Risk assessment is part of a holistic approach to cybersecurity and a requirement of many IT standards. Penetration testing is one of the most common (and often required) ways to assess cybersecurity risks. It’s hard to underestimate the role of penetration testing in risk evaluation: thorough testing helps you identify, assess, and prioritize risks.
Securing a software product can be overwhelming because you have to take care of all possible entry points and vulnerabilities that hackers may exploit. Before you start taking action, it’s good to lay the groundwork and determine what to protect first.
Risk assessment in cybersecurity is about identifying, assessing, and prioritizing security risks in your product. Penetration testing is an important (and often required) way to assess cybersecurity risks. By imitating a hacker attack, penetration testers uncover ways to breach the system, highlighting the parts of your software that most need protection.
In this article, we discuss three common types of security testing for risk assessment and determine their pros, cons, and use cases. We also investigate types and stages of pentesting and share best practices to make a cybersecurity risk assessment effective and painless.
Contents:
What is risk assessment in cybersecurity?
Risk assessment is the first step towards preventing cybersecurity incidents. It allows you to evaluate your system, identify weak spots, and determine which parts of your software require extra protection.
Risk assessment includes:
- Identifying vulnerabilities, threats, and risks that can cause any sort of damage to the organization
- Estimating the probability of risks being realized
- Defining mitigation priorities by risk severity and likelihood of occurrence
In risk management, assessment is preceded by framing (establishing the context of risks) and followed by responding to and monitoring risks.
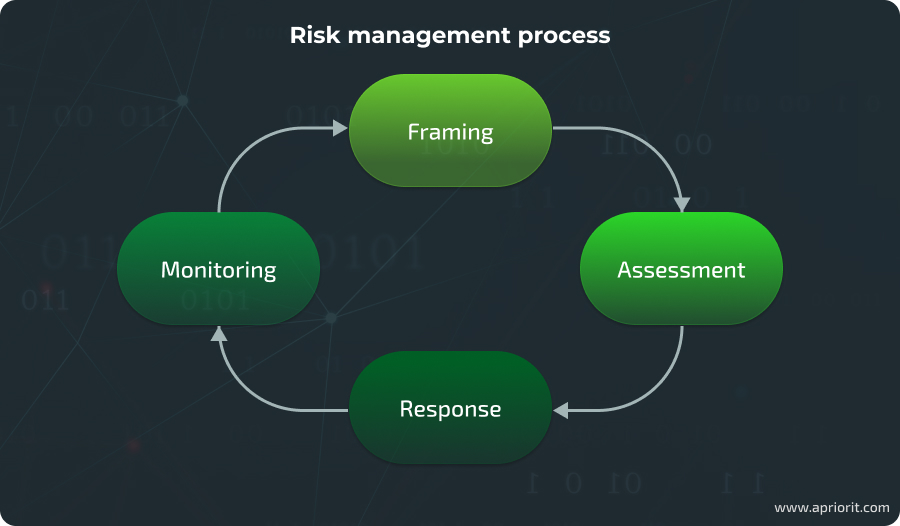
Assessing risks and threats is one of the most important steps to improving cybersecurity. It’s an ongoing process that helps you evaluate your security controls, detect issues, and estimate their impact. According to many cybersecurity standards, businesses are required to conduct risk assessments to:
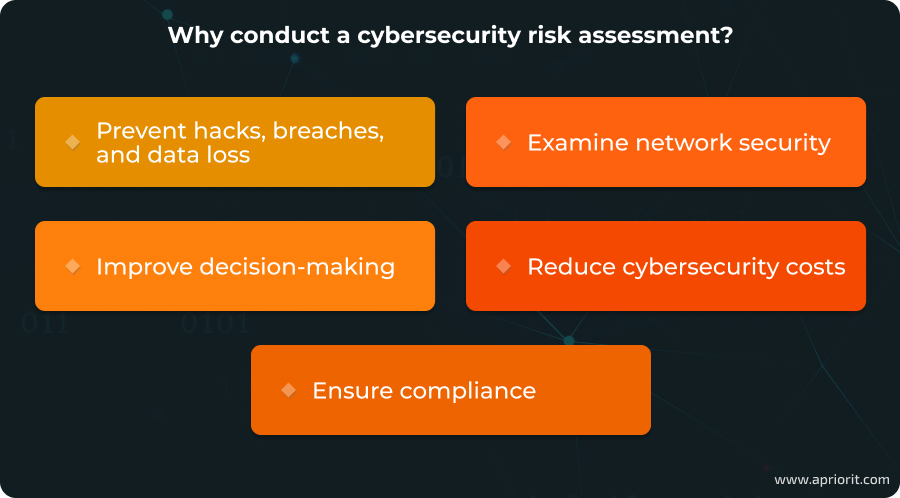
- Prevent hacks, data breaches, and data loss. Regular cybersecurity control reviews allow you to detect and eliminate vulnerabilities before hackers can exploit them.
- Examine network security. An independent risk assessment helps you update knowledge on your protected environment, especially after significant changes like deploying new software, installing new hardware, or moving to a new location.
- Improve decision-making. Determining the impact of discovered risks is an important part of a risk assessment. This information is useful for making further decisions related to cybersecurity: budgeting, planning improvements, prioritizing fixes, etc.
- Reduce cybersecurity costs. A risk assessment is time- and cost-consuming, but in the long term, it can prevent severe losses associated with compliance violations, data breaches, and reputational damage.
- Ensure compliance. Risk management is part of many laws, regulations, and standards including NIST Special Publications, HIPAA, PCI DSS, and the GDPR. Failing to comply with those relevant to your business may lead to substantial fines.
Now, let’s discuss what steps you should take to effectively assess the risks associated with your software product.
Need to protect your software from hackers?
Get bullet-proof protection for your solution with the help of Apriorit experts.
Three stages of effective risk assessment
The procedure and tools for risk assessment are unique to each organization and project. However, effective risk assessment always includes these three stages:
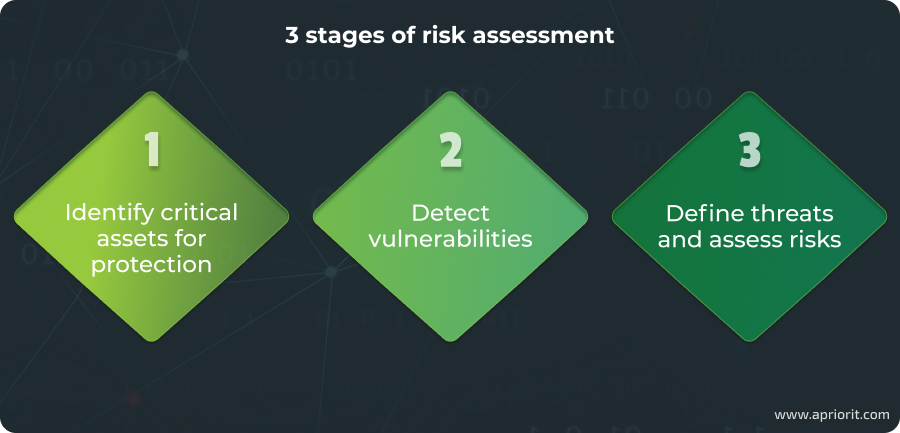
Stage 1: Identify critical assets for protection
This administrative procedure, typically carried out by the security team, involves creating a list of all data and resources that require protection. This list often includes:
- Personally identifiable information of customers and employees
- Financial data
- Trade and industry secrets
- Critical infrastructure
- And more
Stage 2: Detect vulnerabilities
This stage focuses on identifying weaknesses in the cybersecurity system. Automated vulnerability scanning is commonly used to find security issues based on known flaws in software and hardware. As a result of this analysis, you’ll get a list of vulnerabilities present in your environment.
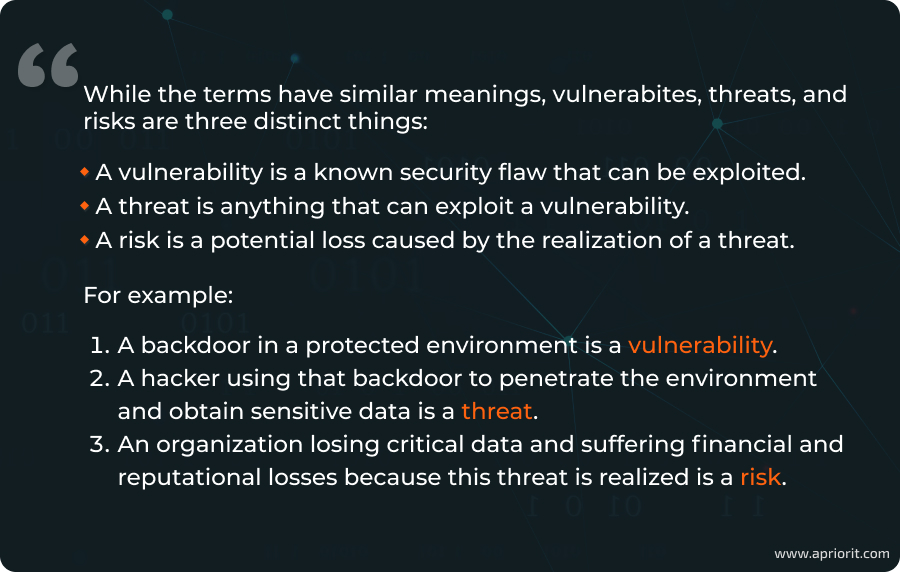
Stage 3: Define threats and assess risks
In this final stage, your team analyzes discovered vulnerabilities, explores possible exploits, and assesses the likelihood of risks occurring. It’s important to evaluate the potential consequences of each risk and its impact on the business. The result is a prioritized list of risks based on their severity and potential business impact.
You can use this list as a starting point for risk mitigation activities, prioritizing security fixes, and implementing new security controls. However, before compiling this list, it’s essential to determine your approach to assessing risks.
There are three popular approaches to conducting the third stage of risk assessment. In the next section, we analyze the workflows, strengths, and applications of each.
Related project
Vulnerability Assessment of a Protected Environment
Discover how we helped our client identify, assess, and prioritize risks in their corporate software and created a refactoring plan to eliminate all vulnerabilities.
Comparing common approaches to risk assessment
A wide range of security practices and approaches can be applied to risk assessment. The three most popular are:
- Penetration testing
- Red team testing
- Risk-based testing
Let’s learn about the pros, cons, and differences of these testing approaches.

Penetration testing simulates an attack on an organization’s cybersecurity systems and applications using both manual techniques and automated tools. During the process, testers identify potential exploits for vulnerabilities and assess the damage they could cause. Penetration testing may also involve vulnerability scanning. The main goal is to identify and evaluate all cybersecurity threats and risks to the organization.
Red team testing is similar to penetration testing but is more targeted, controlled, and strategic. Rather than attempting to exploit all vulnerabilities, red team testing focuses on specific data, security issues, and methods that mimic the actions of advanced threat actors. Red team testing must be performed by an external team to provide an outside perspective on security controls. It’s often used to evaluate security improvements made after penetration testing, but it’s not suitable for assessing the entire protected environment.
Risk-based testing is an approach to security testing that prioritizes activities based on discovered threats and risks. With this approach, testers and security experts agree on potential risks and grade them by their level of impact. Risk-based testing is best applied when a project has severe time limitations or needs urgent risk assessment and security improvements.
Let’s compare the effectiveness of these testing approaches in terms of risk assessment.
Table 1: A comparison of the testing approaches in risk assessment
| Risk-based testing | Pentesting | Red team testing | |
|---|---|---|---|
| Purpose | Prioritizing tests to cover the most probable and dangerous risks | Assessing all threats and risks | Assessing risks in a particular area |
| Characteristics | Limited time for security assessment; need for urgent testing and fixes | Periodic assessment; security checks after changing the environment | Deep investigation of certain vulnerabilities and threats |
| Conducted by | Internal security team or third-party assessor | Internal security team or third-party assessor | Third-party assessor |
| Tools | Mostly automated security testing tools | Automated and manual exploits and security testing tools | Mostly manual exploits; may include simulated social engineering and physical attacks |
| Duration | Short | Medium | Long |
| Cost | $ | $$ | $$$ |
| Result | Acceleration of security testing; fast risk mitigation and security improvements | Comprehensive report on detected risks, their level of impact, and possible losses if those risks are realized | Report with a deep evaluation of a certain security system or component of the tested environment |
Out of these three approaches, penetration testing for risk assessment is the most balanced in terms of time, costs, risk coverage, and results. Also, regular pentesting is a requirement of NIST, HIPAA, PCI DSS, the GDPR, and other standards and regulations.
Before conducting a penetration test, it’s important to know about types of pentesting and the basic workflow for this procedure.
Related project
Smart Contract Security Audit: Penetration Testing and Static Analysis
Discover how Apriorit blockchain experts identified and addressed vulnerabilities in our client’s smart contracts, enhancing their blockchain solution’s integrity and reliability.
What is penetration testing: types, workflow, and risks
Depending on your requirements, desired results, and goals, you need to select the appropriate type of pentesting, then consider what methods you’ll use and what issues you may encounter.
There are three types of penetration testing:
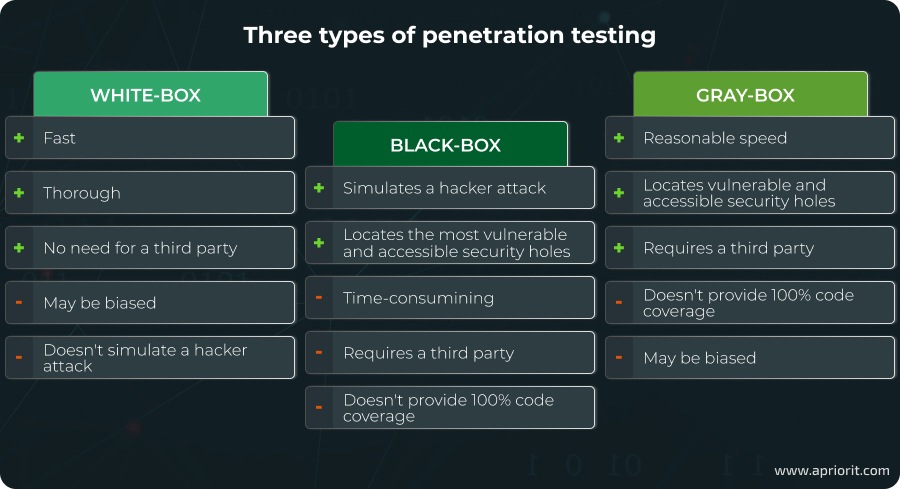
- White-box testing involves giving the testing team full knowledge of the targeted environment, including the software architecture and source code. This eliminates the need for extensive research or vulnerability scanning, allowing more time for testing activities. Instead of actively exploiting vulnerabilities, testers focus on proving the possibility of exploitation. This makes white-box testing particularly effective for mitigating insider threat risks because pentesters have all the information needed to assess the vulnerabilities that an insider could exploit. White-box testing methods include DoS attacks, memory forensics, physical break-ins, reverse engineering, and fuzzing.
- Black-box testing involves a testing team with little to no prior knowledge of the target environment. Testers rely on publicly accessible information and simulated outsider attack methods, replicating the approach of real-world hackers. While time-consuming, this approach offers an objective assessment of security vulnerabilities and risks. Black-box testing is typically performed by external organizations, and your IT team should remain unaware of the test to ensure authenticity. Unlike white-box testing, black-box testing focuses more on reconnaissance and uses methods such as vulnerability scanning, social engineering, brute forcing, privilege escalation, and creating or using malware to breach the system. Physical attacks are usually excluded.
- Gray-box testing is a combination of white-box and black-box testing. In this method, the testing team is given limited information about the target environment, such as application documentation, but no access credentials or source code. This approach is less time-intensive than black-box testing but offers less comprehensive code coverage than white-box testing. Gray-box testing is typically conducted by third-party testers, as they bring an unbiased perspective and can effectively assess security with limited insider knowledge.
Each of these testing types has its own workflow. However, similar to the risk assessment procedure, there are three phases common to any pentesting.
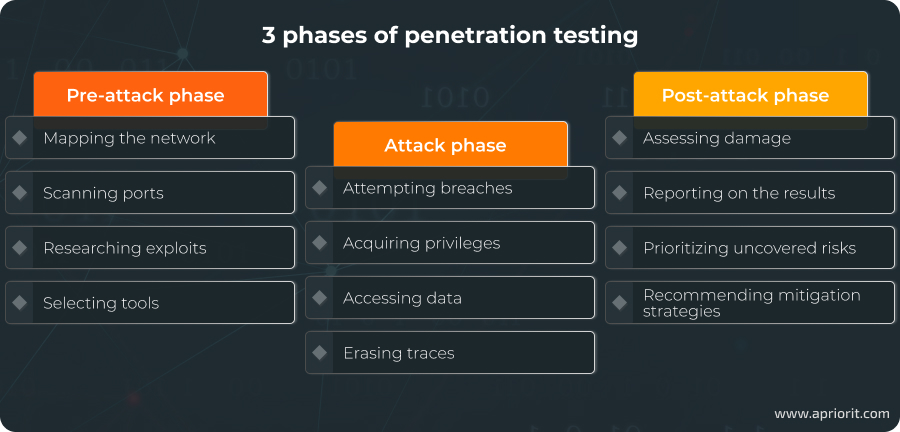
First, there’s a pre-attack phase that’s devoted to preparation: mapping the network and perimeter, scanning ports, researching exploits and known vulnerabilities, selecting tools, etc. In black-box testing, this phase also includes gathering information on the targeted organization and its employees. Preparation is the most time-consuming phase of penetration testing, but it’s also the most important.
During the attack phase, testers attempt to compromise the target network by breaching the protected perimeter, acquiring or escalating privileges, accessing data, and erasing traces.
Finally, the post-attack phase consists of assessing potential damage and reporting on the results of the pentesting process. A report is the culmination of the risk assessment process and usually includes:
- Discovered vulnerabilities (if scanning for them was included in the scope of pentesting)
- A description of the methodology and tools used during testing
- A list of exploits (both used and possible)
- Analysis and severity of the risks these exploits may pose
- An assessment of the possible business impact of the discovered risks
- Recommendations on risk mitigation
With this report, you can proceed to the next stages of risk management: risk mitigation and control. For example, using pentesting results, you can:
- Assess the current state of security controls
- Observe how your security team reacts to a hacker attack
- Make the case for increasing your cybersecurity budget
- Define and prioritize security improvements
- Create hotfixes and take long-lasting mitigation actions
From healthcare and FinTech to cybersecurity and automotive penetration testing — this testing approach can significantly improve software resilience for any industry.
As we can see, pentesting is a great method for assessing cybersecurity controls and risks. But it’s important to keep in mind the risks of penetration testing. Let’s find out about them in the next section.
Read also
Dependency Impact Analysis in Software Testing and Development: What It Is and How to Do It (with Examples)
Ensure your product remains stable and secure after every update. Explore our expert guide for impact analysis best practices and get a template for securing your product’s dependencies.
Key considerations of penetration testing
If conducted by an inexperienced tester or without due attention, penetration testing can cause more damage than benefits. Before conducting it, you need to consider its major drawbacks.
Here are some key penetration testing risks:
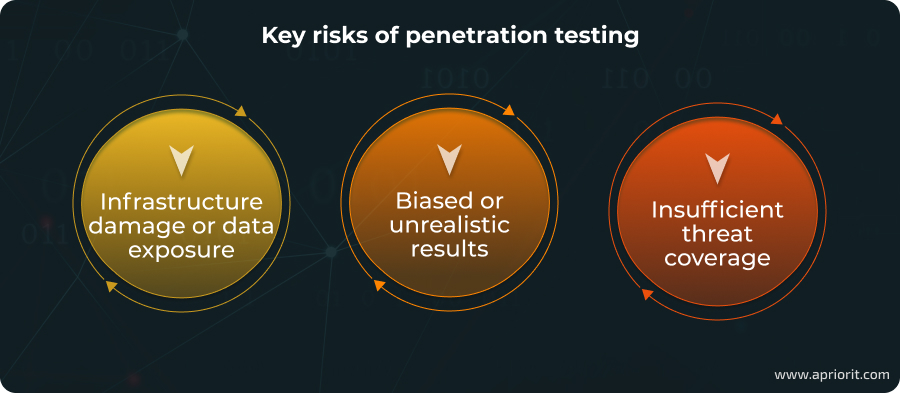
- Infrastructure damage or data exposure. Pentesters work with sensitive data and infrastructure. If tests aren’t carried out properly, they can crash servers and expose or corrupt data. It’s a security risk to be considered, especially during black-box testing.
- Biased or unrealistic results. If your security team knows about an upcoming test or conducts the test themselves, they may prepare for it. The point of any security assessment is to get a reality check and prioritize future improvements. If pentesting is conducted in an unrealistic environment, there’s little hope for meaningful results.
- Insufficient threat coverage. As with any process, there’s a technical task for pentesting and a due date for preparing a report. This limits the number of vulnerabilities pentesters can exploit, especially if you employ a third-party testing organization. Hackers, on the other hand, usually have unlimited time to plan an attack. Therefore, you can’t rely on the results of one instance of penetration testing to improve cybersecurity, especially if the testing is severely time-limited.
Still, if conducted correctly, pentesting brings more benefits than risks. Also, there are several best practices that can help you handle the issues we’ve discussed.
Best practices to maximize pentesting results
Each testing team has a unique penetration testing methodology, and each procedure has a unique outcome. We’ve prepared a list of actions that can help you get the best result from this security evaluation.
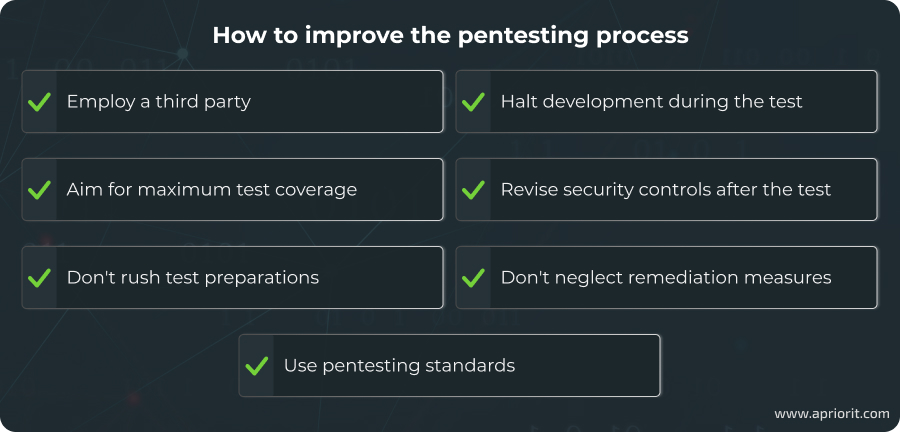
- Employ a qualified third party to conduct penetration testing
Running in-house testing is tempting because it saves lots of time and money. However, it doesn’t guarantee unbiased results due to:
- Potential lack of expertise
- Unrealistic conditions
- Inability to simulate a real attack
- Team’s knowledge of the system’s inner workings
With a third-party organization, you’ll get dedicated pentesters and a fresh take on your security controls. Before starting a pentest, discuss your scope, budget, time limits, and results of previous pentesting with your vendor.
- Aim for maximum test coverage
Any software is an interconnected system, so testing should evaluate it as a whole rather than as isolated components. Even if a specific part of the software environment has been tested and secured, hackers may still exploit vulnerabilities in the operating system, hardware, or other software to access it. Low test coverage or partial testing can create a false sense of security. This approach is only advisable for rechecking security patches applied after a comprehensive penetration test.
Read also
Web Application Penetration Testing: Minimum Checklist Based on the OWASP Testing Guide
Identify vulnerabilities before hackers do to safeguard your software from cyber threats with our comprehensive guide to penetration testing using the OWASP checklist.
- Don’t rush test preparations
During the pre-attack stage, testers assess vulnerabilities, weaponize themselves, and prepare test scenarios. But from outside the testing team, it might look like nothing is happening as there’s no actual testing going on. It’s okay to ask about the testing process from time to time, but make sure not to rush the preparation stage. Remember that this is a time-consuming process. For black-box testing, this stage sometimes can take up to 90% of the total estimate.
- Use relevant pentesting standards
Each tested environment requires a unique approach. Still, there are world-renowned and industry-recognized standards for penetration testing. Use these standards to guide your internal team or make sure your third-party vendor uses it. The most popular ones are:
- Penetration Testing Execution Standard
- OWASP Web Application Penetration Checklist [PDF]
- PCI DSS Penetration Testing Guidance [PDF]
- CREST Penetration Testing Guide [PDF]
- Halt development processes when pentesting
Pentesting uncovers threats and risks within some context in the environment. If you decide to change existing parameters or deploy new software during the test, it will jeopardize the result. It’s best to finish your development activities before the test to include new pieces of the environment in the testing scope.
- Review the integrity of security measures and data after the test
After the security risk assessment with penetration testing is done, the testing team should cover their tracks: close created backdoors, delete exploitation scripts and temporary files, reverse settings changes, etc. However, you should double-check that:
- Security holes created for testing purposes are closed
- User accounts for testers are deleted
- Compromised credentials are changed
- Don’t neglect remediation measures
Penetration testing vendors often provide suggestions for risk remediation in their reports. If testing is conducted rarely (once a year or less) or includes a large scope of tasks, it will probably uncover many critical risks, and remediation actions will require a substantial amount of time and money.
Of course, to cut costs, you can postpone remediation or fix only the most critical issues. But if you don’t have enough resources to act upon the results of pentesting, it’s best to limit yourself to internal vulnerability scanning instead of conducting a full-scale pentest.
Conclusion
Risk assessment is a challenging yet essential component of the risk management process. It can help your organization identify, evaluate, and prioritize risks and their mitigation, thus saving you time and money on cybersecurity efforts. Penetration testing and risk assessment often come together, as pentesting is one of the most important ways to accurately identify risks. It imitates hacker attacks and can highlight your system’s real vulnerabilities.
At Apriorit, we have vast experience conducting both penetration and security testing. Our team includes testers with Systems Security Certified Practitioner certifications. Our combination of theoretical knowledge, practical experience, and motivation to study new testing tools and approaches allows us to conduct the most thorough tests and assessments. With us, you can get a clear roadmap towards your product’s protection — you will know exactly what to improve and how to ensure the safety of your data and infrastructure.
Looking for expert pentesters?
Tap into our extensive experience in penetration testing to uncover your software’s vulnerabilities before hackers do!




