Establishing and maintaining IT compliance in software development is a proven way to deliver a protected product, prove your trustworthiness to customers, and contribute to your product’s success. But with an ever-growing number of IT laws, regulations, certifications, and standards, ensuring compliance becomes challenging. Additionally, failing to comply with requirements can lead to costly penalties and lawsuits.
That’s why one of the first steps in any software development project at Apriorit is identifying and documenting relevant compliance requirements. In this article, we share ways to determine these requirements, practices to deliver a compliant product, and our experience with common security laws and standards.
This article will be useful for development leaders and product owners who want to deliver a new product to highly regulated markets.
Contents:
The role of software development compliance
Software released to the market (and even software for a company’s internal use) must comply with government and industry rules. The main goal of compliance requirements is to ensure the security and reliability of software products and the data they contain.
Many articles online use the terms certification, standards, regulations, and laws interchangeably, but they do not refer to the same thing. Let’s examine how NIST defines these terms:

Some sets of requirements are mandatory for software in a specific field (HIPAA for healthcare, PCI DSS for finance) or regions and countries (the GDPR for EU organizations, FISMA for those in the US). Compliance can also be optional. For example, while no one is legally required to adopt ISO 27001, many companies still require their partners and suppliers to be compliant.
Whether compliance is mandatory or optional for your company, achieving it will bring the following benefits:
Improve cybersecurity posture. Laws, standards, and certifications enforce cybersecurity best practices that are proven to protect organizations from various security incidents. They define which types of data should be guarded with which security mechanisms. You can use compliance requirements as guidelines for establishing reliable protection mechanisms and processes for your sensitive data.
Build trust in your company. Strict compliance with cybersecurity requirements is a sign of a mature company that values its users’ sensitive data. Demonstrating compliance can help you build a public image as a trustworthy company and attract more potential clients and investors.
Ensure business continuity. Security requirements help companies build protected, resilient, and efficient processes. They reduce the chance of experiencing a security incident, and if one occurs, they dictate how an organization should handle it to minimize the consequences.
Avoid penalties and legal issues. Non-compliance with government laws, regulations, and standards can result in penalties and possible lawsuits. The severity of these penalties depends on the scale of non-compliance and its consequences. For example, non-compliance with the GDPR can cost a company up to €20 million or 4% of total global yearly turnover, whichever is higher.
Plan on ensuring compliance for your next product?
Get a dedicated team experienced in delivering high-quality software compliant with numerous government and industry requirements.
5 key factors to determine relevant compliance requirements
The first step to ensuring software compliance is figuring out which sets of requirements you have to or want to comply with. During the project discovery phase, a business analyst (BA) gathers information on your product and uses it to research relevant requirements.
In their research, a BA takes into account the following factors:
Industry. Some government regulations and industry standards apply only to software that caters to a specific industry. For example, only medical software has to meet HIPAA and HITECH requirements, and only educational applications have to comply with FERPA.
Location. Most countries and regions have their own laws and regulations for IT compliance. You have to follow both your local laws and regulations of the countries in which you operate, employ people, or sell your products. For example, a US-based public company that wants to operate in the EU will have to comply with both the Sarbanes-Oxley Act and the GDPR.
Stored data. Compliance requirements apply not only to businesses from specific locations and industries but also to the data you or your users store. Requirements usually secure sensitive data like personally identifiable information, medical and financial data, records that contain intellectual property, and so on. Even if your software doesn’t provide financial services but stores records like credit card information, for example, it still has to comply with PCI DSS.
Processes and technologies. Some requirements apply to software that implements particular tools and technologies. For example, many countries are developing or have already implemented regulations regarding the use of artificial intelligence, like the AI Bill of Rights in the US and the AI Act in the EU.
Organization size. Laws, standards, and regulations sometimes apply different sets of requirements depending on a company’s size. For example, Article 30 of the GDPR states that organizations employing fewer than 250 people don’t have to follow some of the data processing activities the regulation describes.
Related project
Improving a SaaS Cybersecurity Platform with Competitive Features and Quality Maintenance
Explore how we helped our client attract end users from highly regulated industries with their compliant software, We can assist you in fixing issues and establishing compliance with various industry requirements.

Establishing and maintaining software development compliance: best practices from Apriorit
To ensure a product’s compliance, we start researching and preparing for it from the earliest development stages. This approach allows us to take mandatory requirements into account during all crucial development activities, including when choosing the architectural design, functionality, and third-party integrations.
Here are key practices that help us deliver compliant software:
1. Identify all requirements to follow. It’s best to start identifying relevant requirements as early as possible in the software development process. Many clients already know the key standards and regulations they need to comply with and warn us during pre-sale or project discovery. On top of their input, Apriorit’s business analysts conduct their own requirements research.
Note that sometimes software has to comply with unobvious requirements or be partially compliant. For example, we helped one of our clients develop a CRM system for medical transportation. Since this system mainly covered transport-related information, it didn’t have to wholly comply with healthcare requirements. However, we still needed to implement access control features to protect patient information, as it is protected by HIPAA.
2. Reflect requirements in documentation. Project documentation must describe compliance requirements in detail, as well as measures and procedures the development team needs to implement to achieve compliance. The team has to know in advance if they will need to implement cybersecurity features like activity monitoring and logging, data backups, and encryption. This information helps them to design a software architecture and plan the development process to accommodate compliance requirements and avoid rework in the future.
3. Conduct an internal compliance audit. If you need to make existing software compliant, it’s best to start by assessing its current state of cybersecurity as well as the practices your development team uses. This way, you can get an accurate picture of your current compliance and can plan implementation of only the requirements your product lacks.
4. Cover missing requirements. During this stage, the development team implements cybersecurity mechanisms to ensure compliance. To align new features with IT regulations and laws, your team can use the compliance as code approach, which implies writing compliance policies as code that can be repeated, tested, and automated. Then, the quality assurance (QA) team verifies that the implemented mechanics satisfy the project’s functional and non-functional requirements.
5. Leverage compliance management tools. Implementing needed requirements is only half of the job required to deliver compliant software. After the release, software often changes in terms of its scale, infrastructure components, and feature set. You need to make sure that all of these changes correspond to legal requirements.
One way to maintain compliance in the long run is to adopt a compliance management system. Such a system provides tools to monitor compliance with laws, standards, and internal company policies, help conduct internal audits, and alert administrators when deviation from requirements is discovered. While it’s possible to do these tasks manually, using a dedicated system automates routine activities for the development team and helps your team discover cases of non-compliance faster.
6. Monitor compliance-related changes. Laws, regulations, and standards change over time, introducing new security requirements. Monitoring these changes and implementing new requirements is key to keeping your software compliant. Another challenge to maintaining compliance is major product updates that introduce new functionalities or change a product’s market positioning.
For example, one of our clients who delivered a cybersecurity platform wanted to market their software as a forensic product. To do that, they requested our help in adding new security features like data protection auditing capabilities, implementing additional encryption algorithms, and checking and ensuring backward compatibility. Adding these features allowed our client’s software to comply with requirements for forensic products.
To ensure that software meets a certain set of requirements, a business analyst and development team need a full understanding of the difficult environment to create specifications that fully cover compliance requirements. Let’s take a look at the requirements and penalties described in the five most common IT compliance documents.
Read also
Guide to Building GDPR Compliant Software: 5 Software Development and Testing Tips
Explore our practical tips for delivering compliant software to avoid security incidents and costly penalties for non-compliance.
Meeting requirements of 5 common IT laws, regulations, and standards
At Apriorit, we have experience delivering projects according to requirements put forth by various countries and industries. Let’s take a look at the applications of, requirements of, and penalties for violating some of the requirements we often face in our projects.
HIPAA
The Health Insurance Portability and Accountability Act defines policies, procedures, and guidelines for protecting sensitive patient data. To meet HIPAA requirements, organizations working with protected health information (PHI) must implement and follow network, physical, and process security measures.
HIPAA is applicable to the following US-based entities:
- Covered entities — Organizations directly involved in providing medical treatment and in collecting, creating, or transmitting PHI electronically. This includes medical practitioners, healthcare clearinghouses, and health insurance providers.
- Business associates — Organizations who access PHI in any way while performing contracted services on behalf of a covered entity. This includes electronic health record vendors, consultants and auditors, billing companies, IT providers, managed service providers, etc.
Your project should comply with HIPAA if:
- The entity that will use your software is a covered entity or business associate.
- Your software will use, share, or store PHI (any identifiable data about the patient, including names, addresses, phone numbers, medical records, social security numbers, and photos).
There are five main HIPAA compliance rules.
- Privacy Rule — restricts the use and disclosure of PHI so that only the patient has complete control over their information to minimize the possibility of data being stolen.
- Security Rule — outlines the required protection for electronic PHI from being accessed, copied, or destroyed by unauthorized entities.
- Breach Notification Rule — defines the steps an organization must take if a breach occurs.
- Enforcement Rule — regulates all fines that may be applied to companies.
- Omnibus Rule — modifies previous requirements and strengthens the data privacy policy.
Penalties for HIPAA violations range from $100 to $1,500,000 depending on the cause of the incident, the violator’s knowledge of the incident, and the violator’s willingness to fix the violation in a timely manner.
GDPR
The General Data Protection Regulation (GDPR) is a set of requirements designed to safeguard personal information of people within EU borders. The regulation applies to any organization that collects, stores, and processes such data.
The GDPR protects a wide range of user information:
- Personal data such as names, physical addresses, and identification numbers
- Web data such as location, device information, and IP address
- Health and genetic data
- Biometric data
- Racial and ethnic data
- Political opinions
- Union memberships
The GDPR enforces seven key principles of data protection:
Fines for violating the GDPR can get as high as €20 million or 4% of an organization’s annual revenue.
Related project
Developing a Custom Secrets Management Desktop Application for Secure Password Sharing and Storage
Our client needed internal secrets management software that complies with SOC2, SOC3, C5, ISO 27001, and the GDPR. With the solution we developed, the client was able to improve their data protection and cybersecurity posture.

ADA
The Americans with Disabilities Act (ADA) establishes standards to prevent discrimination based on disability in public accommodations, employment, transportation, and telecommunications. It can also be applied to websites of businesses, websites operated by federal, state, and local authorities, and sites funded by government bodies.
In general, ADA applies to:
- Organizations and businesses with 25 or more employees
- Businesses in the private and public sectors
- Government bodies
- Businesses that are open to the public
Since ADA doesn’t provide clear accessibility requirements for websites, most web development teams follow Web Content Accessibility Guidelines (WCAG) to comply. WCAG categorizes accessibility requirements into four groups:
- Perceivable – All information, including user interface components, must be shown clearly (e.g., video content must have subtitles).
- Operable – All users must be able to use the interface without restrictions (e.g., a user should be able to interact with all website functions with keyboard-only commands).
- Understandable – The interface and possible actions must be clear for users (e.g., error messages should be clear and include an explanation of what went wrong and how to correct it).
- Robust — Different assistive technologies can interpret a website’s content (e.g., the site should be compatible with all leading screen readers).
Fines for lack of accessibility of digital products and breaking the ADA range from $55,000 to $75,000 for first-time violations to $150,000 for every repeat violation.
NIST 800-171
National Institute of Standards and Technology Special Publication 800-171 (NIST SP 800-171) provides recommendations for protecting the confidentiality of controlled unclassified information (CUI), which is any information that is not classified but should be protected. For example, CUI can include personally identifiable information, proprietary and confidential business records, sensitive but unclassified law enforcement data, and so on.
Complying with NIST SP 800-171 is mandatory for any organization that has a federal contract and processes or stores CUI. Without NIST SP 800-171 compliance, an organization can’t work with US government entities.
NIST 800-171 consists of 14 families of cybersecurity requirements grouped by security topics:
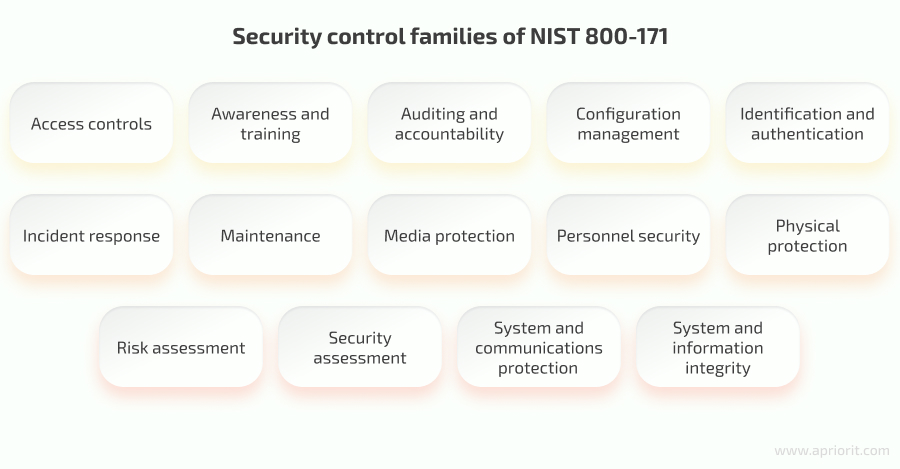
This standard doesn’t set strict non-compliance penalty frameworks, but it can result in fines, contract termination, and damages pursued by the US government.
PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) is a widely accepted set of policies and procedures intended to optimize the security of credit, debit, and other payment card transactions.
Any organization and software that manages cardholder data and payment transactions must comply with PCI DSS. This standard has four levels of compliance and requirements that depend on the number of transactions a company processes annually.
There are 12 requirements to be PCI DSS–compliant:
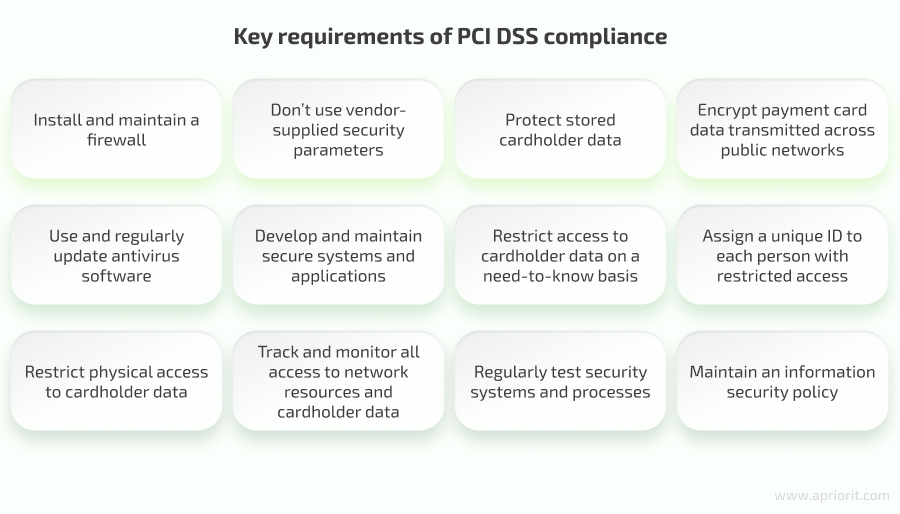
Credit card brands can penalize companies that do not meet PCI DSS with monthly fines from $5,000 to $100,000 until a company implements missing requirements.
Conclusion
Any software that manages sensitive records has to comply with IT security laws, regulations, and standards. Figuring out relevant requirements early in a development project helps you to build a well-protected solution, take compliance requirements into account when designing the software architecture, and streamline the development process.
Apriorit’s business analysts and dedicated development teams successfully deliver applications compliant with both widely applicable and niche regulations and standards. We start working on IT compliance at the project discovery phase, researching and documenting all relevant requirements for a product and ensuring the delivery of compliant software with rigorous QA.
Plan on developing software for a highly regulated industry?
Get yourself a team of experts who know how to plan, develop, and test compliant products.



