Key takeaways:
- OTA updates have become an irreplaceable part of software-defined vehicles (SDVs), providing manufacturers with a convenient way of fixing and upgrading their vehicles remotely.
- When not secured properly, OTA update pipelines can become a gateway for data theft, malware injection, vehicle theft, and other malicious activity.
- Any part of an OTA update — including cloud infrastructure, firmware code, network infrastructure, and target devices — can be vulnerable to attacks.
- To secure OTA updates, development teams should combine automotive and software development requirements with cybersecurity best practices.
Over-the-air (OTA) updates have become a cornerstone of modern vehicle development. They enable manufacturers to patch vulnerabilities, improve performance, and roll out new features without a single trip to the service center. But with this convenience comes a new attack surface.
Each update delivered wirelessly can be a potential entry point for threat actors seeking to compromise critical systems, steal data, or even take control of a vehicle.
In this article, we explore the key attack vectors for update mechanisms and share practices to address OTA cyber security issues. From encryption and authentication to rollout strategies and monitoring, we outline how to prevent security risks and incidents when delivering OTA updates to vehicles.
This article will be useful for automotive development leaders who are looking for ways to ensure the security of their OTA updates.
Contents:
- Why secure OTA updates for automotive software?
- 4 key attack vectors for automotive OTA updates
- 1. Infrastructure risks
- 2. Network risks
- 3. Software risks
- 4. Hardware risks
- How to improve OTA security in automotive
- The future of OTA updates
- How Apriorit can help you secure OTA infrastructure
- Conclusion
Why secure OTA updates for automotive software?
With the rapid development of vehicle connectivity and the rise of software-defined vehicles, OTA updates have become a must for any automotive manufacturer. They allow manufacturers and suppliers of automotive components to fix issues remotely and avoid costly physical recalls of thousands of vehicles.
In 2024, manufacturers fixed 33% of all vehicle recalls with OTA updates instead of visits to a dealership. For example, Tesla avoided a physical recall of over 1.8 million cars with an OTA update that fixed unlatched hood detection.
In this way, OTA updates save automotive companies time and money on vehicle repairs. Drivers also appreciate free vehicle improvements that don’t require any effort on their side. Investing in OTA cybersecurity helps manufacturers and automotive suppliers gain the following benefits:

However, OTA connectivity can also create an open door for malicious actors. Security vulnerabilities it can introduce — especially if they affect a vehicle’s critical systems like advanced driver-assistance systems (ADAS), braking, and vehicle-to-everything (V2X) communications — can lead to damaging hacking incidents, lawsuits, or even physical harm.
By securing OTA software updates, automotive manufacturers prevent cases of malicious code injection, network listening, data theft, vehicle theft, and more. This ensures that vehicles get new features and improvements while keeping their owners’ data safe.
To maintain a high level of OTA security at every stage of an update, you first need to understand how OTA updates can be dangerous. In the next section, we’ll examine the most common vulnerabilities and attack vectors.
Looking for ways to deliver OTA updates securely?
Leverage Apriorit’s 20+ years of cybersecurity expertise to protect your automotive infrastructure.
4 key attack vectors for automotive OTA updates
How can OTA updates endanger a vehicle?
There are four key attack vectors for a vehicle’s OTA update mechanisms: infrastructure, network, software, and hardware. In SDVs, OTA updates touch hundreds of subsystems, ranging from critical (ADAS, steering, braking, V2X communication) to non-critical (infotainment, climate control, voice assistants).
Attackers will look for the weakest link in the vehicle’s security chain to get an initial foothold for lateral movement into safety-critical systems. Since a vehicle’s subsystems are highly connected, it’s important to address all four attack vectors to ensure OTA security.
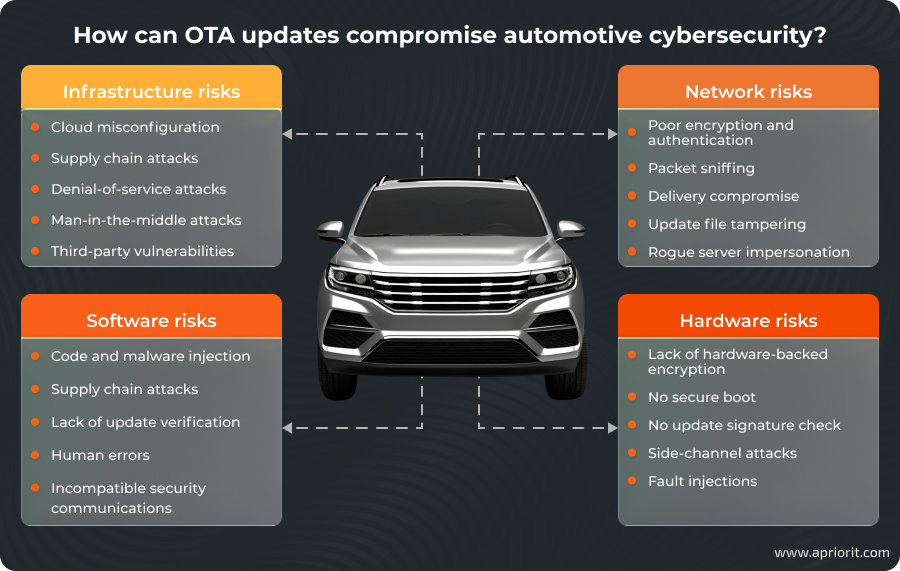
1. Infrastructure risks
Automotive software developers use distributed backend infrastructure and storage instances to deliver updates to vehicles worldwide. Such backend systems usually include multiple cloud environments, edge servers, and pipeline elements — and each of these elements can be vulnerable to an attack. As a result of a successful infrastructure attack, hackers can:
- Steal update files
- Substitute them with their own infected files
- Get unauthorized access to other parts of a manufacturer’s network
- Gain insights into a vehicle’s software protection and architectural elements
Cybersecurity experts believe misconfiguration is the main cloud security risk, as human errors are unavoidable, are hard to detect with cybersecurity monitoring tools, and can lead to severe data breaches. In the automotive sector, misconfiguration of cloud infrastructure can leave OTA files exposed to the world.
OTA update infrastructures are also vulnerable to supply chain, denial-of-service, and man-in-the-middle attacks.
2. Network risks
The OTA update process depends on continuous wireless communication between vehicles and backend servers. Different SDV subsystems can use cellular, Wi‑Fi, or V2X networks to communicate with external infrastructure and other vehicles’ systems. Unprotected communications expose OTA packages to interception and tampering.
Vehicle software that lacks end-to-end encryption, uses outdated cipher suites, or employs weak authentication mechanisms creates serious vulnerabilities. In such cases, attackers can intercept update files, block updates, or monitor sensitive traffic. Proximity-based threats such as rogue access points, Wi‑Fi spoofing, or IMSI catchers further amplify risks in parked-vehicle updates.
3. Software risks
The software layer in OTA systems manages OTA delivery, deployment, monitoring, and rollback. A vulnerability or compromise anywhere in the OTA development or delivery lifecycle can cascade into widespread security breaches.
Attackers can exploit update delivery pipelines through code injection, malware insertion, or a supply chain attack. If any point of the update delivery and deployment is vulnerable, malicious actors will use it to inject their own code with a legitimate update or create a custom update file.
In addition to external attacks, vehicles can be compromised by installing custom firmware from third-party developers. The rise of paid or subscription-based access to premium vehicle features has created demand for unofficial custom firmware. In their search for cheaper or free access to features, users may subscribe to potentially malicious updates from unknown suppliers. If a vehicle’s software system allows for the installation of unverified software, malicious actors have an opportunity to infect a vehicle via third-party updates.
Another frequent cause of security and performance issues resulting from OTA updates is human errors, such as misconfigured build environments, incorrect signing, or incompatible security configurations for different subsystems. Without automated rollback mechanisms, such errors can leave ECUs unstable or vulnerable to an attack.
4. Hardware risks
Even with strong network and software protections, hardware limitations can undermine OTA update security. Many ECUs in existing vehicle platforms:
- Don’t have enough computing power to encrypt data in real time
- Lack hardware-backed cryptographic modules
- Can be misconfigured to prioritize performance over security (such as by disabling secure boot and signature checks)
As a result, ECUs can fail to verify firmware integrity and allow the execution of tampered or unsigned code.
Moreover, legacy hardware and embedded devices with limited processing power often don’t support strong cryptographic algorithms like RSA-2048 or ECC. To still use such encryption, automotive manufacturers have to build centralized encryption gateways. This approach reduces ECU burden, but if the gateway is compromised, all ECUs connected to it become vulnerable to unauthorized updates.
Fault injection and side-channel attacks are also relevant in the automotive context. Researchers have demonstrated techniques for extracting sensitive information and cryptographic keys from ECU chips by analyzing power consumption. Once extracted, these keys can be used to sign malicious updates and defeat OTA protections.
The good news is that your team can implement security practices that protect all stages of OTA updates. In the next section, we overview key regulations to follow and practices to implement to ensure cyber security for automotive OTA.
Read also
AI in the Automotive Industry: 7 Key Applications for a Competitive Advantage
See how AI solutions accelerate automotive transformation, from self-driving capabilities and driver assistance to predictive maintenance. Give your business a technological edge in a rapidly evolving market!
How to improve OTA security in automotive
The first step to ensure the security of OTA processes is determining and implementing relevant requirements. The OTA update process in automotive is regulated by:
- Automotive-specific standards and regulations (ISO 26262, ISO 21434, ISO 24089, EU CRA, SAE J3061, etc.). These describe how OTA updates should be developed, delivered, and managed, as well as overall data security practices automotive manufacturers and suppliers should follow.
- General-purpose cybersecurity requirements, regulations, and laws like the GDPR, the CCPA, and the EU Cybersecurity Act. While they don’t directly describe OTA updates, they contain requirements for secure management of sensitive data, which is commonly handled by OTA processes.
However, keeping up with legal requirements may not be enough to ensure the complete security of OTA updates. With so many trends, emerging technologies, and new attack techniques, the automotive industry is evolving faster than standards and regulations. That’s why, as cybersecurity-focused software developers with automotive experience, we recommend following these six practices:
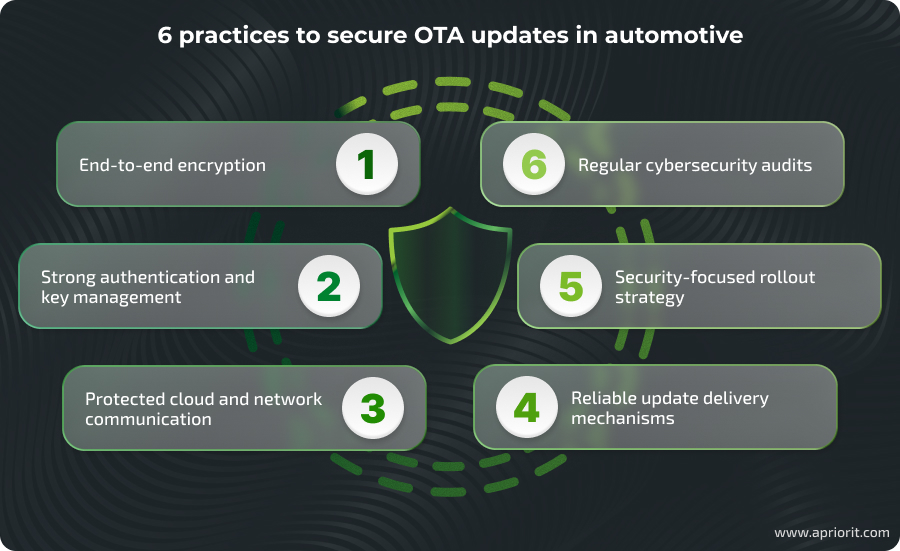
1. End-to-end encryption
Though end-to-end encryption is a standard cybersecurity practice, when it comes to working with IoT and embedded devices, some developers may skip it in favor of a device’s real-time performance. This approach is reasonable for devices that don’t process sensitive data. But in automotive, it may lead to lateral movement attacks: if a non-critical system like an infotainment center doesn’t support encryption, malicious hackers can intercept and analyze its communication to gain valuable insights into other vehicle subsystems.
That’s why both OTA data and communication channels require robust algorithms like AES-256 or TLS. To avoid hardware limitations, your team can:
- Add chips for hardware-based encryption at the design stage
- Allow firmware updates only when a vehicle’s system is not in use (for example, when a vehicle is parked and not charging)
- Limit the amount of data a device can process at a time (this will slow down updates but make the process more secure)
2. Strong authentication and key management
Vehicle ECUs and servers that issue updates should be able to reliably authenticate each other before applying an update. Authentication helps to prevent update file tampering and installation of unapproved and potentially infected software.
To authenticate an update, automotive software usually relies on digital signatures based on asymmetric cryptography. In this case, the server that issues the update signs it with a unique private key, and the targeted in-vehicle device has a corresponding public key to verify the signature before applying the update. If the signatures don’t match, the device automatically rejects the update.
Secure key management is the cornerstone of ensuring strong authentication. Here are the steps your key management process should include:
- Encrypt keys with RSA-4096, ECC, AES-256, or TLS
- Use unique keys for each device and update version
- Store keys using tamper-resistant hardware or cloud services
- Implement automatic key rotation
- Configure role-based access to key vaults and key generation
You can enhance signature-based authentication with hashing. However, hashing can’t be the only means of authentication your device uses, as it’s possible for malicious actors to intercept update communication and substitute it with their own update file and associated hash.
3. Protected cloud and network communication
An OTA update ecosystem relies on seamless interaction between cloud servers, several types of networks, and in-vehicle systems. Any unsecured communication channel creates opportunities for man-in-the-middle and DDoS attacks, data interception, or unauthorized commands targeting vehicle ECUs.
The encryption and authentication mechanisms we described earlier partially secure your cloud services and network channels. Additionally, segmenting OTA infrastructure and applying network-level protections allows your team to detect compromise and reduces the risk of lateral movement within the system if one component is breached.
These network-level protections can include firewalls, intrusion and threat detection systems, traffic filtering, rate limiting, and more. Alternatively, you can use public blockchain networks to store and deliver OTA updates, as they provide a higher level of security and visibility by default.
Read also
Shifting to Post-Quantum Cryptography in Automotive Projects: Reasons, Challenges, Considerations
Stay ahead of quantum computing risks by integrating advanced cryptography into connected vehicle ecosystems.

4. Reliable update delivery mechanisms
An insecure OTA delivery process can be exploited to inject malicious updates, disrupt critical ECU functions, and even brick an ECU or an entire vehicle subsystem. Attackers may attempt to corrupt update files in transit, interrupt installations, or replay outdated update packages with known vulnerabilities.
To counter this, integrate error detection and recovery mechanisms into the software delivery process. Delta updates help minimize the size of transmitted data by allowing an update receiver to download only the updated parts of the firmware instead of the whole file, thus reducing the likelihood of transmission failures. Integrity verification through cryptographic hashes and digital keys ensures that only reliable updates are installed.
Additionally, implementing an A/B partitioning strategy helps your team ensure that OTA updates are applied to an inactive file partition and validated before switching active partitions. If validation fails, the system rolls back to the previous version automatically, preventing ECU bricking or use of a vulnerable update file.
5. Security-focused rollout strategy
Unforeseen issues and attacks on OTA updates can cause system failures or create new vulnerabilities in vehicle software. To minimize the impact of such incidents, the rollout process must include safeguards that verify updates at each stage and ensure vehicles remain operational if an update fails. Your rollout strategy should at least include:
- Geofencing and update segmentation. Rollouts segmented by geography, vehicle type, or other criteria help localize potential issues. Any update should be first tested on a small group of vehicles and, after you verify that the update is successful and safe, gradually rolled out to other vehicles. This way, you can limit the impact of updates as well as reduce network strain and resource consumption.
- Secure bootloader. A bootloader verifies that a trusted entity has signed an update file before it is executed. Then it reloads targeted device and rolls out the signed update. If verification fails, the bootloader prevents the update from initializing device recovery. If verification is successful, the bootloader installs the update and checks that the installation was successful. Secure bootloaders often work alongside hardware-based Trusted Platform Modules to strengthen a device’s defenses against unauthorized modifications.
- Automated OTA update rollback. In case a bootloader fails or an OTA update contains an issue that hasn’t been detected before the rollout, the device should be able to automatically roll back to the previous firmware version. This feature prevents ECUs from bricking, working incorrectly, or creating new vulnerabilities.
- Forced update rollback. Even if an update was successful, you have to be able to roll it back. This feature is helpful when, for example, you discover security issues or potential vulnerabilities in the update code after it has been shipped.
- Update monitoring. The OTA pipeline should include mechanisms that record the process of OTA delivery and rollout, including all errors, issues, and unexpected events. Logs are invaluable evidence for incident investigation and response, further cybersecurity testing, and improvements for future updates. The monitoring system should have alerting functionality so it can notify update providers of any issues discovered during or after an update.
6. Regular cybersecurity audits
An automotive software system is a complex and dynamic environment, with unique OTA update mechanisms for different ECUs. These mechanisms use different types of networks, encryption algorithms, infrastructure elements, and delivery parameters. Moreover, new attack vectors constantly appear. Even if your OTA pipeline is secure today, it may not be secure in a month. That’s why companies must conduct regular security assessments of OTA systems.
Audits should cover both software and hardware layers. On the server side, this includes reviewing access controls, validating API security, and checking for outdated or vulnerable dependencies in the OTA delivery pipeline. On the vehicle side, testing ECUs and communication protocols helps uncover potential vulnerabilities in how updates are received and applied.
Additionally, audits can include penetration testing sessions to simulate real-life attacks using new hacking methods. Findings from audits provide actionable steps for future development cycles, enabling greater system resilience and faster incident detection and remediation.
These six practices, combined with automotive and cybersecurity compliance, create a layered defense system that reduces the risk of unauthorized access, data breaches, and system failures throughout the OTA lifecycle.
As cybersecurity becomes an integral part of automotive software development, the role of OTA updates is set to expand beyond patches and recalls. Next, we explore how emerging technologies and regulations are shaping the future of OTA updates.
Read also
Whys and Hows of Automotive Penetration Testing for Vehicle Software Systems
Explore proven methods for testing automotive systems to identify and fix security vulnerabilities before they impact your vehicles and customers.

The future of OTA updates
OTA updates have become a must for SDV manufacturers. We already see OTA updates evolving alongside technologies like blockchain and AI, so it’s safe to assume we’ll see OTA mechanisms adopt other emerging trends.
In particular, you should be ready for the following:
- Evolution of strict security regulations and standards. Software and hardware regulations are only now catching up with the rapid growth of the automotive industry. We’re already seeing that some standards contain requirements for security of OTA updates, and with time, these requirements will become more defined.
- Enhanced data analytics. Increasing reliance on OTA updates creates a massive, constant flow of data. It’s challenging to analyze this data now, since many stages of OTA updates require real-time or near real-time operations. However, as data analytics algorithms evolve, we’ll see automotive manufacturers apply them to analyze the development, delivery, and performance of their OTA updates.
- Use of AI and ML for OTA security. As OTA ecosystems grow more complex, artificial intelligence and machine learning will play a bigger role in securing them. These technologies can help detect anomalies in update delivery, identify potential tampering attempts, and predict vulnerabilities in software builds. Over time, AI-driven systems will become standard tools for monitoring OTA pipelines and responding to emerging threats.
- Adoption of faster networking. Many vehicle ECUs rely on the cellular network to receive updates, and using faster networks like 5G will help reduce update times and enable real-time patches for safety-critical systems. This shift will not only improve the efficiency of OTA processes but also enhance their resilience by supporting more robust encryption and validation protocols without impacting performance.
With so many changes and emerging technologies, it’s important to partner with a software development expert like Apriorit who can help you stay ahead of automotive OTA challenges and regulatory changes.
How Apriorit can help you secure OTA infrastructure
As a TISAX– and ISO 27001–certified company, Apriorit follows automotive development trends, paying special attention to cybersecurity. Whether your automotive project requires an audit of vehicle communication systems or AI-powered charging support, we can provide you with the necessary development and QA talent.
Here’s how Apriorit will help drive your automotive development project forward:
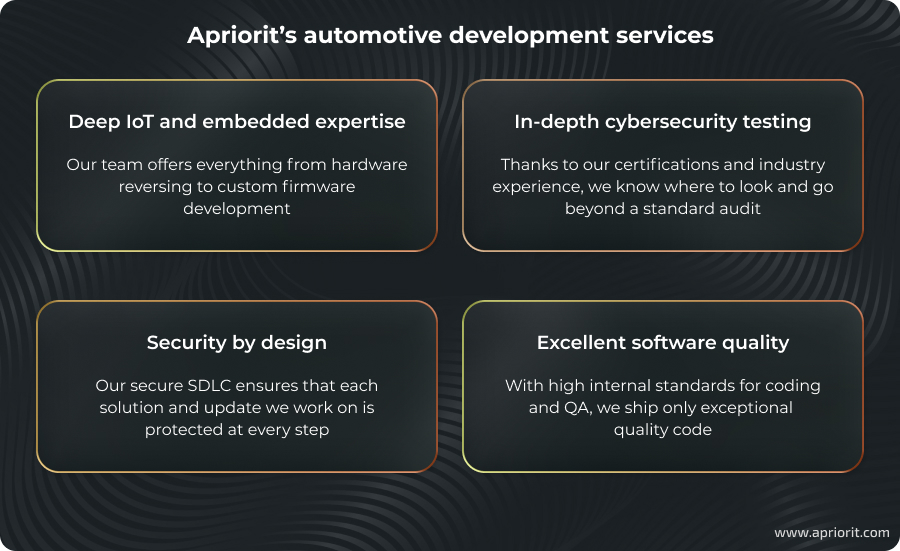
Apriorit will provide you with a team that has the unique talent your project requires.
Conclusion
As vehicles become increasingly connected, securing OTA updates becomes a fundamental requirement for protecting both drivers and manufacturers. Investing in secure OTA practices today is about more than mitigating risks. It’s about delivering new features, performance improvements, and safety enhancements with confidence. By building OTA systems with a security-first approach, organizations can not only comply with emerging regulations but also earn customers’ trust in a highly competitive market.
The shift to fully autonomous, software-defined vehicles will only increase reliance on OTA technology. Partner with Apriorit’s dedicated automotive teams to stay ahead of security threats and ensure OTA protection at every stage of the update lifecycle.
Let’s make your vehicles resilient to attacks!
Collaborate with Apriorit’s cybersecurity experts to bring your automotive software to a new level of security and reliability.



