. Given the high stakes of healthcare data breaches, external compliance checks are not enough. Your teams must adopt a security-first mindset, integrating testing tools and manual reviews that catch issues before they can be exploited in production environments. To achieve this, you can:
- Integrate static application security testing tools into the development pipeline.
- Perform manual reviews for modules handling PHI, authentication, or external connections.
- Use dynamic application security testing before deployment to simulate real-world attacks.
- Include test cases for common healthcare-specific threats, such as HL7 message manipulation or Fast Healthcare Interoperability Resources injection.
Apriorit expert tip: Conduct internal penetration testing for a comprehensive audit or team up with security experts for a more thorough assessment.
Putting these practices into action requires deep technical expertise, industry knowledge, and a strategic development approach. That’s where the right technical partner can make all the difference.
Read also
Healthcare Software Modernization: Overcoming Challenges, Delivering Results
Transform your legacy healthcare systems with actionable modernization strategies that address scalability, regulatory compliance, and technical debt.

How can Apriorit help?
At Apriorit, we bring together over 20 years of experience in cybersecurity and a deep understanding of the specifics of healthcare software engineering. This makes us a trustworthy addition to your team, whether you are building a healthcare product from the ground up or enhancing an existing platform.
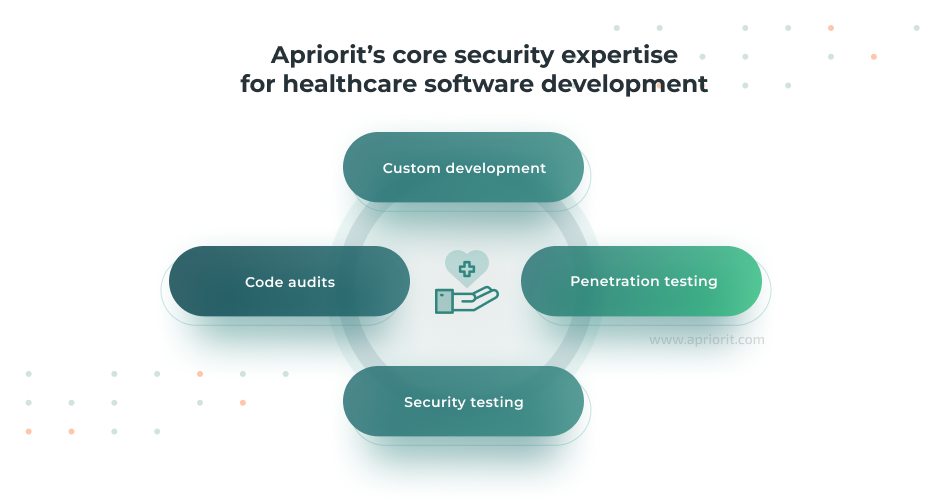
Custom software development. We build healthcare software solutions from the ground up with security at their core, following secure SDLC practices and healthcare compliance requirements.
Penetration testing. Our team simulates real-world attacks to uncover vulnerabilities in your application, APIs, cloud configurations, and network layers before malicious actors can exploit them.
Security testing. We perform hands-on testing throughout development to validate the resilience of your software, identify misconfigurations, and verify compliance with healthcare security standards.
Code audits. We analyze your source code for logic flaws, backdoors, hardcoded credentials, and other security issues that may put patient data or system integrity at risk.
Apart from these services, we provide deeper technical expertise tailored to your unique needs. Here is what our experts can offer:
- Cloud development and configuration to build secure cloud-native healthcare applications
- IoT expertise to design and secure medical IoT ecosystems
- Legacy system modernization to upgrade or replace outdated systems with solutions that maintain continuity while eliminating vulnerabilities
- AI expertise to develop AI-driven healthcare solutions that are secure by design
With Apriorit, you gain a cybersecurity partner for developing secure solutions, mitigating complex risks, and ensuring compliance across regulated industries like healthcare.
Related project
Building an AI-based Healthcare Solution
Discover how we helped a US-based healthcare center develop an AI-powered platform to streamline diagnostics and enhance patient data analysis.
Conclusion
As cyber threats grow more sophisticated, healthcare organizations have to stay vigilant and protect everything from databases and medical devices to cloud infrastructure and AI systems. Securing healthcare software is no longer optional but rather is a critical requirement for a sector where patient data, trust, and lives are on the line.
Overcoming today’s top cybersecurity threats in healthcare requires more than reactive measures. At Apriorit, we take a proactive approach based on deep technical expertise and a solid understanding of healthcare’s regulatory and operational complexities. Our dedicated teams will help you build a secure, compliant, and resilient healthcare product.
Ready to innovate in the digital health sector?
Collaborate with Apriorit to build secure and scalable healthcare solutions tailored to your needs.



