Corporate mailboxes are vital for any organization’s workflow. And because of their importance, business email addresses often become targets for various malicious actors who aim to steal emails, get access to sensitive information, or gain entry to any accounts with software services that might be connected to a given email address.
As an email service provider, you have to make sure your product protects your clients from emails that contain dangerous files, links, and information that can infect a PC or steal data. In this article, we overview eight key security features an email provider should implement in their solution to protect emails.
This article will be useful for engineers and product owners of email-associated projects that want to ensure the security of an email service. It can also be helpful for business owners who want to improve the email protection of their companies and employees and learn practices to enhance email security.
Contents:
- How can emails threaten a business?
- 1. Provide clients with robust email account protection settings
- 2. Ensure robust email authentication
- 3. Establish attachment scanning functionality
- 4. Ensure email body scanning
- 5. Add denylists and allowlists
- 6. Implement a quarantine feature
- 7. Add email encryption functionality
- 8. Help your clients maintain a high domain and IP reputation
- Conclusion
How can emails threaten a business?
Businesses use corporate email domains to communicate with clients, ensure a convenient information flow within the organization, and launch email marketing campaigns. They expect their business emails to be protected by email service providers.
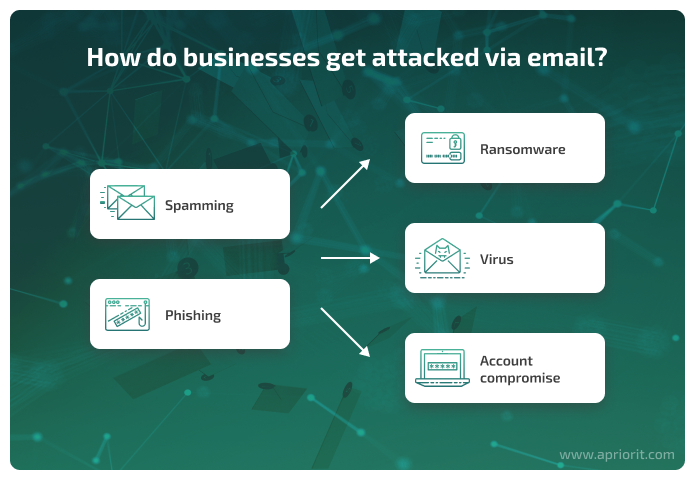
Two common email treats to watch out for are spamming and phishing:
- Spamming is the use of messaging systems to send multiple unsolicited messages to large numbers of recipients. The purposes can vary, from commercial advertising to fraudulent purposes like phishing. Some spam emails try to elicit personal information to add to a database for further spam attempts.
- Phishing is a type of social engineering where an attacker sends a fraudulent email designed to trick a victim into revealing sensitive information to the attacker or deploy malicious software on the victim’s infrastructure.
According to IBM’s X-Force Threat Intelligence Index 2022 report, phishing is one of the most common vectors for ransomware attacks. Ransomware is a type of malware that blocks access to users’ files and data and demands a ransom in order to allow a person or organization to regain access. Another possible threat sent via email is a virus that can distribute malicious code to infect one or more devices. Malicious actors can add viruses to attachments or ask a person to click a link that downloads a dangerous file.
Even emails sent from trusted addresses can be dangerous. Say that a cyber criminal manages to compromise the email account of an organization’s client. In this case, the cyber criminal can send a malicious email from a trusted sender (the client), exploiting the compromised account owner’s reputation to trick email recipients at the organization.
Thus, email service providers should continuously keep an eye on the cybersecurity capabilities of their solutions. When developing a mailbox service from scratch or improving an existing one, pay attention to possible cybersecurity threats and provide features to help your clients mitigate them.
Let’s discuss eight key functionalities that can help email service providers ensure that their customers safely work with corporate emails and follow email security best practices.
1. Provide clients with robust email account protection settings
Let’s start with the creation and use of corporate email accounts. It’s a must for businesses to set up their own email domains instead of letting employees use their personal email accounts for work purposes.
The reason for that is pretty simple: a company can’t control and properly secure employees’ personal email accounts. However, organizations have to ensure the security of corporate and customer data and need to know how employees interact with suspicious emails.
An email provider should help businesses take control of cybersecurity matters when establishing corporate email accounts. Make sure your product allows your clients to:
- Enforce a password policy, including common practices like setting an eight-symbol minimum password length as well as requiring uppercase and lowercase letters, numbers, and special symbols.
- Set the password expiration time according to corporate cybersecurity policies so your clients can ensure regular password updates.
- Restrict access to or delete an email account when an employee leaves the company. If employees use their personal email accounts, they will still have access to work emails after they leave.
- Configure different security features based on business needs.
The best solution would be to use a directory service like Microsoft Active Directory in your secure email service so you can import data from it. In this case, your clients’ system engineers can control user accounts in the directory service as they usually do. The connected email service provider can automatically apply changes to mailboxes based on directory service user updates.
2. Ensure robust email authentication
Email authentication is a collection of techniques aimed at providing verifiable information about the origin of email messages. To do so, these techniques validate the domain ownership of any message transfer agents who participated in transferring and possibly modifying a message.
As a result, properly configured email authentication mechanisms help filter junk emails before they reach users.
The most common email authentication techniques are DomainKeys Identified Mail (DKIM); Sender Policy Framework (SPF); and Domain-based Message Authentication, Reporting and Conformance (DMARC). These are typically used together. You can configure them inside email domain properties.
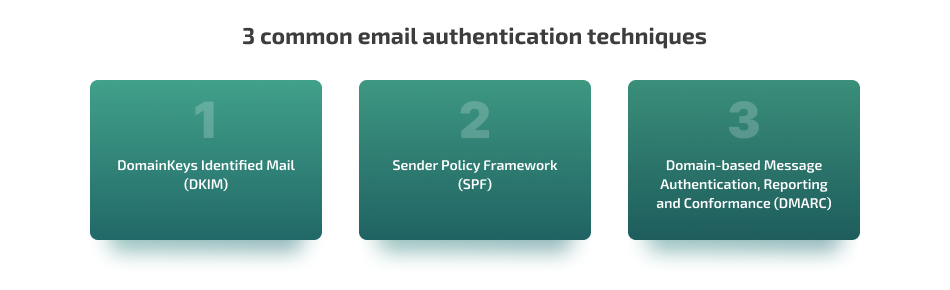
Let’s explore each in detail:
2.1. DomainKeys Identified Mail
DomainKeys Identified Mail (DKIM) is an email authentication method that allows the recipient to verify that an email was actually sent from the declared domain.
DKIM adds a digital signature associated with the organization’s domain name to determine the sender of a message. The organization’s domain name is automatically verified on the recipient’s side. Adding a DKIM signature to your email domain helps you improve the domain’s trustworthiness.
A DKIM signature can look like this:
DKIM-Signature: v=1; a=rsa-sha1; c=relaxed/relaxed; s=20130519; d=example.com; h=From:Date:Subject:To:Message-ID; [email protected]; bh=vYFvy46eesUDGJTH30JfN4=; b=iHeFQ+7rCiSQs3DPjR2eUSZSv4i/BGfkX7X8RVObMQsBasic DKIM parameters are:
- b — the contents of the email (email body and headers encoded in Base64)
- bh — the hash of the canonicalized message body (encoded in Base64)
- d — the domain name of the sender
- h — a list of signed headers
There are also additional parameters:
- a — main algorithm to generate a signature
- v — DKIM version
- s — selector record name used with the domain to locate the public key in DNS (the value is a name or number created by the sender)
- c — algorithm that converts the body of the email and headings to the canonical form
- q — list of algorithms for obtaining a public key
- x — signature expiration time
- i — signature of the client who signed the DKIM
- l — size of the message body in bytes included in the cryptographic hash
- t — timestamp of the affixed signature
- z — copies of headers at the moment of signing
2.2. Sender Policy Framework
Sender Policy Framework (SPF) is an email authentication method that aims to protect users from spoofed emails, or messages created with a forged sender address. It can detect the forging of the visible sender in emails only when used in combination with DMARC.
SPF defines a list of IP addresses authorized to send emails from a specific domain and detects forged sender addresses during email delivery. Organizations can use SPF to check if a sender’s domain has been spoofed.
SPF allows a domain owner to specify in a domain’s TXT record an identified generated structure that specifies a list of servers that have the right to send email messages from that domain.
An SPF record can look like the following:
v=spf1 +mx -ip4:195.31.159.250 +a:smtp.testmail.com include:gmail.com ~allLet’s take a closer look at the parameters:
- v — version of SPF
- + — accepts emails (option set by default)
- – — rejects emails
- ~ — soft deviation: an email will be accepted, but marked as spam
- ? — neutral
- mx — all server addresses specified in mail exchanger (MX) records of the domain
- ip4 — specifies a certain IP address or network of addresses
- a — specifies the behavior in case of receiving an email from a specific domain
- include — includes hosts allowed by the specified domain’s SPF record
- all — all other servers not listed in the SPF record
And here’s the explanation of SPF records from the example above:
- +mx — receives messages from servers specified in MX records
- -ip4:195.31.159.250 — rejects messages sent from IP address 195.31.159.250
- +a:smtp.testmail.com — receives emails from smtp.testmail.com
- include:gmail.com — accepts emails from servers allowed by gmail.com SPF records
- ~all — accepts messages from all other servers, but marks them as spam
2.3. Domain-based Message Authentication, Reporting and Conformance
Domain-based Message Authentication, Reporting and Conformance (DMARC) is an email authentication protocol that helps protect email domains from various cyber threats like spoofing, business email compromise attacks, phishing, and scam emails.
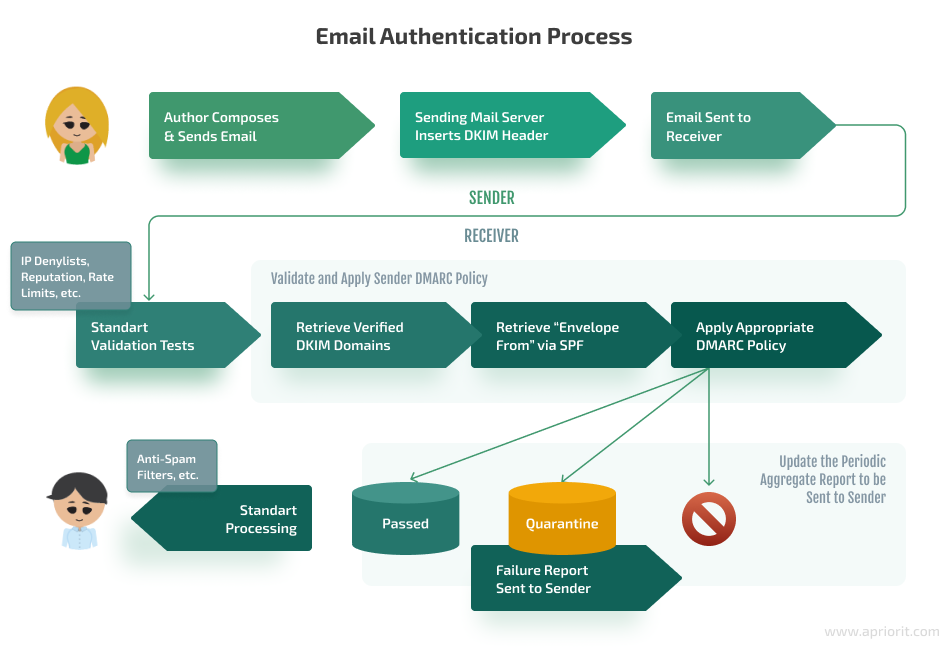
DMARC can be added only after SPF and DKIM records are configured. Here’s how DMARC works together with DKIM and SPF:
- If an email message fails at least one check, then it won’t pass DMARC either
- An email will pass the DMARC check if both the DKIM and SPF checks are successful
This protocol provides a signature that allows the receiving server to reject or quarantine a message that didn’t pass DKIM and SPF checks. The DMARC policy can also specify how an email receiver can report back to the sender’s domain about messages that pass and/or fail.
A DMARC record can look like this:
v=DMARC1; p=reject; sp=reject; ruf=mailto:[email protected]; fo=1Here are parameters that DMARC records can have:
- v is a mandatory parameter that specifies the DMARC version
- p is a rule for the domain, also a mandatory parameter. It can have the following values: none does nothing but renders reports; quarantine adds the email to spam; reject rejects the email.
- sp is responsible for subdomains and can have the same values as p
- aspf and adkim — determine how closely message data must match the signature: SPF for the aspf parameter and DKIM for the adkim parameter. These parameters can have the following values: r allows partial matches like valid subdomains and s allows only strict matches.
- pct specifies the number of messages to be filtered and is indicated as a percentage. For example, pct=20 will filter 20% of messages.
- rua allows you to send daily reports to an email address, like [email protected]. You can also specify several emails separated by a space: [email protected] mailto:[email protected]/
- ruf helps you create reports for messages that didn’t pass the DMARC check
- fo generates reports if one of the mechanisms breaks down. For example, fo=0 is used by default and sends a report if no authentication stage is passed. fo=1 sends a report if at least one authentication stage is not passed. fo=d sends a report if DKIM authentication fails. And fo=s sends a report if SPF authentication fails.
3. Establish attachment scanning functionality
One of the most common ways to get a PC or even a corporate network infected by malware is by interacting with an email that has infected files in attachments. To prevent situations like this, email service providers should ensure special filtering and virus scanning features.
Let’s discuss each of these options in detail.
File type filtering
To help your end users secure their computers from malware, make sure your email service solution can detect emails with suspicious files even without using antivirus software.
To do it, ensure your solution checks the attachment file type and filters emails based on this information.
Here are six file types that are likely to have a virus inside:

1. Executable files
If you run any executable file, its program code will be executed on your PC. Malicious code can also be executed this way. Sending executable files via email is suspicious because there are many more efficient ways to do it: via cloud storage, network folder sharing, FTP, etc.
So if users receive emails with executable files attached, these messages are likely to be a threat. Make sure your solution can filter all emails with such files.
Executable file types to keep an eye on: EXE, MSI, BAT, BIN, APP, etc.
2. Program source code and hypertext files
These files also include program source code and should be filtered for the same reasons as executable files.
Program source code file types that can be a threat: JS, CPP, RB, HTML, PHP, JAVA, etc.
3. Archives
Your clients can’t know for sure what’s inside an archive.
Archives can hide various malware files or even a zip bomb, a malicious archive file designed to crash or render useless the program or system reading it. A zip bomb is often employed to disable antivirus software and create an opening for more traditional malware. A zip bomb allows a program to function normally, but instead of hijacking the program’s operation, it creates an archive that requires an excessive amount of time, disk space, and memory to unpack.
Popular archive file types: ZIP, RAR, TGZ, 7Z.
4. Office document files
These types of files can include macro malware, which is a virus written in a macro language — a programming language embedded inside a software application (e.g. word processors and spreadsheet applications).
Applications like Microsoft Word, Excel, and PowerPoint allow macro programs to be embedded in documents. Macros run automatically when the document is opened, and this provides a distinct mechanism by which malicious computer instructions can spread.
Commonly used office document file types: DOC, DOCX, XLS, XLSX, PPT, PPTX, PDF.
5. Email files
Anyone can easily save any email message as a file using an email client. Receiving a re-sent email in such a form can seem safe to an employee. But in reality, these files can contain viruses just like archives.
Email file types to be aware of: MSG, EML, OFT, etc.
6. Password-protected or encrypted files
Password-protected files sent via email can also look innocent. However, no one knows what can be inside those files. It would be wise to check and filter emails with password-protected or encrypted files as well.
Password-protected or encrypted files could be of any file type.
Antivirus functionality
Viruses can be included not only in those file types discussed in the previous section. Malicious actors can insert a macro virus or virus source code as text inside the email body.
To enhance your email service security, you can use in-house or third-party antivirus libraries as a service which scans emails and sends them to quarantine after a threat is detected.
If your company develops its own antivirus software, you can implement it in your email service provider solution. For example, we worked with an antivirus development company that wanted to expand its services and create an email product. Apriorit developers successfully delivered a solution using the client’s existing antivirus software.
With third-party services, you can even implement several antivirus programs if you want to be sure you don’t miss any infected files. To do it, you should purchase the necessary antivirus licenses. But make sure to assign the order in which they work, because antivirus applications can cause each other to malfunction when operating simultaneously. For example, say Bitdefender starts scanning and placing infected emails in quarantine. If it doesn’t find anything, then it’s Sofos’ time to work, and so on.
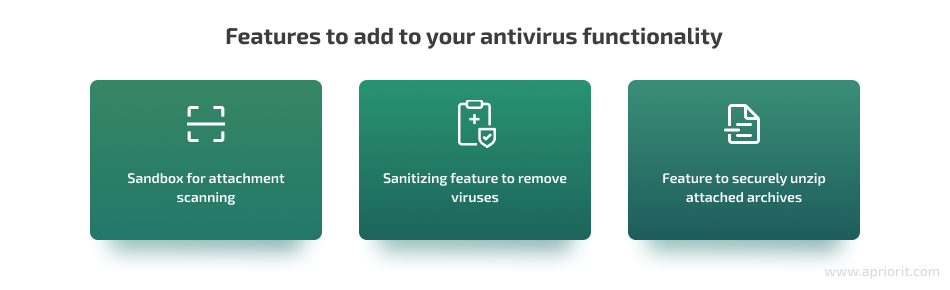
For scanning attachments, consider adding a sandbox feature to your antivirus functionality. A sandbox is a secure place where your antivirus software can store attachments and securely scan them, or even execute a file and check what happens.
Also, consider adding a sanitizing feature. If a virus-infected attachment is detected, your antivirus solution can try to sanitize it. If this action is successful, you can get the email with attachments that don’t have viruses anymore. In other cases, you can get the email but without attachments at all.
Another good idea is to ensure a feature that unzips the attached archives in some secure storage like a sandbox and scans files using an antivirus feature. If threats aren’t detected, then your solution should send an email to the user. If you have a feature like this, you don’t need to automatically filter emails with attached archives.
4. Ensure email body scanning
One of the key practices to improve email security is to ensure your service has a text scanning feature that can detect suspicious email contents. The two most common types of suspicious content are spamming and phishing.
Emails can be considered suspicious if they contain any sexual content or sensitive data like card numbers, phone numbers, license plates, etc.
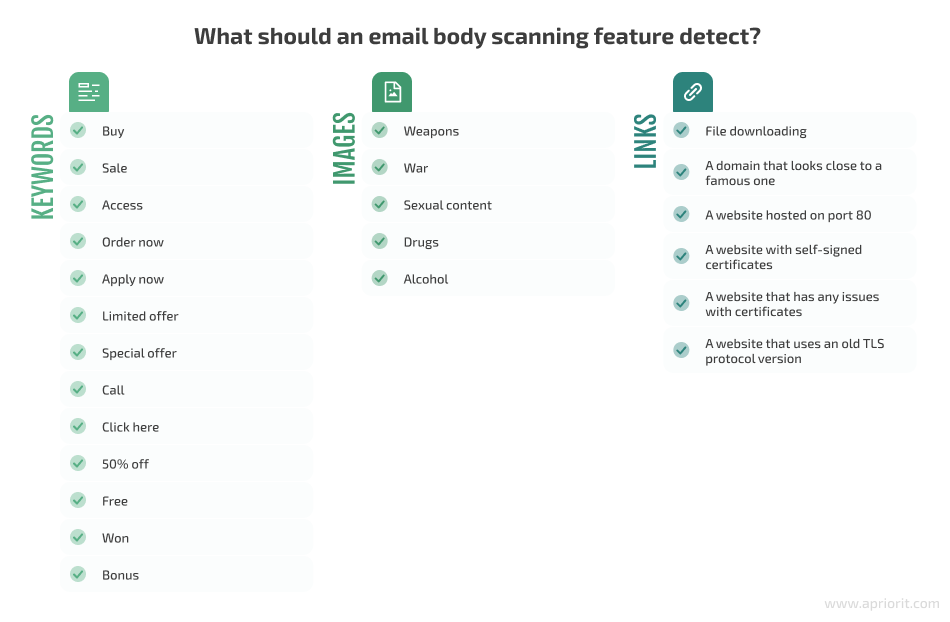
Suspicious emails can be detected by keywords in the text or the email subject. You can have a database of keywords and phrases for suspicious emails. For example: buy, sale, access, apply now, free, won, bonus, etc.
Of course, if only one keyword was detected, then the email can’t be marked as spam. An email should contain at least a minimum number of keywords to be marked as potential spam or phishing. For example, if ten spam keywords were detected, then it’s spam. Every organization should be able to customize the minimum number of spam words for their emails.
If an email contains images attached or placed in the email body, then it would be useful to detect and scan them. To do that, you can use image recognition algorithms. Examples of suspicious image content are weapons, war, sexual content, drugs, and alcohol. An email body scanning feature can also filter unwanted emails and detect content which can be considered suspicious. You can develop such a feature yourself or use relevant third-party solutions.
It would also be useful to ensure the ability to detect and filter links inside an email body or subject. On the one hand, links can lead to viruses or shady websites. On the other hand, adding links to a business email is common. That’s why it would be great not just to detect the links but also scan them for threats.
Suspicious links are those which lead to:
- File downloading
- A domain that sounds close to a famous one, such as gooogle.com instead of google.com. In this case, a user can miss the difference and think it’s a real safe website. You can integrate your product with an existing third-party solution with databases of fake domains for mitigating such threats.
- A website hosted on port 80 (HTTP protocol)
- A website with self-signed certificates
- A website that has any issues with certificates (expired, revoked, etc.)
- A website that uses an old TLS protocol version (TLS 1.0, 1.1)
The last four examples pose the same threat: they aren’t protected by common security protocols. Websites with these issues can’t guarantee your actions are safe and that no data will be stolen by threat actors.
5. Add denylists and allowlists
Make sure your email solution allows clients to easily and conveniently create allowlists and denylists. This will help them ensure they receive emails they expect and block emails from spammers.
A denylist is a feature that automatically sends all of a sender’s emails to quarantine based on the user’s or administrator’s decision. For example, if an organization doesn’t want employees to receive emails from a certain user, domain, or IP, they can add the sender to the denylist.
An allowlist feature allows you to always get emails from a certain sender. If a sender is added to the allowlist, their emails will be ignored by previously discussed features. This can be useful if senders typically use words or phrases from the spam keyword database. Another case is when the sender attaches files which are automatically filtered. Make sure to notify your clients to be careful with this feature and use it only if they are 100% sure that emails from a certain sender are safe.
6. Implement a quarantine feature
Quarantine is a must-have feature for any secure email provider. Quarantine is storage for suspicious or threatening emails. Common users don’t have access to this place — only administrators do. You can ensure different types of quarantine for different email threat types: viruses, phishing emails, spam, etc.
Why would your client want a feature like this? Why not just reject all those emails? Organizations might need to get access to suspicious emails in case they were sent to quarantine by mistake or to restore those suspicious emails and send them to recipients. Here are a few examples of situations in which IT administrators may take emails out of quarantine:
- Businesses know for sure that a certain email that was automatically filtered by file type is not a threat. For example, say one employee sends a Microsoft Word document to another. The employee must be certain that the information the file contains is safe.
- Any non-spam/phishing email sent to quarantine based on keywords or any other cause. In this case, an employee can ask the administrator to find the necessary email and restore it from quarantine.
- Use virus files from emails for improving antivirus databases.
- Use phishing emails for anti-phishing training.
- Emails were sent to quarantine by a program bug. In this case, your development team should fix the issue, and an administrator should release the emails from quarantine.
7. Add email encryption functionality
Sometimes, it may be necessary for users to send an email which can’t be read by anyone except the intended recipient.
For example, suppose a user needs to send another employee confidential or sensitive information. They are aware that an email containing this information could be seen by other people. That’s why they want advanced security.
To help your clients protect their sensitive data in emails, offer the ability to encrypt them. With encryption functionality, a user can choose an encryption option when sending an email, and the recipient can open the email using one of the following methods:
- Enter an additional password
- Use a private security key
- Use a hardware key (FIDO2 or Google Titan)
- Use a code from multi-factor authentication, such as from an SMS
Encryption can protect emails from being read by anyone except the intended recipient even if the emails are intercepted.
8. Help your clients maintain a high domain and IP reputation
An organization’s domain reputation is like a credit score for their sending email domain. To improve the user experience with your services, consider helping your clients maintain this reputation at a high level.
Domain reputation isn’t an absolute value that is the same for all email service providers. Every provider has their own domain reputation rating. For example, a domain can have the best reputation according to Gmail but a medium reputation according to Outlook.
Email service providers can calculate domain reputation in different ways, but the most common way is by evaluating it on a scale of 0 to 100. The closer to 100 a domain’s score is, the more receiving email servers will trust emails sent from the particular business domain. And the closer to zero the domain score is, the more likely an email sent from this domain will go to spam.
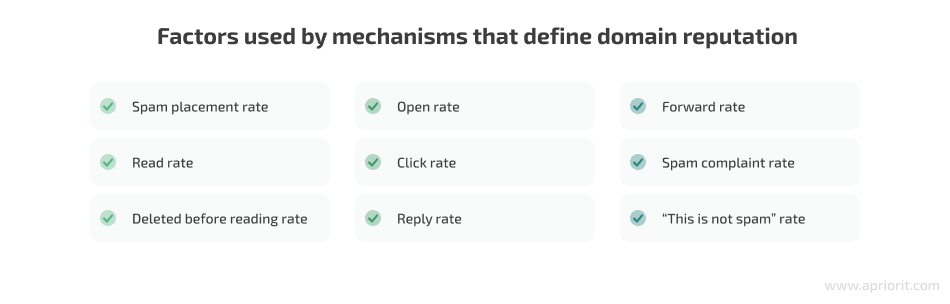
Every email service provider has their own mechanism to determine domain reputation. These mechanisms can have different reputation calculation algorithms, but they are usually based on the same factors such as open rate, click rate, etc.
The reputation of a sender’s IP address is also part of the domain reputation. Email servers which send emails using a certain domain get the same reputation as the emails they send.
For example, say all example.com emails are sent from the server with the IP address 11.22.33.44. If the example.com email domain has a Neutral reputation, then the 11.22.33.44 IP address has a Neutral reputation too. If the email server changes its IP, it can change the domain’s reputation too.
Here are a few practices for keeping your business email domain reputation clean:
- Use more than one email server. Offer your clients a cluster of email servers which can send emails with the same domain. In this case, every server will have its own reputation because it has a unique IP address. The low reputation of one server doesn’t mean that all other servers’ reputations will be low.
- Ensure proper email authentication. We already discussed the benefits email authentication methods like DKIM, SPF, and DMARC bring to security. But if they are configured for a business domain, they also keep the domain’s reputation higher. Therefore, emails sent from that domain will less often be filtered out by reputation or spam filters.
- Determine the sender server’s geolocation. Every IP address has a geolocation which can be easily found. Use this information for email filtering. For example, an email service provider can have an email statistics feature that shows the percentage of emails from different geolocations which are rejected or sent to quarantine. Thus, you can find which countries or regions send a lot of junk emails. Then, you can configure filtering conditions based on this information.
Conclusion
All the features of email security discussed above can help your clients protect employees from most email-based threats. By enhancing your email service with top-notch security features and promoting best practices to ensure email security, you can keep your product competitive on the market and trusted by clients.
Improving the protection of your service is a never-ending process, since threat actors constantly adapt to security features and find new ways to overcome them. To be ahead of cyber criminals, make sure to continuously enhance your email service solution. Apriorit engineers have experience in the development, configuration, and testing of various communication services, including ones for email.
If you want to develop a highly protected web solution or improve the security of an existing solution, contact us!




