Key takeaways:
- Malicious actors are increasingly interested in sensitive data from FinTech apps. In January 2025, 87.5% of monitored financial services apps reported attacks.
- When planning your FinTech app security strategy, pay attention to common attack vectors, the rise of AI threats, and risks related to third-party APIs and open banking platforms.
- The most prominent cybersecurity practices for FinTech projects focus on minimizing access rights, enhancing data protection, verifying each access request, and implementing secure development practices.
- When gathering a FinTech development team, consider engaging an outsourcing vendor with both cybersecurity expertise and experience building scalable apps for banking and finance.
It’s hard for organizations to balance security, performance, and usability in mobile apps. And when the project involves financial services, the complexity increases due to higher hacking risks and strict compliance regulations.
However, developing a scalable, competitive, yet protected mobile app for finance and banking is possible. As a software development company with more than 20 years of experience, Apriorit knows how to handle mobile protection strategically, making an app secure by design and safeguarded against modern threats.
In this article, we share major security tips for protecting FinTech applications based on our experience in mobile development, cybersecurity, and security auditing.
Our recommendations apply to solutions for mobile banking (lending, money transferring, investments, InsurTech, budgeting, etc.), blockchain, and other financial and banking services. This article will be helpful for engineering and product leaders who want to strengthen app protection while maintaining compliance, performance, and the user experience.
Contents:
- Threats and vulnerabilities in FinTech mobile apps
- How to secure your FinTech mobile project
- 1. Stick to a zero trust approach
- 2. Secure the application runtime environment
- 3. Research and secure platform-specific vulnerabilities
- 4. Establish data security
- 5. Secure third-party integrations
- 6. Enable secure development practices
- Compliance and regulatory considerations for FinTech apps
- Enhance your FinTech app protection with Apriorit (+3 client success stories)
- Conclusion
Threats and vulnerabilities in FinTech mobile apps
You can’t consider your app and its environment safe by definition. Here are a few reasons why:
- A device that runs your application might be stolen or compromised
- Some of your users might be hackers in disguise with a rooted device
- A user might accidentally install root-access malware
- A user device can be infected with keyloggers or traffic sniffers
- A user may install a patched application version by trusting a phishing ad or email
According to the 2025 Application Security Threat Report, in January 2025, there was an 87.5% attack rate among all financial services apps surveyed by Digital.ai. Attackers target digital banking, FinTech, and payment platforms to intercept data, reverse-engineer authentication mechanisms, and automate fraud.
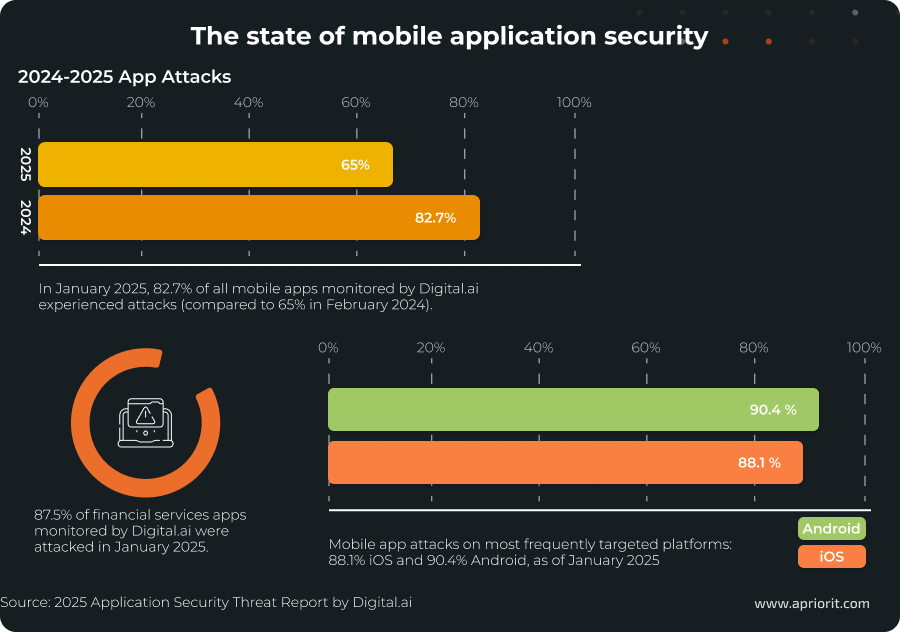
After seeing such numbers, you might want to add the most robust measures to your FinTech app as soon as possible. But first, your team should define what threats to expect. Only after that will your developers be able to pick the most fitting and effective cybersecurity measures.
It’s worth saying that the majority of FinTech security challenges live in:
- The application itself
- The application environment
- The connection between the application and back end
Based on industry research and our own experience securing FinTech apps, we can outline the following threats, risks, and vulnerabilities:
1. Malware targeting banking and financial apps remains one of the most persistent threats in the FinTech space. These malicious programs are designed to infiltrate mobile devices, steal sensitive credentials, and manipulate transactions without user consent.
For example, ToxicPanda, an Android banking trojan, was designed to steal banking and digital wallet logins and perform unauthorized transactions. During an analysis of this malware, researchers discovered a botnet of more than 1,500 compromised Android devices.
For FinTech apps, such attacks can lead to large-scale financial losses and reputational damage.
2. Data breaches in FinTech mobile projects pose many risks due to the highly sensitive nature of financial data. Attackers often exploit vulnerabilities in third-party libraries, insecure APIs, or cloud misconfigurations to gain access to confidential information such as account details, transaction histories, and personally identifiable data. Breaches result in regulatory penalties, erosion of customer trust, and significant financial losses.
In 2025, Wealthsimple experienced a data breach caused by a supply chain attack on a third-party software vendor. One specific software package that was written by a trusted third party had been compromised. Although this incident exposed sensitive client data for less than 1% of users, it likely undermined customer confidence. Such an example illustrates how even limited breaches can harm a brand’s reputation.
3. Man-in-the-middle (MITM) attacks involve intercepting communication between the app and backend services, allowing attackers to capture sensitive financial data or manipulate transactions.
In 2026, we expect MITM threats to be commonplace, as attackers have been exploiting weaknesses in mobile network protocols, outdated SSL/TLS configurations, and compromised Wi-Fi hotspots in recent years. For FinTech apps, where real-time payment processing and personal data exchange occur constantly, such attacks pose severe risks of unauthorized fund transfers and identity theft.
4. API exploitation risks in FinTech mobile projects are escalating as apps rely heavily on APIs for payment gateways, account management, and third-party integrations. Attackers might target exposed or poorly secured APIs to bypass authentication, extract sensitive data, or initiate fraudulent transactions.
There’s also a risk of shadow APIs created during rapid development cycles. Shadow APIs might introduce hidden vulnerabilities, making API exploitation one of the most critical threats for FinTech mobile ecosystems.
5. AI-related risks. Hackers now use AI tools to break app protection measures and complicate the detection of malicious activity. Therefore, FinTech development teams must know what to prepare for.
From Apriorit’s experience, it’s also crucial to watch for AI-related threats and vulnerabilities including:
- Authentication simulation (penetration)
- Sensitive corporate data leaks through AI customer support
- Vulnerable APIs created with the help of LLMs
- Misleading risk signal generation by ML models
- Deepfake threats
According to the Q2 2025 App Threat Report, the banking sector saw a 1,530% surge in deepfake attacks across Asia–Pacific between 2023 and 2024. Such sophisticated AI-powered threats now directly target bank authentication systems and customer accounts.
6. Poor security measures. When conducting security audits on FinTech mobile projects, Apriorit engineers have noticed vulnerabilities that might lead to security incidents.
Here are the most common vulnerabilities we’ve spotted:
- Hardcoded strings aren’t obfuscated
- Sensitive data in session management (no cleanups)
- Hardcoded keys for data encryption
- Hardcoded credentials for bug report and logging systems
- Sensitive data stored in file storage
- MD5 hashing (no longer considered cryptographically secure)
With the main threats in mind, let’s move to practical tips on how to protect your FinTech mobile project.
Looking to strengthen FinTech app security?
Protect your mobile FinTech applications with Apriorit’s mature app development and cybersecurity services. We apply proven protection practices designed to reduce risks, prevent breaches, and support regulatory compliance.
How to secure your FinTech mobile project
True security comes from detailed planning and a strategic approach. To help you plan your application development, we’ll provide several recommendations based on our experience, covering the most crucial areas of mobile app security.
Below, we offer six strategic tips that will help your team ensure reliable protection for a FinTech mobile app. These FinTech app security best practices are a good starting point for reliable cyber protection.
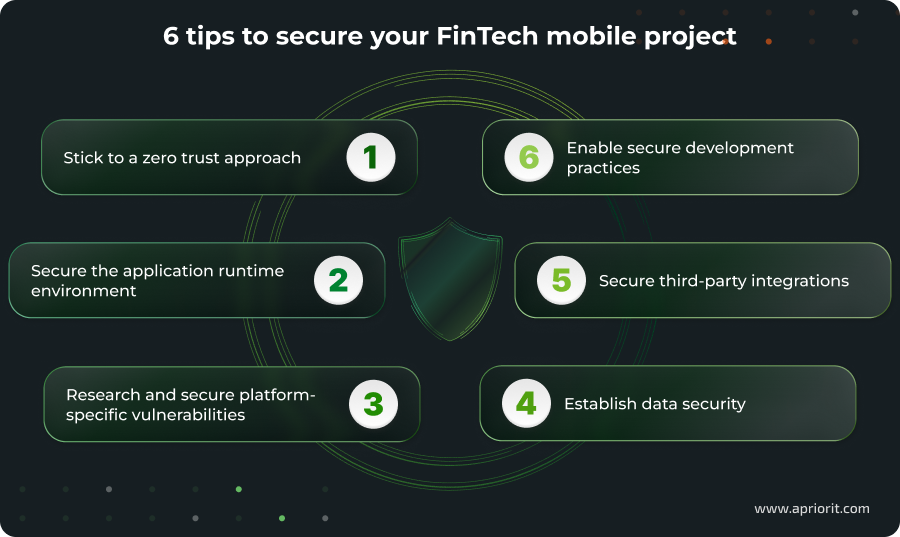
1. Stick to a zero trust approach
Zero trust architecture assumes that no entity (device, app, network, user session, or admin account) is trustworthy by default. This approach prioritizes continuous identity verification and context checking instead of only relying on network location.
This is why zero trust became crucial for FinTech mobile apps that store and process sensitive financial and user data.
Why use a zero trust approach:
- Mitigate risks from rooted or jailbroken devices, compromised operating systems, malware, reverse-engineered apps, API abuse, stolen tokens, and replay attacks.
- Ensure a clear security blueprint for mobile architecture, enabling secure innovations step by step without slowing down delivery.
- Align the development process with your compliance needs while reducing the impact of breaches and preserving the user experience.
How to apply a zero trust approach in your FinTech mobile project:
- Ensure advanced authentication and authorization to effectively secure accounts and data, protecting them from unauthorized access.
- Enable mechanisms that support the principle of least privilege, making sure that users, devices, and services get only the access they actually need.
- Introduce explicit verification for every action related to sensitive data: transferring money, editing personal information, etc.
- Apply risk-based policies and adaptive access, tightening controls when risks increase.
- Establish continuous monitoring to detect anomalies in user and system behavior: impossible travel, unusual transaction patterns, etc.
Getting into the right mindset before planning FinTech app architecture is crucial. Consider designing your system as if attackers already have partial access to it. Assume it’s been breached. Such a mindset will help your team ensure robust security at all layers, reducing the attack surface and minimizing consequences in case of a successful attack.
Maksym Itskovich, Director of Global Markets Development at Apriorit
2. Secure the application runtime environment
Almost any application can be compromised while running on a user’s device. The reason is that at runtime, attackers can hook functions, inject malicious code, or manipulate API requests. Therefore, it’s crucial to introduce advanced measures to your runtime environment before releasing the product.
Though each project might require specific security mechanisms, we can offer several key recommendations suitable for the majority FinTech apps:

- Obfuscate code to reduce the risk of hacking and reverse engineering, making it harder for attackers to extract or alter critical algorithms.
- Conduct pre-production obfuscation to safeguard intellectual property and sensitive logic and to complicate malicious reverse engineering efforts before release.
- Obfuscate hardcoded strings like credentials and API keys to reduce exposure if the app is decompiled.
- Restrict the app’s launch on rooted and jailbroken devices with dedicated checks to prevent attackers from bypassing your security controls with root-level privileges.
- Implement integrity checks and patching protection, as validating the app signature and bytecode at runtime prevents unauthorized modifications or injected code from executing.
- Schedule app releases to reduce the window for exploiting known vulnerabilities and keep security patches current. The frequency depends on your product roadmap, security audit results, current patching needs, implementation of functionality updates, etc.
- Force users to update the application with in-app pop-ups to ensure all users run the latest secure version, minimizing risks from outdated builds.
- Use safe logging with no sensitive data, ensuring that logs don’t expose sensitive information. Sanitizing them prevents data leaks during debugging or attacks.
- Implement runtime defenses to block attackers’ code injection attempts.
- Refresh authorization tokens when the app goes to background to reduce the risk of session hijacking if the device is compromised while idle.
- Implement device-related trust scoring (by device identifier, geolocation, IP, etc.), adding an extra layer of behavioral analysis and helping to detect suspicious activity or compromised environments.
Watch webinar
Mastering Security for FinTech Mobile Applications: Advanced Strategies
Learn how to fortify your FinTech mobile app, safeguard transactions, and enhance compliance with robust security practices. Watch the webinar now!
3. Research and secure platform-specific vulnerabilities
When building truly protected FinTech applications, it’s vital to understand the unique risks associated with Android and iOS. Each ecosystem has its strengths and weaknesses, and your security strategy should reflect them.
Let’s break down the most important aspects of each platform:
Platform-specific considerations when securing FinTech apps
| Android | iOS | |
|---|---|---|
| Overall security | Considered more vulnerable due to open ecosystem and fragmentation | Considered safer thanks to closed ecosystem and strict app review |
| Update consistency | Fragmented; many devices run outdated OS versions | Regular updates enforced by Apple |
| Device risks | Budget devices often lack timely patches | Strong hardware security in iOS 12+ |
| Malware threats | High; risks of keylogging and traffic sniffing | Low; exploits are rare and costly |
| Third-party apps | Unsigned apps can be installed from unknown sources | No root access for regular vendors |
| Secure features | TrustZone available for sensitive operations | Secure Enclave and advanced encryption |
| Safe features | Google Pay, NFC, biometric authentication | Apple Pay, NFC, biometric authentication |
4. Establish data security
Every piece of data your financial app processes and stores must be protected, from sensitive account details to transaction histories.
In FinTech projects, data security must be an ongoing process rather than a one-time effort. Maintaining a resilient environment against breaches and fraud directly impacts your product success and compliance. So, make sure your team implements robust encryption, minimizes offline storage, runs regular updates, and adds hardware-backed security features.
Maksym Itskovich, Director of Global Markets Development at Apriorit
Our biggest tip is to pay attention to data across all states: at rest, in use, and in transit.
Data at rest:
- Minimize offline storage unless absolutely necessary, as it increases risks of data exposure and data theft.
- Implement additional security measures for relational database management powered by SQLite. SQLite databases are common in mobile apps, so it’s worth encrypting and restricting access to prevent data leaks.
- Encrypt sensitive data with hardware encryption algorithms, as hardware-backed encryption provides stronger protection than software-only solutions.
- Apply a hardware-backed keystore for Android (such as Android Keystore) to securely store cryptographic keys, reducing the risk of extraction.
- Use StrongBox Keymaster, which offers tamper-resistant hardware for key storage on supported Android devices.
- Enable Secure Enclave for iOS that isolates sensitive operations, protecting keys and biometric data.
- Store tokens and API keys in an encrypted keystore to prevent attackers from retrieving credentials if the app is compromised.
- Avoid using outdated cryptographic algorithms like MD5, SHA-1, and RC4. Instead, consider AES, RSA, or ECDSA with ≥128-bit keys (256-bit recommended).
Data in use:
- Store session data only when the application is active and clean session data when it goes to the background. This reduces exposure if the device is compromised while idle.
- Store sensitive data only when necessary, and avoid keeping sensitive information in memory longer than required.
- Protect the app with PIN-based authentication to add an extra layer of security for accessing sensitive features.
- Introduce screenshot restrictions to prevent sensitive data from being captured by malicious apps or users.
- Avoid sharing CVC codes and rotate CVC codes to reduce the risk of card fraud.
- Implement two-factor authentication to strengthen protection against unauthorized transactions.
- Apply additional API requests for sensitive data like bank account credentials and full credit card numbers. Splitting sensitive data requests reduces exposure in case of interception.
Data in transit:
- Use reverse proxy for application API access to securely manage traffic and hide backend architecture.
- Use TLS handshakes with Diffie–Hellman for key exchange and encryption. This ensures secure communication and prevents eavesdropping.
- Check bundle checksums to avoid MITM attacks. Verifying app integrity prevents tampered app versions from running.
- Conduct regular audits and release application updates. Make sure to establish code audit and security audit schedules, aligning their frequency with your project needs. Such measures help you detect issues early and quickly prepare app updates, patching vulnerabilities and maintaining security compliance.
Read also
How to Ensure the Security of Your Mobile Banking App: Tips and Best Practices
Improve the cybersecurity of your mobile banking app by applying proven security practices that help protect sensitive data and prevent financial fraud.

5. Secure third-party integrations
Third-party services are crucial to make your FinTech app competitive, as they offer features such as payments, advanced analytics, and 24/7 customer support. On the downside, they introduce significant security risks if not properly managed.
We recommend starting to secure your integrations by outlining all integrations your project uses. This way, you will know what to secure before deciding how to secure it.
Below, we outline best practices for securing APIs, external libraries, and SDKs to help your team maintain a robust security posture:
- Follow proven third-party library security practices such as automated vulnerability scanning, rigorous vetting, version control maintenance, and continuous monitoring. This will help you mitigate supply chain risks, aligning with DORA requirements and OWASP guidelines.
- Develop your own authentication and authorization logic, as custom implementation can help you ensure proper compliance and control. Relying on third-party solutions may be insecure.
- Make integrations through the back end as much as possible to help your team reduce exposure of sensitive logic and credentials on the client side.
- Don’t use untrustworthy repositories, as third-party packet downloads from unofficial sources increase the risk of malicious code injection. Make sure your team prioritizes acknowledged resources, reads package vulnerability publications, and checks whether regular updates are in place.
- Secure WebView-based solutions from exploits due to XSS and CRLF attacks. As an application developer, you’re responsible for the protection of a WebViews-based app, so make sure your team sanitizes inputs and disables risky features.
While third-party tools accelerate development and enhance functionality, they can become weak links in your security chain. Continuous monitoring and timely updates are critical to keeping your app secure against evolving threats.
6. Enable secure development practices
Protecting your app development environment is just as critical as securing the application itself. A compromised development pipeline can lead to severe vulnerabilities.
Securing the development environment is a proactive measure that prevents vulnerabilities from entering your application as it’s being built. Consider implementing role-based access control for repositories, mandatory code reviews for critical modules, and dependency vulnerability scanning as additional safeguards.
Implementing strong and adequate secure development practices before production is much cheaper and faster than fixing breaches, losing customers, and paying fines for non-compliance. Beyond financial penalties, security failures can also damage your brand’s reputation, erode customer trust, and lead to long-term loss of market credibility.
Maksym Itskovich, Director of Global Markets Development at Apriorit
Our recommendations to protect the development environment for your FinTech mobile app:
- Apply a general incident management approach. Establish clear protocols for detecting, reporting, and mitigating security incidents during development to reduce response time and impact.
- Protect developers’ workstations. Endpoint security solutions protect developers’ machines from malware, unauthorized access, and data leaks.
- Avoid hardcoding wherever possible. Leaving hardcoded credentials or keys is one of the most common, yet dangerous, mistakes. Hardcoded credentials are easily extracted from source code. Make sure to use secure vaults or environment variables instead. Hardcoding might be acceptable for non security-related values and for apps that have a demo environment as long as it’s clearly separated from production code.
- Establish security benchmarks. Define measurable security standards for code quality, encryption, and compliance to maintain consistency across teams.
- Introduce development routines. A secure software development lifecycle (SDLC) helps your team integrate security checks at every stage, reducing vulnerabilities before release.
- Use separate staging and production environments. Isolating environments prevents accidental data leaks and unauthorized access to production systems during testing.
- Introduce coding standards. Enforcing coding standards and using approved static analysis tools helps detect vulnerabilities early. And a standardized way to create tests ensures functional and security integrity.
- Implement CI/CD pipelines. Automated pipelines streamline secure deployments and allow integration of security scans into build processes.
- Use separate pre-compiled modules for the most critical logic and perform runtime checksum verification. Pre-compiling sensitive logic and verifying integrity at runtime prevents tampering and malicious reverse engineering attempts.
Related project
Building a Blueprint for Secure Lending Mobile App Development: Discovery Phase
Find out how our discovery process supported the successful launch of a microfinance app by aligning business objectives with technical feasibility, timelines, and development priorities.

Compliance and regulatory considerations for FinTech apps
Compliance and regulatory considerations directly affect the way you secure your mobile apps.
Regulatory frameworks define strict requirements for data protection, authentication, and risk management. Failure to comply can lead to hefty fines, reputational damage, and even service suspension.
More importantly, these regulations often dictate security architecture choices, such as encryption standards, secure APIs, and audit mechanisms.
Here’s how major compliance requirements impact FinTech mobile app development:
- The Payment Services Directive 2 (PSD2) requires Strong Customer Authentication and secure communication between banks and third-party providers. This means implementing multi-factor authentication and encrypted APIs.
- The Payment Card Industry Data Security Standard (PCI DSS) governs how cardholder data is stored and transmitted. To comply with it, developers must use end-to-end encryption and tokenization, and they must avoid storing sensitive card data on mobile devices.
- System and Organization Controls 2 (SOC 2) focuses on security, availability, and confidentiality for service providers. For mobile apps, this translates into robust access controls, monitoring, and incident response plans.
- The General Data Protection Regulation (GDPR) requires data minimization, user consent, and breach notification. Apps must implement privacy by design principles, ensure secure data storage, and allow users to manage their personal data.
- The Digital Operational Resilience Act (DORA) introduces requirements for IT resilience and risk management. Mobile apps must support continuous monitoring, disaster recovery, and vulnerability management.
Building truly secure yet successful FinTech apps demands balancing robust cybersecurity mechanisms with availability of useful features and a smooth user experience. Delegating tasks to a software development vendor with relevant experience and cybersecurity expertise is your key to achieving that balance.
Enhance your FinTech app protection with Apriorit
With 22+ years in cybersecurity and 160+ completed security audits, Apriorit is ready to help you deliver a reliable and competitive FinTech mobile project. We focus on creating bullet-proof solutions that mitigate threats and scale on demand without degrading the user experience.
To align your app architecture with cybersecurity best practices and compliance standards, we will:
- Implement strong authentication and authorization mechanisms
- Encrypt data and tokenize sensitive information
- Replace card data with tokens to reduce PCI DSS compliance scope
- Minimize data collection, anonymize data where possible, and provide clear consent flows for GDPR compliance
- Enable continuous monitoring and logging, integrate SIEM functionality, and configure automated alerts
- Help create a clear plan for incident response and disaster recovery to ensure resilience and compliance with DORA requirements

Apriorit’s experience covers various types of projects. We have:
- Developed an app for the Saudi Arabian government that’s integrated with seven ministries
- Successfully participated in a public bug bounty for the second largest neobank in Ukraine (7.9 million clients)
- Created a US-based data-in-rest storage product with unique quantum encryption algorithms
- And more
Let’s take a look at a few other client success stories:
Case 1. Developing a flexible and secure dApp for international remittance payments
Our client wanted to create a secure and transparent solution for international money transfers using blockchain technology.
A key part of their goal was to overcome the following challenges:
- Low flexibility, as smart contracts are hard to update once deployed
- Slow operations due to Ethereum’s Proof of Work limitations
- High transaction costs, as smart contract execution costs could spike under heavy network load
The Apriorit team delivered a new decentralized application built on an Ontology fork, along with a web wallet and an Android client, all hosted on AWS.
As a result of our collaboration, the client received:
- A fast, flexible, and cost‑efficient cross‑border remittance solution
- Higher throughput with ultra‑low fees
- Improved smart contracts
- Multi-platform app support
Case 2. Evaluating smart contract security for decentralized finance (DeFi)
Our client, a decentralized yield farming platform on the Tezos blockchain, wanted to ensure the security and reliability of their smart contracts before scaling their solution.
The client’s main challenges were:
- Detecting vulnerabilities in DeFi and swap smart contracts
- Building trust with users through an independent security audit
The Apriorit team conducted a comprehensive audit that included code analysis, manual testing, and reviewing against known vulnerabilities.
By the end of this project, our client received:
- A detailed report uncovering 15 vulnerabilities, including 2 high-risk and 6 medium-risk issues
- Actionable recommendations to fix critical flaws and strengthen governance mechanisms
- Improved code quality and a 20–30% increase in unit test coverage
- Optimized gas usage for better performance
Case 3. Developing a secure enterprise MDM solution for Android tablets
A US-based provider of secure communication services to corporations and government institutions needed a tamper-proof MDM solution for Android tablets.
Challenges included:
- Preventing users from rebooting, resetting, loading safe mode, or turning off tablets
- Disabling access to device settings and unauthorized internet connections
- Implementing centralized device management and activity monitoring
- Offering a custom content marketplace alongside core MDM functions
The Apriorit team delivered a complex, custom MDM solution with firmware-level controls to lock device functions. We also developed a secure admin panel, an integrated custom store, and a system for centralized user/device management.
Results our client gained included:
- Secure deployment of 5,000+ tablets to enterprise users
- Robust protection against unauthorized device manipulation
- Seamless centralized management and content distribution via the admin portal
Conclusion
An excess of protection measures inevitably degrades the user experience, so your team must balance go-to-market plans and security. And since it’s not possible to make a 100% safe solution, your team has to continually review and upgrade your software security to deal with current and upcoming threats.
To deliver a competitive and functional FinTech product:
- Create a list of prioritized risks
- Teach your users about application security
- Conduct regular (preferably external and independent) security audits and penetration testing
- Learn as you go, but keep your security in focus
Whatever project you have in mind and whatever FinTech app security requirements you’re obliged to follow, Apriorit is ready to assist you with professional FinTech development and cybersecurity services.
Need end-to-end FinTech mobile security expertise?
Develop and protect mobile FinTech applications with our cybersecurity-focused approach that helps you mitigate threats, meet compliance demands, and deliver secure user experiences.
FAQ
What is FinTech mobile security?
<p>FinTech mobile security is a set of practices, technologies, and measures designed to protect financial technology applications on mobile platforms from cyber threats such as data breaches, fraud, identity theft, and unauthorized access.</p>
<p>FinTech security ensures the confidentiality, integrity, and availability of sensitive financial data and transactions conducted through mobile devices.</p>
What are the top security threats specific to FinTech mobile applications?
<p>When establishing mobile application security for FinTech projects, pay attention to unique risks that FinTech apps face due to handling financial transactions and sensitive data.</p>
<p>Common threats include:</p>
<ul class=apriorit-list-markers-green>
<li>Data breaches from insecure storage or transmission</li>
<li>MITM attacks during network communication</li>
<li>API exploitation through weak authentication or improper rate limiting</li>
<li>Client-side attacks like reverse engineering, code tampering, and root/jailbreak exploits</li>
<li>Fraud and account takeover via phishing or credential stuffing</li>
</ul>
How can I protect sensitive data in my FinTech mobile app?
<p>Key security measures for FinTech mobile projects include:</p>
<ul class=apriorit-list-markers-green>
<li>End-to-end encryption for data in transit</li>
<li>Strong encryption for data at rest</li>
<li>Secure key management using hardware-backed keystores</li>
<li>Tokenization for sensitive identifiers like card numbers</li>
<li>Not storing unnecessary data on the device or server</li>
</ul>
What are best practices for securing APIs and backend services in FinTech apps?
<p>Best practices for securing APIs and backend services in FinTech apps include:</p>
<ul class=apriorit-list-markers-green>
<li>Use OAuth 2.0 or OpenID Connect for secure authentication</li>
<li>Implement rate limiting and throttling to prevent abuse</li>
<li>Validate all inputs to avoid injection attacks</li>
<li>Enforce HTTPS and HSTS for all API calls</li>
<li>Apply role-based access control and least privilege principles</li>
<li>Regularly rotate API keys and credentials</li>
</ul>
How can I protect my mobile FinTech app from client-side threats like root/jailbreak, reverse engineering, or tampering?
<p>Secure FinTech app development requires a comprehensive cybersecurity strategy that’s tailored to your project. However, certain practices are suitable for the majority of FinTech projects:</p>
<ul class=apriorit-list-markers-green>
<li>Root/jailbreak detection and block execution on compromised devices</li>
<li>Code obfuscation and anti-tampering checks to make reverse engineering harder</li>
<li>Runtime integrity checks to detect unauthorized modifications</li>
<li>Secure storage using OS-provided mechanisms like Keychain and Keystore</li>
<li>Certificate pinning to prevent MITM attacks</li>
</ul>
Which regulations and standards apply to FinTech mobile apps, and how do they affect security design?
<p>Key regulations and standards to pay attention to include:</p>
<ul class=apriorit-list-markers-green>
<li>PCI DSS for handling payment card data</li>
<li>GDPR for protecting personal data in the EU</li>
<li>PSD2 for secure payment services in Europe</li>
<li>SOC 2 for service organization controls</li>
<li>Local banking regulations in regions where your product operates</li>
</ul>
How can I balance strong security controls with a user-friendly mobile FinTech experience?
<p>Here are a few recommendations to deliver secure FinTech apps while providing a smooth user experience:</p>
<ul class=apriorit-list-markers-green>
<li>Use biometric authentication like fingerprint and Face ID for convenience and security</li>
<li>Implement risk-based authentication: for example, step-up verification only for suspicious activity</li>
<li>Optimize encryption and security checks to avoid performance bottlenecks</li>
<li>Provide a clear UX for security actions: for example, explain why extra verification is needed</li>
<li>Leverage secure SDKs and APIs to reduce complexity for developers and users</li>
</ul>




