
How to Identify a Microcontroller Model Using Firmware Analysis
Use the firmware analysis process to automatically identify a microcontroller model you need to work with by analyzing the firmware source code.


Use the firmware analysis process to automatically identify a microcontroller model you need to work with by analyzing the firmware source code.

Try reversing a macOS API to see how reverse engineering can help you integrate an undocumented API into a Swift project.

Learn about the risks of vulnerable routers, common attack vectors, and ways to detect and mitigate vulnerabilities in router firmware.

Explore step-by-step instructions on how to make an Android application debuggable without changing its APK file.

Explore what static and dynamic analysis tools and techniques can be used for software reverse engineering automation.

Learn how LLVM works and how to create an obfuscating pass with it.

In this article, we share our experience in dynamic fuzzing to identify security bugs in such popular image viewers as ACDSee, FastStone Image Viewer...

This article is about discovering vulnerabilities even in closed source software by applying fuzzing testing.

This article covers the implementation of forensic features in SIEM solutions and the key requirements to ensure admissibility of data in court.
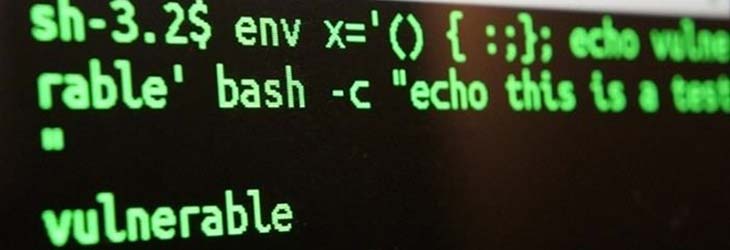
Learn how to protect your application from ever popular stack overflow exploits
Tell us about
your project
...And our team will:
Do not have any specific task for us in mind but our skills seem interesting? Get a quick Apriorit intro to better understand our team capabilities.