Cloud technologies evolve rapidly, enabling cloud-based alternatives to almost any known service and product. The cloud computing market is expected to grow to a staggering $947.3 billion by 2026 according to a report by Markets and Markets. However, the growth and diversity of cloud-based services excites both software vendors and malicious actors who might want to gain access to your data.
To ensure the secure storage of sensitive data, developers need to enhance the protection of both on-premises and cloud environments. They also have to demonstrate compliance with the GDPR, NIST standards, PCI DSS, ISO/IEC 27001, and other regulations, standards, and laws. So how can you ensure data security in the cloud? Is it even possible to track down and eliminate all vulnerabilities in cloud-based software?
So, what is cloud application security and how can you ensure it? Is it even possible to track down and eliminate all vulnerabilities in cloud-based software? What are the cloud application security issues and how to fight them?
In this article, we focus on five key cloud data security threats as well as legal requirements for protecting data in the cloud that can help you combat them. This article will be useful for development teams and leaders that plan on developing a cloud-based application.
Contents:
- What is cloud application security?
- Who is responsible for protecting data in the cloud?
- What are the cloud application security issues and how to fix them?
- 1. Misconfiguration and incorrect setup of the cloud platform
- 2. Exfiltration of sensitive data
- 3. Unauthorized access
- 4. Insecure APIs
- 5. External data sharing
- Ensuring compliance in the cloud
- Conclusion
What is cloud application security?
Cloud application security is a combination of approaches, practices, technologies, and policies towards protecting data, applications, and infrastructure within cloud environments.
The need for cloud app security emerged because businesses increasingly rely on cloud-based solutions. And with new opportunities, new threats and vulnerabilities appear as well.
Being a wide concept, cloud application security encompasses a broad range of activities, such as:
- Identity and access management (IAM)
- Threat detection
- Data encryption
- Application and infrastructure security
- Incident response and recovery
- Practices towards compliance with regulatory standards
Cloud application security best practices include:
- Ensuring threat monitoring capabilities
- Conducting regular security testing
- Applying the principle of least privilege
- Educating employees on cybersecurity awareness
- Developing and enforcing strong security policies
All those measures aim to safeguard sensitive information from unauthorized access, data breaches, and other cyber threats that exploit vulnerabilities in cloud services. They also can assist in protecting against DDoS attacks and mitigating issues caused by exposed application services due to misconfigurations.
Have a SaaS project in mind?
Deliver a robust and protected product by leveraging Apriorit’s expertise in cybersecurity and cloud application development.
Who is responsible for protecting data in the cloud?
Vendors and users share responsibility for data security in the cloud. Everyone knows this, but everyone understands it differently.
For example, only 10% of security professionals believe that developers are responsible for data security in their cloud-native applications according to a survey by Snyk. At the same time, over 36% of developers think that protecting cloud data is their responsibility.
And the State of Cloud-Native Security Report 2024 by Palo Alto discovered that security processes trigger delays, stress, and DevOpsSecOps conflict. They surveyed more than 2,800 executives and practitioners from development, information security, or information technology departments. The survey results show that 83% view security processes as a burden, and another 79% say their employees frequently ignore or work-around security processes.
Many organizations believe they don’t need to worry about data security and compliance with IT requirements once they upload data to a cloud service. Indeed, a lot of cloud vendors implement strict cybersecurity procedures to help their clients protect sensitive data. And it’s up to their clients to decide whether or not to enforce these procedures, properly configure access rights, and demonstrate IT compliance.
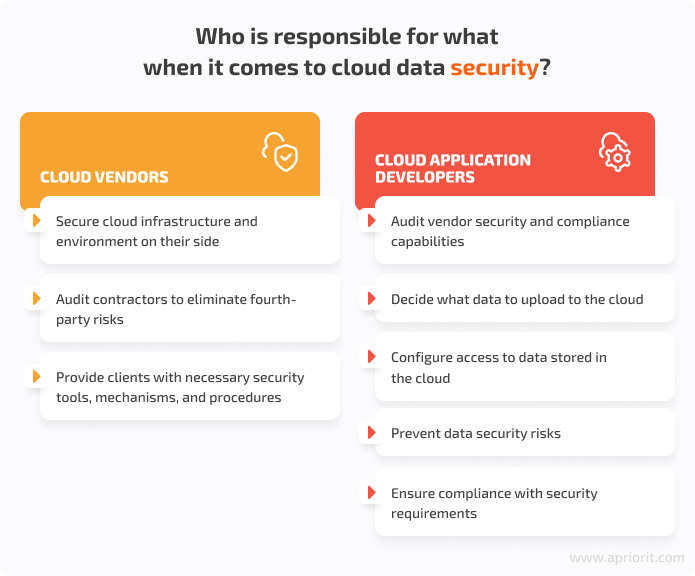
The areas of responsibility for cloud vendors and application developers (or DevSecOps specialists working on an application) are usually fixed in a service-level agreement (SLA). A typical SLA for cloud services defines:
- The volume and quality of work that a cloud vendor agrees to provide
- The required service performance parameters
- Security features and mechanisms that a vendor uses
- Plans for the remediation of security incidents and service outages
- Penalties for agreement violations
And while both cloud service providers (CSPs) and developers have robust opportunities to enhance data protection in cloud-based solutions, each party has to deal with numerous cybersecurity challenges in the cloud.
But what are the potential risks and mitigations for cloud-based application security? Let’s take a look at key challenges you can face when ensuring proper cloud-based application security and ways to avoid or tackle them.
Read also
Cloud Computing Attacks: Types, Examples, and Prevention Tips
Become aware of key vulnerabilities of cloud computing technology and most common types of attacks on cloud computing. Discover best practices and helpful insights from our own experience for ensuring the security of your cloud-based solution.

What are the cloud application security issues and how to fix them?
The use of cloud environments creates unique security challenges for cloud application development teams. The Cloud Security Report by Cybersecurity Insiders outlines the five biggest cloud security threats:
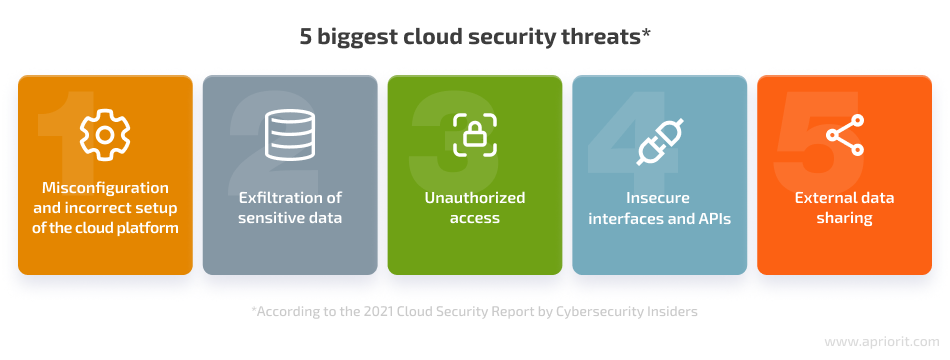
Let’s take a closer look at each of these problems and ways to mitigate them in order to create secure cloud-based software.
1. Misconfiguration and incorrect setup of the cloud platform
Leading cloud platforms like Microsoft Azure and Amazon Web Services (AWS) provide developers with lots of preconfigured security features. It’s up to developers to define the level of security that their product requires. And sometimes, unfortunately, this results in security-threatening misconfigurations of cloud environments.
Cybersecurity misconfigurations are considered one of the biggest security threats because it’s almost impossible to detect them with usual monitoring tools. Misconfiguration mostly happens due to the complexity of and constant changes to cloud environments, in addition to human errors.
Examples of common misconfiguration are:
- Unrestricted outbound access for elements of the cloud environment
- Open access to non-HTTP/HTTPS ports
- Errors in security rule configurations
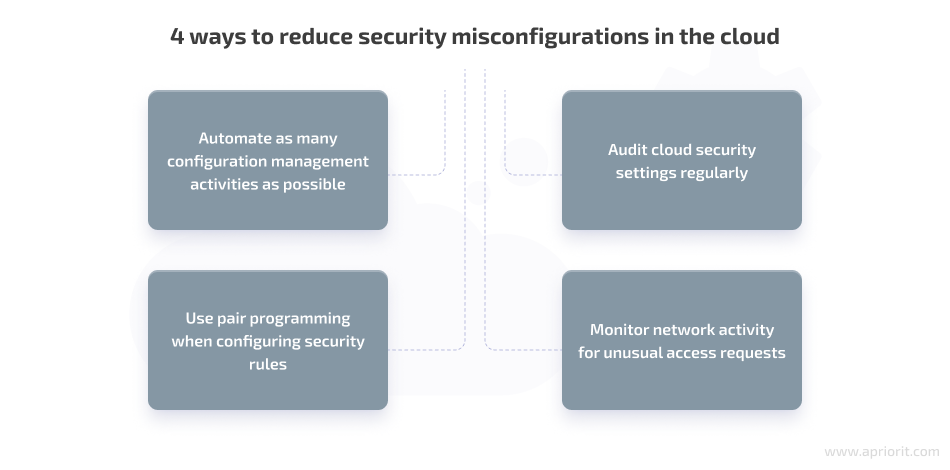
Most cloud security misconfigurations are discovered during a manual security review or as the result of a security incident. Fortunately, there are ways to prevent cloud security misconfigurations from happening. In particular, you can:
- Automate as many configuration management activities as possible
- Use pair programming when configuring security rules
- Audit cloud security settings regularly
- Monitor network activity for unusual access requests
2. Exfiltration of sensitive data
One of the major concerns of any cloud service provider and user is securing their data from unauthorized access and theft. Storing sensitive data in the cloud creates more entry points for malicious actors, and it’s up to both to secure them.
In this article, we will follow Google’s definition of data exfiltration:
Data exfiltration is defined as when an authorized person extracts data from the secured systems where it belongs, and either shares it with unauthorized third parties or moves it to insecure systems. Authorized persons include employees, system administrators, and trusted users. Data exfiltration can occur due to the actions of malicious or compromised actors, or accidentally.
Google Cloud documentation
The key causes behind data exfiltration are unrestricted data sharing capabilities, manual reconfiguration of virtual machines, and malicious insider activity.
Here’s how to secure cloud-based applications from data exfiltration:
- Create educational materials and cybersecurity tips for end users. This will help to prevent accidental data exfiltration.
- Enforce strict data protection policies and audit compliance. These policies should include the principle of least privilege for sharing access to data along with various levels of sharing capabilities for different categories of sensitive data.
- Encrypt data in transit and at rest. For instance, it’s common practice to secure network traffic with SSL/TLS encryption.
Related project
Building AWS-based Blockchain Infrastructure for International Banking
Explore a success story of designing and implementing AWS infrastructure that satisfied the client’s requirements and met the project deadlines. Discover how our client managed to deploy custom smart contracts and conduct a project demo for their customers thanks to Apriorit’s help.

3. Unauthorized access
Stealing the account or identity of a legitimate user is one of the most convenient ways to get inside a cloud environment. It’s crucial to ensure a high level of identity management and granular access management for cloud application data.
Securing cloud data storage from illegitimate access usually involves using the following types of tools:
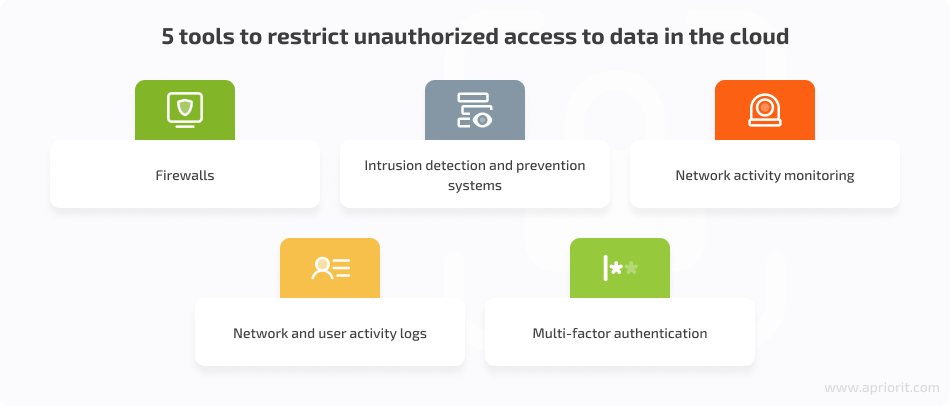
If your application has a multi-tenancy mode, you also need to ensure data segregation in order to prevent your tenants from accessing each other’s data.
The main advantage of using cloud services of big vendors, such as Microsoft Azure or AWS, is that they offer robust access management services that can help you ensure the needed level of security.
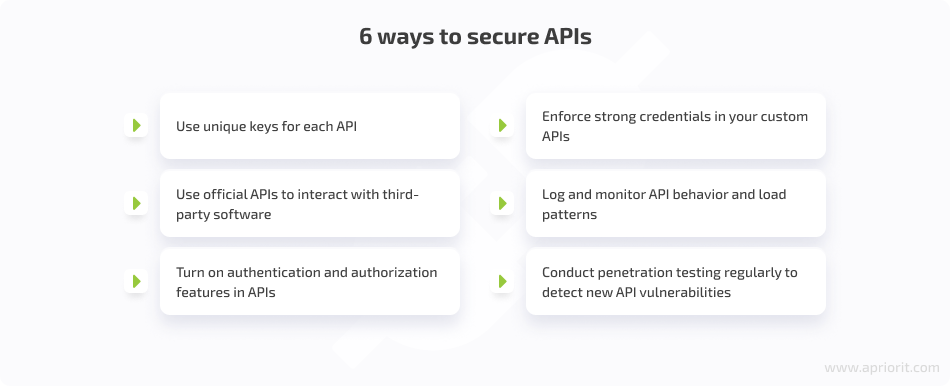
4. Insecure APIs
APIs allow parts of cloud software and third-party products to seamlessly interact with each other. When poorly protected, APIs can become gateways for hacking attacks and data leaks. For example, attackers can brute force a weak password an API uses to communicate with other software elements and sabotage their work or steal sensitive data.
Here are a few tips that will help you overcome API security challenges used in your cloud solution:
5. External data sharing
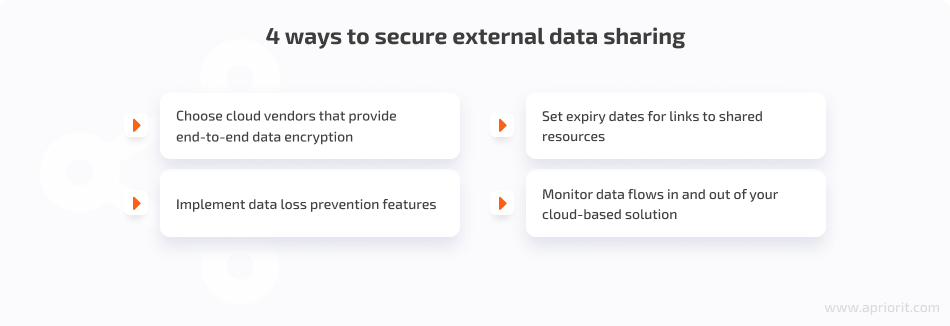
Cloud services make it extremely easy to share data with vendors, employees, and clients all around the world. Some enterprises even develop multi-cloud environments and use cloud services from different vendors to share various types of data and resources more conveniently. If you want to explore multi-cloud pros and cons, check out our article on multi-cloud computing.
Unmanaged and poorly managed data sharing may result in data leaks and loss of control over an organization’s sensitive data. That’s why you need to implement protection mechanisms that help your customers share their data in a secure manner.
You can ensure safe data sharing by following these rules:
With the cybersecurity tools and practices we discussed above, you’ll be able to protect sensitive data used by your cloud-based application and ensure proper data management. However, they might not be enough to comply with applicable cybersecurity requirements. Let’s see how you can create a cloud-based app using security standards.
Related project
Building a Microservices SaaS Solution for Property Management
Find out how Apriorit helped an American provider of property management solutions successfully implement a microservices-based SaaS platform with an updated design. Discover the details of how we managed to enrich the new platform with better scalability, easier code maintenance, and a more enjoyable user experience.
Ensuring compliance in the cloud
When building cloud-based software with security compliance in mind, you need to keep an eye on lots of IT security requirements, industry standards, local laws, and regulations. Below, we list several steps that require special attention.

1. Define your list of compliance requirements. The list of requirements you need to comply with depends on the services you’re offering, your target industry, and the geographical location of both your business and your customers. ISO/IEC 27001 is one of the most widely recognized international standards for information security. There are also four specific standards for cloud computing security: ISO/IEC 27002, ISO/IEC 27017, ISO/IEC 27018, and ISO/IEC 27036-4.
Other common examples of IT security regulations are special publications by the National Institute of Standards and Technology. The General Data Protection Regulation lays out rules for protecting the data of EU residents.Depending on the region and industry you’re working in, you may also need to comply with HIPAA (for US healthcare organizations and those working with them) and PCI DSS (for organizations storing, processing, or transmitting credit card data).
2. Choose compliant cloud services. If you aren’t building your entire system from scratch, you need to choose the right CSPs. When picking providers, it’s crucial to think about what compliance requirements are vital for you now and which you may need to follow in the future. Otherwise, you risk wasting extra time and money down the road when switching to a different vendor because of compliance issues.
3. Conduct internal IT compliance audits. Automating and managing infrastructures in the cloud enables developers to adjust cloud applications more quickly than on-premises solutions. Regular internal compliance audits can help you verify that required security mechanisms work and that your application is still protected even after updates. But keep in mind that IT compliance and data security aren’t always the same. It’s best to run compliance and security audits separately.
Conclusion
When building a cloud-based product, you need to take into account cloud characteristics that may endanger your product’s data security and IT compliance. Even if you work with a big cloud provider that offers additional security services and complies with the laws, regulations, and standards you must follow, there are still many factors you should pay close attention to.
Knowing how to protect your data in the cloud is essential. By mitigating the most common security threats in the cloud, you can increase the security of cloud solutions and boost your customers’ confidence. This can be useful for various projects. For example, when working with the Internet of Things (IoT) technologies, you need to know how to overcome IoT security challenges.
At Apriorit, we have dedicated teams with vast expertise in cybersecurity, cloud computing and virtualization development, and cloud infrastructure management. We have rich experience helping many enterprises build and protect custom SaaS products, and are ready to assist you with a project of any complexity.
Need help with a cloud-based project?
Get in touch with Apriorit to leverage our hands-on experience and secure your cloud-based software!




