Customers like things running nice and smoothly. Distributed denial of service (DDoS) attacks leave servers and data centers unresponsive to all requests. That’s why cyber criminals continue relying on these attacks, aiming to compromise the performance and availability of their victims’ products and services.
To mitigate the risk of losing your customers’ trust and maintain the reputation of your business, it’s important to prioritize DDoS mitigation when working on a new product.
In this article, we discuss the most common types of DDoS attacks and techniques that help detect them. We also offer several recommendations to help your development team introduce necessary adjustments and build a secure and resilient web application in a timely manner.
Contents:
Types and methods of DDoS attacks
Imagine someone calling your phone over and over again, using different phone numbers so you can’t blacklist them. You’d probably end up turning off your phone and becoming unreachable. This is what a usual DDoS attack looks like.
A distributed denial of service (DDoS) attack is a coordinated attack intended to render a victim’s resources unusable. DDoS attacks usually target websites, web applications, or APIs and can be performed by hackers or with the help of multiple compromised devices connected to the internet — botnets.
DDoS attacks were here long before Steve Jobs presented the first iPhone. And they’re still extremely popular among hackers because they’re effective, easy to initiate, and leave little to no trace.
A single DDoS attack may last for several minutes, hours, or even days. But the impact of an attack is usually calculated not by the time it lasts but by the amount of traffic that hits the victim. One of the largest incidents reported so far is the 3.47 terabytes per second (TBps) attack stopped by Microsoft in early 2022. It targeted Asian customers of Microsoft Azure services and reportedly originated from around 10,000 workstations all over the globe.
Sometimes, cyber criminals launch DDoS attacks just to improve their hacking skills or because they’re bored. But more often, these attacks are carried out for specific reasons, including:

- Ransom — Cyber criminals may launch an attack or just threaten to do so to extort money or other benefits from their victims. Such attacks are sometimes also called ransom denial of service attacks.
- Business competition — Some organizations can use DDoS attacks as a method of unfair competition and try to gain an advantage by causing damage to their competitors’ business flows and reputation.
- Hacktivism — Technology-savvy activists may use DDoS attacks to showcase their disapproval of certain businesses, political and social initiatives, or public figures.
- Cyber warfare — Governments can authorize DDoS attacks to damage critical online infrastructure of an enemy country or take down opposition websites.
Depending on their goals and motivations, cyber criminals perform various types of attacks, using various tools. Usually, a DDoS attack is executed by:
- Exploiting software vulnerabilities — Hackers can target both known and unknown software vulnerabilities and send malformed packets in an attempt to crush the victim’s system.
- Consuming computational or communication resources — Attackers can send massive volumes of legitimate-looking packets. Thus, they consume the victim’s network bandwidth, CPU, or memory until the targeted system can no longer process requests from legitimate users.
If you’re also working with blockchain-powered products, make sure to check out our article about blockchain attack types.
While there’s no standard classification of DDoS attacks, we can divide them into four large groups:
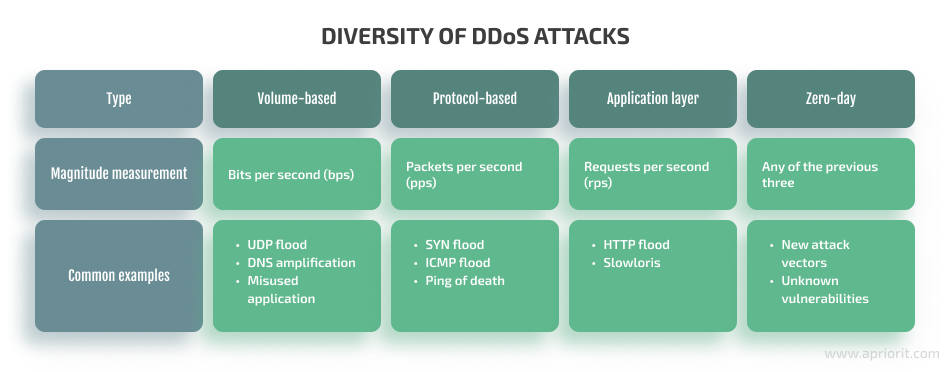
Let’s take a close look at each of these types of attacks.
1. Volumetric attacks
Volumetric attacks aim to block access to the victim’s resources by flooding them with massive volumes of traffic, usually with the help of botnets and amplification techniques. The magnitude of these attacks is usually measured in bits per second (bps).
The most common types of volumetric attacks are:
- UDP flood — Attackers send User Datagram Protocol (UDP) packets forged with the victim’s source address to random ports. The host generates massive volumes of reply traffic and sends it back to the victim.
- DNS amplification — Cyber criminals compromise and manipulate publically accessible domain name systems (DNS) to flood the victim’s system with DNS response traffic.
- Misused application attacks — Hackers compromise client machines that can send extensive volumes of legitimate-looking traffic and redirect that traffic to the victim’s server, exhausting its resources and eventually taking it down.
In 2020, Amazon Web Services suffered a massive 2.3 TBps attack executed using the Connectionless Lightweight Directory Access Protocol (CLDAP) reflection technique.
2. Protocol attacks
Protocol attacks target weaknesses in the way different internet communication protocols work. Usually, the magnitude of this type of DDoS attack is measured with the number of network packets per second (pps). The most common types of protocol attacks are:
- SYN flood — Hackers exploit a weakness in the three-way handshake TCP mechanism. A client sends an SYN packet to a server, receives an SYN-ACK packet, and never sends an ACK packet back to the host. Thus, the victim’s server is left with numerous unfinished SYN-ACK requests and, eventually, crashes.
- ICMP flood — Malicious actors use an extensive series of Internet Control Message Protocol (ICMP) requests, or pings, in an attempt to exhaust the victim’s server bandwidth.
- Ping of death — Hackers use a simple ping command to send oversized packets, causing the victim’s system to freeze or crash.
In 2020, Akamai reported combatting a massive 809 million packets per second (Mpps) DDoS attack targeting a European bank.
3. Application layer attacks
Application attacks exploit weaknesses in the Level 6 and Level 7 protocol stack, targeting specific applications instead of the entire server. The force of this type of DDoS attack is usually measured in the number of requests per second.
Application layer attacks usually target common ports and services such as DNS or HTTP. The most common application-level attacks are:
- HTTP flood — Using botnets, attackers flood an application or a web server with massive volumes of standard GET and POST requests. As these requests often appear as legitimate traffic, detecting an HTTP flood attack is quite a challenge.
- Slowloris — True to its name, Slowloris crashes the victim’s server slowly. Attackers send an HTTP request to a victim’s server in timed intervals and small portions. The server keeps waiting for these requests to be completed, which never happens. Eventually, these unfinished requests exhaust the victim’s bandwidth, making the server unreachable for legitimate users.
In 2022, an unnamed cryptocurrency service was hit with a 15.3 million request-per-second attack according to a recent statement by Cloudflare.
Read also:
IoT Toys: A New Vector for Cyber Attacks
4. Zero-day DDoS attacks
Alongside well-known attacks are also so-called zero-day DDoS attacks. They exploit previously unknown software vulnerabilities that haven’t been patched yet or use an uncommon attack vector and, therefore, are much more difficult to detect and protect from.
Now let’s talk about ways of detecting a DDoS attack.
Detecting a DDoS attack
While it’s impossible to prevent DDoS attacks from happening altogether, there are effective practices and approaches that can help you detect and stop a DDoS attack that’s already underway.
Below, we list several of the most common DDoS protection methods you can rely on to detect an attack and secure your product or service.
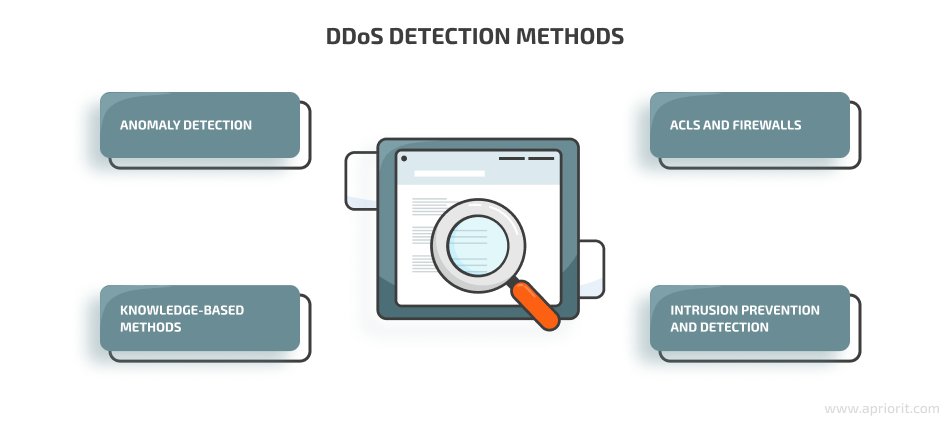
Anomaly detection
One way to detect a potential DDoS attack is by analyzing network traffic and classifying traffic patterns as normal or potentially threatening. You can do this with the help of either traditional static analysis or more sophisticated technologies like machine learning and artificial intelligence.
Alongside network traffic analysis, you can search for anomalies in other network performance factors such as device CPU utilization or bandwidth use.
Knowledge-based methods
You can also detect DDoS-like activities by comparing traffic to specific patterns of known attacks. Common DDoS protection techniques include signature analysis, state transition analysis, expert systems, description scripts, and self-organizing maps.
ACLs and firewalls
Alongside ingress/egress traffic filtering, you can enhance traffic visibility using access control lists (ACLs) and firewall rules. In particular, you can analyze ACL logs to understand what kind of traffic runs through your network. You can also configure your web application firewall to block suspicious incoming traffic based on specific rules, signatures, and patterns.
Intrusion prevention and detection
Intrusion prevention systems (IPS) and intrusion detection systems (IDS) also enhance traffic visibility. IPS and IDS alarms serve as early indicators of anomalous and potentially malicious traffic. But keep in mind that these systems tend to provide a lot of false positives.
As for the approaches to handling traffic potentially involved in a DDoS attack, we can outline three common strategies:
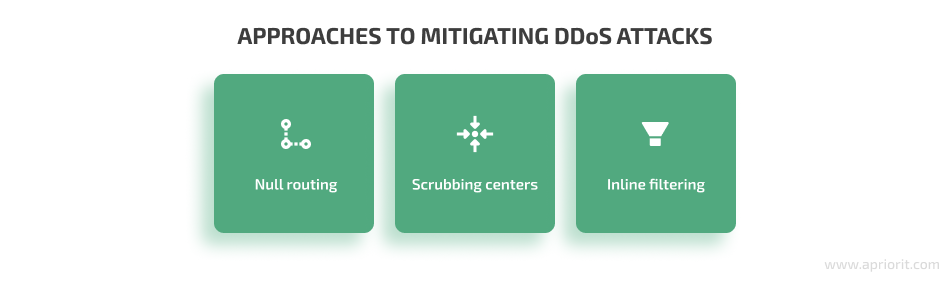
- Null routing or blackhole routing — All traffic and sessions are redirected to an IP address without a final destination. As a result, the server becomes unable to either receive or send data. Normal traffic processing is restored once the DDoS attack is over. While this approach is easy to implement, it negatively affects all legitimate traffic and basically helps the attackers accomplish their initial goal — render the victim’s server unavailable.
- Scrubbing centers — This approach is based on redirecting traffic from a victim server to a remote scrubbing center where the traffic is analyzed and filtered. Any potentially dangerous traffic, like DDoS requests, is blocked, while legitimate requests are processed as usual.
- Inline filtering — In this approach, all traffic passing across the network is analyzed and compared to different rules and attack metrics. Traffic related to an identified DDoS attack gets immediately blocked, while legitimate requests are processed normally.
The choice of a particular approach and technique will depend on the peculiarities of a particular service or solution. However, ensuring early detection of DDoS attacks is crucial for any projects, as it can help you significantly lessen the consequences of an attack and maintain normal performance of your service or solution.
In the next sections, we discuss several ways you can try to prevent a DDoS attack and overview some types of DDoS protection measures for your web application or service.
DDoS protection best practices for your web app
Prevention is better than cure. So think about how you will ensure the DDoS resilience of your web application or service before you even start building it.

1. Apply DDoS prevention mechanisms
Even though you can’t prevent a DDoS attack from happening, it’s in your power to make it much harder for attackers to take down your website or application. This is where DDoS attack prevention techniques come into action.
There are two groups of DDoS prevention mechanisms you can use:
- General DDoS prevention mechanisms
- Filtering mechanisms
General DDoS prevention mechanisms are common measures that can help you make your web application or server more resilient to DDoS attacks. These measures include:
- Using firewalls – While firewalls won’t protect your app or server from complex DDoS attacks, they can still effectively handle simple ones.
- Installing the latest security patches – Most attacks target specific software or hardware vulnerabilities, so deploying all patches on time can help you lessen the risk of attack.
- Disabling unused services – The fewer applications and services hackers can possibly attack the better. Make sure to disable all unneeded and unused services and applications to improve the security of your network.
Filtering mechanisms use different approaches for filtering traffic and blocking potentially dangerous requests. These mechanisms include ingress/egress filtering, history-based IP filtering, and router-based packet filtering.
2. Choose your CSP wisely
When choosing a cloud service provider (CSP), aim for one with its own DDoS mitigation strategy. Make sure this strategy ensures detection and mitigation of protocol-based, volume-based, and application-level attacks.
Also, research your CSP’s recommendations on DDoS mitigation and implement them when building your web product. Most cloud service providers have detailed guidelines with best practices for securing your web products and services against common DDoS attacks. You can start by taking a look at recommendations from Google Cloud, Microsoft Azure, and Amazon Web Services.
3. Aim for scalability
Enable your web application to efficiently handle sudden load changes by putting enough planning and resources into its scalability. You can deploy application and network load balancers or a content distribution network (CDN) to protect your solution from traffic overload by distributing all traffic across multiple instances. In this way, you’ll be able to mitigate potential attacks at both the infrastructure and application layers.
4. Limit the number of weaknesses
Don’t expose your application and resources unless it’s truly necessary. This way you can limit the number of weak spots in your infrastructure that can be targeted by attackers. You can also prohibit direct internet traffic to database servers and other critical parts of your infrastructure.
5. Secure your APIs
DDoS attacks can be focused not only on your website and application but also on your APIs.
There are different ways to enhance anti-DDoS protection for an API: apply traffic filtering tools and techniques, limit the number of requests your API can process in a given time period, or even deploy honeypots.
6. Employ third-party DDoS mitigation services
Consider delegating the protection of your web application to a third-party vendor. DDoS prevention tools and mitigation services can remove problematic traffic even before it reaches a victim’s networks. You can look for a DNS-based service that redirects problematic traffic from your network or a Border Gateway Protocol-based solution for handling sustained attacks.
Conclusion
Hackers keep using and improving DDoS attacks, aiming to disrupt the work of particular websites, applications, and services. When working on a web application, pay special attention to hardening your solution against possible DDoS attacks.
It’s important to build your web product with stability and resilience in mind. You can combine different DDoS attack prevention methods and DDoS defense techniques to increase your chances of efficiently mitigating a potential attack. Or you can deploy multiple clouds to ensure better availability of your service.
While most CSPs offer anti-DDoS recommendations, designing a comprehensive DDoS mitigation strategy when developing a web application requires additional expertise. At Apriorit, we have teams of high-profile cloud and web security experts who will gladly assist you in building a stable, resilient, and well-performing web product.
Get in touch with us to find the best approach for hardening your web product against relevant DDoS threats.



