Many security leaders are rightfully suspicious about implementing DevOps despite its numerous benefits, including fast software delivery and increased code quality. It doesn’t matter how fast your continuous delivery cycle is if you’re releasing software with vulnerabilities. And cybersecurity is the one thing that DevOps lacks desperately.
That’s where DevSecOps comes into play — a development approach that shifts security left in the software development lifecycle (SDLC). DevSecOps emphasizes the importance of implementing security checks at the earliest stages.
In this article, we show you the benefits of adding security to DevOps, the key challenges of adopting DevSecOps, and best practices of implementing DevSecOps with AWS services.
Contents:
Why isn’t DevOps secure?
DevOps is a combination of tools, practices, and cultural philosophies that allow IT companies to reduce the time needed for software development. This is achieved by breaking down the traditional barriers between development, testing, and operations. DevOps practices include automation and monitoring of all activities during software development, allowing companies to achieve continuous integration (CI) and continuous delivery (CD). You can combine DevOps and blockchain, artificial intelligence, embedded, mobile, and other types of technologies.
Building an efficient CI/CD pipeline can greatly speed up development activities and your product release, thus saving time and money for solutions vendors.
However, today it’s not enough for IT companies to implement faster and more innovative methods of software development. They also need to keep cybersecurity in mind. By design, DevOps lack security for several reasons:
- Traditionally, information security is handled at the last stages of the software development cycle and results in detecting security flaws that need to be eliminated under strict time limits. For the DevOps approach, securing each release in a traditional way would require too much effort.
- DevOps is often implemented with cloud-first architecture and containerization. These both create a broader attack surface and new potential vulnerabilities.
- Security mechanisms have to be updated or at least checked during each iteration. Yet release teams sometimes neglect these recommendations in order to meet delivery deadlines.
Fortunately, we have DevSecOps: a shift-left mindset where security is a shared responsibility so both developers and IT operations specialists keep security requirements in mind. Let’s see how DevSecOps is different from DevOps and what benefits it offers.
What is DevSecOps?
DevSecOps implements continuous and automated security mechanisms at the early stages of software development and ensures security throughout the whole cycle. Security is no longer the function of a separate department but is an integral part of a team’s culture and practices.
Integrating security into your DevOps team helps your company achieve the following benefits:
DevSecOps allows you to spend more time adding customer value and less time and money fixing vulnerabilities that are identified late in the delivery process or during product use. But shifting left is not without its limitations. Let’s take a look at the key challenges you can run into.
Challenges of implementing DevSecOps
Integrating security into DevOps requires some organizations to significantly transform their workflows. That affects not just the cybersecurity system but organizational and business processes as well. Such changes always bring numerous challenges, and it’s best to prepare for them in advance. Let’s explore four major challenges.
1. Changing the established corporate culture
The most common issue that organizations run into is the cultural change needed to adopt DevSecOps. People that have been using traditional or Agile development approaches often have trouble adapting to a completely different approach.
When shifting to DevSecOps, your team has to learn a lot about cybersecurity, become more open about work issues, and make security practices part of their routine. A lot of organizations underestimate how challenging these changes can be and fail to implement DevSecOps to its fullest as a result. Make sure to provide your team with enough knowledge, support, and leadership during the transition to DevSecOps.
2. Combining Agile and DevSecOps
Another issue is that some organizations try to completely substitute an Agile workflow with DevSecOps. When this attempt fails, they decide that DevSecOps isn’t for them. The real challenge here is to combine Agile and DevSecOps in the most efficient manner for your organization.
DevSecOps can complement Agile. While Agile introduces collaboration, iterations, and constant feedback to the development process, DevSecOps can reinforce QA and delivery processes while making your code secure all along the way.
3. Staying compliant with government regulations
Implementing DevSecOps is harder for organizations from industries that must comply with strict cybersecurity requirements: healthcare, manufacturing, financial services, etc. Regulations in these industries aren’t flexible enough to allow companies to fully introduce DevSecOps practices.
That’s why organizations often have to combine flexible and secure DevOps with traditional development approaches. Some government agencies like the U.S. Food and Drug Administration do allow companies to change their development practices any way they want if they can ensure a high level of security and recertify their workflow.
4. Integrating traditional, DevOps, and DevSecOps tools
There’s also a technical challenge in adopting DevSecOps. Integrating traditional security tools like antivirus software and firewalls, DevOps, and DevSecOps tools into one system requires significant changes to an organization’s infrastructure. CI/CD pipelines, binary libraries, static application security testing, software composition analysis, and many other tools usually come from various vendors, but you’ll need to make them work together.
The best way to overcome this challenge is to thoroughly plan the implementation of DevSecOps tools and deploy the tools you choose one by one. Deploying and configuring them all at once is quicker and might seem more convenient, but in fact it will create chaos and lead will lead to security vulnerabilities.
Researching these challenges and planning your way around them is the key to smooth DevSecOps implementation. Now, we can take a look at must-have security practices and mechanisms to ensure your DevOps processes are secure.
Best practices to integrate security into DevOps
The main task of DevSecOps is to integrate security into DevOps by ensuring secure coding practices in the early stages of the SDLC. While automation is required, DevSecOps is not only about this. First of all, developers and operations specialists should be trained to understand a hacker’s logic and know how to prevent attacks with security measures. Only after that can they properly use tools that are designed to discover flaws and ensure security during development and testing.
1. Cultivate security and openness as part of your organization’s culture
If you want to integrate security into your DevOps team, the first step is changing your culture with the following activities:
- Build a knowledge base. Train developers and QA specialists to ensure they know basic principles of secure coding and testing and thus can take responsibility for meeting security requirements.
- Promote openness. Encourage open communication and collaboration between the DevOps and security departments, which usually work independently. Make sure that security metrics and dashboards are transparent, available, and understandable to developers so they can apply them to check code quality.
- Create security champions. Hire professional security officers who understand security within traditional DevOps teams and can coach your team to ensure they’re security conscious during the transition to DevSecOps. Security champions should be aware of industry best practices and be involved in DevSecOps consulting on how to adapt security for software development.
However, don’t go overboard with this practice. Your employees don’t need to become experts on cybersecurity — they only need enough knowledge and training to ensure security in their sphere of responsibility.
2. Acquire a reliable version control system
Short sprints and continuous delivery require developers to make many changes in the application’s code each sprint. You have to be able to track those changes, see what was changed and by whom, and see whether they had the authorization to do so. You also need the possibility to quickly roll back changes and revert to the previous version of the code.
That’s why it’s important to deploy a version control system before implementing DevSecOps practices into your SDLC. Choose a version control system that has:
- Authorization and identity verification mechanisms
- Digital signatures for developers
- Diverse change control techniques
- Collection of metadata for code versions
- Application lifecycle management tools
You can also opt for a distributed version control system that mirrors the software’s codebase and all the code changes on the developer’s machines.
3. Build DevSecOps processes
Building a secure CI/CD pipeline requires adding security checks and scans at each stage of the development process. Let’s see what you can do to protect your software during each iteration:
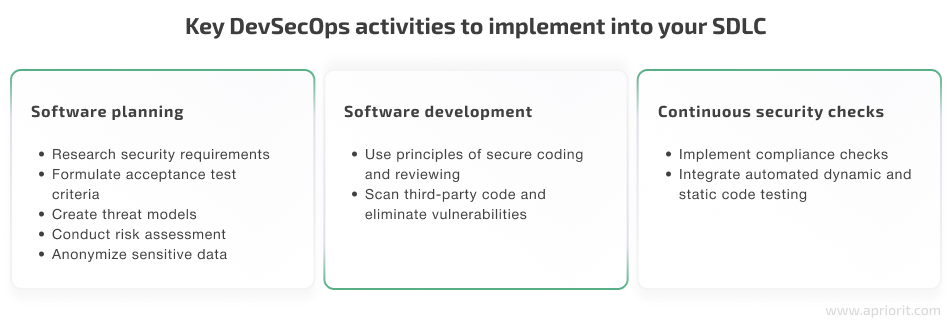
1. Security measures during software planning
In addition to collecting functional and non-functional software requirements, product features, and potential use cases, you also need to research security requirements, acceptance test criteria, and threat models. Potential security issues should also be taken into consideration starting from the software planning stage.
During the planning stage, you can use threat modeling and risk assessment tools to understand your application’s level of risk. You may need to build a deeper threat model if your application will process sensitive data or directly access the internet. Moreover, if you apply any data for application testing, think about how you’ll anonymize it to avoid privacy issues.
2. Security measures during software development
At the development stage, DevSecOps requires your team to follow principles of secure coding and reviewing of software design and code. However, all these tests and checks shouldn’t slow down the development process. That’s why you need to automate as many processes as possible.
You also need to integrate automated dynamic and static code testing that can detect security vulnerabilities before software is released. These autonomous scans don’t require the intervention of security officers and can add results directly to a bug tracking system.
As an alternative to such tests, you can let developers use lightweight tools for quick code scanning within their integrated development environments. Making automated scanning and security test software an integral part of the continuous integration test toolchain helps to significantly reduce the number of security vulnerabilities.
3. Continuous security checks
DevSecOps practitioners should secure their code by securing their environments. While developers frequently use open-source applications and pre-built libraries, containers, and frameworks, they need to eliminate any known critical vulnerabilities in these components before using them.
That’s why you need to conduct vulnerability checks for all contents of all system images, including:
- Cloud environments
- Virtual machines
- Containers
- Operating systems
- Other software
Continuous integration should include checking that all operating system and application platform settings are configured in compliance with security best practices.
While containers use a common operating system, any attacks on them may result in compromising your container. Thus, the best practice is to use containers on workloads of similar trust levels. However, for stronger isolation, it’s better to use hypervisors or physical separation.
4. Prioritize iterations over perfection
Traditional development approaches teach us to fix all issues before releasing software. With the frequency of releases in the DevSecOps approach, polishing your code until it’s perfect can be time-consuming and can even lead to crunching before the release — which, in turn, will lead to more time spent fixing and patching during the next sprint.
Planning ahead and iterating your work is the key to the successful implementation of DevSecOps. So instead of trying to achieve perfection in one sprint, assess discovered security issues, decide which have to be addressed as soon as possible, and save others for a future iteration.
Continuous risk assessment and threat monitoring can help you decide which vulnerabilities you need to fix as fast as possible.
Read also:
API Security Risks: The 6 Most Common Security Issues in API Development and How to Fix Them
5. Automate processes with a security as code approach
While DevOps works with programmable infrastructure as code, security measures should also be adjusted to this principle. Secure coding principles should apply to the automatic configuration of scripts, templates, recipes, and blueprints. Security as code helps you to apply these principles automatically.
Security as code is a practice that allows developers to define security requirements, policies, and best practices in code. Then, they can integrate this code into a CI/CD pipeline, automating security tests, checks, and scans. With security as code, you can automate:
- Static and dynamic code analysis
- Certain penetration testing activities
- Compliance checks
- Scans for vulnerabilities and risks like embedded credentials, API keys, and encryption keys
- Delivery of feedback to developers

Describing your security requirements as code demands a great deal of caution and expertise because there’s a risk of deploying misconfigurations and vulnerabilities with this code through all of your CI/CD pipeline. That’s why you need to use pair programming or conduct a code review before deploying. Also, it’s best not to automate risk assessment and prioritization tasks, or at least to review their results before acting on them.
Read also:
Infrastructure Automation: 7 DevOps Tools for Orchestration, Secrets Management, and Monitoring
6. Manage access to DevSecOps tools
Traditional static access control tools aren’t enough for securing sensitive resources in the DevSecOps environment. A rapidly changing environment and blurred areas of user responsibility make it hard to configure user access rights once and for all using, say, role-based access management tools.
To ensure a high level of security, you need to use dynamic access provisioning tools and approaches like zero trust network access control, the Kerberos authentication protocol, or customizable attributed permissions.
Also, DevSecOps requires enhanced secrets management. With all code uploaded to public repositories or cloud services, you can’t hardcode sensitive data or upload files with credentials, SSH keys, and API keys. Instead, you should implement a secrets management tool that will encrypt these secrets and store them in a protected vault.
These practices will help you build a fast, iterative, and secure CI/CD pipeline. And since you’ll also need reliable tools, let’s find out how to implement DevSecOps in AWS infrastructure.
Which AWS services should you use when shifting to DevSecOps?
Building a complete CI/CD pipeline with tools from numerous vendors is extremely challenging because you have to worry about integrations, data collection and compatibility, and securing the work of each tool. Also, any update to any tool may damage your software infrastructure or automated processes and lead to more work.
That’s why we prefer to secure DevOps with AWS tools and services that help us build a consistent and secure pipeline. AWS virtual infrastructure includes a set of tools aimed at automating code testing and, in particular, applying security checks during the whole code development and quality assurance process.
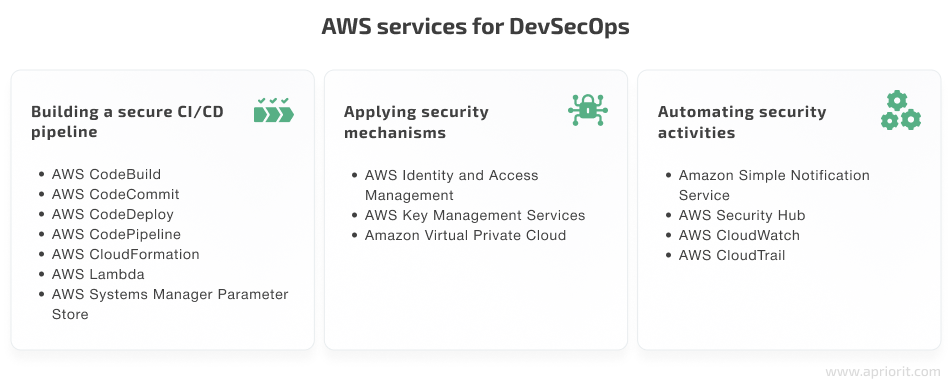
Building a secure CI/CD pipeline
You can integrate security into the DevOps pipeline with these AWS tools and services for automated code building, deployment, and analysis:
- AWS CodeBuild — A service that compiles source code, runs tests, and prepares software packages for deployment.
- AWS CodeCommit — A source control service for hosting secure Git-based repositories. To use it, your DevSecOps team needs to configure their Git client to communicate with AWS CodeCommit repositories.
- AWS CodeDeploy — A service for automated code deployment to AWS-based, on-premises, and third-party computing services.
- AWS CodePipeline — An efficient CI/CD service that allows DevOps engineers to automate preventive and detective security controls. Implementing DevSecOps using AWS CodePipeline ensures swift and secure software updates.
- AWS CloudFormation — A service for describing and provisioning infrastructure resources automatically and securely. Using this service, DevSecOps practitioners can create a secure template of the demo pipeline.
- AWS Lambda — A serverless computing tool that automatically runs your code in response to detected triggers. You can use it to perform static code analysis and conduct dynamic stack validation for security groups in the scope.
- AWS Systems Manager Parameter Store — A part of AWS Systems Manager that allows you to securely store configurations and manage secrets. Parameter Store makes AWS infrastructure transparent and controllable.
Applying security mechanisms
Protecting sensitive data is especially important when you upload it to public (or even private) repositories or cloud services. Use the following AWS tools for DevSecOps implementation:
- AWS Identity and Access Management — A service that shows who is responsible for what when making changes to a product. It helps to verify who implements changes, audit logs, and configuration repositories and manage access rights.
- AWS Key Management Services — Services for creating and managing the encryption keys necessary for data protection. These services use validated hardware security modules to ensure the security of your keys.
- Amazon Virtual Private Cloud — A service that lets you create private clouds within the AWS public cloud. Virtual Private Cloud provides not only isolation from other customers in the private cloud but also Layer 3 isolation from the internet.
Automating security activities
Automation is the core of DevSecOps AWS services. The following security automation tools can come in handy for automating incident response, remediation, and forensics:
- Amazon Simple Notification Service — A fully managed messaging service for automating application-to-application and application-to-person communications.
- AWS Security Hub — A service that gives you a comprehensive view of your security alerts and security posture across your AWS accounts. It also helps to automate security checks and alert management.
- AWS CloudWatch — An AWS resources monitoring tool that collects and systematizes logs from your AWS accounts and parts of AWS infrastructure.
- AWS CloudTrail — A service that can monitor calls made to the CloudWatch API for an AWS account. With CloudTrail, your security officers can quickly respond to suspicious activities.
Conclusion
DevOps is an effective approach for improving software engineering and maintenance processes. However, companies can benefit from its full potential only after integrating security into DevOps practices.
Introducing DevSecOps with AWS services requires extensive security training, careful planning, and the right balance of automation and manual activities. However, following the best practices of integrating security into DevOps will help you successfully overcome these challenges.
Apriorit has experience establishing secure DevOps processes in many cloud computing and cloud infrastructure services, including AWS. Contact us to leverage our knowledge for the benefit of your cloud-based projects!




