Key takeaways:
- Blockchain-based identity verification can fix issues inherent to traditional access management: centralized databases with sensitive records, the need for manual verification, data oversharing, etc.
- Thanks to its decentralized nature, blockchain can reduce the cost of identity verification, improve the user experience, and enhance user data security.
- There are a variety of blockchain approaches and tools to implement identity verification, designed for simple to complex use cases and varying security requirements.
- Companies that need specific business integrations and require total control over data often choose to build custom blockchain solutions for identity management.
Traditional identity verification comes with a lot of hidden risks: oversharing of sensitive data, security vulnerabilities from centralized data stores, and the operational burden of repeating the same verification processes for every interaction.
Blockchain-based identity verification offers a fundamentally different approach. It results in faster onboarding, reduced operational costs, enhanced security, and a user experience that doesn’t force customers to surrender their privacy for access.
This article breaks down how blockchain verification works in practice, how your business can benefit from it, and when you should choose a custom solution over ready-made tools. It will be useful for cybersecurity leaders who are looking for ways to make their identification processes more efficient while remaining secure.
Contents:
- Why use blockchain for identity verification?
- Business use cases for blockchain-based verification
- Tools for blockchain-based identity verification
- How does blockchain identity verification work?
- When to develop a custom blockchain identity verification tool
- How can Apriorit help you develop a blockchain identity verification tool?
- Conclusion
Why use blockchain for identity verification?
Identity verification is one of the cornerstones of online interactions, whether between service providers and consumers, employers and employees, or governments and citizens. Users expect to provide logins, passwords, documents, and even biometric data in order to access services or interact with institutions.
However, this everyday action comes with critical cybersecurity issues, IT overhead, and end-user frustration.
Data used for identity verification is often stored in a centralized database, which is a magnet for malicious activity. Securely storing and managing such data is a continuous challenge for cybersecurity experts, who have to balance new protection mechanisms with database performance. Some services, like banking or e-voting, may require manual checks of data submitted by users, which can take hours or even days. Errors during identity verification can lead to either access denial for legitimate users or unauthorized access for those who should be denied.
How does blockchain fix these issues?
As a decentralized technology, blockchain simply doesn’t have these issues. For example, a blockchain does not contain a single database with sensitive user data waiting for a breach — instead, identity data is distributed across the blockchain network. Meanwhile, access to this data and to the identity verification process is instantaneous.
Implementing blockchain for digital identity verification provides these benefits:

Enhanced security. Blockchain eliminates the need to store a complete copy of a user’s personal data in a centralized repository. Instead, data remains with the user and is transmitted only with their consent. Moreover, each interaction with user data is confirmed by a digital signature, making forgery impossible. There’s also the possibility of selective data disclosure so that a user can choose which private records they want to share.
For example, if a healthcare provider needs to confirm a patient’s vaccination record, the patient can choose to share only relevant records instead of their entire medical history.
Reduced chance of fraud and falsification. Identity verification using blockchain is based on cryptographic verification methods, and each identifier is unique and linked to a real person. In this way, blockchain makes it extremely difficult to create fake documents, open multiple accounts under one person’s name, and use stolen data to access services.
Cost-effective verification. Traditional identity verification processes often take too much of security professionals’ time, strain company infrastructure, and require additional storage. Blockchain allows companies to avoid repeated verification requests. Companies can accept verifiable credentials (VCs) issued by trusted participants and use them repeatedly for as long as they are valid.
For example, a bank that has implemented blockchain identity verification can accept KYC verification results from another financial institution, cutting customer onboarding costs in half.
Improved user experience. Fast registration, login, and verification without endless forms and repeated document uploads is a direct path to increasing customer loyalty. Blockchain can enable one-click onboarding for users, immediately providing them with access to multiple platforms. It can also result in a lower dropout rate during registration, a higher conversion rate, and an improved UX.
Businesses can rely on blockchain for digital identity management in both internal processes and customer interactions. Let’s see how companies from different industries can leverage blockchain technology for identity verification.
Streamline your identity management with blockchain
Leverage Apriorit’s experience with blockchain technology to build, audit, and integrate a blockchain identity solution into your workflow.
Business use cases for blockchain-based verification
Blockchain-based identity verification delivers the most value in processes where traditional systems create bottlenecks, security vulnerabilities, or unnecessary friction. Understanding these specific applications will help technical leaders identify where implementation will yield the greatest returns.
Despite differences in architecture and application, all blockchain-based identity verification solutions share a common goal — to create a reliable, private, and portable digital identity. Blockchains can be used across various domains, from online banking and travel to voting and medical records.
Cases where blockchain-based verification is efficient include:
- Simplified access management. Midsize and large companies manage credentials for thousands of employees, clients, and vendors. Hundreds of thousands of identity verification requests create a heavy load on corporate systems and risk data exposure. With blockchain-based access, a company can issue verifiable credentials for all users and entities with which it interacts. As a result, the verification process becomes simpler, sensitive data is cryptographically protected, and access can be revoked with one click when someone leaves or changes roles.
- Optimized government services. When citizens interact with multiple government agencies, they must repeatedly prove their identity and eligibility for services. A blockchain-based digital identity allows citizens to verify once with a trusted authority, then reuse that credential across agencies. This way, a blockchain helps to avoid manual documentation checks, reduces waiting time, and eliminates clerical errors.
- Streamlined supply chain and partner verification. Verifying supplier certifications, insurance coverage, and compliance statuses traditionally requires reviewing stacks of documents. Blockchain systems enable partners to maintain verified credentials that can be instantly validated before contracts are signed or system access is granted.
- Safe age verification. When businesses selling age-restricted products and services need to verify a user’s age, they are forced to store and process information in compliance with cybersecurity laws and regulations. Users are often forced to share documents that confirm their age or disclose additional information like their birth date. Blockchain verification with selective disclosure allows customers to prove they meet age or other requirements without revealing unnecessary personal information. As a result, a company can receive cryptographic proof of eligibility while minimizing data breach risks.
- Reliable customer due diligence and compliance. For regulated businesses, KYC and AML checks lead to duplicated effort and customer frustration. Blockchain allows customers verified by one institution to present their credentials to other institutions without disclosing personal data. Businesses can then receive automatic notifications when credentials are revoked or updated. As a result, audit trails become simplified, immutable, and transparent.
- Secure patient data sharing. Transferring patients, confirming their insurance coverage, and handling healthcare information remain challenging due to privacy concerns and interoperability issues. Blockchain-based credentials allow patients to share their medical records, vaccination statuses, or insurance eligibility with new providers while maintaining control over their complete medical history. And healthcare organizations don’t have to handle that data.
These use cases demonstrate that blockchain-based verification isn’t just a theoretical concept — it solves business problems across many industries. Depending on the use case and target level of blockchain integration, businesses can choose different identity verification tools. Let’s take a look at the key identity verification options, their pros and cons, and examples of how they work in practice.
Read also
How Much Does Blockchain App Development Cost? A Detailed Overview
Get an accurate estimate of the cost to build your blockchain app. Learn about cost factors and how to optimize your project without sacrificing quality.

Tools for blockchain-based identity verification
Blockchain enables many ways of verifying users. In this article, we’ll focus on three options:
- Decentralized identifier (DID)
- Verifiable credential (VC)
- Zero-knowledge proof
You can use these independently or combine them in one identity verification system. Let’s see how they work and complement each other.
Decentralized identifier
A decentralized identifier, or DID, is a unique, verifiable identifier that doesn’t depend on a centralized registry. Unlike traditional IDs such as email, username, or passport number, a DID can be created and managed directly by the user. And it’s recorded on a blockchain, allowing third parties to verify its authenticity without involving a centralized intermediary.
The key idea behind DID is that users own their digital identity and can share it with others without revealing unnecessary information.
Each DID is linked to a specific set of credentials or verifiable claims, such as a person’s age, driver’s license, or affiliation with a particular organization. These credentials can be issued by trusted entities and then used to verify a user’s eligibility or status without the user needing to repeatedly provide documents.
Verifiable credential
A verifiable credential, or VC, is a digital record signed by a trusted issuer that confirms a specific fact about a person (age, citizenship, possession of a diploma or professional license, etc.). Any party can ensure that the credential was issued by a specific issuer and hasn’t been altered.
As with a DID, users can provide only part of the information from a VC without revealing other details. They can also reissue a VC or transfer it to a new user account in case they lose access to the old account.
Verifiable credentials can be paired with decentralized identifiers to make blockchain identity verification more convenient for users. In the classic DID model without VC, losing a private key essentially means losing the identity associated with it. Verifiable credentials fix this issue by:
- Storing user data in a secure backup repository — for example, encrypted in the cloud or on a hardware device. This way, even if a user loses their VC, they can regain access to their gain access to certifications without contacting the trusted authorities who issued them.
- A trusted authority can reissue credentials to a new DID after conducting an identity recovery procedure. This process is similar to restoring access to a banking account. It allows users to regain their access privileges without requesting new access approval.
- VC ownership is protected with the corresponding private key. Even if an attacker obtains a VC, they won’t be able to use it without confirming ownership.
Zero-knowledge proof (ZKP)
Zero-proof knowledge, or ZKP, allows users to prove certain information without revealing the information itself. It’s based on complex mathematical algorithms that transform a statement requiring proof into a mathematical problem.
For example, say a user requests access to an age-restricted online platform. The user has a verified digital credential with their birth date from a trusted issuer, such as a government agency.
The platform requests proof that (current_date – user_birth_date) >= 18 years.
The user’s mobile application or digital wallet uses data from the VC as a private input parameter, or a witness. This parameter is fed into an arithmetic circuit that implements the age verification logic. The app then generates zero-proof knowledge (ZPK), which the user can send to the platform.
With this information, the online platform can verify the proof of age using the issuer’s public key. If the user is of age, the system confirms that the user meets the age requirement and grants access.
Meanwhile, the user’s exact birth date remains hidden from the platform.
ZKP enables maximum privacy while allowing organizations to reliably verify information about users users. Combined with DID, this technology creates conditions where users not only retain control over their data but also minimize the risk of data leaks or misuse.
As you can see, you can use several methods of blockchain-based user identity verification for different verification goals. In the next section, we break down a combination of DID, VC, and ZKP from the standpoint of a company that needs to verify a user before providing a service.
Read also
Comparison of Identity and Access Management Services: Building an On-premises Solution vs a Cloud-Hosted Solution
See how the best IAM tools stack up across security, usability, and integration criteria. Get actionable insights to strengthen identity management and safeguard enterprise data.

How does blockchain identity verification work?
Let’s see how blockchain identity verification works in a practical use case. For our example, let’s imagine that an airline has to check if a passenger has a valid passport for international travel.
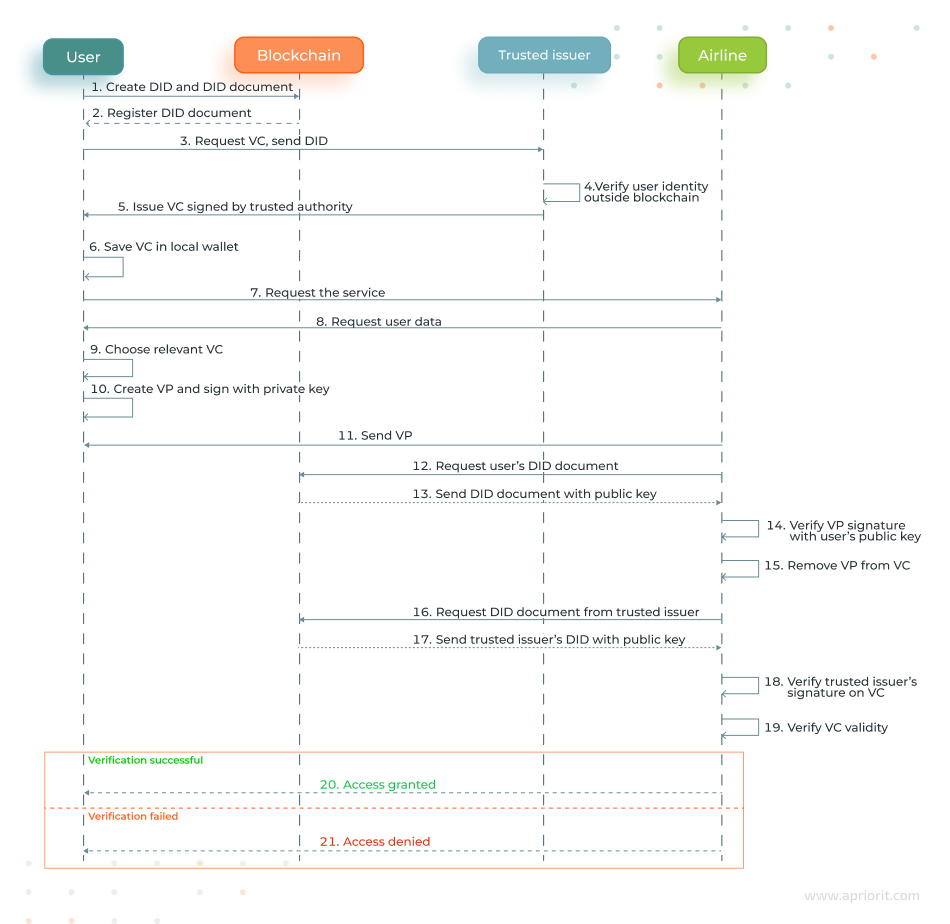
Let’s review the complete blockchain identity verification lifecycle, from creating an identifier to passing verification with the airline.
Stage 1. Creating a digital identity
- The user creates a unique DID and publishes it on the blockchain. This identifier is linked to a DID document containing the user’s public key and authentication methods.
- The user approaches an issuer (for example, a government agency or university) and requests a verifiable credential.
- After identity verification, which typically happens off-chain, the issuer creates a VC signed with their private key. The VC states, for example, that the user is of legal age, has a diploma, is unmarried, etc.
- The user stores the received VC in their digital wallet.
Stage 2. Passing verification by the airline
- The user attempts to check in for a flight.
- The airline requests confirmation of certain data (for example, the user’s age, visa status, and vaccination status).
- The user selects the necessary VCs and forms a verifiable presentation (VP) signed with their private key that proves they own the selected VCs.
- The user sends the VP to the airline for verification.
- The airline extracts the user’s DID from the VP, retrieves the user’s public key from the blockchain, and verifies the VP signature.
- The airline extracts the issuer’s DID from the VC, retrieves the issuer’s public key, and verifies the authenticity of the VC.
- The airline can also verify whether the VC has expired or been revoked.
If all checks pass, the airline lets the user check in for the flight. Otherwise, they deny access.
For the end user, the verification process seems automated and takes seconds to complete. The airline can obtain all necessary information to provide services without processing or storing the user’s sensitive data.
Read also
Blockchain Attack Vectors: Main Vulnerabilities of Blockchain Technology
Explore the most common blockchain attack vectors and learn how to secure decentralized systems against evolving threats and vulnerabilities.

When does developing a custom blockchain identity verification tool make sense?
The idea of using blockchain for identity verification isn’t new. There are a lot of solutions for blockchain identity verification on the market that aim to reimagine the approach to digital identity.
However, some organizations choose to develop custom blockchain-based identity verification systems. Here are the key criteria for choosing between a commercial and a custom solution:
| Criterion | Commercial solution | Custom solution |
|---|---|---|
| Time to market is critical | ✔️ | ❌ |
| Data protection and total data control are a must | ❌ | ✔️ |
| Solution must integrate with customized and unique business processes | ❌ | ✔️ |
| Business needs affordable identification solution quickly | ✔️ | ❌ |
| Reliable verification is critical | ❌ | ✔️ |
Strategic success comes from implementing innovative verification approaches that align with your business needs, scale, and growth trajectory. For most companies, a hybrid approach works best: launch quickly with an off-the-shelf solution, then migrate to a custom implementation as your requirements evolve and your business scales.
Companies that choose to develop custom blockchain-based identity verification software usually prioritize cybersecurity and need a reliable tool for internal verification for employees, vendors, and clients. In this case, they act both as the trusted issuer that provides users with VCs and as the verifier.
Developing, integrating, and maintaining a custom system can be challenging for companies that have little experience with this type of blockchain application. That’s why it’s best to outsource this task to a team that has already delivered solutions of the type that you need.
How can Apriorit help you develop a blockchain identity verification tool?
Building products for cybersecurity and data protection is our core expertise at Apriorit. Over the past seven years, we have worked with blockchain technology to help clients build secure solutions for exchanging and protecting data. From blockchain-based asset management to international banking infrastructure, we’ve done it all.
Clients trust us with their projects because we have proven expertise in:
- Cybersecurity development. Apriorit specializes in building custom tools for data, network, and endpoint security. We take into account cybersecurity compliance requirements that are relevant for your product as well as development best practices to deliver software that is protected even from the most advanced threats.
- Blockchain development. Our engineers will select a suitable blockchain and network protocols, then design smart contracts tailored to your specific needs and business processes. We’ll build you a blockchain system that is fast, resource-efficient, and secure.
- Smart contract auditing. Blockchain-based identity verification is built on smart contracts, which have to be well-designed and well-executed. We’ll help you analyze the security and behavior of your existing contracts. As the result of an Apriorit audit, you’ll get a comprehensive security analysis and clear steps for improving your smart contracts.
With this skill set, we can be your one-stop shop for any blockchain development project, helping you focus on business goals while we build technical solutions.
Conclusion
Blockchain provides companies with a revolutionary method for verifying users’ identities. It solves many challenges of traditional verification, eliminating long waits and manual checks, the need to store and process sensitive data, and data oversharing. A combination of decentralized identifiers, verifiable credentials, and zero-knowledge proofs creates a framework in which users control their identity while businesses gain cryptographic certainty.
Apriorit helps companies build custom identity verification systems that are resource-efficient, secure, and integrated with specific solutions. Whether you want to secure access to established corporate services or build a new product with strict security requirements, we are here to help.
Looking for a cybersecurity development partner?
Leverage Apriorit’s experience in this niche to ensure instant, secure, and convenient access for your users.
FAQ
How does blockchain impact identity verification?
<p>Blockchain offers a decentralized and transparent approach to verifying identities. It eliminates the need for centralized storage of user data, constant re-validation of provided credentials, and oversharing of sensitive data by users.</p>
<p>Smart contracts enable users to securely store and share their sensitive data selectively, ensuring that data is only provided with explicit user consent.</p>
Where can I use blockchain for identity verification?
You can use a blockchain for any process that requires user identity verification: KYC processes, online transactions, voting systems, access to corporate resources, etc. This technology enables instant, low-cost identity verification without the need for centralized data storage.
Are there different blockchain platforms for identity verification?
Yes, multiple blockchain platforms — Ethereum, Hyperledger, and Tezos, to name a few — offer identity verification solutions. These platforms differ in terms of performance, scalability, available privacy controls, customization capabilities, and transaction costs. The best choice of platform depends on your use case and verification requirements.
How does blockchain ensure privacy and comply with regulations like the GDPR?
<p>Blockchain addresses privacy and regulatory compliance through a hybrid approach. Sensitive personal information is stored off-chain in secure databases, while the blockchain contains only cryptographic proofs that verify the authenticity of data without exposing the data itself.</p>
<p>This design facilitates the GDPR’s right to be forgotten. Since blockchain data is immutable, storing only cryptographic proofs allows organizations to delete off-chain personal information upon request while maintaining the blockchain’s integrity. </p>
What are the challenges and limitations of using blockchain for identity verification?
Key limitations include:</p>
<ul class=apriorit-list-markers-green>
<li>Scalability, as many blockchain networks struggle to process high transaction volumes quickly and cost-effectively</li>
<li>A steep learning curve, with complex user interfaces that can deter widespread adoption among non-technical users</li>
<li>Regulatory uncertainty, as many jurisdictions lack comprehensive legal frameworks governing blockchain-based identities</li>
</ul>
<p>We can help you address these challenges by thoroughly researching compliance requirements, choosing the best blockchain platform, carefully designing smart contracts, and assigning a team of blockchain experts with practical development skills.</p>



