Key takeaways:
- Although a multi-cloud infrastructure lets businesses choose only the best services from different providers, it also expands the attack surface.
- A properly secured multi-cloud environment ensures consistent monitoring and resilience across your business infrastructure.
- To secure multi-cloud infrastructure, your team must be ready to address challenges such as cloud misconfiguration, compliance complexity, and integration issues.
- Best practices including a zero-trust approach and strong identity and access management can effectively protect your multi-cloud environment.
- An experienced vendor can help you maximize the security of a multi-cloud environment, including through AI-based threat detection and response or post-quantum cryptography.
Multi-cloud environments allow businesses to skim the cream, taking advantage of the distinct strengths and best services of different cloud providers. Yet using services from multiple clouds requires a definite effort to design and manage secure infrastructure as the number of workloads constantly increases.
Diverse midsize and large entities, from SaaS providers to FinTech and telecom companies, often adopt multi-cloud when they need to:
- Meet region-specific compliance rules
- Guarantee the stability of critical systems
- Integrate different cloud environments when merging businesses
- Minimize latency by deploying their apps and services closer to users
- Use ready environments to get rapid access to advanced technologies
Are these goals worth the security challenges multi-cloud environments bring? If your team can ensure robust protection, then yes.
In this article, we explore multi-cloud security challenges and give you insights on how to implement multi-cloud security effectively. You’ll also find out what trends exist to enhance cross-cloud protection.
This article will be useful for technical leaders and cloud architects looking for ways to fortify their multi-cloud infrastructure or boost its protection.
Contents:
- What is multi-cloud security, and why is it important?
- What are the challenges of establishing multi-cloud security?
- What are the best practices for multi-cloud security?
- Overview of multi-cloud security tools
- Multi-cloud security trends
- How Apriorit can help you secure multi-cloud infrastructure
- Conclusion
What is multi-cloud security, and why is it important?
A multi-cloud approach involves using cloud services from two or more cloud providers to manage applications and resources, as if they were part of a single cloud. This approach allows you to choose the best-fitting services for your infrastructure while avoiding vendor lock-in and optimizing costs.
However, running a resilient and robust multi-cloud infrastructure requires maintaining consistent security across clouds. According to the 2024 State of Multicloud Security Report by Microsoft, an average organization that has adopted a multi-cloud strategy has 351 exploitable attack paths and faces, on average, 59 data security incidents annually. The main sources of these vulnerabilities are internet exposure and insecure credentials.
Ensuring multi-cloud security means applying different best practices and technologies to protect apps, data, and workloads in multi-cloud environments. To provide comprehensive cross-cloud protection, it’s essential to consider the following when planning your security strategy:
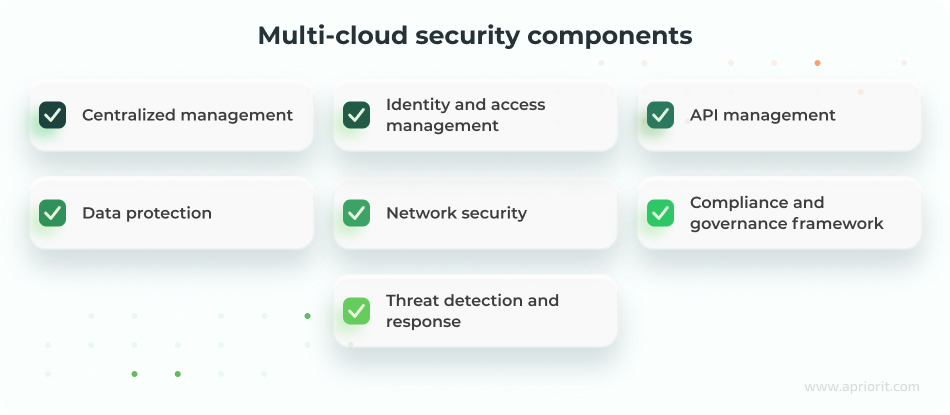
With a properly secured and configured multi-cloud infrastructure, your business can count on the following advantages:
- Unified visibility and consistent monitoring. A centralized view across all cloud environments helps your security team to effectively manage security by analyzing events and system performance holistically.
- Consistent security policy enforcement. Ensuring coherent security policies across the whole infrastructure lets you minimize vulnerabilities caused by inconsistent configurations and policy gaps due to the diverse nature of cloud environments.
- Business continuity and resilience. Security policies spread across a multi-cloud infrastructure enable business continuity if one cloud provider fails, while automated cross-cloud backups guarantee prompt recovery from cloud-specific outages or cyber attacks.
- Enhanced incident response. Centralized multi-cloud security lets your team speed up breach detection, investigation, and remediation across various clouds.
Establishing multi-cloud security requires significant effort to address the range of challenges associated with heterogeneous cloud environments. In the next section, we outline the main challenges of securing a multi-cloud infrastructure.
Looking to bring your multi-cloud security to the highest level?
Let Apriorit specialists improve the security of your multi-cloud environment using our vast experience in cybersecurity and cloud computing.
What are the challenges of establishing multi-cloud security?
When securing multi-cloud infrastructure, your team should be ready to address various challenges. Below, we list the eight most common challenges of safeguarding multi-clouds:
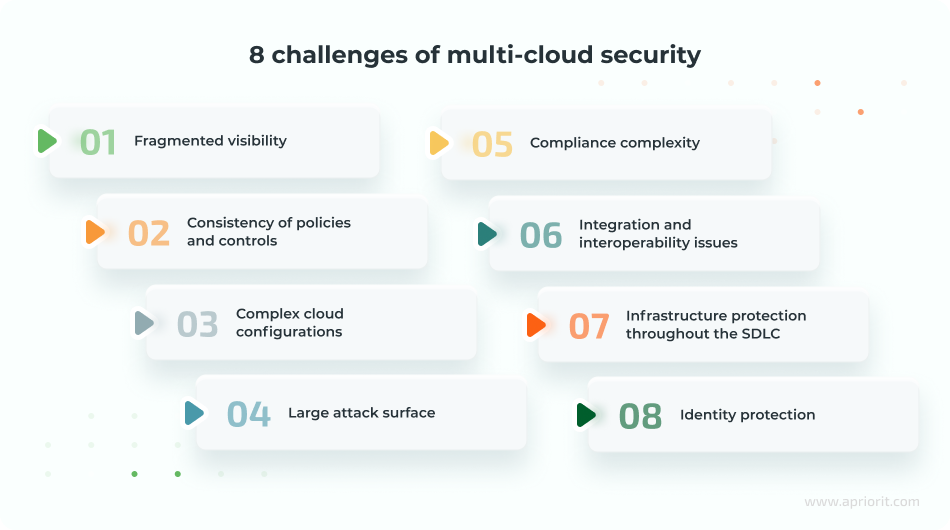
1. Fragmented visibility. Each cloud platform has its own monitoring tools, logs, and interfaces. However, these cloud-native tools are not designed to work together to provide a holistic picture of events across the entire infrastructure. The result is monitoring blind spots, delayed incident response, and obstacles to root cause analysis.
To avoid monitoring fragmentation, consider deploying a unified monitoring platform that will consolidate telemetry across the whole multi-cloud infrastructure.
2. Consistency of policies and controls. Security configurations can vary widely between cloud providers. For example, cloud providers may apply different network rules or encryption methods. Such inconsistencies may lead to security risks, including unauthorized access or data breaches.
To mitigate these risks, you can use tools that operate across different cloud environments to standardize encryption or access controls.
3. Complex cloud configurations. The rapid evolution of cloud services and differences in security models complicate the management of configurations across multiple cloud providers. Reasons for misconfigurations include human errors, misunderstanding of the shared responsibility model, constant changes and updates to services from cloud providers, and manual processes.
Automating configuration management and compliance checks will help you avoid these risks and effectively secure your multi-cloud environment.
“We use a cloud security posture management tool to control cloud configurations and identity access. Cloud vendors usually provide built-in tools, but when you need to manage several clouds, it’s better to use an external tool that is all-in-one.”
Ivan, Web Development Team Development Coordinator at Apriorit
4. Large attack surface. Using several cloud platforms (each with its own configurations, APIs, and identities) significantly increases the number of entry points, vulnerabilities, and attack vectors.
To manage all of these and prevent (or at least decrease) the risk of security incidents, it’s important to implement cross-cloud risk assessments and standardized policies, perform regular security and penetration testing, and use AI-based threat protection tools.
5. Compliance complexity. Different cloud providers adhere to different legal, regulatory, and industry-specific requirements. Organizations must meet various compliance requirements such as the GDPR, HIPAA, PCI-DSS, and regional data sovereignty laws depending on the cloud provider’s location, workload residency, and type of data or service.
Implementing automated compliance checks to validate cloud configurations against compliance standards will help you reduce manual errors and speed up remediation.
6. Integration and interoperability issues. An efficient multi-cloud strategy depends on the harmonious interaction of services from various cloud providers. To effectively manage and secure a multi-cloud infrastructure, it’s essential to resolve various integration and interoperability issues between platforms. These include use of proprietary APIs and protocols, poor data synchronization, app incompatibility, and differences in networking protocols.
Adopting middleware solutions, containers and orchestration tools, and standardized APIs and protocols will ensure seamless and secure communication and data exchange among different cloud platforms.
7. Infrastructure protection throughout the SDLC. Since attackers can exploit vulnerabilities at different stages of the development lifecycle, you need to ensure the security of your multi-cloud infrastructure from design through maintenance.
Adhering to secure SDLC principles allows for adopting security best practices throughout the infrastructure development lifecycle, enabling early detection and mitigation of vulnerabilities.
8. Identity protection. Fragmented identity and access management (IAM), identities with excessive permissions, and poor monitoring of workload identities (especially inactive ones) increase the attack surface and make such identities an attractive target for attackers.
You can address this risk by implementing unified IAM solutions that aggregate identities across multiple clouds and enable consistent policy enforcement and streamlined identity lifecycle management.
To overcome these challenges without significant complications that might affect your infrastructure, you can apply multi-cloud security best practices. Let’s explore them.
Read also
Multi-Cloud Computing: Use Cases, Pros, and Cons for Enterprises
All you need to know about multi-clouds: benefits, challenges, adoption strategies, and preparation tips.

What are the best practices for multi-cloud security?
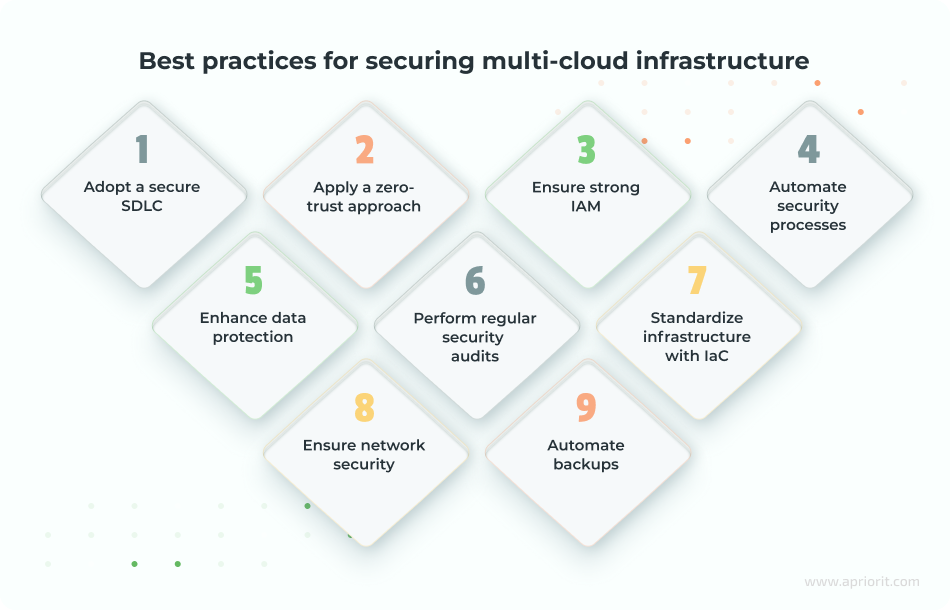
1. Adopt a secure SDLC
Following the principles of a secure SDLC means prioritizing security at every stage of the software development process. This involves:
- Eliciting security requirements and identifying security risks before launching the project
- Applying secure coding guidelines
- Continuous integration and testing
- Threat modelling
- Penetration testing
- Secure configurations and deployment
This approach helps you detect vulnerabilities early and proactively address security risks throughout the infrastructure development lifecycle.
2. Apply a zero-trust approach
Multi-cloud increases the attack surface, and a zero-trust approach can help you handle this by requiring regular identity verification and authorization when accessing resources both inside and outside the perimeter.
To secure a multi-cloud infrastructure, you can implement the following zero-trust principles:
- Least privilege access to limit user and system access strictly to those resources that are necessary to perform tasks
- Continuous verification of security configurations for every user and device before granting access to apps and data
- Never trust, always verify to prevent granting access automatically based on a user’s location
- Micro-segmentation of the network and workloads into smaller isolated zones to limit lateral movement by attackers if one segment is breached
3. Ensure strong IAM
Running a multi-cloud infrastructure means managing more identities. When attackers increasingly target credentials, tokens, and API keys, robust identity and access management becomes paramount.
Aspects of IAM can involve:
- Adaptive multi-factor authentication, which allows for evaluating multiple contextual factors (such as user behavior, location, device type, time of access, role-based factors) and determining additional authentication factors, if required
- Role-based access control to restrict access to cloud infrastructure based on user roles within an organization, ensuring that users only have the permissions necessary for their job functions
- Machine identity control to avoid permanent privileges for machine identities, implement automated key rotation, and manage the lifecycle of every workload
- Federated authentication so that users can access a multi-cloud environment with a single set of credentials that enhances security by centralizing authentication and enforcing consistent policies
“It often happens that no one monitors access to the infrastructure, and when a person resigns, their account isn’t deleted, and access is still available. We avert such cases by using tracking software that monitors users’ activity. It validates access tokens and alerts if it detects invalid ones.”
Ivan, Web Development Team Development Coordinator at Apriorit
4. Automate security processes
We strongly advise automating processes such as security policy enforcement, security scans, and compliance checks. This can help your security team detect vulnerabilities earlier, take remediation actions faster, and decrease the number of manual security tasks.
To enhance the security of multi-cloud infrastructure through automation, you can apply the following approaches:
- Security-as-code to embed security policies into code and automation scripts that configure cloud environments, ensuring uniform security controls. This allows for integrating security early in development, automating security checks, and enabling repeatable security configurations.
- Automating CI/CD pipeline scanning, which involves continuous security testing of source code, dependencies, container images, infrastructure as code (IaC) templates, and runtime environments whenever code is committed and in order to detect issues before deployment.
- Continuous monitoring to detect configuration drift and remediate it automatically by enforcing the desired infrastructure state.
5. Enhance data protection
Distributing sensitive information across multiple cloud platforms increases the risk of data breaches and non-compliance with the GDPR, HIPAA, PCI DSS, and other legal and regulatory requirements.
Adopting the following encryption and protection mechanisms helps you prevent such security incidents:
- Strong encryption algorithms, such as AES-256 and TLS, to encrypt data at rest and in transit
- Centralized key management to ensure consistent cryptographic key policies, rotation, and revocation across all clouds
- Data classification to label data according to sensitivity and ensure stronger protection (stronger encryption or stricter access) for sensitive data
6. Perform regular security audits
You can achieve continuous security auditing of your multi-cloud infrastructure through integrating automated reporting into DevOps workflows. Automated reporting lets you generate, update, and distribute security posture reports as part of CI/CD pipelines across the whole infrastructure.
These reports may cover:
- Results of security scans
- Compliance status
- IAM roles or permissions audits
- Drift from the desired configuration
7. Standardize infrastructure with IaC
Standardizing through IaC involves using common modules, naming, policies, folder structures, and tools so that infrastructure in different clouds behaves the same way. It’s also possible to include security best practices and compliance requirements in IaC scripts, ensuring that all infrastructure is configured securely from the beginning and reducing the risk of misconfigurations.
Best practices for integrating IaC into multi-cloud infrastructure include:
- Using a cloud-agnostic IaC tool that supports multiple cloud providers so that much of the IaC code can be shared or adapted
- Modularizing code — breaking down your infrastructure into reusable modules that can be deployed in multiple clouds — to reduce the duplication of code and improve maintainability
- Integrating IaC with a CI/CD pipeline to automate deployment and testing of infrastructure changes
8. Ensure network security
Diverse networking models, APIs, and services create more entry points for attackers. Without strong network security, a single misconfigured firewall rule or open port in any cloud can expose the whole multi-cloud environment. Implementing consistent policies across clouds can ensure robust network security.
Key network security mechanisms include:
- Using tools for centralized application of firewall rules to new or changed resources across all cloud environments
- Defining network policies, firewalls, routing, and segmentation in IaC templates to apply them consistently across clouds
- Securing communication channels between clouds through VPN or private links
- Performing regular audits of network security postures, rules, and configurations
9. Automate backups
Automation allows you to standardize how backups are scheduled, stored, and validated, ensuring no gaps or inconsistencies, minimizing human errors, and guaranteeing that data is always available, even if one provider is down.
To implement effective cross-cloud backup, you can:
- Use IaC for consistent, reproducible backup configurations across multiple clouds
- Use backup solutions supporting multiple clouds to increase redundancy and avoid vendor lock-in
- Align backup automation with disaster recovery to enable fast recovery of a multi-cloud environment
Securing multi-cloud infrastructure also requires choosing the right technology stack. In the next section, we briefly overview tools you can use for securing your multi-cloud.
Read also
Cloud Application Security Best Practices: Data Safety and IT Compliance Challenges
Explore how to safeguard sensitive information in the cloud from unauthorized access, data breaches, and other cyber threats.

Overview of multi-cloud security tools
When it comes to safeguarding your multi-cloud infrastructure in practice, choosing the technology stack can be challenging.
The best choice of tools depends on the specifics and complexity of your multi-cloud infrastructure. Also, your team must keep in mind which tools are compatible with which cloud platforms.
Below, we offer a list of commonly used tools. For convenience, we have grouped them according to the tasks they help you accomplish to establish multi-cloud security:
Table 1. Multi-cloud security tools
| Task | Tools |
|---|---|
| Configure IAM module | Okta, Auth0, Microsoft Entra ID, AWS IAM, Google Cloud IAM, Keycloak |
| Enhance network security | Zscaler, Prisma Access (Palo Alto Networks), Cisco Umbrella, Cloudflare Zero Trust, Aviatrix |
| Ensure data protection | AWS KMS, Azure Key Vault, GCP KMS, HashiCorp Vault, Thales CipherTrust, Fortanix |
| Manage compliance and posture | AWS Security Hub, Azure Security Center, GCP Security Command Center, Prisma Cloud (Palo Alto Networks), Check Point CloudGuard, Wiz, Open Policy Agent (OPA), Kyverno (for Kubernetes) |
| Detect threats and manage vulnerabilities | Tenable.io, Qualys, Rapid7, CrowdStrike Falcon, SentinelOne, Microsoft Defender for Cloud, Wiz, Orca Security, Prisma Cloud (Palo Alto Networks) |
| Integrate IaC and automation | Terraform, Ansible, Pulumi, Checkov, TFSec, Kics |
Multi-cloud security trends
The desire to enhance security motivates businesses to constantly search for better solutions and innovations. Here are promising trends that are likely to come in handy when enhancing multi-cloud security in the near future:
AI-driven threat detection and response. AI allows for dynamic analysis of vast, heterogeneous data from multiple clouds, identifying unusual patterns or user behaviors that may indicate threats. It also enables automated and rapid incident response, such as network isolation, which reduces response times compared to manual processes.
Quantum-resistant encryption. As quantum computing becomes more realistic, businesses are preparing for its broad adoption. Quantum-resistant algorithms aim to protect data against future threats of quantum computing attacks when quantum technology is widely used. Hybrid approaches let you combine classical and post-quantum cryptography algorithms in order to maintain system interoperability.
DevSecOps. Integrating secure development practices into DevOps ensures continuous, automated security throughout the development lifecycle. Moreover, incorporating DevSecOps lets you consistently enforce your security policy across all cloud platforms, reducing risks from misconfigurations.
Unified security platforms. These tools help businesses manage increasing multi-cloud complexity while maintaining a robust security posture. Instead of having separate security stacks per cloud, a unified security platform allows for enforcing consistent policy, visibility, threat detection and incident response, compliance, and identity controls throughout the whole multi-cloud environment.
Establishing multi-cloud security requires profound knowledge and expertise in different spheres, from cybersecurity and cloud computing to DevOps practices and AI technology. Engaging an experienced vendor can help your team effectively cope with all the challenges.
How Apriorit can help you secure multi-cloud infrastructure
With 20+ years of experience in cybersecurity and vast expertise in cloud computing, we can assist you with tasks including:
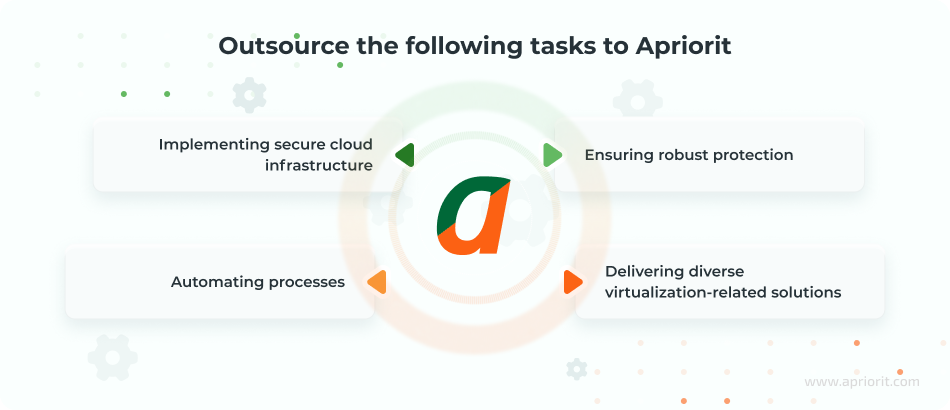
- Implementing secure cloud infrastructure, from single-cloud to multi-cloud, or improving existing infrastructure according to compliance requirements and security best practices
- Ensuring robust protection of your cloud infrastructure by adhering to secure SDLC principles
- Automating processes, from cloud vulnerability scanning to compliance checks, to ensure the consistent security and reliability of your cloud infrastructure
- Delivering diverse virtualization-related solutions, from desktop to network virtualization
Conclusion
Multi-cloud provides a significant advantage — it allows you to simultaneously use only the best and most suitable services of different cloud providers. However, it multiplies the risks of vulnerabilities, configuration drift, and non-compliance.
To protect your multi-cloud, you need to automate cross-cloud processes and implement robust IAM. It’s also crucial to perform regular security checks and ensure unified security management.
By outsourcing the safeguarding of your multi-cloud environment to Apriorit specialists, you will get a reliable multi-cloud infrastructure that complies with all relevant laws, regulations, and standards.
Looking for an experienced vendor in cybersecurity and cloud computing?
Apriorit experts will help you overcome the challenges and ensure a strong security posture for your multi-cloud.
FAQ
What are the benefits of adopting a multi-cloud environment?
Adopting a multi-cloud environment brings key benefits such as:
<ul class=apriorit-list-markers-green>
<li>No vendor lock-in</li>
<li>Improved resilience</li>
<li>Cost-efficiency</li>
<li>Access to unique services from multiple providers</li>
</ul>
What are the risks of inadequate multi-cloud security?
Risks of inadequate multi-cloud security include:
<ul class=apriorit-list-markers-green>
<li>Data breaches and data loss</li>
<li>Identity and access threats</li>
<li>Regulatory non-compliance</li>
<li>Configuration drift</li>
<li>Operational complexity</li>
</ul>
How often must we conduct a multi-cloud security audit?
The frequency of conducting multi-cloud security audits depends on compliance requirements. Audits should also be conducted following major changes in your cloud environment. We recommend combining scheduled audits (yearly or quarterly) with continuous automated monitoring to ensure a consistent security posture across all clouds.
How much does it cost to build a secure multi-cloud infrastructure?
<p>The cost depends on industry specifics and different factors, including the number of cloud providers and workloads; use of advanced technologies (AI, Kubernetes); the cost of security tools, team training, and certification; etc. We can give you a precise estimate of the resources required during the project discovery phase.</p>
<p>Contact the Apriorit sales team for more detailed information. Our specialists will prepare realistic estimates, considering the details of your business niche and your project’s complexity.</p>




