Key takeaways:
- The Cyber Resilience Act makes cybersecurity a built-in part of product development, not something added after release.
- Most CRA challenges come from product architecture and development processes, and fixing them late can become costly in the long run.
- Any company selling digital products in the EU must consider CRA requirements, regardless of where the company is based.
- Starting early with readiness assessments and secure development practices is the safest way to reduce compliance risks and penalties.
The EU Cyber Resilience Act (CRA) introduces a dedicated regulatory framework for how digital products are designed, developed, and maintained from a cybersecurity perspective. Unlike earlier regulations that addressed security primarily at the organizational or data protection level, the CRA directly targets product development. It requires cybersecurity to be built into product architectures, development processes, and long-term maintenance from day one.
In this article, our experts break down what the Cyber Resilience Act means in practice. You’ll learn who it applies to, what core security requirements it introduces, how timelines and penalties work, and what concrete engineering and SDLC changes are needed to prepare for compliance.
This EU Cyber Resilience Act guide has been created for CTOs, CIOs, CISOs, and tech decision-makers who need actionable insights into how CRA compliance affects product strategy, development workflows, and market access.
Contents:
- What is the EU Cyber Resilience Act?
- CRA timelines and transition periods (2024–2027)
- Core CRA requirements explained
- Penalties and risks of non-compliance
- How to prepare for the CRA: A practical step-by-step framework
- Step 1. Define the scope and classify security-critical components
- Step 2. Assess security and compliance gaps
- Step 3. Modernize high-risk architecture components
- Step 4. Implement a secure SDLC approach
- Step 5. Build systems for vulnerability management and disclosure
- Step 6. Set up SBOM automation and supplier validation
- Step 7. Prepare technical documentation to assess conformity
- How Apriorit can help you build CRA-aligned solutions
What is the EU Cyber Resilience Act?
The EU Cyber Resilience Act (CRA) is a landmark regulation that fundamentally changes how digital products are designed, built, and maintained. Unlike previous EU cybersecurity initiatives that focused on organizations or critical infrastructure, the CRA directly targets products with digital elements, including software, firmware, and connected devices.
The goal of the Cyber Resilience Act is to raise the minimum cybersecurity baseline for all digital products sold in the EU. The regulation addresses a long-standing gap where many connected products reached the market with weak default security, unclear update mechanisms, and no long-term strategy for handling vulnerabilities.
The CRA introduces binding requirements to make sure that:
- Digital products are secure by design and by default
- Known classes of vulnerabilities are proactively mitigated
- Security is maintained throughout the entire product lifecycle
From an engineering perspective, the CRA effectively infuses cybersecurity into architectural decisions, SDLC practices, and long-term maintenance planning.
Classification of digital products under the CRA
Many modern products are built on multiple elements such as firmware, cloud services, and mobile applications. This is why determining whether the CRA is applicable requires careful architectural and functional analysis instead of a simple software vs hardware distinction. The CRA defines three product categories based on their risk profile and potential impact.
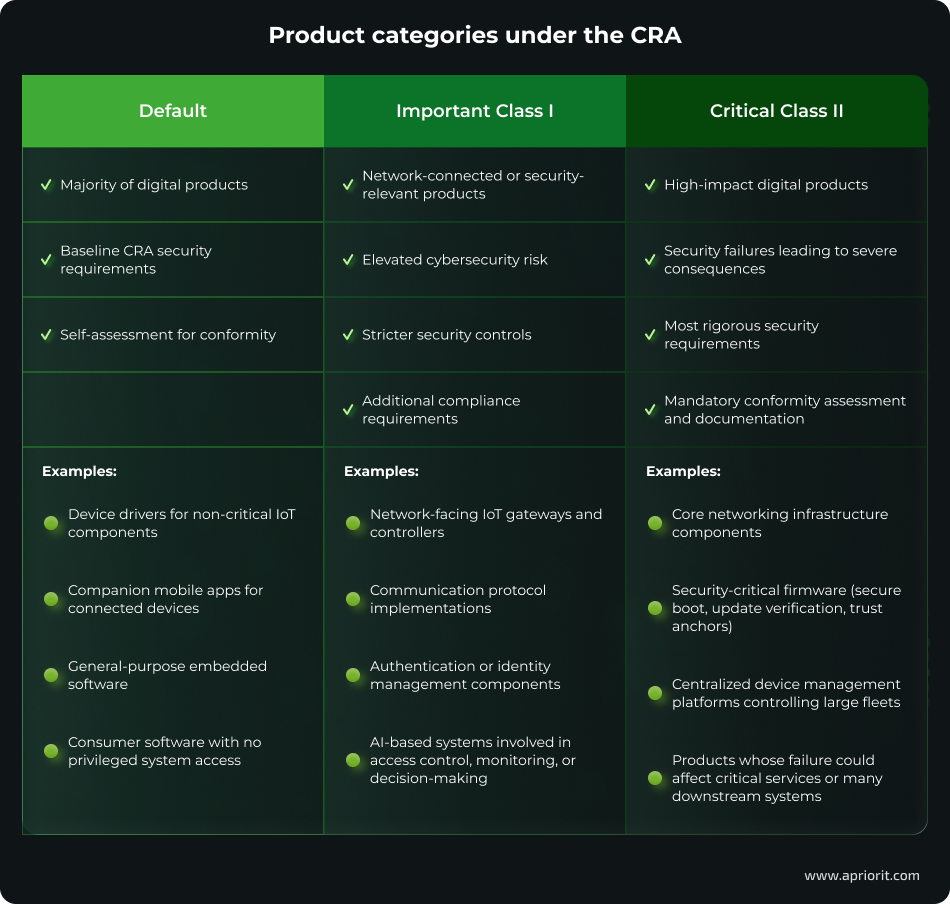
Development teams need to understand their product’s CRA classification early on. This helps determine how deeply security must be embedded into architecture, development, and maintenance processes.
Who needs to comply with the Cyber Resilience Act?
The CRA is a European Union regulation, but mandatory compliance is not limited to EU-based companies. If you intend to sell or distribute digital products in the European Union, the CRA applies to you, regardless of where your company is headquartered or where development takes place.
The CRA does not apply to everyone distributing software in the EU. Instead, it targets defined categories of economic operators involved in placing products on the market, including hardware manufacturers, software vendors, importers, distributors, and retailers acting as manufacturers, regardless of where they are based.
There are several notable exclusions and special cases where the CRA does not apply:
- Non-commercial open-source software
- Pure SaaS with no direct link to a product with digital elements
- Products for certain regulated industries (for example, medical devices, aviation, and marine equipment)
Products that fall under these exclusions may be governed by sector-specific regulations or other cybersecurity limitations. Understanding when specific CRA obligations apply is the first step toward building a realistic compliance roadmap.
Build CRA-ready products with confidence
Apriorit helps product teams strengthen cybersecurity and address EU Cyber Resilience Act requirements across architecture, development, and testing.
CRA timelines and transition periods (2024–2027)
The CRA provides different compliance timelines for new and existing products:
- New products are digital products placed on the EU market after CRA obligations go into effect.
- Existing products are those already placed on the market before CRA obligations go into effect but that are still subject to specific CRA obligations, such as vulnerability handling and incident reporting.
In practice, this means that existing products cannot ignore the CRA. Vendors must maintain an acceptable level of cybersecurity throughout the remaining product lifecycle, even if full architectural changes are deferred. Let’s take a look at the CRA timeline.
Table 1. CRA compliance roadmap
| Timeframe | CRA status | Who is affected | Key obligations | What must be done by this stage |
|---|---|---|---|---|
| 2024 | CRA adopted, transition period begins | All product vendors targeting the EU | No direct obligations yet | ✔️Start CRA impact assessment ✔️Identify product scope and classification ✔️Review architecture and SDLC gaps |
| 2025 | Preparation phase | Manufacturers, software vendors, importers | Still no direct obligations | ✔️Design secure-by-design architectures ✔️Plan vulnerability management processes ✔️Define SBOM approach ✔️Prepare OTA/update mechanisms |
| September 2026 | Vulnerability obligations become mandatory | New and existing products | ❗Vulnerability handling process required ❗Coordinated vulnerability disclosure ❗Incident reporting | ✔️Operational vulnerability response workflows ✔️Patch delivery pipelines ✔️Internal security ownership defined |
| Late 2026 | Final readiness window | All in-scope products | Full CRA requirements approaching | ✔️Complete technical documentation ✔️Finalize conformity assessment strategy ✔️Validate update, logging, and monitoring mechanisms |
| December 2027 | Full CRA enforcement | New products placed on the EU market | ❗Secure-by-design compliance required ❗Conformity assessment mandatory | ✔️Only CRA-compliant products can be sold in the EU ✔️Ongoing lifecycle security enforcement |
Implementation of the CRA is phased in order to give manufacturers and software vendors time to adapt their products, development processes, and security practices. However, this transition is not passive: key preparation activities must start well before full CRA enforcement. Next, we explore what the CRA demands from those to whom it applies.
Core CRA requirements explained
The Cyber Resilience Act translates into a set of mandatory engineering, process, and documentation controls. While all products must meet a common baseline, the depth of controls, documentation, and assessment increases for higher-risk product categories.
In other words, CRA requirements apply across all categories, but Important Class I and Critical Class II products face stricter implementation and conformity obligations.
Our experts have created an overview of the core requirement areas related to the CRA for your convenience.
Table 2. Core CRA requirements
| Principle | Key controls | CRA class |
|---|---|---|
| Secure-by-design & secure-by-default principles | ✔️Security built into design ✔️Threat modeling applied early ✔️Hardened product architecture ✔️Reduced attack surface by default ✔️Memory-safe critical components ✔️Secure boot and firmware integrity | Default: Baseline Important Class I: Enhanced Important Class II: Most rigorous |
| Mandatory vulnerability management | ✔️Vulnerability intake process ✔️Coordinated Vulnerability Disclosure (CVD) ✔️Defined remediation ownership ✔️Timely security fixes ✔️Continuous risk tracking | Default: Required Important Class I: Stricter timelines Important Class II: Strictest controls |
| Security update & patch delivery mechanisms | ✔️Secure update channels ✔️OTA updates for IoT ✔️Update integrity verification ✔️Coordinated device–cloud updates ✔️Rollback and tamper protection | Default: Required Important Class I: Advanced mechanisms Important Class II: Full lifecycle assurance |
| Logging, monitoring & incident reporting | ✔️Security event detection ✔️Centralized logging ✔️Protected log storage ✔️Incident escalation rules ✔️Mandatory incident reporting | Default: Required Important Class I: Expanded scope Important Class II: Mandatory reporting and audits |
| Documentation & conformity assessment | ✔️Technical compliance files ✔️Risk assessment records ✔️SBOM creation and updates ✔️Evidence of controls ✔️Class-based conformity assessment | Default: Self-assessment Important Class I: Extended documentation Important Class II: Third-party assessment |
Instead of prescribing specific technologies, the act defines outcome-based security requirements that manufacturers and software vendors must meet throughout the product lifecycle. Now, let’s see what penalties organizations will face for not meeting CRA requirements in a timely manner.
Penalties and risks of non-compliance
The CRA gives regulators strong enforcement tools that can affect a product’s ability to remain on the EU market. Non-compliance with the EU Cyber Resilience Act creates direct financial, operational, and strategic risks.
Table 3. Penalties and risks of non-compliance
| Risk type | Impact |
|---|---|
| Financial | ❌ Fines up to €15M or 2.5% of global turnover ❌ Additional penalties for repeated violations |
| Market access | ❌ Product withdrawal or recall ❌ EU sales ban until compliance is restored |
| Operational | ❌ Emergency remediation ❌ Unplanned engineering costs ❌ Delayed launches |
| Reputational | ❌ Loss of partner and customer trust ❌ Increased regulatory scrutiny ❌ Competitive disadvantage |
Addressing CRA requirements early is significantly cheaper and safer than reacting after enforcement begins. To turn compliance from a regulatory requirement into an actionable engineering plan, companies need a structured approach that includes compliant architecture, development processes, vulnerability management, and documentation. In the next section, we outline what steps you can take to prepare yourself for the upcoming deadlines.
Read also
6 Emerging Cybersecurity Trends for 2025 to Futureproof Your Product
Learn which security trends are becoming critical for modern software development. Our experts share insights that can help you anticipate risks, align development efforts, and support greater product resilience.

How to prepare for the CRA: A practical step-by-step framework
EU Cyber Resilience Act compliance requires coordinated changes across architecture, development processes, security operations, and documentation. The Cyber Resilience Act can’t be implemented through a single audit.
Our experts have broken down CRA preparation into clear steps that you can realistically execute, whether you’re building a new product or adapting an existing one.
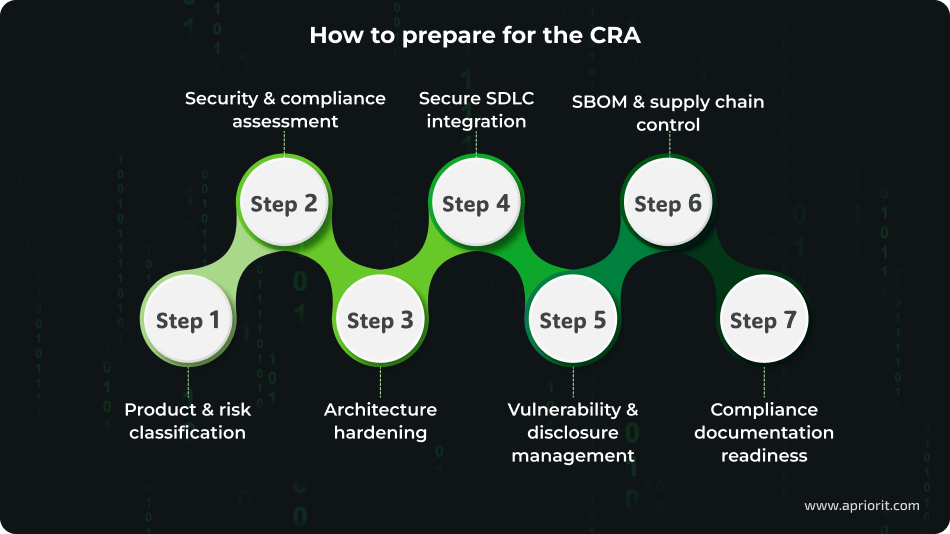
Step 1. Define the scope and classify security-critical components
CRA compliance depends not only on the product category but also on which components are security-critical. In practice, this step includes:
- Identifying components that affect authentication, authorization, updates, or data integrity
- Determining which failures could lead to the compromise of the entire system
- Separating components by their security level
- Aligning security depth with Default, Class I, or Class II expectations
If your team misclassifies components, the result could be non-compliance (regulatory risk) or over-engineering (cost and time overruns).
Apriorit expert tip: We recommend classifying components, not just products. This allows your team to apply targeted and relevant security controls and optimize development efforts.
Step 2. Assess security and compliance gaps
A CRA assessment should:
- Map all digital elements of the product: firmware, OS, drivers, backend services, APIs, mobile apps, cloud components
- Identify trust boundaries and privilege levels between components
- Review how credentials, keys, and secrets are generated, stored, and rotated
- Assess update mechanisms, including rollback protection and failure handling
- Evaluate existing logging, monitoring, and incident response capabilities
The final result of this step should be a gap map that clearly shows which CRA requirements are currently unmet. Your teams will also learn which requirements call for architectural changes instead of configuration fixes.
Apriorit expert tip: Assessing legacy components is challenging for many teams. You might need reverse engineering and firmware analysis to assess security posture when documentation is incomplete or outdated.
Step 3. Modernize high-risk architecture components
Once your CRA readiness assessment has identified which requirements cannot be addressed through configuration or process changes, the next step is targeted architectural modernization. Most CRA blockers are architectural instead of procedural. Legacy design decisions often prevent teams from meeting secure-by-design, update, and vulnerability management requirements without structural changes.
Your team should focus on introducing or strengthening the following controls, depending on product type and risk profile:
- Root of trust and secure boot, which are applicable to embedded devices, firmware-based products, and security-critical components
- Cryptographically protected updates, which are required for products supporting OTA or remote updates
- Credential and key management hardening, which is relevant across all product types, to eliminate hardcoded secrets, static keys, and weak authentication mechanisms
- Secure communication protocols, which are essential for network-connected products
- Component isolation and privilege separation, which are important for complex systems combining device, cloud, and mobile components
The main goal of this step is to reduce systemic risk by modernizing only those components that directly affect CRA compliance.
Apriorit expert tip: Incremental hardening is often more realistic than a full redesign. Identifying security leverage points allows your team to achieve compliance without rebuilding the entire system.
Step 4. Implement a secure SDLC approach
The CRA requires security to be repeatable and demonstrable instead of being dependent on individual engineers. During this step, your teams should:
- Apply threat modeling during design and major architectural changes
- Perform code audits for memory safety, authentication logic, and cryptographic use
- Integrate security testing into CI/CD (static, dynamic, fuzzing where relevant)
- Continuously monitor third-party dependencies for vulnerabilities
Notice that these controls need to be documented and consistently applied across releases.
Apriorit expert tip: A secure SDLC works best when aligned with existing development workflows. When security gates are too complex, they slow down delivery and generate friction, so teams bypass or postpone them to keep releases moving. Automated checks with clear ownership integrate more naturally into workflows and are therefore applied consistently.
Read also
How to Share IT Compliance Responsibilities at Different SDLC Stages
Find out how understanding IT regulations can shape better software development decisions and help you create compliant solutions without slowing down innovation or delivery.

Step 5. Build systems for vulnerability management and disclosure
The CRA explicitly requires vendors to handle vulnerabilities predictably and transparently. Your compliant workflow should include:
- A public vulnerability intake channel
- Defined severity scoring and triage rules
- Clear internal ownership for incident investigation and remediation
- Patch development and validation processes
- Coordinated disclosure timelines aligned with CRA expectations
This workflow also needs to cover both newly discovered vulnerabilities and issues found in third-party components.
Apriorit expert tip: Some teams underestimate the operational load of handling vulnerabilities. You can reduce response times and compliance risk with the help of dedicated tooling and defined service level agreements.
Step 6. Set up SBOM automation and supplier validation
A software bill of materials (SBOM) is not a static document. Creating SBOMs manually can quickly become unmanageable, especially for products with frequent releases.
Under the CRA, SBOMs turn into living artifacts. Effective SBOM implementation requires:
- Automated generation during builds
- Coverage across firmware, backend, cloud, and mobile components
- Continuous monitoring of dependencies against vulnerability databases
- Supplier validation for externally sourced components
- Clear mapping between SBOM entries and remediation actions
Apriorit expert tip: The value of an SBOM comes from its integration, not its mere existence. When you connect SBOMs to vulnerability tracking and patch workflows, your compliance becomes operational instead of reactive.
Step 7. Prepare technical documentation to assess conformity
CRA-compliant documentation must prove the security of your products, not just describe it. During this step, your teams need to prepare the following documentation deliverables:
- Product architecture and data flow diagrams
- Threat models and risk assessments
- Evidence of secure boot, update mechanisms, and access controls
- Vulnerability management and CVD procedures
- SBOMs and dependency policies
- Conformity assessment artifacts aligned with product classification
Well-prepared documentation can help you reduce audit friction and prevent last-minute remediation under regulatory pressure.
Apriorit expert tip: Documentation should evolve alongside your product. If you treat it as a final deliverable, it often leads to inconsistencies that regulators quickly detect.
As you can see, CRA compliance is a process of continuous improvement. Companies that approach it systematically not only reduce regulatory risk but also build more secure, maintainable, and competitive products.
Related project
Custom Cybersecurity Solution Development: From MVP to Support and Maintenance
Find out how Apriorit engineers delivered a cybersecurity solution that strengthened the client’s security posture, supported safe operations, and laid the foundation for future scalability.

How Apriorit can help you build CRA-aligned solutions
The Cyber Resilience Act introduces complex technical requirements that affect both new products and existing solutions on the EU market. Meeting these requirements often involves enhancing architecture, adding security features, and improving your SDLC approach.
Apriorit helps technology teams assess the current state of their software, identify security gaps, and implement engineering improvements necessary for CRA alignment. Here is what we bring to the table:
- Secure-by-design development. We help integrate security from the ground up, including architecture hardening, memory-safe code, secure boot, and OTA update mechanisms. With us, you can be sure that your firmware and software components follow CRA-aligned best practices.
- Security testing and vulnerability management. Our engineers perform comprehensive security testing, code audits, and threat modeling. These practices can help you identify weaknesses early and maintain robust security over time.
- IoT, embedded, and firmware development expertise. The CRA impacts products across connected devices, industrial systems, and embedded hardware. Our team brings deep expertise in IoT, firmware, and automotive security.
- Compliance-oriented engineering and documentation support. Beyond implementation, we help teams structure products for compliance readiness. Our business analysts and engineers support requirement mapping, technical documentation, security testing, and validation activities. Your high-risk components will be developed with the CRA and other legal and regulatory requirements in mind.
- Enhancement of existing products. When your existing solution allows, we’ll modernize it by adding CRA-relevant features, thus helping you avoid the costly rebuilding of your product from scratch. This includes implementing secure update chains, logging and monitoring enhancements, SBOM integration, and improved vulnerability response mechanisms.
Preparing for the CRA is a multi-layered effort that spans architecture, development processes, and ongoing security operations. Apriorit will be your trusted partner for building CRA-aligned solutions, helping you integrate the security, update mechanisms, and documentation needed to meet regulatory expectations.
Need stronger protection for your software systems?
Strengthen your cybersecurity posture with our team’s hands-on expertise in risk assessment, secure architecture, and threat mitigation.
FAQ
Does the CRA apply to purely software products?
<p>Yes. The Cyber Resilience Act applies to commercial software products, including standalone software, mobile applications, and firmware, as long as they have a direct or indirect connection to a network or device and are placed on the EU market. </p>
<p>However, the CRA generally does not apply to:</p>
<ul class=apriorit-list-markers-green>
<li>Pure Software-as-a-Service (SaaS) or online services that do not support or operate a hardware product</li>
<li>Non-commercial open-source software</li>
<li>Products already regulated under other specific EU frameworks, such as medical devices</li>
</ul>
<p>In short, if software is sold or distributed as a product and plays a role in the operation or security of connected systems, it likely falls under the CRA.</p>
How is the CRA different from NIS2?
<p>The CRA focuses on product security. It regulates how digital products, including software, firmware, and connected devices, are designed, developed, maintained, and updated throughout their lifecycle.</p>
<p>NIS2 regulates organizational cybersecurity and operational resilience. It applies to companies operating essential or important services and covers governance, risk management, incident response, and supply-chain security.</p>
Do non-EU companies need to comply with the CRA?
<p>Yes. The Cyber Resilience Act applies to any company that places digital products on the EU market, regardless of where the company, development team, or infrastructure is located.</p>
<p>This includes non-EU companies that:</p>
<ul class=apriorit-list-markers-green>
<li>Sell hardware, software, or connected devices to customers in the EU</li>
<li>Distribute products through EU-based partners, resellers, or marketplaces</li>
<li>Integrate software components into products that are marketed in the EU</li>
<li>Provide firmware, embedded software, or security-critical components for EU-bound products</li>
</ul>
<p>Companies that do not place products on the EU market, such as those offering pure SaaS with no link to EU-distributed digital products or developing non-commercial open-source software, generally fall outside the scope of the CRA.</p>
What are the key CRA compliance deadlines?
The CRA introduces a transition period throughout 2026, with vulnerability management obligations applying in early 2026. Full enforcement is expected in December 2027, meaning only CRA-aligned products can be placed on the EU market after that point.




