The blockchain is no longer hype; it’s a widespread and reliable technology for managing finances and data. Many organizations invest in blockchains, use them to store and share data, and implement them in their business processes. But blockchains also attract lots of attention from cybercriminals, who target sensitive corporate data and crypto assets.
Protecting a blockchain network from hacking involves constantly auditing and researching new vulnerabilities and potential attack vectors. In this article, we overview key blockchain security vulnerabilities, explore common attack vectors, and share our knowledge on mitigating risks that allow these attacks.
This article will be useful for businesses that are considering developing or adopting a blockchain-based application and are looking for ways to check and ensure its security.
Contents:
Why do hackers often attack blockchains?
As blockchain technology becomes commonplace for handling data and finances, successful attacks on blockchain-based applications and networks are regularly in the news. Let’s take a look at key reasons blockchains get attacked:
Insecure information processing. Many businesses use blockchains not to manage their finances and tokens but to store data: health-related information, supply chain records, trade secrets, and even voting details. If they aren’t encrypted or otherwise protected, such records always attract malicious actors, as they can be used for malicious activities: selling data on the darknet, blackmailing an organization, committing fraud, etc.
Huge and untraceable amounts of crypto. Cryptocurrencies and trading platforms become common tools for investments, money handling, and international transactions, making them a target for hacking. In 2022, hackers stole over $3.8 billion from crypto-related services. By design, transactions within a blockchain network are hard to trace to a specific person, which allows crypto thieves to go unpunished.
Challenges in bringing hackers to justice. Investigating blockchain attacks entails lots of technical and legal challenges. Blockchain transactions are anonymous and encrypted, which means investigators need a lot of time to trace a fraudulent transaction back to a hacker. Also, attackers and their victims often live in different countries and are governed by different blockchain-related legislation (if any), which further complicates investigations.
Poor security of blockchain implementations. While blockchain networks and applications spring up like mushrooms, not all organizations that develop them pay enough attention to security. For example, over 280 networks containing $25 billion worth of crypto are at risk of attack because of the Rab13s vulnerability. The lack of protection measures is practically an invitation for cybercriminals.
Limited ability to make fixes. Being decentralized solutions, blockchain applications and their core logic are often managed by open-source code. If a vulnerability is discovered in that code, it becomes known to everyone. Also, it’s challenging or sometimes impossible to fix blockchain code because it is immutable once released.
Lack of cybersecurity talent to prevent attacks. Protecting a blockchain application from attack involves not only secure design and implementation but also regular security audits and fixes for newly discovered vulnerabilities. This kind of work requires cybersecurity expertise many organizations don’t have.
Despite many use cases for blockchain in cybersecurity, we constantly see successful blockchain attacks. The number of attacks also grows year by year. Comparitect, which keeps track of cryptocurrency heists, reports that there were 136 successful crypto heists in 2021, 199 in 2022, and 220 between January and November of 2023.
Ensure the security of your blockchain!
We can help you develop a protected and performant blockchain network that fits your business needs. Reach out to discuss your project!
Let’s examine several devastating attacks on blockchain from 2023:
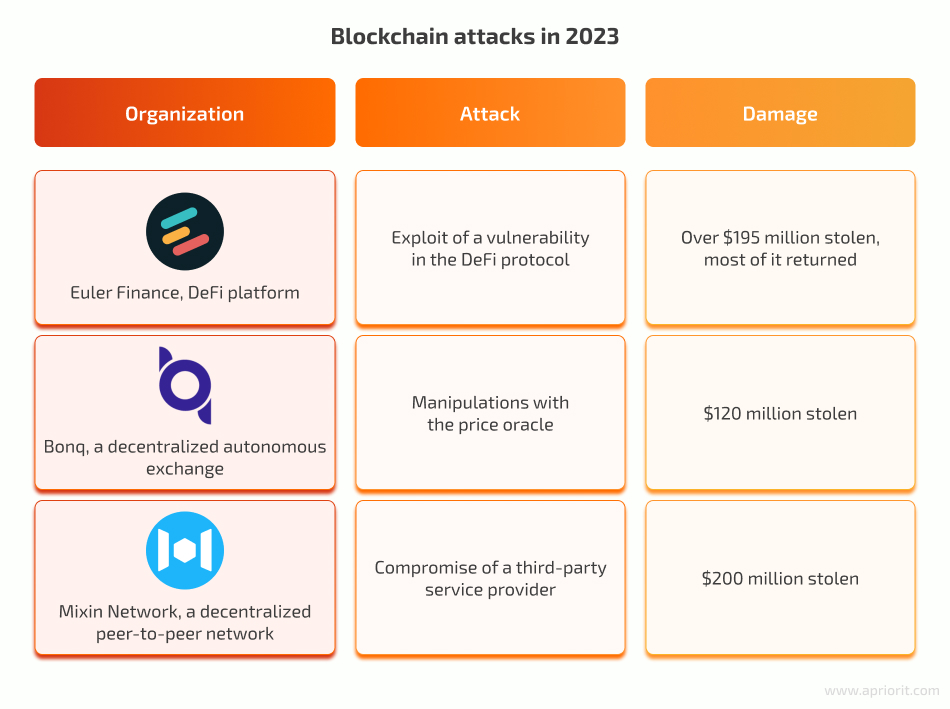
- Euler Finance suffered a series of flash loan attacks that resulted in over $195 million in theft. The attacker abused a vulnerability in the platform’s protocol which allowed them to borrow money from Euler’s deposit pool without the need for collateral assets. Euler negotiated with the hacker to return most of the stolen funds and initialized independent audits of their platform.
- Bonq’s smart contracts experienced an oracle hack, which allowed the attacker to manipulate exchange prices for some cryptocurrencies. Because of the hack, Bonq lost the majority of its investors. They paused the use of the exploited protocol but weren’t able to recover stolen funds.
- Mixin Network lost $200 million worth of its mainnet assets. The network uses a centralized database hosted in the cloud. The attacker compromised this database and gained unauthorized access to the mainnet. The stolen funds weren’t returned, but Mixin Network promised to refund 50% of users’ losses.
As you can see, even blockchain networks that hold millions of dollars aren’t secure enough to ensure the protection of users’ finances. Let’s take a look at the key potential vulnerabilities a malicious actor can exploit.
Key sources of blockchain security threats
Understanding possible vulnerabilities is the first step in securing your application. Here are the key sources of vulnerabilities that make common types of blockchain attacks possible:
Networking
Networking is one of the core aspects of blockchain systems, which consist of multiple nodes communicating with each other. Blockchain nodes should be discoverable by other nodes, synchronized, and resilient to attacks and packet loss. The underlying network logic is managed by:
- A networking protocol, which is responsible for transmitting transactions and blocks between nodes. Discoverability is an important part of this protocol, as it may affect what data the node receives.
- A consensus protocol, which determines the current state of the network that most network participants agree with.
Poorly protected networking between nodes can allow an attacker to disrupt or modify communication.
Cryptography
Cryptographic algorithms allow a blockchain to encrypt messages and verify signatures using public–private key pairs. Implementing such algorithms in a decentralized platform eliminates the need for a third party to issue a private key. Instead, the key can be generated by anyone with the necessary software and the correct implementation of the cryptographic algorithm.
In general, cryptography helps secure blockchain transactions from unauthorized access. But when implemented poorly, it can create backdoors and grant access to malicious actors.
Storage
A blockchain relies on decentralized storage to contain data like user and wallet details and transaction records. Blockchain platforms not only synchronize data between nodes but also check that the inputs used in each transaction are unique. When a network grows to hundreds of thousands of blocks, this may take a lot of time. To make it more efficient, blockchain platforms use indexers that process blocks and transactions to provide fast access to data.
Establishing storage and designing an indexer requires a careful approach, as it can introduce issues like double spending or relying on unconfirmed transactions.
Governance
Despite the many security advantages of blockchain technology, blockchain-based platforms are still managed by people. Usually, all network participants become stakeholders, and any changes in the network require stakeholder consensus. Bitcoin Classic is an example of such a network. Public governance protects the network from suspicious changes and raiding attempts, but it also blocks meaningful improvements if they aren’t approved by the majority of nodes.
Some blockchain platforms are integrated with on-chain decentralized governance, like Tezos with its self-amending protocol. Such an approach makes integrating improvements a smooth process and reduces the risk of a network split.
Read also
Smart Contract Vulnerabilities and Their Mitigation Through Security Audits
Explore how a smart contract audit works and how it can improve the security of your blockchain solution.

Application code
Development errors can make a blockchain application behave unexpectedly. In the case of incorrect use of a programming language, it can even lead to a program crash. And given the decentralized nature of blockchain systems, if a crash happens because of a specific transaction, it may halt all nodes.
If an application has logic errors, it will not be able to handle all negative usage scenarios. For example, a function may operate correctly when it processes balances until an incorrect negative value is passed.
In the next section, we overview attacks that malicious insiders often use to exploit these blockchain vulnerabilities. We also take a look at blockchain attack vectors and prevention techniques that can be useful for your network.
Blockchain attack vectors
There are hundreds of possible blockchain attacks that target different parts of an application. Let’s take a look at key vectors and examples of attacks:
Peer-to-peer attacks
A peer-to-peer (P2P) network is what allows a blockchain to be a distributed ledger. It includes all network participants who cooperate to handle transactions, manage users, and administer the blockchain.
For decentralized applications (dApps) and crypto wallets, the main network requirement is to establish a secure connection with a trusted blockchain node provider. Additionally, wallets and dApps need a secure connection between each other and must be able to handle misbehavior of other parties.
Examples of common P2P attacks:
- A Sybil attack is arranged by assigning several identifiers to the same node. Blockchain networks have no trusted nodes, and every request is sent to a number of random nodes. During a Sybil attack, a hacker takes control of multiple network nodes. Then the victim is surrounded by fake nodes that close all their transactions. Finally, the victim becomes open to double-spending attacks.
- An eclipse attack requires a hacker to control a large number of IP addresses or to have a distributed botnet. Then the attacker overwrites the addresses in the tried table of the victim node and waits until the victim node is restarted. After restarting, all outgoing connections of the victim node will be redirected to IP addresses controlled by the attacker. This makes the victim unable to obtain transactions they’re interested in.
- Timejacking exploits a theoretical vulnerability in blockchain’s timestamp handling. A hacker alters the network time counter of the node and forces the node to accept an alternative blockchain. This can be achieved when a malicious user adds multiple fake peers to the network with inaccurate timestamps.
Apriorit’s recommendations to secure P2P networks:
- Use an HTTPS connection and verify SSL certificates. These measures allow network nodes to establish a secure connection and encrypt data in transfer. This protects data from theft and hijacking.
- Validate resource authenticity. Creating an exact copy of popular resources that perform malicious actions is a common hacking technique. You can validate trusted resources by, for example, verifying resource names.
- Increase user trustworthiness. In a pure peer-to-peer network, all entities are equal, but you can change that to give more authority to trustworthy users. For example, you can increase the cost of creating a new identity, require some type of trust proof for joining the network, and determine a user’s power based on reputation.
Remote procedure call protocol attacks
Nodes based on the Remote Procedure Call (RPC) protocol facilitate communication among network elements in a blockchain. In particular, RPC nodes allow for retrieving data such as transaction histories, executing smart contracts, communicating new transactions, and maintaining network consensus.
Attacks on RPC nodes are aimed at disrupting or hijacking this communication. Common examples of such attacks:
- A distributed denial of service (DDoS) attack allows hackers to bring down network nodes by consuming all their processing resources with repeated requests. DDoS attackers aim to disconnect a network’s mining pools, e-wallets, data exchanges, and other elements.
- Eavesdropping doesn’t seemingly stop node operations, but it allows a malicious actor to listen to a node’s communication. A hacker can inject malicious code or exploit a backdoor to gain unauthorized access to node data, network routing, and sensitive information transmitted through the node. Based on this information, the hacker can find vulnerabilities in the blockchain and plan their next attack.
- Phishing is a widespread type of social engineering attack where a hacker steals a user’s sensitive information by making them click malicious links or submit their data to a fake website. In this way, the hacker can gain information about the user’s communication with blockchain nodes, mimic it, and gain access to the user’s wallet.
Apriorit’s recommendations to secure PRC nodes:
- Run validators. Validators check new transactions according to network rules and cybersecurity standards before adding them to the blockchain. Validation may slow down transaction processing, but it reduces the chance of permanently recording a fraudulent or malicious transaction to the blockchain
- Enforce user authentication and access control. All users should confirm their identities before accessing the blockchain network. They also should be able to access only those elements they need. Such access limitations reduce the attack surface in case a hacker gains unauthorized access to a user’s account.
Read also
How to Protect Your Assets: Crypto Wallet Security Best Practices
Secure your crypro assets with proven practices and tips from Apriorit experts. We explore the key threats to wallets and the essentials of crypto wallet security.

Consensus attacks
The consensus mechanism means that the majority of network nodes have to agree on the state of the blockchain system and any changes to the system. There are several consensus mechanisms, the key ones being:
- Proof of Work (PoW), where participants compete to solve complex mathematical puzzles. The first to solve a puzzle gets the right to add a new block to the blockchain and is rewarded with cryptocurrency.
- Proof of Stake (PoS), which selects the creator of a new block based on their ownership or stake in the cryptocurrency. Participants with a higher stake have a greater chance of being chosen to validate transactions and create new blocks. PoS is considered more energy-efficient than PoW since it doesn’t require the same level of computational work.
These mechanisms help maintain the integrity and security of the blockchain by preventing malicious actors from manipulating the system. Hackers can try manipulating network consensus with the following types of attacks:
- Long range attacks target networks that use a PoS consensus algorithm, in which users can mine or validate block transactions according to how many coins they hold. In a long range attack, the hacker uses a purchased or stolen private key of a sizable token balance that has already been used for validating in the past. Then, the hacker can generate an alternative history of the blockchain and increase rewards based on PoS validation.
- A 51%, or majority attack, is possible when a hacker gets control of 51% of the network hash rate and creates an alternative fork that finally takes precedence over existing forks. All small cryptocurrencies are at risk of majority attacks. Since these cryptocurrencies attract fewer miners, attackers can just rent computing power to gain a majority share of the network.
- A race attack is executed when an attacker creates two conflicting transactions. The first transaction is sent to the victim, who accepts the payment (and sends a product, for instance) without waiting for confirmation of the transaction. At the same time, a conflicting transaction returning the same amount of cryptocurrency to the attacker is broadcast to the network, eventually invalidating the first transaction.
Apriorit’s recommendations to secure blockchain consensus
- Implement a punishment system. Such a system should detect harmful activity and assign penalties to responsible nodes. For example, this can be done by locking some governance participants and having a random set of witnesses that validate every action.
- Delay blockchain confirmations. Many attacks on consensus algorithms need to be executed quickly before network nodes catch malicious activity. You can manually slow down transaction confirmations to have more time to detect harmful actions.
Encryption attacks
Cryptographic algorithms help blockchains protect data and transactions from prying eyes. Malicious actors can target networks that rely on weak protocols or have bugs in their encryption implementation. Such attacks help hackers steal data or funds, or get more information about the network to prepare their next attack.
Common encryption attacks:
- A hash collision is a hash function error that generates a fixed-size array for input of any size. A hash collision happens when two different inputs generate the same output. It may be a significant problem if a new transaction has the same hash as an existing one.
- Private key prediction is an attempt to guess or brute-force the private cryptographic key associated with a particular user or entity. Such predictions can be based on dictionary attacks, keylogging, social engineering, and other attack vectors.
Apriorit’s recommendations for blockchain encryption
- Use trusted and strong encryption algorithms. You can implement TLS, RSA, SHA-256, or any other cryptography algorithm to secure your transactions. Make sure to research the algorithm you choose and follow implementation best practices to reduce the risk of creating vulnerabilities.
- Implement multi-signature wallets. This type of wallet requires at least two private keys to sign a transaction. This way, even if a hacker acquires the private key of a legitimate user, they can’t use it to steal the user’s funds or data.
Transaction attacks
Malicious actors often target transactions within a blockchain network. They aim to compromise the integrity, confidentiality, or availability of transactions. Such attacks target vulnerabilities in smart contracts, network design, and implemented algorithms that govern transactions inside a network. Hackers can attack transactions with:
- Transaction malleability attacks, which intend to trick the victim into paying twice. For example, in the Bitcoin network, every transaction has a hash that’s a transaction ID. If attackers manage to alter a transaction’s ID, they can try to broadcast the transaction with the changed hash to the network and have it confirmed before the original transaction. If this succeeds, the sender will believe the initial transaction has failed, while the funds will still be withdrawn from the sender’s account.
- Verification attacks aim to abuse the transaction verification process. All blockchain transactions need to be verified by users in order to be recognized as valid, which takes time. Attackers can use this delay to their advantage and trick the system into using the same coins or tokens in more than one transaction.
- Time-locked transaction attacks allow a hacker to exploit vulnerabilities related to time-locked transactions that cannot be added to the blockchain until a specific future time or until certain conditions are met.
Apriorit’s recommendations for blockchain transactions
- Prevent double-spending. Double-spending attacks like Vector 76 are a common result of consensus algorithm abuse, where a user spends tokens twice in seemingly the same transaction. You can prevent this issue by monitoring received transactions during a listening period, forwarding double-spending attempts, inserting other nodes to observe transactions, and rejecting direct incoming connections.
- Use timelock smart contracts. This type of smart contract adds various time-based constraints to transactions. A timelock smart contract typically enforces a time delay during which users cannot execute the specified action. This gives network nodes time for making decisions and detecting suspicious transactions.
Conclusion
Though blockchain popularity is still on the rise, an increasing number of cyber attacks on blockchains may negatively affect the reputation of this technology. While there’s a huge variety of possible attacks and vulnerabilities to abuse, knowing the core blockchain security threats and attack vectors gives you an opportunity to implement reliable security measures. And being able to withstand major blockchain attacks helps you improve trust in your product and avoid negative consequences of being hacked.
Apriorit’s security testing team often conducts security audits of smart contracts, dApps, and crypto wallets to help our clients assess and improve the protection of their products. We provide detailed descriptions of the vulnerabilities we discover and expert tips on how to fix them.
Need to prove that your blockchain is secure?
Reach out for a detailed, unbiased, and expert Apriorit security audit!




