The blockchain and the Internet of Things (IoT) have huge potential, and people are already working on combining these technologies. This combination may enhance data security within IoT networks and ensure support for massive IoT solutions. Let’s take a close look at how exactly you can use blockchain features to enhance IoT networks.
Although global spending on IoT is expected to reach $745 billion in 2019, according to a forecast by the International Data Corporation, data security in IoT networks remains a significant issue.
How can we secure IoT devices and networks before implementing them into businesses, organizations, and industries? Would it be helpful to use blockchains alongside the Internet of Things?
In this article, we define the benefits of integrating blockchains into IoT networks, discuss major security challenges in IoT and possible ways to overcome them, and show examples of real-life use cases.
This article will be helpful for developers who want to implement blockchain technology in IoT networks and for everyone who’s interested in enhancing the security of IoT networks.
Contents:
Why do IoT networks need blockchains?
Before we point out the major pros and cons of using a blockchain in the Internet of Things, let’s briefly define what an IoT network is and how it works.
The high-level concept of an IoT network is that smart devices like sensors, actuators, and wearables gather data about their environments, wirelessly connect to the internet and to other connected devices via routers and gateways, and share the information they’ve collected within the network.
In addition, there are remote devices with user interfaces (smartphones, tablets, computers, various control panels) that control IoT devices and transmit data to users. In an IoT network, the collected data flows between IoT devices and can be stored in the cloud, in a local database, on a remote device, or on IoT devices themselves.
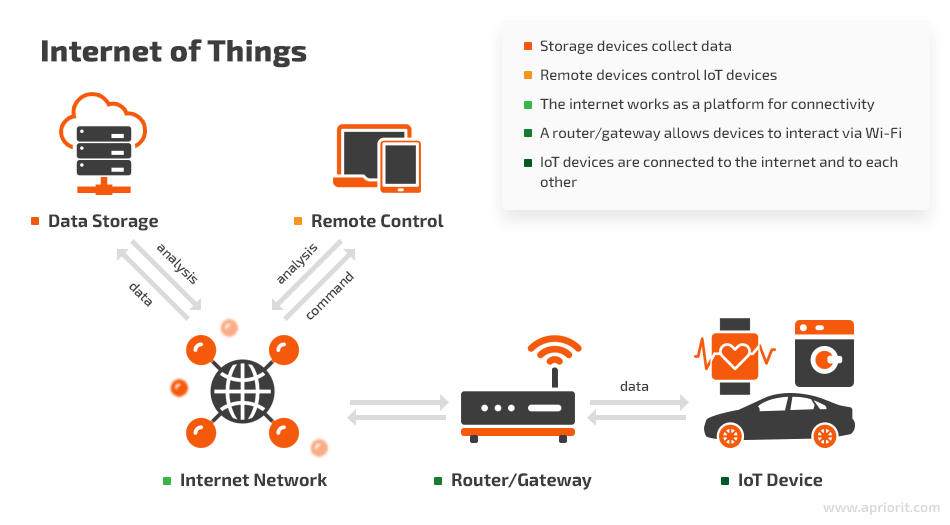
IoT technology is used in workplaces, on the streets, in public places, and at home, facilitating the work of smart home systems, security systems, smart city infrastructure, etc. IoT devices are also widely used in healthcare, agriculture, construction, manufacturing, and other industries.
Wireless connections make IoT networks easier to implement for home and business use. However, wireless connections also leave plenty of room for data breaches and hacking.
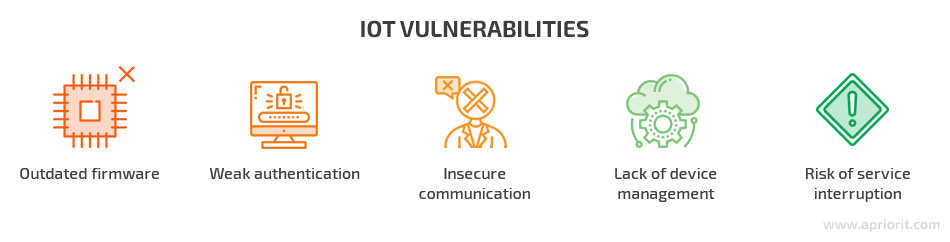
Let’s consider the major IoT vulnerabilities:
Outdated firmware. Not all manufacturers provide regular firmware updates, and not all users will update firmware when a new version is available. Weaknesses in firmware can be abused to infect a device with malware or change its performance.
Weak authentication. The risk of data leaks remains significant for IoT devices with hardcoded passwords. Also, cybercriminals can take advantage of guessable passwords if there are no strict requirements for passwords created by users.
Insecure communication. Data leaks in IoT networks usually happen because of insecure data transfer (among devices and between devices and the cloud) and storage (both in the cloud and on devices). Hackers can get access to device information if it’s unencrypted.
Lack of device management. Without professional device management, IoT networks will perform poorly and be extremely vulnerable to attacks.
Risk of service interruption. Risks such as physical damage to smart devices, loss of network connectivity, and the security of third-party cloud services bring new challenges to IoT security. There’s also the risk of an attacker reconfiguring the way a device operates. For instance, cybercriminals can use compromised devices for eavesdropping or for launching DDoS attacks to disrupt the service of other systems.
One possible solution to eliminate the main vulnerabilities of IoT networks is adding a blockchain.
A blockchain is a distributed ledger maintained by a peer-to-peer network, which is a collection of nodes. Nodes are individual computers, which are interconnected and each have a copy of the blockchain. Each block in the chain contains encrypted information about transactions performed at a given time that were verified by nodes. Information encrypted into a blockchain is immutable and protected against tampering.
Let’s look closer at how exactly a blockchain works:
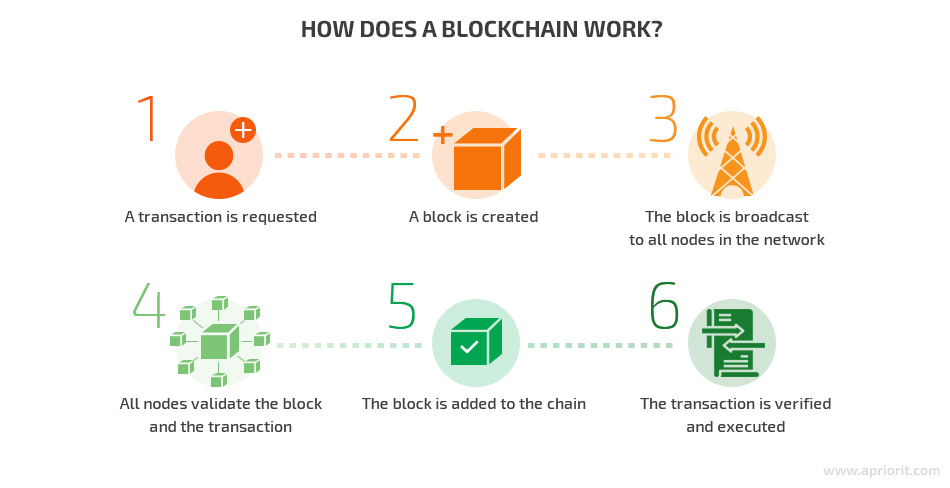
Considering the data protection and immutability, a blockchain can enhance the security and privacy of IoT systems by:
- Protecting transactions from being modified or removed
- Recording an immutable history of events
- Offering complete transaction traceability for users
Let’s discuss the main advantages of enhancing IoT networks with blockchains.
Benefits of IoT and blockchain integration
How exactly can developers leverage blockchain technology to enhance IoT systems?
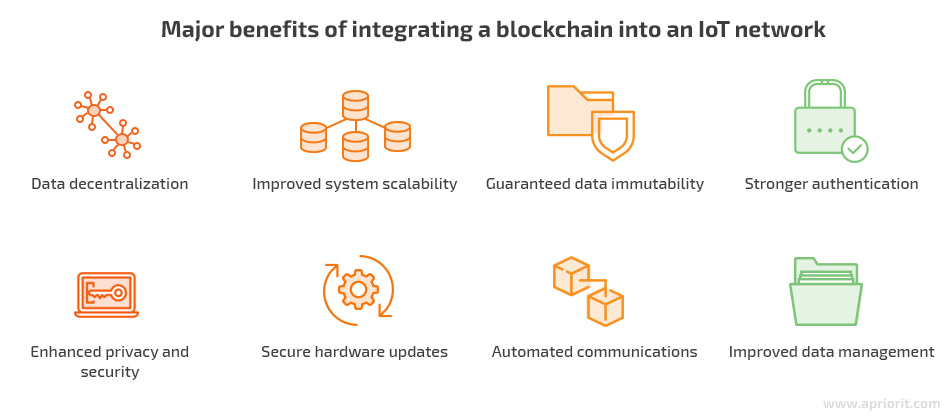
Data decentralization
Data centralization is a significant problem for IoT networks. Information collected by IoT devices is often stored on centralized servers, opening the possibility for private data to be transmitted to third parties. And with a single point of failure, an entire network can be disabled at once.
The distributed architecture of the blockchain means there’s no central point of control, eliminating single points of attack or failure, reducing costs for infrastructure, reconciliation, and management, and improving fault tolerance.
In contrast to the cloud, all nodes in a blockchain collectively manage the distributed digital ledger and are responsible for confirming new blocks.
Improved system scalability
Not only does decentralization reduce IoT silos, it also contributes to improved scalability.
Decentralized networks distribute workloads over many computers and therefore provide more computing power than centralized networks.
Additional storage, bandwidth, and processing power are exactly what IoT networks lack to support an increasing number of smart devices and transactions.
Guaranteed data immutability
The immutability of data in a blockchain is ensured with cryptography that makes the distributed ledger permanent and unalterable.
By adding cryptography to smart devices, you can ensure secure data transfer and storage. With this approach, a blockchain can keep an immutable history of smart device communications within the IoT network.
Stronger authentication
With a blockchain, every single IoT device can be identified. Moreover, a blockchain can ensure trusted authentication and authorization for smart devices, meaning all data within the IoT network will be secured.
To register users’ identities, most blockchain platforms use a decentralized approach to the cryptographic Public Key Infrastructure (PKI) authentication, which requires a key generator in the blockchain to create a private and public key pair.
Conventional PKI is centralized, and therefore has its own limitations and problems like vulnerability to man-in-the-middle attacks. However, blockchain technology enhances the PKI mechanism by making it decentralized.
The private key remains only with the user and is used to prove their identity, while the public key is distributed to the network provider. Being generated cryptographically, both keys are incredibly hard to crack.
Enhanced privacy and security
Another benefit is a variety of cases of using blockchain for cybersecurity purposes. The blockchain can secure communication between IoT devices by storing data in transactions and validating those transactions with nodes. This ensures the traceability and accountability of sensor data.
A blockchain can also optimize current IoT protocols by providing data encryption. Using cryptography for communications, the blockchain eliminates the risk of data breaches. Each transaction within a network of distributed ledgers is protected in transit thanks to end-to-end encryption.
Secure hardware updates
The blockchain’s secure and immutable storage allows developers to safely and securely push code to IoT devices. This can potentially solve the issue of outdated IoT software. IoT middleware can use this functionality to update IoT devices securely and automatically.
For instance, experts from the University of Tulsa suggest that blockchain technology can be used for securing over-the-air IoT firmware updates. The solution they propose was tested using an open-source blockchain framework and a Wi-Fi-capable ESP8266-based board.
The proposed architecture has an additional blockchain layer that consists of two sublayers — infrastructure and smart contracts — that support numerous providers, devices, and services within the network.
Specifically, the infrastructure sublayer of the blockchain supports the basic functionality of a permissioned blockchain network: certificate authority (CA) for authentication and peer nodes. Apart from CA, this sublayer includes the consensus protocol and distributed immutable ledgers.
The smart contract layer verifies firmware updates and handles incidents that may occur during the update process.
Automated communications
Blockchain technology can treat device messages as transactions and automate them with smart contracts. These self-executing computer programs can help IoT networks leverage automation that most day-to-day transactions need as well as enhance data safety.
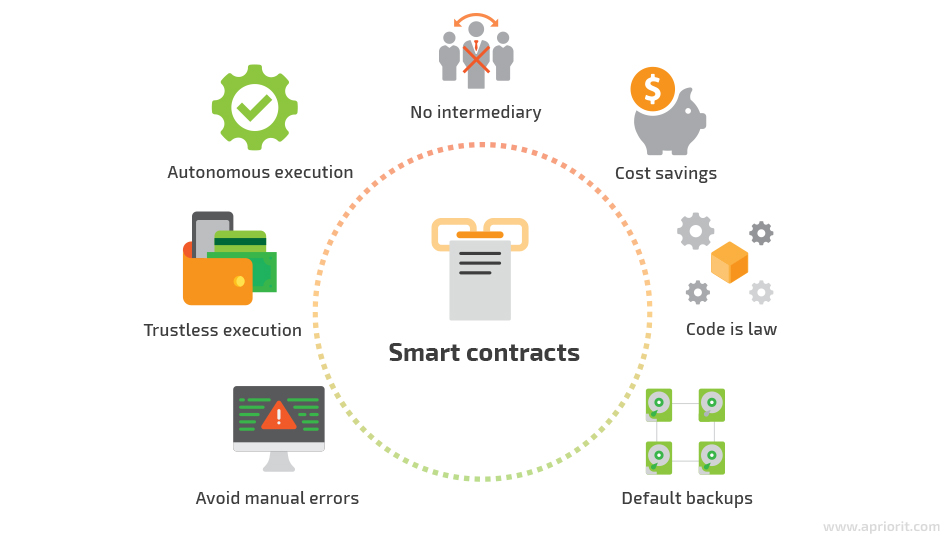
Smart contracts can easily be accessed and executed by IoT devices to conduct machine-to-machine transactions automatically, securely, and without third-party approval. Smart contracts follow strict rules and don’t require human intervention.
For example, a smart contract can be used for data analysis, aggregating temperature measurements from IoT devices and providing a daily average or min/max temperatures.
Improved data management
IoT networks have to transmit large amounts of data through devices, systems, platforms, and various administrative boundaries in real time, which makes it hard to ensure proper data management and the secure functioning of an IoT system.
A blockchain allows IoT devices to communicate without the involvement of a server, cloud storage, or a local database. This means IoT developers can use blockchains to provide device-agnostic and decoupled applications.
Besides, there are no intermediaries in a blockchain, as network participants interact directly with each other through encrypted identities using peer-to-peer communication. Each transaction is added to an immutable block and distributed to all network nodes.
How to integrate a blockchain into an IoT network
A blockchain can be integrated into an IoT network in several ways. We discuss three possible approaches to developing a blockchain-based IoT network architecture.
The first thing to consider before creating a network is where interactions will take place. Interactions can happen not only in the IoT network or on the blockchain but within a hybrid architecture that involves both the IoT network and blockchain.
Another essential component of IoT and blockchain convergence could be fog computing. This technology has already revolutionized IoT networks, adding a new layer between cloud computing and IoT devices.
Let’s explore three possible architectures for a blockchain-based IoT network.
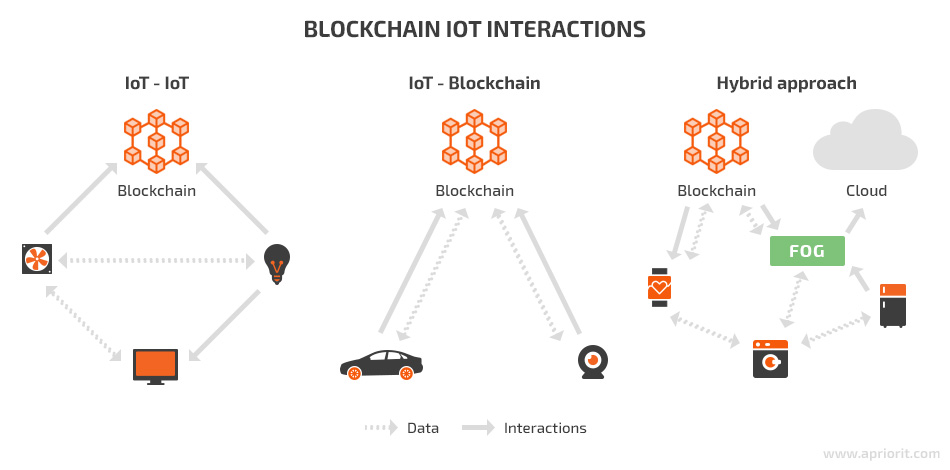
1. IoT–IoT
This approach entails using the blockchain to store only part of the IoT data. IoT devices communicate without using the blockchain, instead using discovery and routing mechanisms. Transactions are transmitted fast because of low latency. This approach is also considered one of the most secure because it allows devices to work offline.
2. IoT–blockchain
In this case, all communications between IoT devices go through the blockchain, which basically takes the place of the cloud in a traditional IoT network. Records stored in the blockchain are immutable, traceable, and secured from third-party access.
On the one hand, this approach increases the autonomy of devices and ensures the security and traceability of communications. On the other hand, recording and storing all transactions in the blockchain leads to increased bandwidth and data.
3. Hybrid approach
This approach ensures that most data and interactions are shared directly between IoT devices, whereas the blockchain stores only some data. Thus, this design leverages the benefits of both the blockchain and real-time IoT interactions.
The hybrid approach allows for implementing fog and cloud computing to make up for the limitations of blockchains and IoT devices. For example, fog computing uses gateways and other edge devices to conduct mining or store data. Analyzing sensitive data locally with edge devices instead of sending it to the cloud significantly reduces operating expenses.
Choosing which interactions should go through the blockchain and providing a way to decide this at runtime is the biggest challenge of this approach.
Your choice of approach to IoT and blockchain integration will mainly depend on the requirements of your IoT network.
For instance, if you need to use a blockchain consensus protocol that requires mining, the best choice may be a hybrid approach. This architecture can include fog computing, which involves fewer computationally limited devices such as gateways and therefore can be used for mining.
Challenges of developing blockchain-based IoT networks
When developing blockchain-based IoT solutions, various technical challenges arise. In this section, we list some major issues you can encounter when combining blockchain and IoT technologies and consider ways to solve them.
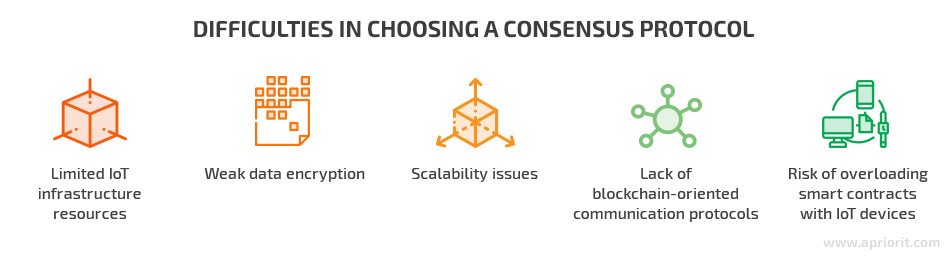
Difficulties in choosing a consensus protocol
When it comes to combining a blockchain-based approach and an IoT environment, developers are trying to solve two crucial issues:
- Blockchains are computationally expensive
- IoT devices are resource-constrained
These issues have brought about the necessity to develop an IoT-centric consensus protocol.
There are several methods in which different nodes in a blockchain network can reach consensus over a new block. These methods are called consensus protocols.
Existing blockchain consensus protocols can hardly be implemented in an IoT environment in their current state due to high computational requirements, scalability issues, transaction fees, the monetary concept, and other challenges that conflict with the nature of IoT devices.
To develop the perfect consensus algorithm for an IoT network, you need to consider a number of strict requirements that are different than those for typical blockchain applications. An ideal IoT-centric consensus protocol has not yet been proposed. However, we can define the main requirements that such a consensus protocol should meet.

Let’s take a closer look at some of the most popular and promising consensus protocols for IoT networks.
Proof of Work
The most famous consensus protocol, Proof of Work (PoW), is used by the Bitcoin network and has high computational and bandwidth requirements, making it impractical for IoT networks.
However, it can potentially be used in a hybrid approach where mining is handled by fog computing. Another option is to consider other consensus protocols based on PoW such as Proof of Capacity (PoC) or Proof of Elapsed Time (PoET).
Proof of Stake
The second most popular blockchain protocol is Proof of Stake (PoS), which eliminates the high computational requirements of PoW. In PoS, nodes use digital signatures to validate blocks instead of solving complicated hashes. The other difference is that in PoS, nodes don’t compete for the right to solve the next block. Instead, they’re chosen to mine the next block based on their proportional stakes in the network.
However, PoS also isn’t quite suitable for IoT devices, mostly because it’s based on a monetary concept (stakes) that doesn’t exist in IoT networks. Moreover, PoS has more issues to solve – for instance, the nothing at stake problem, which still isn’t covered in some PoS-based protocols.
Byzantine Fault Tolerance Protocols
Mechanisms in the Byzantine Fault Tolerance (BFT) family are used for integrating blockchains into IoT networks. These machine replication protocols eliminate the Byzantine Generals’ Problem and protect against arbitrary faults by replicating services on multiple nodes. Let’s discuss some of them below:
1) Practical Byzantine Fault Tolerance
Practical Byzantine Fault Tolerance (PBFT) is a consensus method used by private blockchains like Hyperledger projects. In this method, all nodes participate in the voting process to add the next block. Consensus can be reached if more than two-thirds of nodes agree on the block.
PBFT can potentially be used in IoT networks because of its low computational overhead, fast transaction speed, and low latency. However, this consensus method is still unscalable for large networks, so it can be applied only to small IoT projects.
2) Delegated Byzantine Fault Tolerance
Delegated Byzantine Fault Tolerance (dBFT) is another BFT consensus mechanism. It operates in almost the same way as PBFT, with the only difference being that dBFT doesn’t require the participation of all nodes to add a block.
In dBFT, some nodes are chosen as delegates on behalf of the other nodes and according to the set rules. These delegates then pursue a consensus protocol similar to PBFT. The only problem is that the average time for block creation in dBFT is 15 seconds, which is too long for an IoT network. Therefore, it’s not an option.
However, the NEO open-source blockchain project has already implemented the dBFT consensus protocol into its smart economy projects. NEO has even come up with a dBFT 2.0 solution that improves network performance and reduces the block time when the consensus node process or system restarts due to hardware failure, a power outage, or other system issues.
Tendermint
Tendermint is a permissioned hybrid consensus method based on PBFT and PoS. In Tendermint, there are two types of participants: validators and delegators. First, validators propose blocks of transactions and pre-vote on and then pre-commit these blocks. Consensus is reached when more than two-thirds of validators pre-commit to the same block in the same round.
Just like PBFT, Tendermint provides high scalability, fast transaction speed, and low latency, which is valuable for IoT networks. However, IoT and Tendermint convergence requires the monetary concept to be replaced by some other concept.
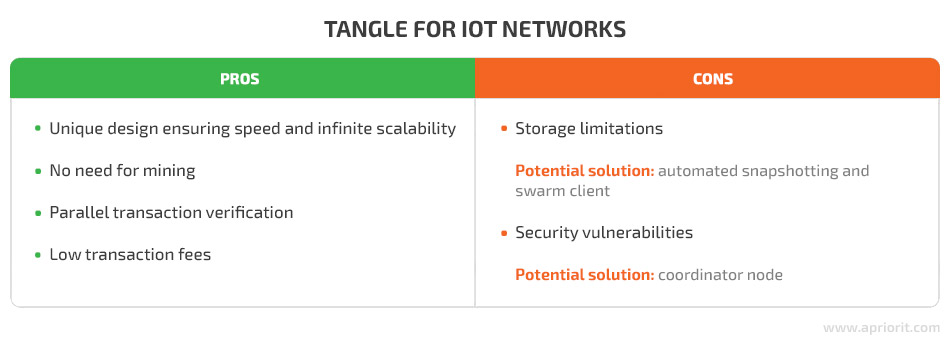
Tangle
The Tangle is a new directed acyclic graph (DAG), a ledger that stores transactions in a graph format that points in one direction. This method was proposed by IOTA.
A Tangle doesn’t require mining to achieve consensus. It also doesn’t use blocks to store transactions. Each transaction is a unique block by itself that must approve two older transactions in order to be added to the ledger.
Tangle is applicable for IoT networks thanks to its unique design that makes it fast and infinitely scalable. Moreover, this solution eliminates the need for mining, enables parallel transaction verification to verify more transactions in a shorter time, and has low transaction fees.
On the other hand, smart devices can’t store an entire Tangle due to space limitations. IOTA is already working on potential solutions to this issue, such as automated snapshotting and a swarm client. The other issue is security vulnerabilities. If anyone gains control over more than one-third of the hash power, a Tangle becomes vulnerable to cyber threats. IOTA overcomes this issue by using a node called a coordinator that amasses the hash power itself; however, this can be considered a form of centralization.
Limited IoT infrastructure resources
The next issue is that IoT devices are limited in computational, memory, and storage capacity, while a blockchain requires lots of space for its records. Also, if we consider solutions based on the PoW consensus or similar protocols, we have to keep in mind that IoT devices lack the computational resources needed for mining.
Addressing the issue of limited IoT resources is still a work in progress. However, IBM has introduced one possible solution to the issue of blockchain size.
IBM experts have come up with the concept of universal and regional blockchains, achieved by categorizing network nodes into light peers, standard peers, and peer exchanges. The functionality of these nodes depends on their processing, storage, networking, and power capabilities.
Light nodes only store their own blockchain address and balance, standard peers store recent transactions of their own and of the light peers, and peer exchanges replicate the complete blockchain and perform data analysis.
Weak data encryption
Encryption is an essential part of the blockchain’s nature and a vital element of data security. Unfortunately, IoT devices don’t interact with users in a way that allows them to produce reliable cryptography.
One possible solution to improving encryption security in IoT networks is providing them with entropy created by a quantum random number generator. This approach leverages data driven by quantum physics, which is fundamentally random, contrary to classical physics.
You can implement a mechanism of quantum random number generation for enhancing encryption in your IoT network by using entropy as a service (EaaS).
EaaS providers ensure high-quality sources of entropy based on physical processes of quantum devices. These devices provide true randomness that developers can leverage to protect their applications and devices against cyberattacks.
Scalability issues
Scalability is one of the biggest challenges when it comes to integrating blockchain and IoT technologies. The problem is that IoT networks continue evolving, which means more smart devices, more transactions, and more data.
In addition to this, the nature of IoT requires immediate data transfer. However, blockchain implementations may cause problems because of the time needed to confirm transactions.
The ideal blockchain architecture for IoT is able to process a high throughput of transactions and secure an enormous number of peers within the network.
This issue can be potentially solved in a few ways:
1. Parallel computing
With parallel computing (or parallel processing), many calculations or processes are carried out simultaneously.
When implemented in blockchain systems, parallel processing ensures the ability to process multiple transactions with non-competing data to improve transaction efficiency. In addition, when one chain becomes too complex to be effectively processed, it can be split into parallel chains to offload the traffic.
Parallel computing can be used to collect and analyze IoT data, analyze real-time big data, and handle other projects that require lots of computations.
2. Other solutions that accelerate transaction speed
There are also other possible ways of enhancing transaction speed that seem promising.
The Plasma and Plasma Cash protocols allow for an exponential increase in scalability by using child chains, parent chains, and a root chain and adding a layer of smart contracts that can interact with the main blockchain.
Most blockchain scalability solutions are created for transferring funds and are always trying to reach Visa transaction capabilities. However, their algorithms can potentially be used to solve the issues of transaction speed and scalability for IoT networks and blockchains.
Read also:
How to Use Blockchain in Supply Chain: A Practical Example of a Custom Network Implementation
Lack of blockchain-oriented communication protocols
The biggest difficulty in developing a standard security protocol that fits all types of IoT devices and systems is the diversity of communication protocols used within IoT networks. This diversity affects users’ security and privacy as well as the integration of blockchains.
First, IoT devices interact with each other wirelessly through specific protocols that aren’t designed for blockchains. Moreover, unlike conventional network devices that have the same operating system and data format, smart devices within a single IoT network often have application-specific functionality and lack operating systems.
Another issue is that end devices in traditional IoT networks commonly connect to the internet or gateway devices through secure and fast connections (both wired and wireless) such as fiber optic, DSL/ADSL, Wi-Fi, 4G, and LTE. However, smart devices usually connect to the internet or gateway devices through low-bandwidth and low-power wireless communication protocols such as 802.15.4, 802.11a/b/g/n/p, LoRa, Zigbee, NB-IoT, and Sigfox.
Creating specific blockchain-oriented communication protocols for IoT networks is possible; however, it requires time for thoughtful planning and implementation, while both hardware and software have to be kept in mind.
Risk of overloading smart contracts with IoT devices
Earlier, we mentioned the essential benefits that IoT environments gain with the adoption of smart contracts. However, this convergence comes with some challenges.
The first challenge is that smart contracts require the use of oracles — third-party information sources that provide data to blockchains that permit the creation of smart contracts. Oracles supply smart contracts with information essential to executing the contract in a trusted manner. The problem is that smart contract validation may be compromised, since oracles have to be provided with reliable authentication, security, and trust in an IoT environment that can be unstable.
Since oracles need to access multiple data sources, smart contracts can get overloaded. Although smart contracts are distributed and decentralized, they still require a large amount of computational power, which is a critical problem for IoT devices.
Blockchain to enhance IoT: use cases
Let’s take a look at existing solutions in which IoT and blockchains have been combined to create a strong synergistic effect and improve technologies, work processes, living conditions, and even entire industries.

HDAC
The Hyundai Digital Access Currency (HDAC) is a blockchain-based IoT contract and M2M transaction platform that’s still under development.
M2M transactions are payments made by devices on the blockchain. These payments are executed by an IoT smart contract. IoT contracts control and access devices as well as facilitate communications among them while assuring anonymity through transactions recorded on the ledger.
HDAC uses a combination of public and private blockchains and quantum random number generation to secure these transactions. The HDAC cryptocurrency-enabled public blockchain can be effectively used with multiple private blockchains. Hyundai promotes its blockchain-driven project in various business areas including consulting, blockchain-based hardware, and IoT solutions for businesses and smart homes.
Quorum
Quorum is another platform that can bring blockchain security to IoT. It supports both private and public transactions, allows for multiple consensus mechanisms, and increases data privacy through cryptography and segmentation.
The initial goal of Quorum was to service the financial services industry, but the platform can be used to create secure links between physical assets like smart devices and blockchains.
For example, smart contracts can be implemented in an IoT food safety network between a warehouse and a supermarket to send, accept, and store information about the temperature in warehouse freezers.
To ensure privacy for its projects, Quorum uses public/private state separation and peer-to-peer encrypted message exchanges. Thus, private transactions and contracts are securely transferred to network participants.
Quorum decided to use multiple consensus mechanisms that are more appropriate for consortium chains than standard PoW and PoS protocols. Raft-based consensus is applied for faster block times, transaction finality, and on-demand block creation, while a PBFT-inspired consensus algorithm called Istanbul BFT ensures transaction finality.
Slock.it
Slock.it is a company that strives to expand the possibilities of blockchain adoption in IoT and has already come up with several use cases.
One of their projects is designed to develop shared economy applications and create a Universal Sharing Network (USN) on which IoT devices can be shared, sold, or rented without intermediaries. Slock.it solves the issue of scalability by reducing the number of transactions to be mined in a block. It uses the Ethereum framework and smart contract technology to allow users to control smart physical goods with the blockchain.
Slock.it has also worked with the Energy Web Foundation to combine IoT devices (smart meters) with blockchain technology to enhance the process of tracking and supplying renewable energy. Built on Ethereum, this project uses a Proof of Authority (PoA) consensus mechanism in which a pool of authorized and trusted computers called validator nodes validate transactions and create blocks. Slock.it claims that their Proof of Authority consensus implementation increases network capacity by thirty times compared to Ethereum.
VeChain
VeChain is a global public blockchain platform with a focus on advanced IoT integration. It offers solutions for various industries including logistics, agriculture, retail, and document management.
In particular, VeChain leverages the blockchain and the Internet of Things to help companies with complex logistics, inventory, and warehousing needs. The VeChainThor Blockchain is based on the PoA protocol and stores core transportation data such as temperature, humidity, and location, gathered by smart devices in real time.
VeChainThor is a public blockchain that offers multi-party payments, multi-task transactions, a controllable transaction lifecycle, and transaction dependency.
In a similar way, VeChain tries to solve issues in the agriculture industry. VeChain developers have designed a big data platform for agriculture that keeps track of all data generated during planting/breeding, production and processing, packaging, logistics, and sales.
VeChain also combines IoT and blockchain technologies for luxury goods, allowing customers to verify their products by scanning an NFC chip with the VeChain Pro App. This feature is already available for Fuji Marumo Tea Garden and sea cucumbers.
IOTA projects
IOTA is a blockless distributed ledger developed to enable micropayments in the IoT industry. It’s based on the distributed ledger technology called Tangle, which functions as a stream of entangled transactions.
IOTA has developed a partnership with several organizations to create several impressive and promising projects.
The LEGIC Secure Sensor Evaluation Kit is a programmable sensor device and Internet of Things prototyping platform. It can be used to collect specific real-time data and sell it via the IOTA Data Marketplace. This tool allows developers with all levels of programming experience to pursue projects using XDK as a starting point. All informational materials are free.
Another famous partner of IOTA is Volkswagen, which is planning to implement IoT in its cars. In 2019, Volkswagen has already implemented IoT-related trends such as autonomous driving, pWLAN technology, and artificial intelligence. With IOTA, Volkswagen plans to solve the issue of customers being restricted only to their manufacturer’s network, as IOTA is a universal protocol that is striving to become an industry standard.
Conclusion
Core blockchain technologies can potentially enhance both the security and performance of IoT networks by providing data immutability, decentralization, and smart contracts.
Both blockchain and IoT technologies are constantly developing, solving existing problems and meeting new ones. Their convergence entails certain challenges such as limited IoT resources, weak data encryption, and scalability issues, which should be taken into account by developers.
At Apriorit, we have an experienced team of blockchain developers that can enhance the security of your IoT network using blockchain technology. And our blockchain QA and blockchain pentesting specialists will help you ensure a top-notch quality of your solution. Contact us for help with projects of any complexity.




